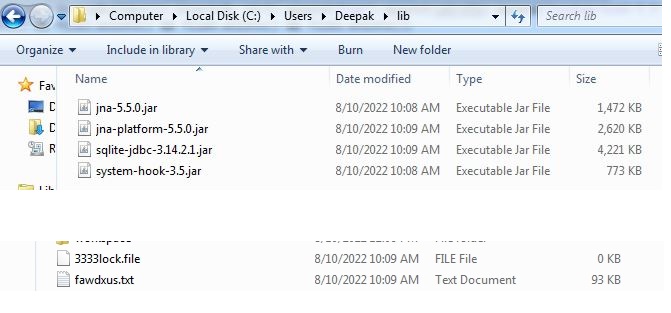
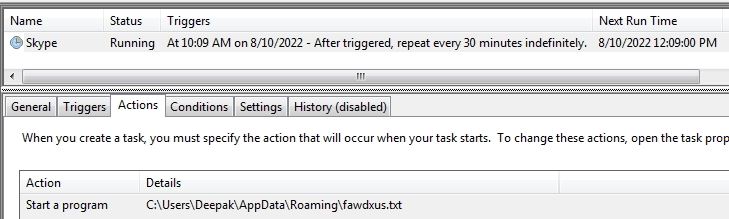
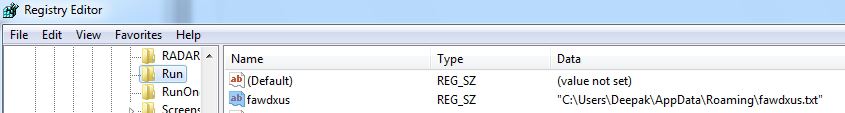
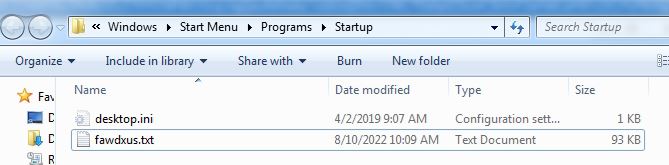
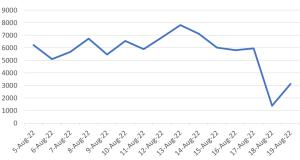
Security Platform Vendors vs. Best-of-Breed Approach to Security Architecture
In the debate over adopting an all-in-one cybersecurity platform versus assembling best-of-breed solutions, there’s only one answer: It depends. The questions are: How many tools can you afford, and is the software in your stack designed for security? Do you have skilled resources to manage? Does this approach make sense now that we have a greater number of users outside the organization, and most of the services we use are in the cloud?
Traditionally, a best-of-breed approach means buying multiple security programs, each a separate tool that is the best at the individual problem it solves, given your particular use case. For example, you might use SonicWall for next-gen firewall, but another vendor for next-gen endpoint, yet another vendor for log correlation, etc.
Business challenges
Hybrid and remote work have changed the IT landscape forever, as users are working from anywhere and at any time. With as many as 70% of employees embracing remote work today, protecting endpoints has never been a more critical component of securing your perimeter.
Alongside this shift, the COVID-19 pandemic has accelerated digital transformation, resulting in more customers moving to cloud and SaaS applications.
It’s past time for organizations to take another look at their security architecture.
Advantages and Disadvantages of Best-of-Breed Security Technology Vendors
First, let’s look at the advantages:
- Security products are more specifically focused, leading to better fit and functionality.
- Provides best-in-class capabilities for security operations to manage and monitor security risks.
- Security technologies are easier to switch out for something else if necessary, making you more agile in responding to business needs.
- Less risk of vendor lock-in, as you can replace any security product in your architecture with that of another vendor.
- Less stakeholders involved in the decision and management of a point solution.
But there are also some significant drawbacks to the best-of-breed approach:
- Implementing best-of-breed security technology at every layer becomes cumbersome. When integrating multiple vendor security technologies in the detection and response layer, interoperability becomes challenging.
- Today’s security architecture is shifting from a preventative approach to a detection and response approach with “assume compromise” design. Adding best-of-breed security technology at every problem increases cost and makes management challenging.
- The security skill shortage is another big challenge in the cybersecurity industry, and this is exacerbated by a best-of-breed approach. This patchwork of products increases complexity and increases the trained resources required to manage security operations.
- If best-of-breed solutions aren’t well managed, the cost of ownership can be significant — especially for SMBs. Not to mention, managing security vendors and vendor relationships may require a substantial time investment.
Advantages and Disadvantages of Security Platform Vendors
Here are some advantages of the security platform approach:
- One of the biggest advantages of security platform vendors is intermesh operation: endpoint, network, and cloud security technologies work together to address both known and unknown threats.
- Enabling artificial intelligence and automation can be easier when there’s just a single interface to manage, and they work in security mesh.
- With an assume-compromise approach to security architecture, security platform vendors lower your TCO by providing EDR/XDR capabilities into their platform. Customers can use these vendor tools to detect and respond to threats and implement artificial intelligence to detect advanced threats.
- Security platform vendors are offering disruptive technologies such as SASE, CASB and XDR, which are cloud-native security solutions that work together to address risk from advanced threats.
But there are also disadvantages:
- Vendor lock-in can become a concern.
- Security functionality of certain features can be compromised for ease of use when you compare that feature to a specialized security product, e.g., dedicated XDR solutions, SIEM solutions or SOAR solutions.
- Security platform vendors might not offer all the security solutions that an organization is looking for. (You might still have to use a hybrid best-of-breed/security platform vendor approach to mitigate risk.)
- For security platform vendor selection, broader stakeholder and management involvement may be required.
In the past, you might have heard more CIOs tell you that vendor lock-in was a concern — but these days, you hear this much less frequently.
That’s because the advantages of vendor security platforms are overriding the negatives. This represents a tremendous change in the industry from three or four years ago: the hybrid movement has significantly narrowed the gap between these two approaches.
Security technology convergence is accelerating across multiple disciplines. Security vendor consolidation is occurring on the heels of a large architectural shift, which in turn is due to the hybrid shift among today’s workforce.
The consolidated security platform approach is the future, driven by the need to reduce complexity, leverage commonalities and minimize management overhead. Technology consolidation is not limited to one technology area or even to a closely related set of technologies; these consolidations are happening in parallel across many security areas.
There may still be some customers — such as those with full-blown Security Operation Centers and Incident Response teams, who still have many applications hosted in physical data centers — for whom a best-of-breed approach may be the way to go. (However, even in this case, security assessment and ROI need to be considered to lower the TCO.)
But for many customers, particularly those with distributed enterprises covering multiple branches and those with many cloud-native applications, a single-platform vendor that offers SASE, CASB, NGFW and endpoint protection solutions makes much more sense.
Over the past four years, SonicWall has introduced countless new security products and innovations. Our product portfolio now includes offerings that scale to businesses of all sizes and provide industry-leading performance at a lower TCO.
SonicWall’s solutions are well suited to either a best-of-breed approach or a single-vendor strategy. For more details on SonicWall’s security platform, please visit our website: https://www.sonicwall.com/capture-cloud-platform/.