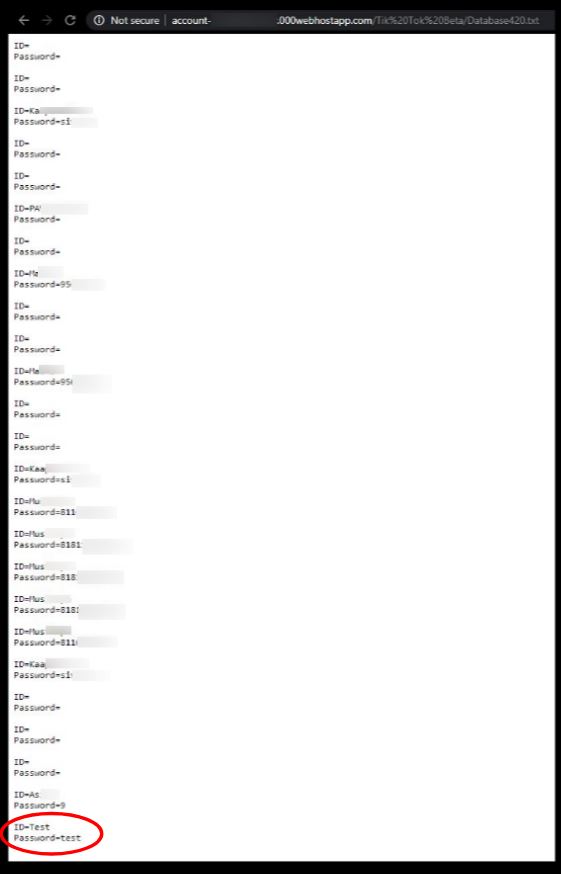
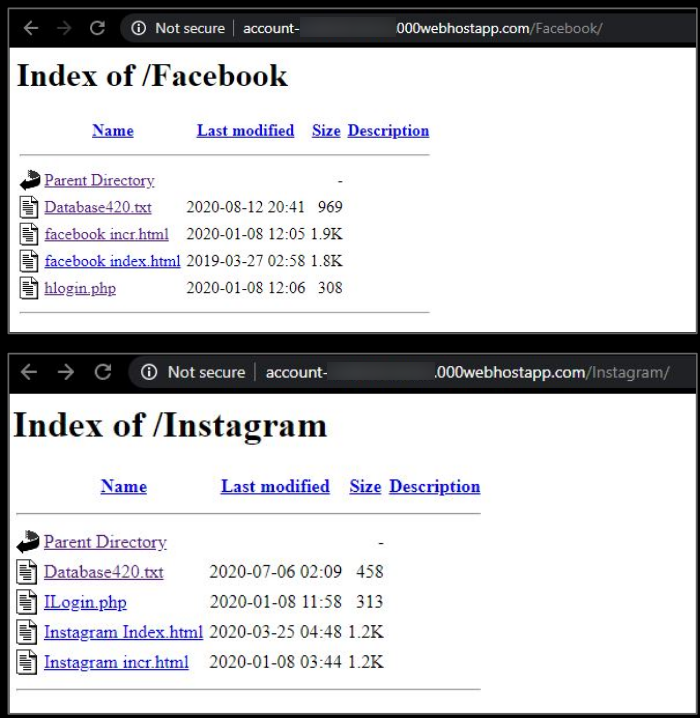
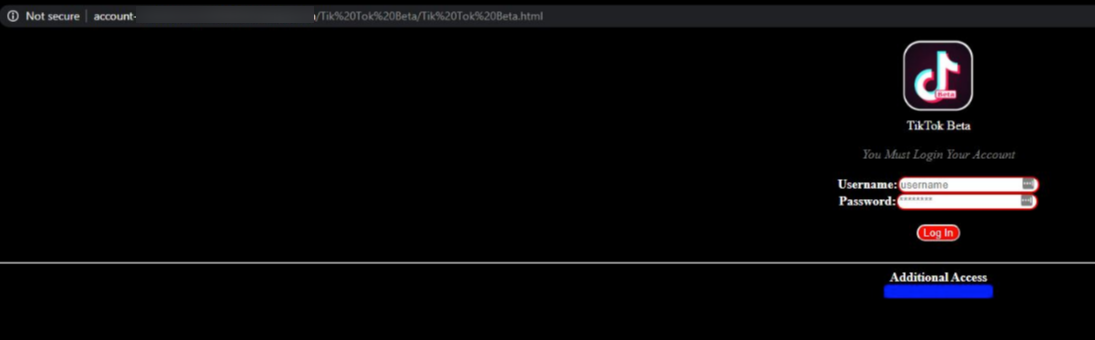
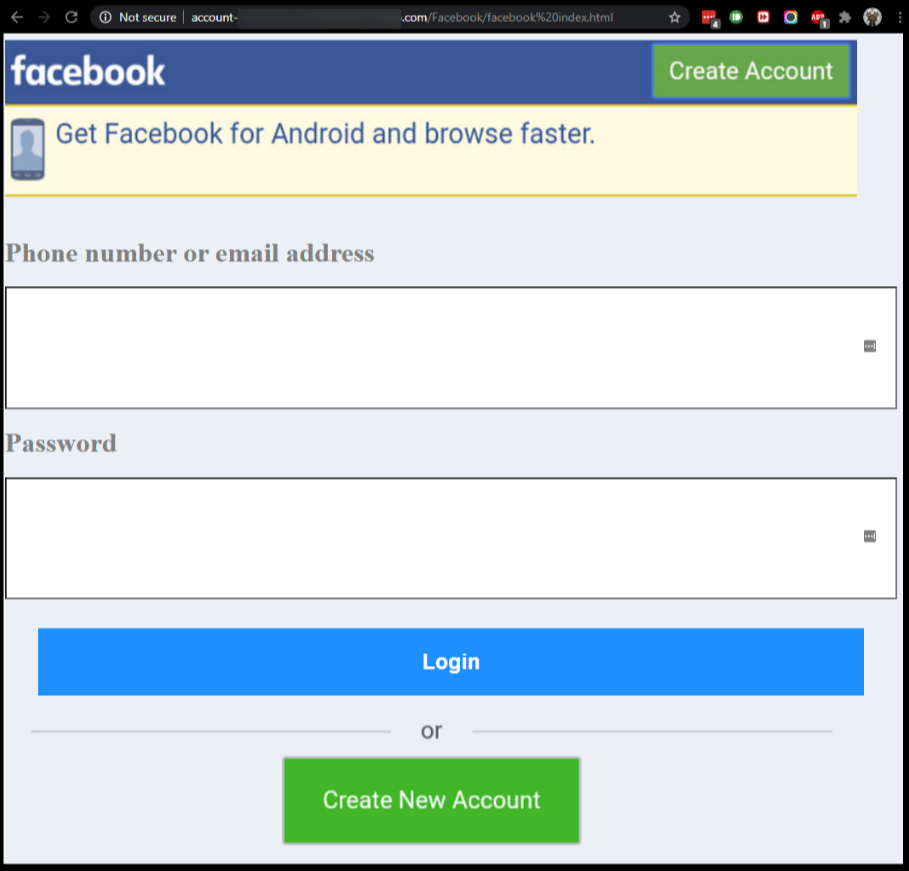
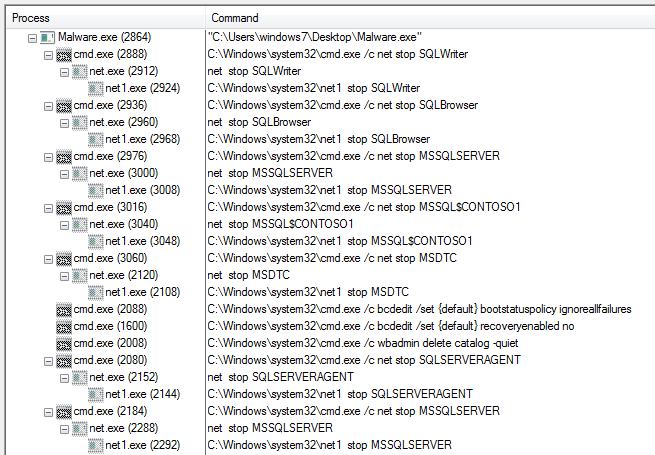
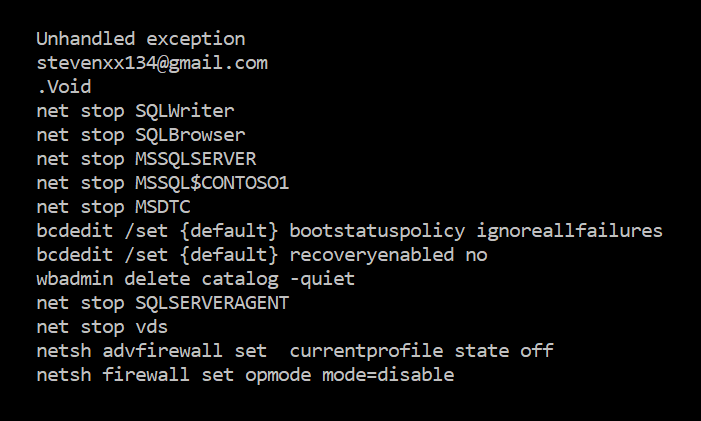
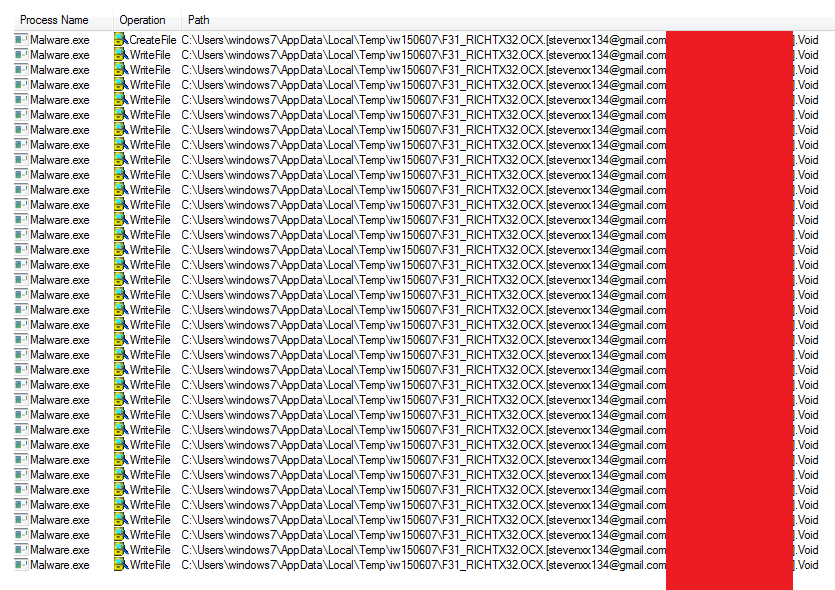
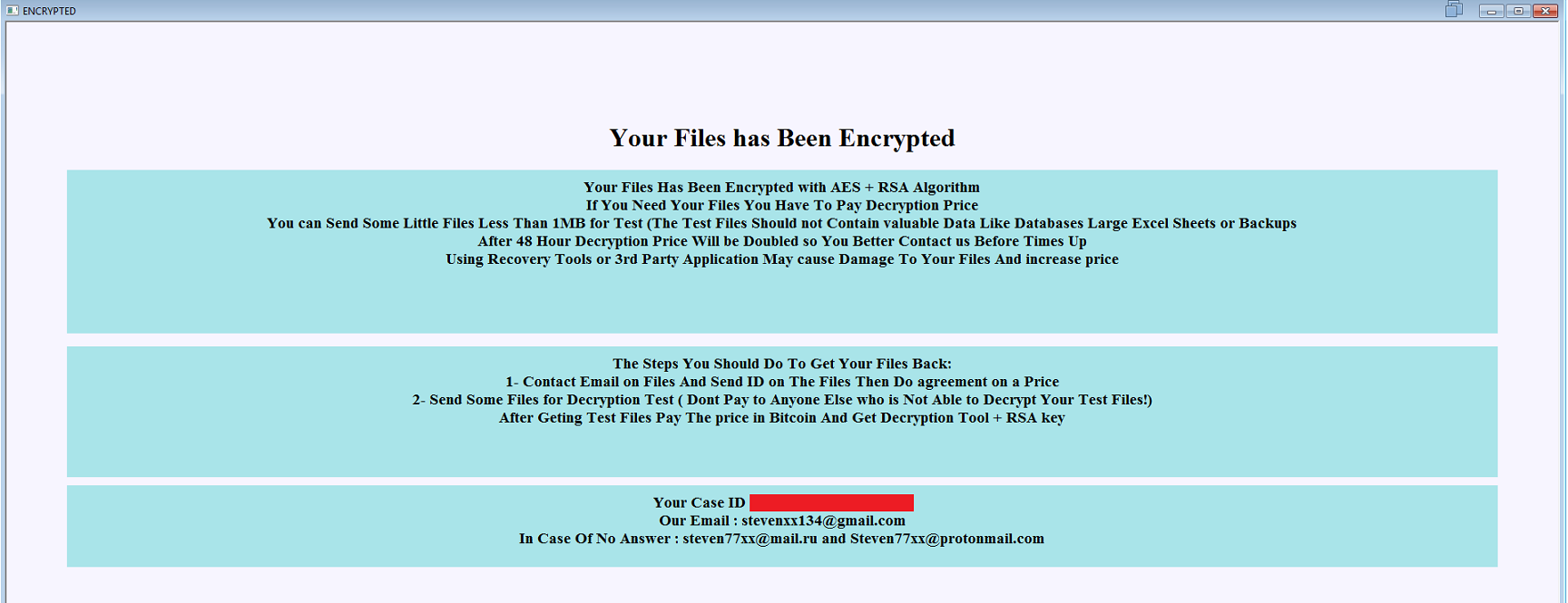
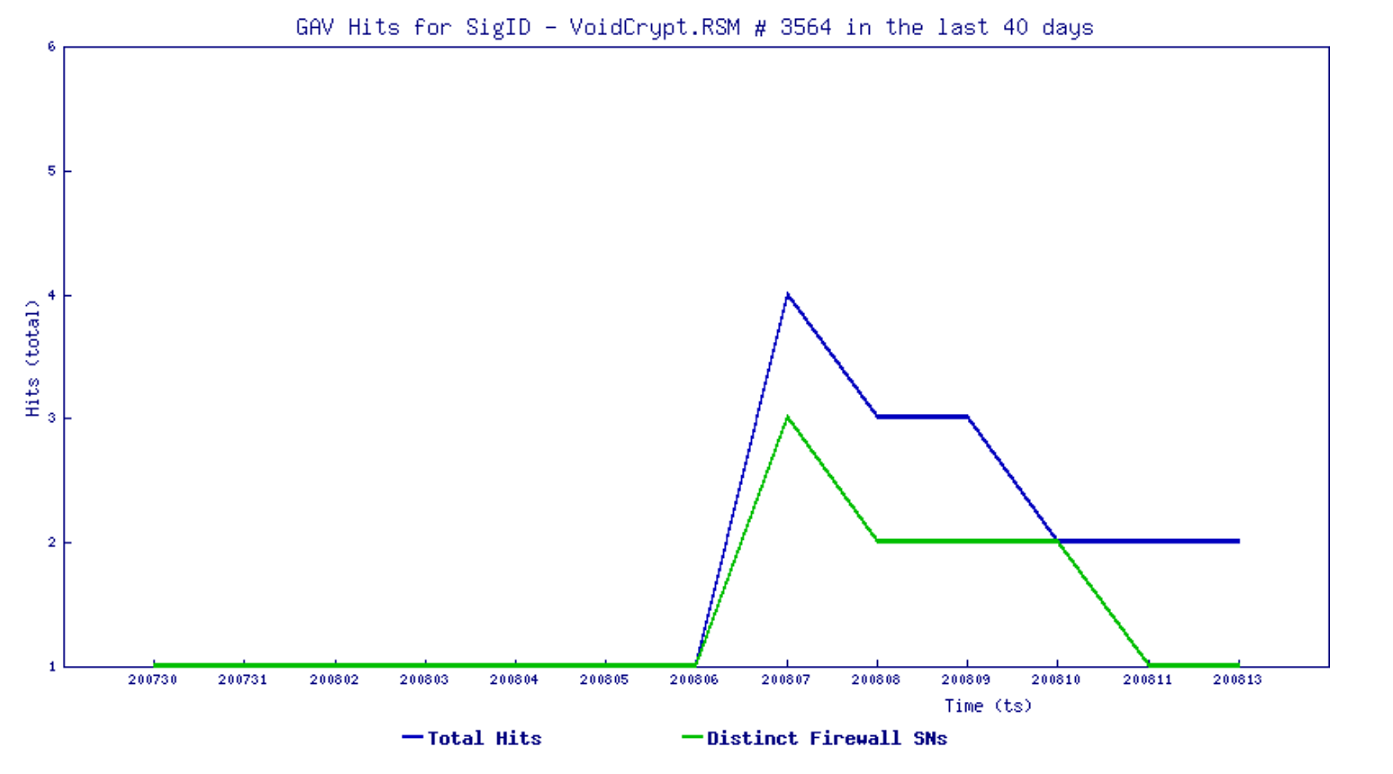
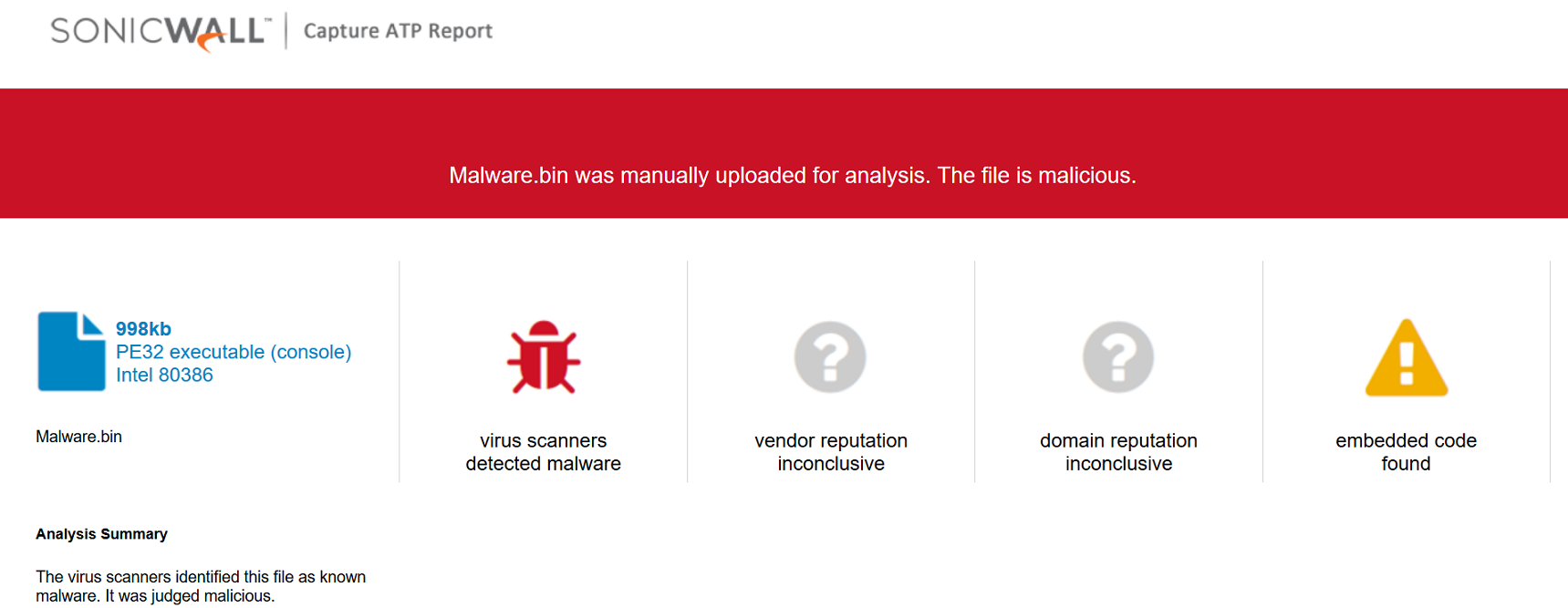
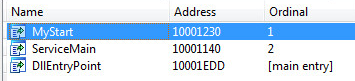
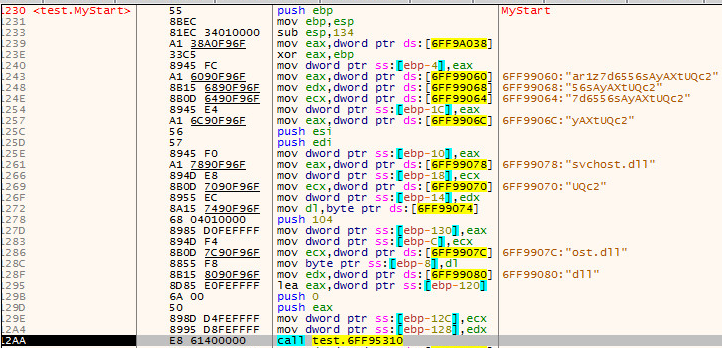
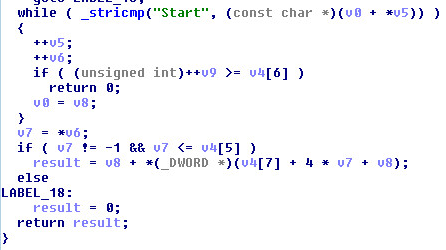
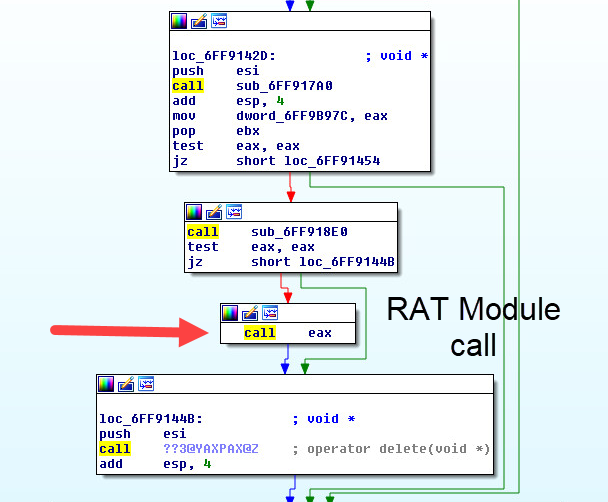
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of August 2020. A list of issues reported, along with SonicWall coverage information are as follows:
CVE-2020-1380 Scripting Engine Memory Corruption Vulnerability
IPS 15107:Scripting Engine Memory Corruption Vulnerability (CVE-2020-1380)
IPS 15109:Scripting Engine Memory Corruption Vulnerability (CVE-2020-1380)2
CVE-2020-1464 Windows Spoofing Vulnerability
ASPY 5983:Malformed-File msi.MP.1
CVE-2020-1472 Netlogon Elevation of Privilege Vulnerability
IPS 15143:Windows Netlogon Elevation of Privilege Vulnerability(CVE-2020-1472)
CVE-2020-1480 Windows GDI Elevation of Privilege Vulnerability
IPS 2282:BAD-FILES: Suspicious Executable File Download 9
CVE-2020-1529 Windows GDI Elevation of Privilege Vulnerability
ASPY 5982:Malformed-File exe.MP.150
CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability
ASPY 5452:Malformed-File exe.MP.64
CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability
IPS 15105:MSHTML Engine Remote Code Execution (CVE-2020-1567)
CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability
IPS 15106:Scripting Engine Memory Corruption Vulnerability (CVE-2020-1570)
CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability
ASPY 5981:Malformed-File exe.MP.152
CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability
ASPY 5980:Malformed-File exe.MP.151
CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
ASPY 5979:Malformed-File exe.MP.153
Adobe Coverage:
CVE-2020-9697 Acrobat Reader Disclosure of Sensitive Data
ASPY 5984:Malformed-File pdf.MP.334
CVE-2020-9693 Acrobat Reader Arbitrary Code Execution
ASPY 5985:Malformed-File pdf.MP.335
Following vulnerabilities do not have exploits in the wild :
CVE-2020-0604 Visual Studio Code Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1046 .NET Framework Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1337 Windows Print Spooler Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1339 Windows Media Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1377 Windows Registry Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1378 Windows Registry Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1379 Media Foundation Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1383 Windows RRAS Service Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1417 Windows Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1455 Microsoft SQL Server Management Studio Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2020-1459 Windows ARM Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1466 Windows Remote Desktop Gateway (RD Gateway) Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2020-1467 Windows Hard Link Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1470 Windows Work Folders Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1473 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1474 Windows Image Acquisition Service Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1475 Windows Server Resource Management Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1476 ASP.NET and .NET Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1477 Media Foundation Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1478 Media Foundation Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1479 DirectX Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1483 Microsoft Outlook Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1484 Windows Work Folders Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1485 Windows Image Acquisition Service Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1486 Windows Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1487 Media Foundation Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1488 Windows AppX Deployment Extensions Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1489 Windows CSC Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1490 Windows Storage Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1492 Media Foundation Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1493 Microsoft Outlook Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1494 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1495 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1496 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1497 Microsoft Excel Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1498 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1499 Microsoft SharePoint Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2020-1500 Microsoft SharePoint Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2020-1501 Microsoft SharePoint Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2020-1502 Microsoft Word Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1503 Microsoft Word Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1504 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1505 Microsoft SharePoint Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1509 Local Security Authority Subsystem Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1510 Win32k Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1511 Connected User Experiences and Telemetry Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1512 Windows State Repository Service Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1513 Windows CSC Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1515 Windows Telephony Server Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1516 Windows Work Folders Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1517 Windows File Server Resource Management Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1518 Windows File Server Resource Management Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1519 Windows UPnP Device Host Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1520 Windows Font Driver Host Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1521 Windows Speech Runtime Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1522 Windows Speech Runtime Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1524 Windows Speech Shell Components Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1525 Media Foundation Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1526 Windows Network Connection Broker Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1527 Windows Custom Protocol Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1528 Windows Radio Manager API Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1530 Windows Remote Access Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1531 Windows Accounts Control Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1533 Windows WalletService Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1534 Windows Backup Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1535 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1536 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1537 Windows Remote Access Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1538 Windows UPnP Device Host Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1539 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1540 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1541 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1542 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1543 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1544 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1545 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1546 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1547 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1548 Windows WaasMedic Service Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1549 Windows CDP User Components Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1550 Windows CDP User Components Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1551 Windows Backup Engine Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1552 Windows Work Folder Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1553 Windows Runtime Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1554 Media Foundation Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1555 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1556 Windows WalletService Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1557 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1558 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1560 Microsoft Windows Codecs Library Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1561 Microsoft Graphics Components Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1563 Microsoft Office Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1565 Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2020-1571 Windows Setup Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1573 Microsoft Office SharePoint XSS Vulnerability
There are no known exploits in the wild.
CVE-2020-1574 Microsoft Windows Codecs Library Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1577 DirectWrite Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1580 Microsoft Office SharePoint XSS Vulnerability
There are no known exploits in the wild.
CVE-2020-1581 Microsoft Office Click-to-Run Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2020-1582 Microsoft Access Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1583 Microsoft Word Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2020-1585 Microsoft Windows Codecs Library Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2020-1591 Microsoft Dynamics 365 (On-Premise) Cross Site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2020-1597 ASP.NET Core Denial of Service Vulnerability
There are no known exploits in the wild.