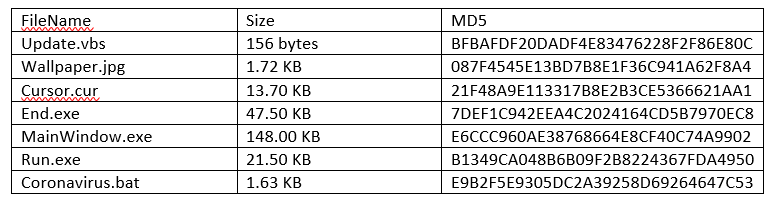
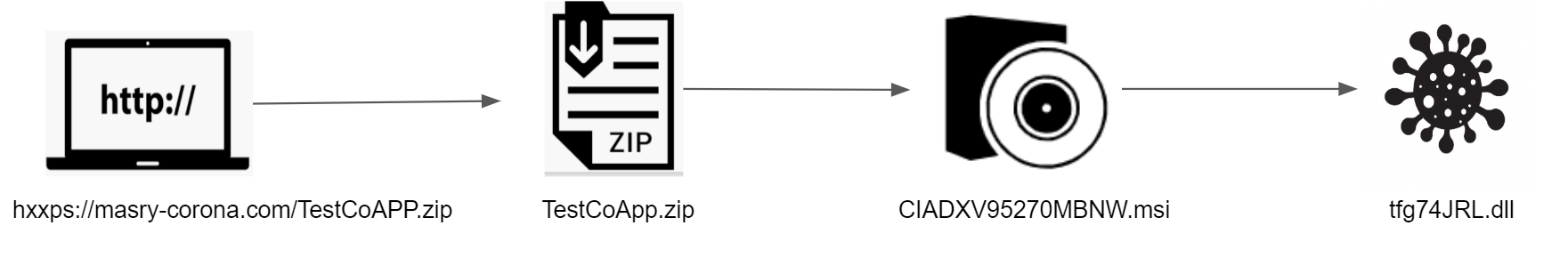
It’s the start of a perfect day: You wake up, have your morning coffee followed by a delicious breakfast, and enjoy a traffic-free drive to work. Then you fire up your system to begin the frustrating and time-consuming process of evaluating threat detections in your organization’s different SaaS environments.
Between just Office 365 email, OneDrive, SharePoint Online, Box and Dropbox use, there are at least three different environments to review and verify protection against the latest breach of the day.
Staying on top of the constantly evolving threat landscape, coupled with the responsibility of securing and managing different SaaS applications across the organization, is a difficult and painstaking task. Using disparate solutions with siloed protections brings additional complexity and high potential for misconfigured policies, which increase your risk. To ensure protection against the latest SaaS threats, whether they be email or file storage, technology must keep up with changing trends.
SonicWall Cloud App Security (CAS) ensures this by introducing new features and enhancements throughout the year. Our initial release brought SonicWall protection into your SaaS environment, with advanced threat protection that spans across SaaS email and SaaS file storage in a single solution. Our February 2020 release, also known as CAS 2.6.0, expands protection capabilities and efficiencies even further.
Here are some of the new features and enhancements added to CAS:
Stop sensitive data leaks in outbound email
Data loss/leak prevention (DLP) is often an overwhelming concept for many organizations. Companies in every industry sector around the globe have seen sensitive data lost in almost every conceivable way. As a primary external communication method, email is a common source of exposure.
Preventing sensitive data such as personally identifiable information (PII), patient medical data, credit card information, or financial data from being leaked outside the organization requires constant vigilance. A wide range of high-profile data loss incidents has cost organizations millions of dollars in direct and indirect costs and has resulted in tremendous damage to brands and reputations. Whether the data was leaked accidentally, leaked intentionally or stolen, the business ramifications are the same.
Preventing sensitive data from being sent externally via email should be a critical component of any email security policy. The Office 365 email and Gmail DLP Protect (Inline) policies intercept and block outbound emails containing sensitive data before they can leave the organization. Using regulatory compliance-based templates, preventing data loss through email requires just a few easy clicks.
Identify credential compromise
Deviations from a user’s “normal” pattern of behavior, referred to as anomalies, can be indicative of credential compromise or an account takeover attack. Using AI for end-user behavior analysis (EUBA), CAS identifies and alerts on these deviations across your SaaS landscape. Just as AI evolves, feature capabilities do too.
Expanded alerting
When deviations in behavior are detected, admins need to know NOW—not the next morning when (or if) they look at a dashboard. We’ve expanded alerting for anomaly detections beyond the dashboard by offering CAS admins the ability to receive email alerts. Simply checking the “Email anomaly alerts to admins” option located in Configuration > Security App Store > Anomaly Detection > Configure is all it takes to get alerts sent right to your mailbox.
Exception management
In some situations, the activity flagged as anomalous is legitimate. Employees have emergencies, job roles change, or unusual patterns of business travel may occur. Often, the IT and Security teams are the last to know. If they find out at all, it’s usually through an alert that gets triggered based on a new user behavior.
Anomaly Exceptions offer additional flexibility by providing the ability to whitelist specific activity. While available whitelisting options are specific to the type of detection (e.g., geo suspicious, or other), the ability to whitelist for a defined time period or permanently is available for all detected activity types.
Increase efficiency with enhanced workflows and refined visibility
Managing tasks and exceptions can be part of everyday life for security admins — so efficient, streamlined management with state-of-the-art, cloud-native protection spanning your SaaS email and file storage apps is critical for organizations of any size. Several key workflows have been upgraded to increase efficiencies and simplify management even more.
Create anti-phishing whitelist or blacklist rules from within a security event
The process of creating whitelist and blacklist rules from scratch can be complex and cumbersome. We’ve made the process easier by including the ability to add rules from within a specific event. When you select one of the options, the fields are auto-populated using the event details. From there, you can modify or deselect fields as needed.
Use Mail Explorer to easily identify email messages based on specific criteria
The life of the security admin is rarely dull. When you want to find a specific email(s) sent or received by a user(s), you need to be able to do it quickly and simply. Mail Explorer brings the ability to easily identify and action specific emails with a few simple clicks. Using the tool provides the flexibility to not only quickly locate emails, but also to quarantine or blacklist.
Use dashboard customization for a refined view
Each organization, and each admin, is different. Adding the ability to save dashboard customizations as a user preference allows each admin a personalized view. Whether it’s updating a Security Event widget to display data from a custom query or isolating specific event types, the additional flexibility allows you to define what is important.
Increase compliance with read-only permissions
As administrators, we face the constant dilemma of determining who needs access to manage a product vs. who needs only data/reporting access. MySonicWall Workspace streamlines managing access permissions for SonicWall products, including CAS. Providing the ability to restrict permissions to a “read-only” view allows resources access to product data without the ability to modify the security controls or policies.