Online threats come in many forms. Depending on what’s most important to you dictates your online behavior and your diligence for practicing online safety.
For families, protecting the identities and well-being of children is a top priority. A single person may be more concerned about social engineering or account takeover. An older couple may be worried about ransomware locking sensitive or valuable information.
Like businesses, individuals and families should use a layered approach of security controls and technology management to defend against online threats. Implement the below best practices to help protect what’s most important.
Safeguarding Children Online
First and foremost, the safety of children is top of mind for any parent. While you may trust your child, far too many people lurk online waiting to compromise children or their identities.
On social media alone, almost one out of four 8- to 11-year-olds and three out of four 12- to 15-year-olds have a profile. By age 15, 83 percent of children have their own smartphone. By that same age, nearly 99 percent are online at least 21 hours each week. That’s a lot of surface area to protect. And an almost impossible task without the child being taught to continually exercise online awareness.
“Many of today’s parents didn’t grow up in the age of hyper-connectivity, so they aren’t always quite sure how to properly educate their children about cyberawareness without invading too much of their privacy,” said Dr. Chase Cunningham, a cybersecurity industry analyst and co-founder of The Cynja, a cybersecurity education and awareness organization that designs technology and graphic novels to illustrate the importance of online safety to children.
“Many of today’s parents didn’t grow up in the age of hyper-connectivity, so they aren’t always quite sure how to properly educate their children about cyberawareness without invading too much of their privacy.”
Dr. Chase Cunningham
Cybersecurity Analyst & Co-Founder of The Cynja
Cunningham, a retired U.S. Navy chief with more than 19 years’ experience in cyberforensic and cyberanalytic operations, has made protecting children online a personal priority.
“It’s important to connect with kids in ways that are comfortable, engaging and effective,” said Cunningham. “While that’s certainly a daunting task, I feel the use of different media and technology — apps, characters, stories — is the smart complement to sound parental oversite. Parents should strike the right balance that works for their family and the specific behavior of their children.”
To get started, many government, non-profit organizations and tech companies provide valuable tools and resources to help empower parents to educate their children on various online threats, including sexual predators, cyberbullying, identity theft, malware prevention and more. Explore these quick-start resources:
Parental Controls, Oversite
While third-party technology are powerful tools, parental management is still key in safeguarding children from cyber threats. Parents need access to all applications, contacts and websites their children use to communicate with large communities or unknown users — no matter how innocent or benign they appear.
Unfortunately, predators lurk everywhere kids spend time, so a certain level of strict oversite is necessary until children gain better awareness. For example, popular console games like Fortnite are being infiltrated by adults posing as children to maliciously connect with minors. The UK Child Exploitation and Online Protection (CEOP) organization even issued a warning to parents about this type of threat.
The concern spans all apps and sites. Cases involving apps like Snapchat, Instagram and WhatsApp are rampant. While the list evolves by the week, parents should routinely monitor the apps — particularly what’s new or trending — kids use to communicate online. This includes:
| Snapchat |
Facebook |
Twitch |
| Instagram |
Twitter |
Mixer |
| Yubo |
Telegram |
Musical.ly |
| Bumble |
WhatsApp |
TikTok |
| YouTube |
Sarahah |
Reddit |
| Kik |
Whisper |
Tumblr |
While policy-makers and app developers alike are doing more to control and protect underage users, data and privacy, parents should still be the primary line of defense for protecting their kids. Use this general guidance from the FBI to help safeguard children online.
| Monitor your children’s use of the internet (and connected mobile apps) |
Remind kids to only add people they know in real life |
| Tell your kids why it’s so important not to disclose personal information online |
Encourage kids to choose appropriate usernames |
| Check your kids’ profiles and what they post online |
Talk to your kids about creating strong passwords |
| Explain to your kids that once images are posted online they lose control of them and can never get them back |
Ask your kids about the people they are communicating with online |
| Restrict your kids from posting photos or personally identifying information (PII) without first gaining your consent |
Make it a rule with your kids that they can never give out personal information or meet anyone in person without your prior knowledge and consent |
| Instruct your kids to use privacy settings to restrict access to profiles |
Educate yourself on the websites, software and apps that your child uses; start with the list above |
‘Never Stop Patching’
Inside the home, it’s best to assign a primary manager of laptops, mobile phones and IoT devices (e.g., streaming boxes, consoles, security cameras, appliances) to ensure they are routinely updated and patched. Memorize it like a movie quote: “Never stop patching.”
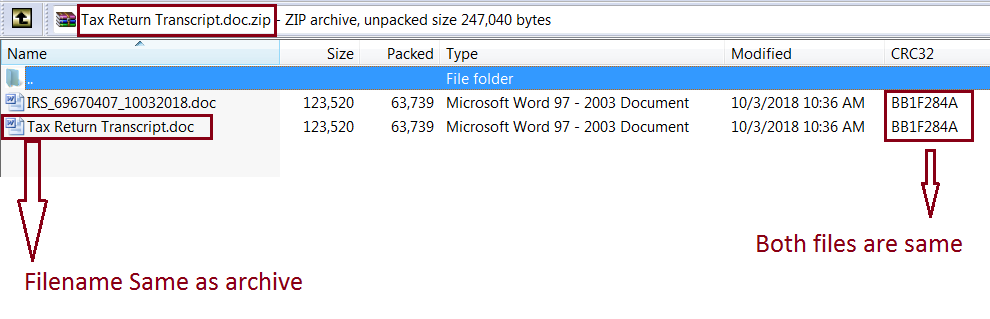
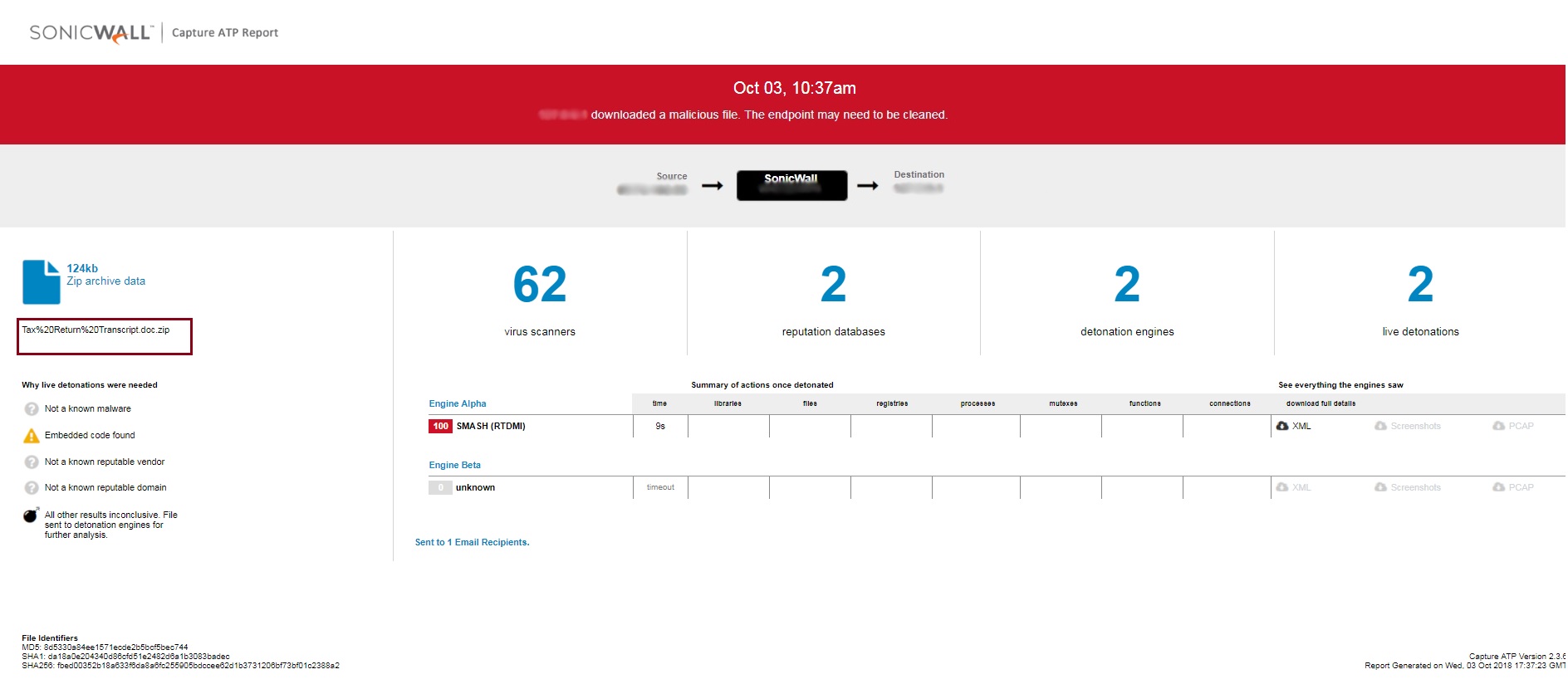
Consistent patching — particularly on computers and mobile devices — is one of the most proven methods of mitigating cyberattacks. It’s for this reason that zero-day threats (i.e., not previously seen before) are the most dangerous to individuals and organizations alike. Real-time solutions, such as the multi-engine Capture Advanced Threat Protection sandbox service can identify and block known and unknown cyberattacks.
While patching hardware like routers, web cams and wireless access points isn’t always so straightforward, manufacturers and developers like Google, Microsoft and Apple have made patching a fairly common, easy-to-do practice. It’s so common, in fact, that Microsoft’s monthly patch update is unofficially named “Patch Tuesday.” The pseudo tradition has been in practice since 2003.
In many cases, operating systems have an “automatic update” option to further simplify the process. It is particularly important to protect your consumer devices and sensitive data from malware and ransomware.
Globally, the SonicWall Capture Threat Network, which includes more than 1 million sensors across the world, recorded 7.8 billion malware attacks (70 percent increase from 2017) and 238.9 million ransomware attacks (108 percent increase) year to date in 2018.
Proactive Password Management
If patching is the No. 1 best practice, proper password creation and management is No. 1B. Two-factor authentication has helped offset the use of weak passwords, but far too many people still reuse passwords across sites, services and applications. Even if they properly used strong passwords, continued re-use leaves users vulnerable to attack.
Many free and paid password management solutions include options specifically for families. The top include Dashlane, 1Password and LastPass. While they each offer basic encrypted password creation and management, many feature tools for safely sharing passwords between authorized family members.
“Cybercriminals take advantage of people with poor password health to gain access to sensitive personal and payment information,” said Dashlane’s Eitan Katz in ‘Your Password Health Is the Key to Protecting Your Digital Identity.’ “The best way to prevent these online attacks and ensure that only you have access to your private data is to create complex, unique passwords for each account, and to change passwords that are compromised in a breach or hack immediately.”
More proactive password management services will analyze password health, suggest passwords that should be replaced, and even alert users to breached sites where they may hold an account.
Be Suspicious of Unknown Email
Even though learning how to stop phishing attacks is getting easier, email remains the No. 1 threat vector for cybercriminals. It’s the easiest and most successful approach for cybercriminals to deliver their payload to unsuspecting users or organizations.
Families may not often invest in business-grade secure email solutions, but they should practice consistent awareness about phishing email threats and email hygiene. Is your family aware of the latest email attacks? Take the SonicWall Phishing IQ Test to find out.
Be Smarter on Wi-Fi
There’s nothing more comforting than connecting to Wi-Fi when you’re on the go. It’s an addicting and predictable behavior that cybercriminals feast upon. When remote (e.g., airport, mall, coffee shop), always think three times before connecting to unknown wireless networks. Follow these best practices for ensuring safe connectivity when mobile:
| Turn off “auto connect” features in your phone’s settings |
| Avoid free or unsecured Wi-Fi signals altogether |
| Look for spoofed Wi-Fi names similar to the location you’re visiting |
| If you must connect, use a virtual private network (VPN) |
Most of this guidance has been focused on user behavior, but deploying wireless security at home — even if it’s right out of the box from your ISP — is also recommended. Users comfortable with advanced controls can also take additional steps:
| Change SSID (Wi-Fi) name and default password |
| Create separate secure wireless network for friends and guests |
| Hide network(s) altogether |
| Limit the power and range of the wireless signal |
| Monitor connected devices through router’s management dashboard; revoke access to unknown or suspicious devices |
| Limit the types of devices connected to your network; does your dog’s water dish really need access to the internet? |
About Cybersecurity Awareness Month
The 15th annual National Cybersecurity Awareness Month (NCSAM) highlights user awareness among consumers, students/academia and business. NCSAM 2018 addresses specific challenges and identifies opportunities for behavioral change. It aims to remind everyone that protecting the internet is “Our Shared Responsibility.”
In addition, NCSAM 2018 will shine a spotlight on the critical need to build a strong, cyber secure workforce to help ensure families, communities, businesses and the country’s infrastructure are better protected through four key themes:
- Oct 1-5: Make Your Home a Haven for Online Safety
- Oct 8-12: Millions of Rewarding Jobs: Educating for a Career in Cybersecurity
- Oct 15-19: It’s Everyone’s Job to Ensure Online Safety at Work
- Oct 22-26: Safeguarding the Nation’s Critical Infrastructure
Learn more at StaySafeOnline.org.



 For what we believe is that reason, SonicWall is pleased to have been recognized as a
For what we believe is that reason, SonicWall is pleased to have been recognized as a 



