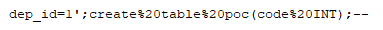Microsoft Security Bulletin Coverage for September 2021
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of September 2021. A list of issues reported, along with SonicWall coverage information, is as follows:
CVE-2021-36963 Windows Common Log File System Driver Elevation of Privilege Vulnerability
ASPY 214:Malformed-File exe.MP_199
CVE-2021-36955 Windows Common Log File System Driver Elevation of Privilege Vulnerability
ASPY 221:Malformed-File exe.MP_203
CVE-2021-36975 Win32k Elevation of Privilege Vulnerability
ASPY 219:Malformed-File exe.MP_202
CVE-2021-38633 Windows Common Log File System Driver Elevation of Privilege Vulnerability
ASPY 215:Malformed-File exe.MP_200
CVE-2021-38639 Win32k Elevation of Privilege Vulnerability
ASPY 216:Malformed-File exe.MP_201
CVE-2021-40444 Microsoft MSHTML Remote Code Execution Vulnerability
GAV 25418:CVE-2021-40444_7
GAV 25417:CVE-2021-40444_6
GAV 25414:CVE-2021-40444_5
GAV 25413:CVE-2021-40444_4
GAV 25412:CVE-2021-40444_3
GAV 25390:CVE-2021-40444_2
GAV 25389:CVE-2021-40444_1
GAV 25387:CVE-2021-40444
GAV 25379:CVE-2021-40444.X
GAV 25378:CVE-2021-40444.AB
GAV 25377:CVE-2021-40444.C
Adobe Coverage:
CVE-2021-39836 Acrobat Reader Use After Free Vulnerability
ASPY 217:Malforned-File pdf.MP.490
CVE-2021-39843Acrobat Reader Out-of-bounds Write Vulnerability
ASPY 218:Malforned-File pdf.MP.491
The following vulnerabilities do not have exploits in the wild :
CVE-2021-26434 Visual Studio Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-26435 Windows Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2021-26436 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-26437 Visual Studio Code Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-26439 Microsoft Edge for Android Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36930 Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36952 Visual Studio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-36954 Windows Bind Filter Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36956 Azure Sphere Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36959 Windows Authenticode Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-36960 Windows SMB Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36961 Windows Installer Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2021-36962 Windows Installer Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36964 Windows Event Tracing Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36965 Windows WLAN AutoConfig Service Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-36966 Windows Subsystem for Linux Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36967 Windows WLAN AutoConfig Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36968 Windows DNS Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36969 Windows Redirected Drive Buffering SubSystem Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36972 Windows SMB Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-36973 Windows Redirected Drive Buffering System Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-36974 Windows SMB Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38624 Windows Key Storage Provider Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2021-38625 Windows Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38626 Windows Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38628 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38629 Windows Ancillary Function Driver for WinSock Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-38630 Windows Event Tracing Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38632 BitLocker Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2021-38634 Microsoft Windows Update Client Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38635 Windows Redirected Drive Buffering SubSystem Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-38636 Windows Redirected Drive Buffering SubSystem Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-38637 Windows Storage Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-38638 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38641 Microsoft Edge for Android Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-38642 Microsoft Edge for iOS Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-38644 Microsoft MPEG-2 Video Extension Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38645 Open Management Infrastructure Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38646 Microsoft Office Access Connectivity Engine Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38647 Open Management Infrastructure Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38648 Open Management Infrastructure Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38649 Open Management Infrastructure Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38650 Microsoft Office Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-38651 Microsoft SharePoint Server Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-38652 Microsoft SharePoint Server Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2021-38653 Microsoft Office Visio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38654 Microsoft Office Visio Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38655 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38656 Microsoft Word Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38657 Microsoft Office Graphics Component Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2021-38658 Microsoft Office Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38659 Microsoft Office Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38660 Microsoft Office Graphics Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38661 HEVC Video Extensions Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2021-38667 Windows Print Spooler Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-38669 Microsoft Edge (Chromium-based) Tampering Vulnerability
There are no known exploits in the wild.
CVE-2021-38671 Windows Print Spooler Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-40440 Microsoft Dynamics Business Central Cross-site Scripting Vulnerability
There are no known exploits in the wild.
CVE-2021-40447 Windows Print Spooler Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2021-40448 Microsoft Accessibility Insights for Android Information Disclosure Vulnerability
There are no known exploits in the wild.