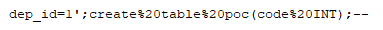IoT Devices: If You Connect It, Protect It
7 “Smart” Steps to secure and protect your Home Network
A refrigerator that tells you there was a power outage — and whether it lasted long enough to spoil your food. Doorbells show you who’s at the door and allow you to communicate with them from across the country. Home medical devices that can collect data and transmit it directly to your doctor.
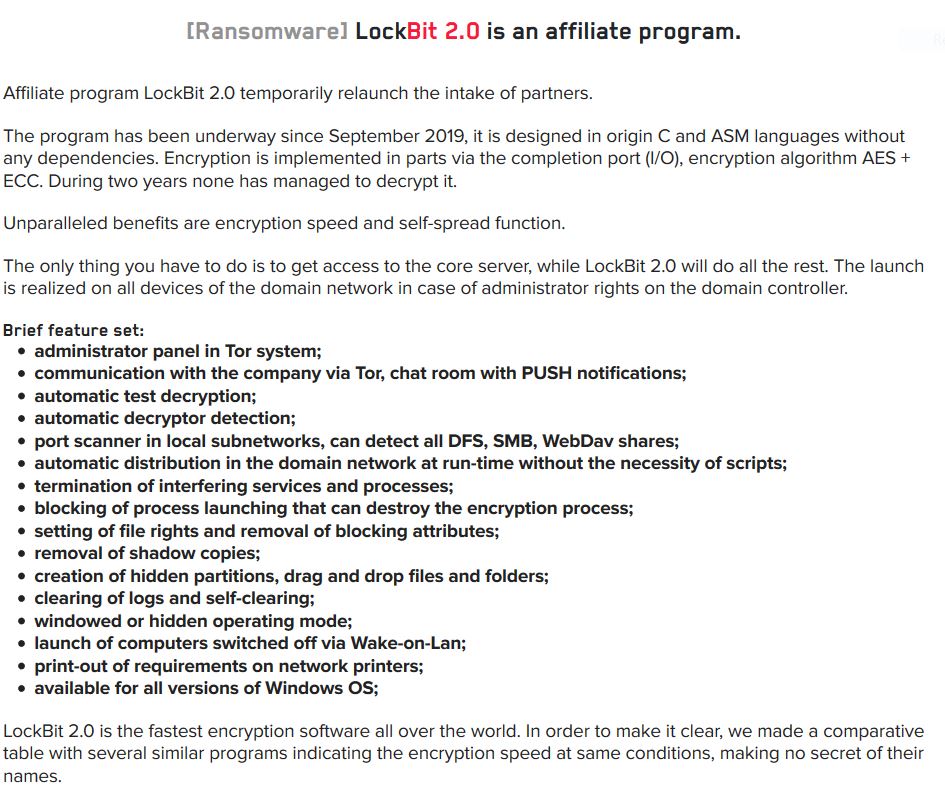
Present in countless applications, smart devices have revolutionized the way we live and work. Smart devices are a subset of a larger group of internet-connected products known as IoT (Internet of Things) devices. These devices can be controlled remotely, usually through a smartphone app or webpage, and send and receive data without human intervention.
In the 20 years since the term got wide usage, the number and scope of IoT devices have grown tremendously. According to Security Today, from 2018 through 2020, IoT devices jumped from 7 billion to 31 billion, with 127 new IoT devices coming online each second.
By 2020, IoT technology is expected to be present in the designs of 95% of new electronics products. And over the next five years, the number of connected devices is forecasted to climb to 41.6 billion and generate a mind-boggling 79.4 ZB of data (for reference, the entirety of the World Wide Web, as it existed in 2009, was estimated to be less than a half a ZB.)
Smart devices introduce conveniences unthinkable a decade ago. But unfortunately, they also bring a new set of risks that could endanger your privacy and your data, your other devices, and even other connected networks.
For starters, there’s currently no standard for securing IoT devices — companies are free to put as much or as little security in their products as they want. Even when vulnerabilities are discovered, many devices are not updated because their cost is too low, or there is no way to update them. When are updates are available, they’re never pushed out, or customers never hear about them. In all, IoT devices are open to wide exploitation.
However, there are several other risks related to the way people use these devices. Many users believe they don’t have the time or expertise to secure their IoT devices adequately — and that, because they’re not a large business or high-profile individual, they’re unlikely to be targeted.
But work statistics since COVID-19 has changed all that. According to Global Workplace Analytics, 25-30% of the American workforce now works from home. That means cybercriminals increasingly see remote employees’ home networks — especially poorly secured IoT devices that connect to them — as a back door to compromise corporate networks with lower chances of detection.
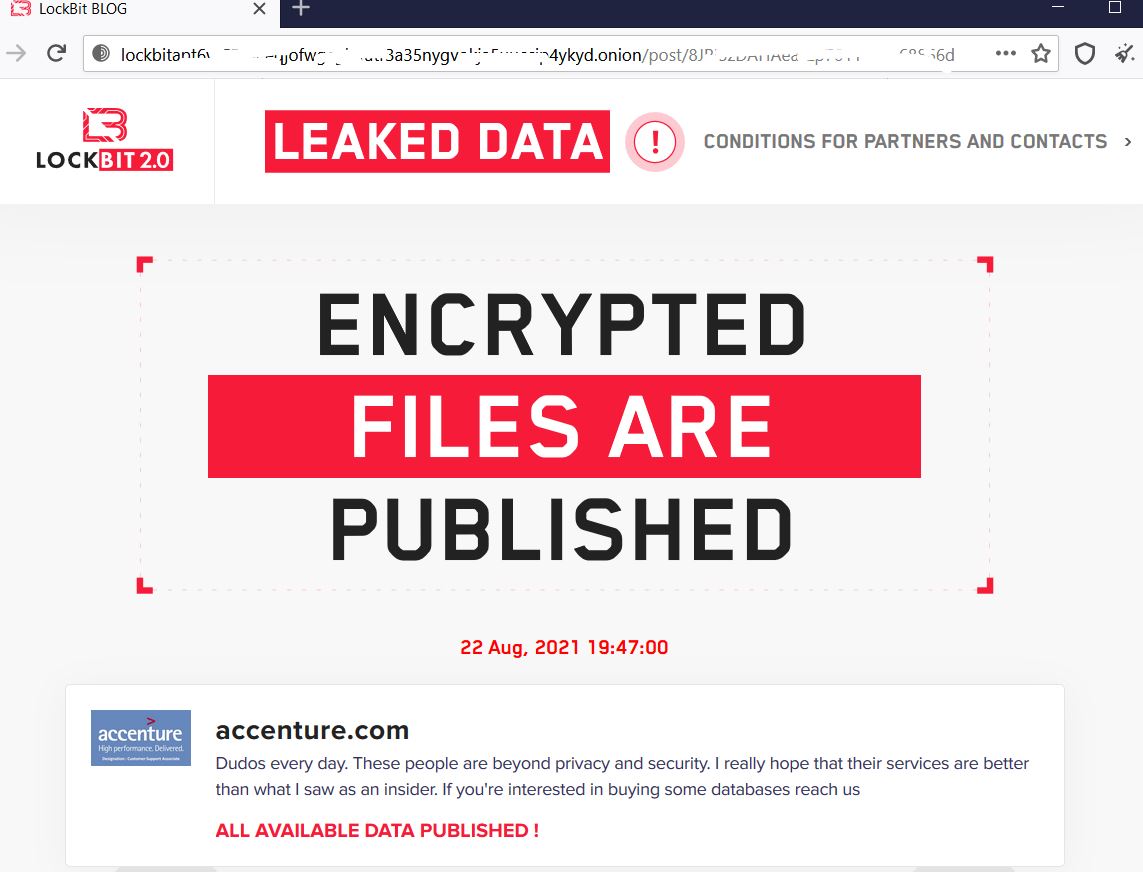
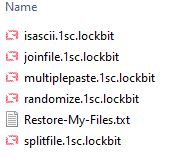
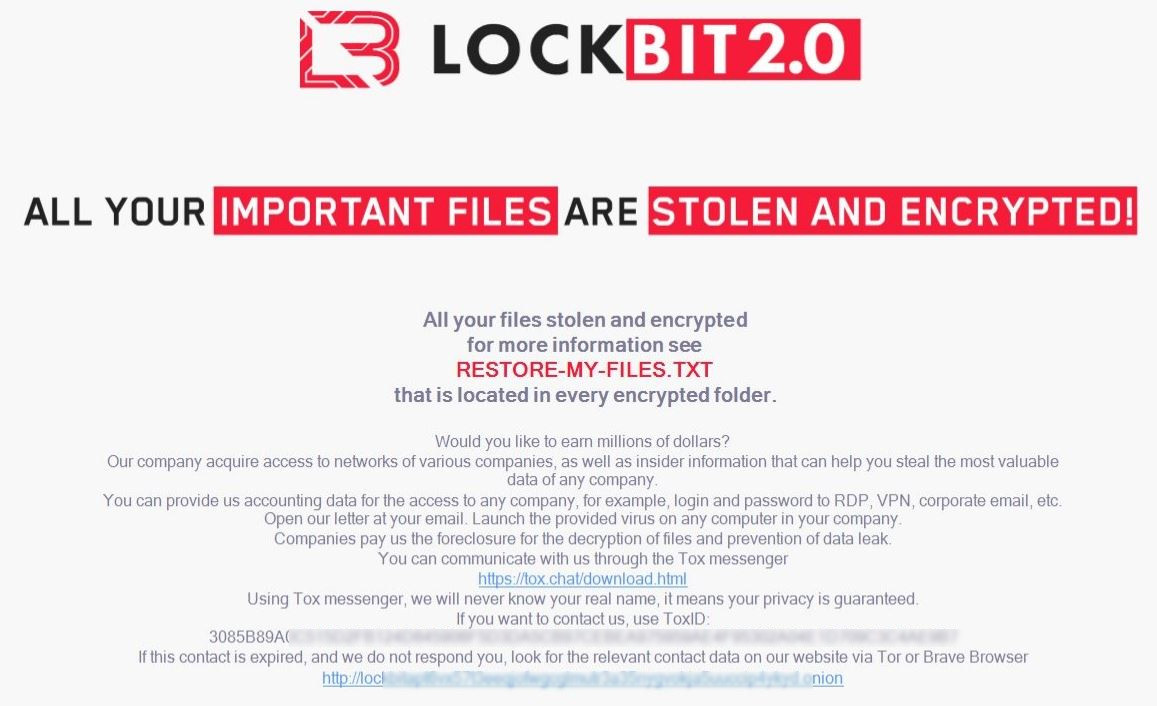
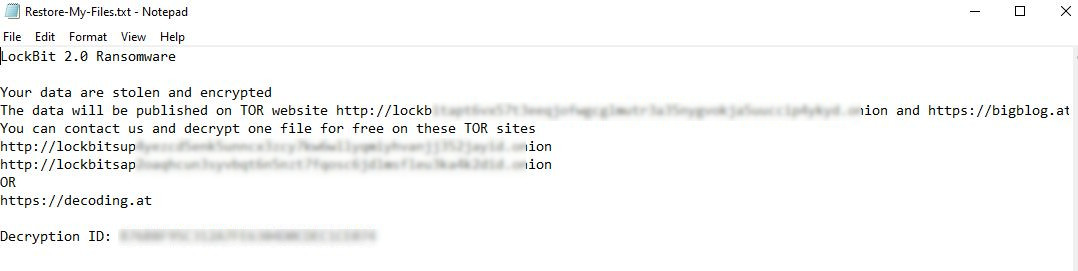
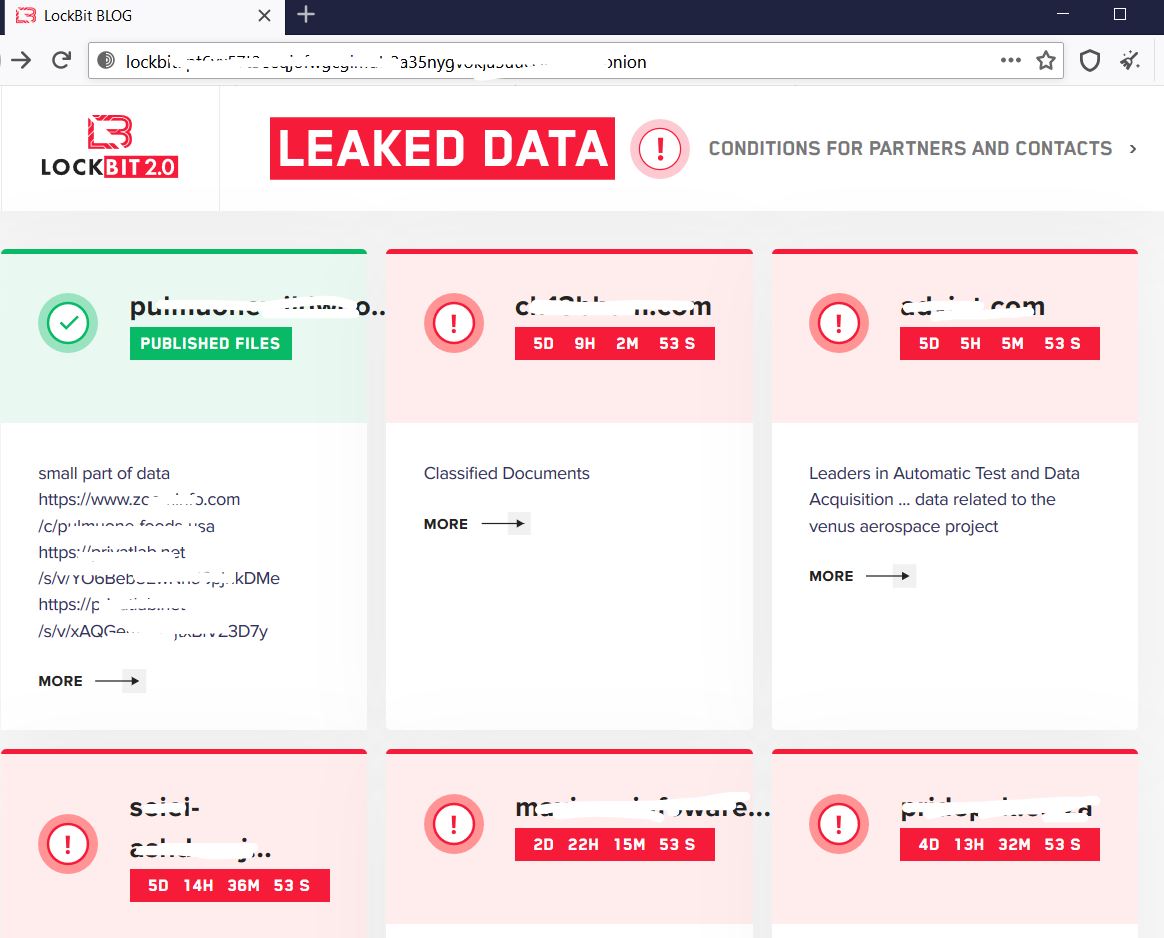
According to the mid-year update to the SonicWall 2021 Cyber Threat Report, cybercriminals have taken advantage of the increasingly distributed data landscapes. Not only have they increased the frequency of their attacks, but they’ve also expanded how they attack. As a result, ransomware attacks sharply rose to 304.6 million in 2020, up 62% over 2019. And the attacks increased to 226.3 million through May of 2021 — up 116% year-to-date over 2020.
While you can’t necessarily avoid being targeted, you can significantly decrease your odds of compromise by taking these 7 “smart” steps for better cybersecurity:
- Safeguard Your Router. By default, Routers are accessible with a simple password like “admin” — or no password — and are easily accessible to cybercriminals. Another risk flag is when users do not change the default Wi-Fi network name (or SSID), thus revealing the brand of the router. All a would-be hacker has to do is search default settings. Ditching the default settings go a long way toward increasing security.
- Stay Up to Date. Many devices offer the option to receive updates for firmware, vulnerability/bug fixes and more automatically. If this option is not enabled by default, turn it on. In cases where you must perform updates manually, make a note on your calendar to remind you to check for them regularly.
- Buy from the Best. Stick with companies known for prioritizing security in their offerings. These established brands are also more likely to push updates and patch vulnerabilities.
- Be Password Savvy. Password protection is significantly less effective when you use the same email and password combo for multiple accounts. If any of these accounts are breached, you’ve put your entire online existence at risk — and in the case of IoT devices connected to corporate networks, your company’s existence is at risk as well. With the advent of password managers, which assign a different password for each account and remember them for you, there’s no excuse to be lazy with credential hygiene.
- Leverage Two-Factor Authentication. With two-factor authentication (2FA), you’re offered the security of the traditional credential-based sign-in, plus an added layer of protection in the form of a code that is sent to a separate device and must be entered into the original app. With 2FA, even if the login credentials are compromised, the account won’t be accessible unless the attacker also has access to the secondary device.
- Divide and Conquer. Many popular routers provide a feature to create a secondary guest Wi-Fi access to your router. The guest Wi-Fi feature allows internet access without granting access to the full home network (and your computers, hard drives, etc.). Use Guest settings to isolate less-secure Wi-Fi connected smart home devices (and the malware that might infect them).
- Do I Need This? No matter how secure a smart device is, it can never match the safety and privacy of a non-internet-enabled device. Before purchasing a new smart device, ask yourself if the increased risk is worth adding convenience and features. If you’re likely to use the smart features only occasionally or not at all, opt for the non-smart device.
The network of connections created by the Internet of Things creates opportunities and challenges for individuals and businesses. SonicWall encourages everyone to be smart about smart devices and assume the responsibility of maintaining the health of their home network. Cybersecurity is everyone’s business. By being diligent, we can ensure the security of our home networks and anywhere else our connections may take us.