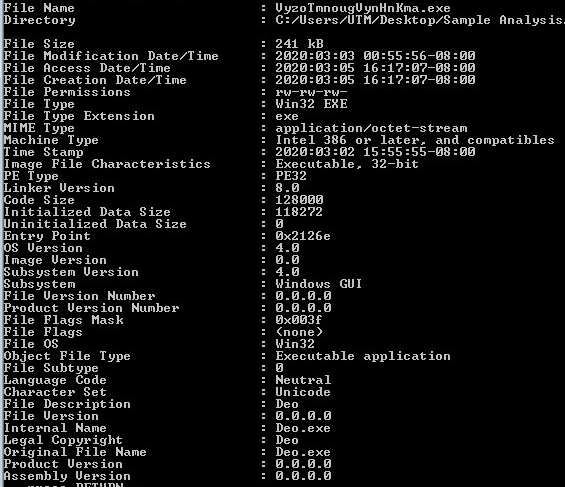
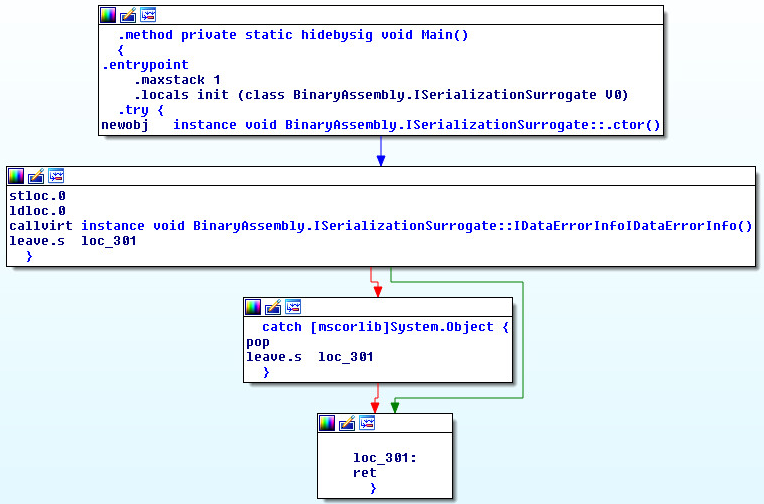
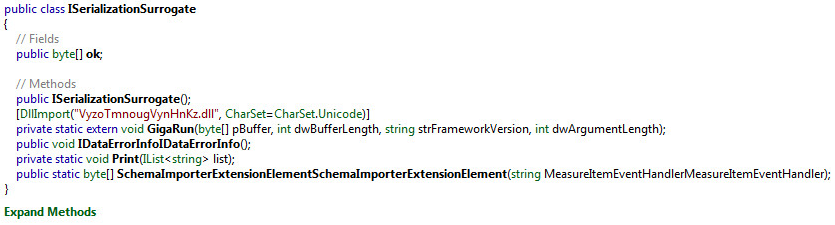
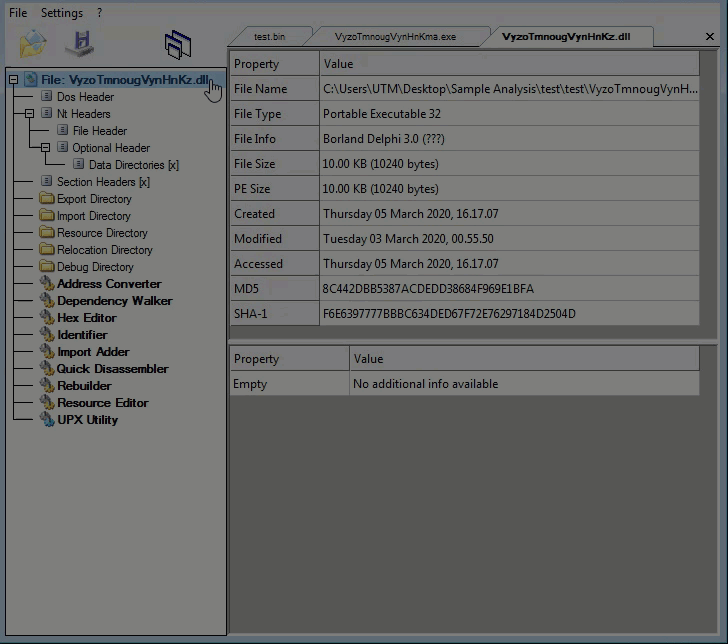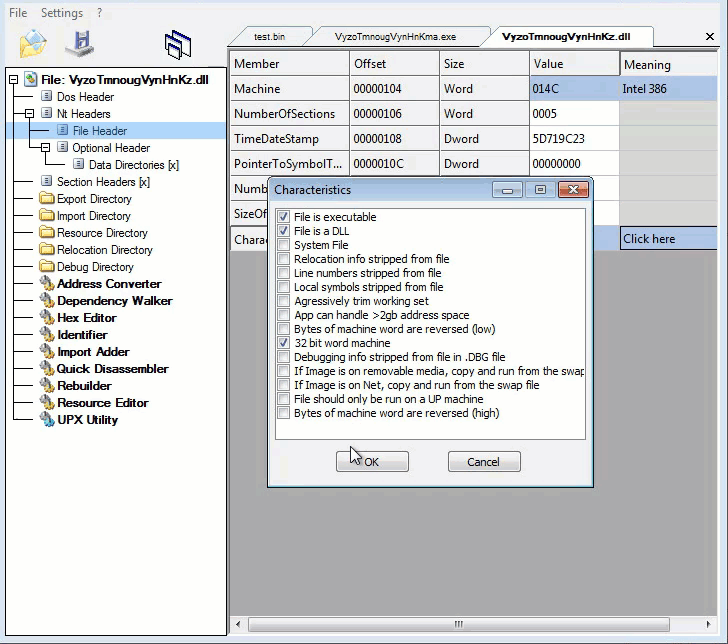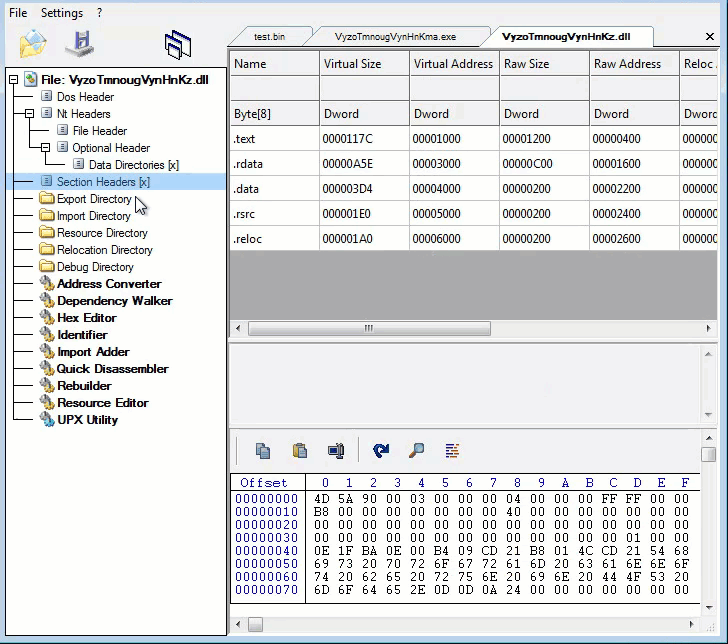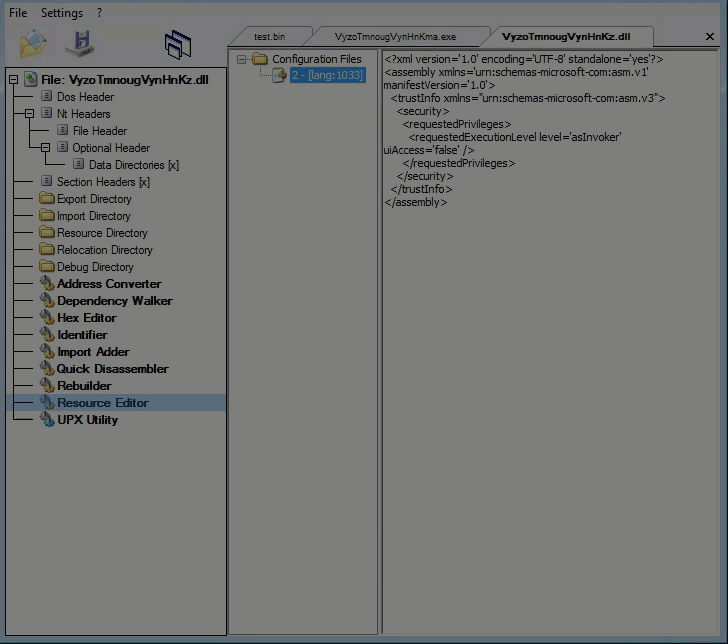
Cyber Security News & Trends – 03-13-20
This week, vote for SonicWall in this year’s CRN Channel Madness!
SonicWall Spotlight
2020 CRN Channel Madness – CRN
- This year’s CRN Channel Madness has SonicWall’s HoJin Kim up for best channel leader in the security category. Vote early, vote often, vote today!
8 Million UK Shopping Records Exposed – Information Security Buzz
- SonicWall’s Terry Greer-King is reached for comment after researchers uncovered a leak of personal data from third-party apps used by Amazon UK. Greer-King explains the value of personal information on the Dark Web and the importance of a good cybersecurity plan.
7 Factors to Consider When Evaluating Endpoint Protection Solutions – MSSPAlert
- SonicWall’s Vishnu Chandra Pandey lists 7 basic checks to help enhance endpoint compliance and better protect from cyberattacks.
Cybersecurity News
State-Sponsored Hackers are now Using Coronavirus Lures to Infect their Targets – ZDNet
- Government-backed hacking groups worldwide have been detected using coronavirus-based phishing lures as part of their efforts to spread malware. ZDNet investigates campaigns that have taken place over the past month.
Election Commission Hires Cybersecurity Expert to Help States With 2020 Infrastructure – CyberScoop
- The Election Assistance Commission has hired Joshua Franklin, who spent six years as an engineer at the National Institute of Standards and Technoligy, to act as top cybersecurity expert helping oversee the technology that will be involved in the 2020 US Presidential Election.
Commission to Propose Sweeping National Cybersecurity Strategy – Axios
- An upcoming report on cybersecurity will, over the course of 75 recommendations, propose “a very ambitious reorganizing of the federal government, perhaps the most ambitious since the 9/11 Commission,” to combat cybersecurity threats.
Australia Sues Facebook over Cambridge Analytica Data Breach – The Hill
- The Australian information commissioner has sued Facebook for sharing the personal data of more than 300,000 Australians as part of the Cambridge Analytica controversy. The Australian government says that it is actively seeking an order that Facebook pay a monetary penalty.
European Power Grid Organization says its IT Network was Hacked – CyberScoop
- The European Network of Transmission System Operators for Electricity (ENTSO-E) this week confirmed that its IT network was successfully compromised by hackers. It stresses that the network was not connected to any critical control systems that would have allowed the hackers access to any power infrastructure.
Hackers Get $1.6 Million for Card Data from Breached Online Shops – Bleeping Computer
- A known MageCart hacking group has collected $1.6 million from selling more than 239,000 payment card records on the dark web.
In Case You Missed It
- Strength in Numbers: SonicWall Named New Member of Cyber Threat Alliance – Lindsey Lockhart
- SonicWall Wins Best UTM Security Solution at SC Awards 2020 – Geoff Blaine
- Catapult the Wi-Fi User Experience: Fast, Secure & Easy to Manage – Srudi Dineshan
- SonicWall Firewall Certified via NetSecOPEN Laboratory Testing, Earns Perfect Security Effectiveness Score Against Private CVE Attacks – Ken Dang
- SonicWall Secures 3 Spots on Annual CRN Channel Chief List – Lindsey Lockhart
- 7 Factors to Consider When Evaluating Endpoint Protection Solutions – Vishnu Chandra Pandey