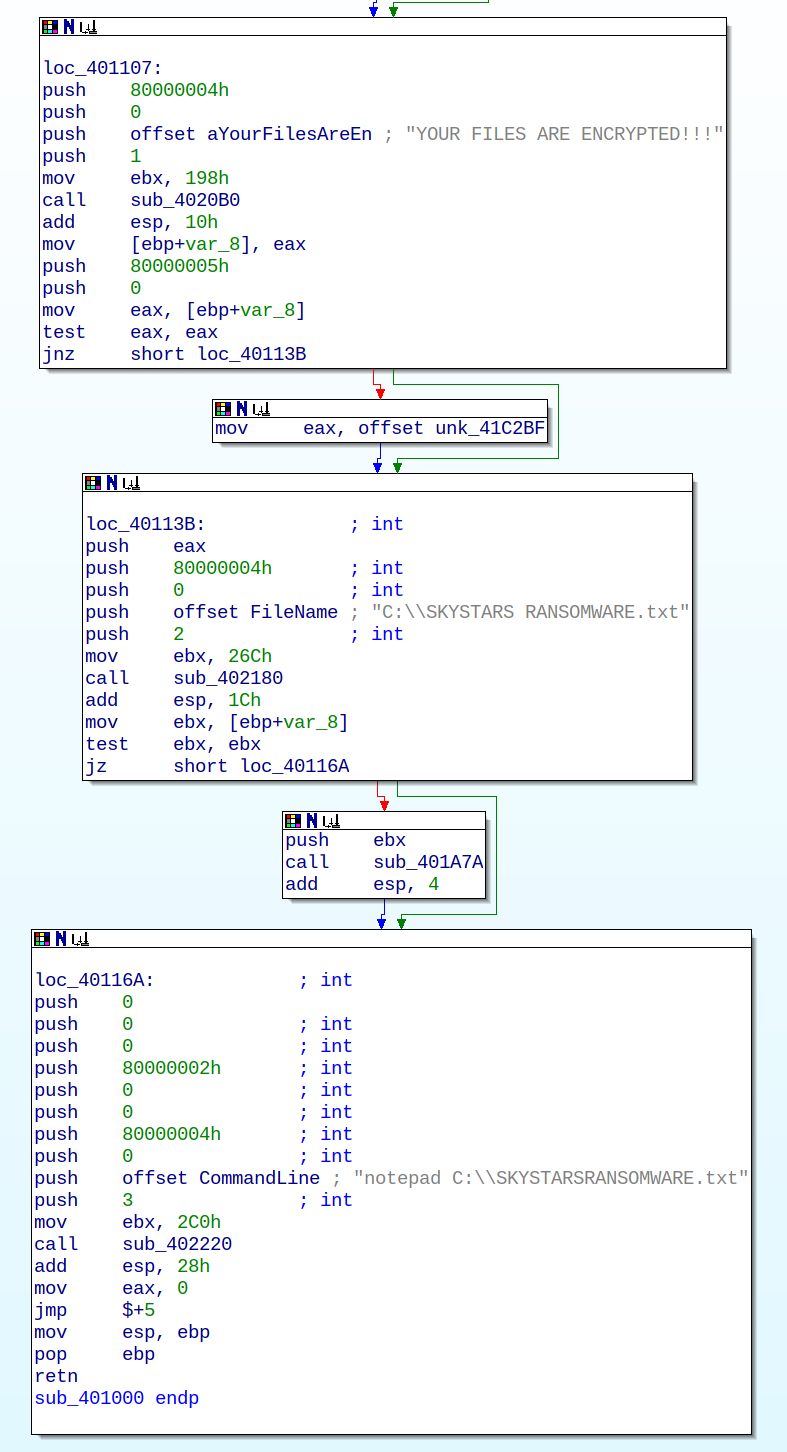
Inside the Capital One Data Breach: What Went Wrong
In one of the biggest data breaches publicly disclosed, Capital One revealed that a hacker gained access to personal information from 106 million credit card applicants and customers in the United States and Canada.
Capital One’s breach disclosure comes after Equifax recently agreed to pay up to $700 million to federal and state agencies to settle litigation around a 2017 data breach that affected 147 million people.
“While I am grateful that the perpetrator has been caught, I am deeply sorry for what has happened,” said Richard D. Fairbank, Chairman and CEO in a public statement. “I sincerely apologize for the understandable worry this incident must be causing those affected and I am committed to making it right.”
According to Capital One, beyond the credit card application data, the individual also obtained portions of credit card customer data, including:
- Customer status data (e.g., credit scores, credit limits, balances, payment history, contact information)
- Fragments of transaction data from a total of 23 days during 2016, 2017 and 2018
No bank account numbers or Social Security numbers were compromised, other than:
- About 140,000 Social Security numbers of credit card customers
- About 80,000 linked bank account numbers of our secured credit card customers
The intrusion allegedly occurred through a “misconfigured web application firewall that enabled access to the data.” Capital One immediately fixed the configuration vulnerability that the individual exploited and promptly began working with federal law enforcement.
“Based on our analysis to date, we believe it is unlikely that the information was used for fraud or disseminated by this individual,” said a statement from Capital One.
Capital One expects to spend between $100 million and $150 million on customer notifications, credit monitoring, technology costs and legal support associated with the breach in 2019 alone, according to CRN.
How can you prevent such a breach using SonicWall WAF?
The SonicWall web application firewall supports OWASP Top 10 and PCI DSS compliance, providing protection against malicious injection and cross-site scripting attacks, credit card and Social Security number theft, cookie tampering and cross-site request forgery.
SonicWall WAF offers Information Disclosure Protection, a data loss prevention technique that ensures that sensitive information, such as credit card numbers and Social Security numbers, are not leaked. SonicWall WAF also provides strong authentication mechanisms (i.e., two-factor or multifactor authentication) and facilitates seamless configuration/deployment through admin friendly management API.
To ensure your SonicWall is properly configured, please refer to the our in-depth administration guide and the SonicWall WAF settings resource.