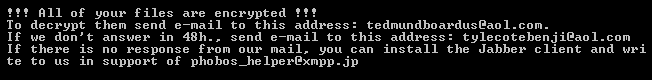
NanoCore RAT delivered through phishing campaigns
SonicWall Capture Labs Threat Research team has observed a huge phishing campaign that spreads NanoCore Remote Access Trojan (RAT) through malicious attachments.
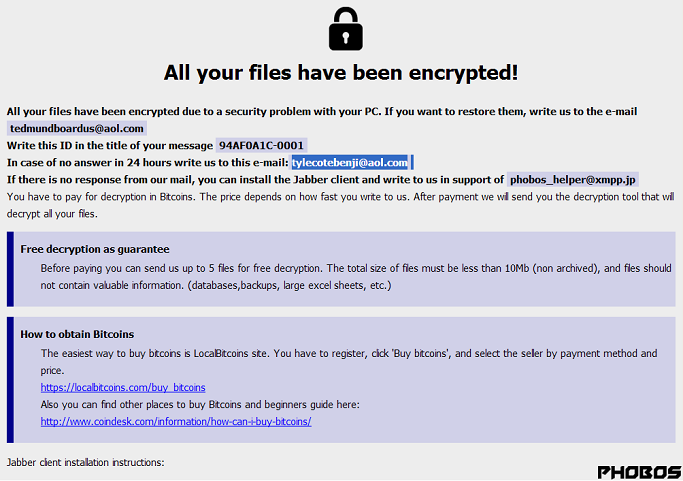
As with many other attacks, this campaign starts with a phishing email that distributes the malicious ISO malware as an email attachment. ISO file is named to look like an image file and the contents of the email messages vary but spoofed to look like it’s coming from one of its vendors and encourages user to open the attached file.

ISO:
An ISO file (referred as an ISO image) is an archive file that contains all the information that would be written to an optical disc. ISO files are commonly used to create a backup of a CD or DVD. They’re also very useful for distributing large programs over the internet as an ISO image can handily contain all of a program’s files in a single file.
ISO file is used in this attack as many email gateway scanners don’t scan ISO file attachments properly. This may be due to the fact that ISO’s tend to be larger in size. In the past, third party software utility is required to open an ISO file, but modern versions of Windows (Win 8 & later) feature a native ISO mounting tool. Opening an ISO is now as simple as double-clicking the file. This increases the chances of the target opening the file. All the ISO files observed in this campaign are of size 1-2MB.
EXE:
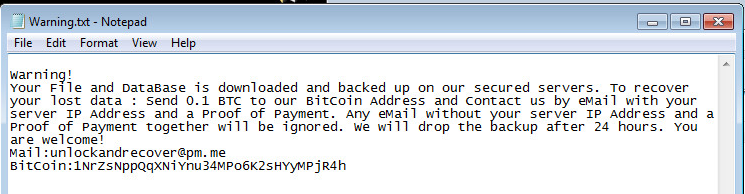
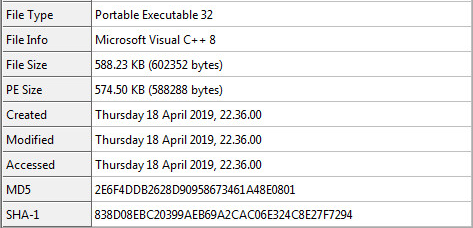
The executable file “SKMBT#2019-04.exe” embedded within ISO, is shown below.

AutoIt:
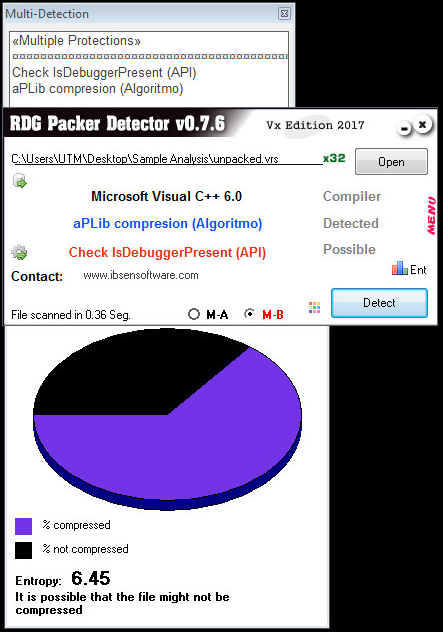
The malicious payload presented as a single exe file, is actually an AutoIt Interpreter with the AutoIt compiled script embedded into it as a resource. Analyzing the file using PEStudio tells that it’s an AutoIt Compiled script.

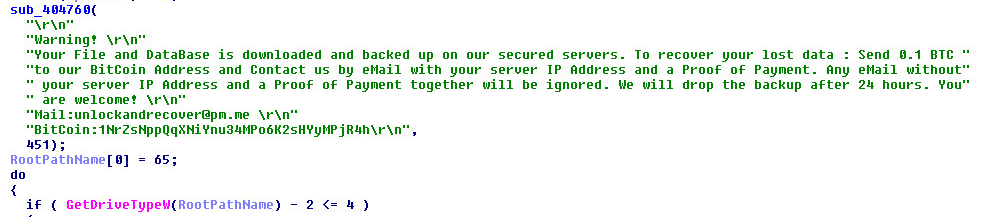
Using Exe2Aut tool, we successfully retrieved the AutoIt source code from the compiled script but it is heavily obfuscated. Find below the snippet from the AutoIt source code.

NanoCore RAT:
String “NanoCore.ClientPluginHost” that belong to NanoCore RAT is found in the memory.
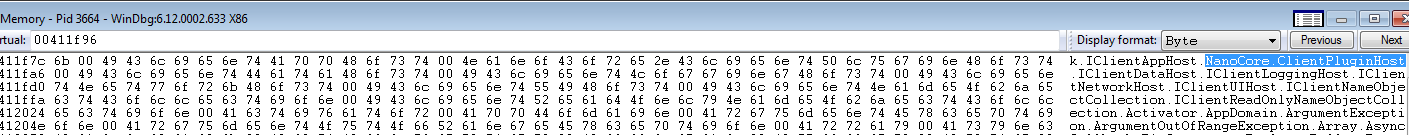
NanoCore is one of the most sophisticated RAT (Remote Access Trojan ) out there. This malicious program uses NanoCore’s plugins to take control of victims machine.
Behavior:
Upon execution, it exhibits the following behavior.
- Anti-debugging:
It exits with an error dialogue if debugger is present.
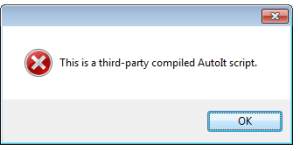
- DNS Lookup
It performs the DNS lookup for “billionscome1.duckdns.org” and establishes connection with the server 191.101.150.90. Most of the similar malicious programs used in the campaign perform DNS queries to *.duckdns.org.

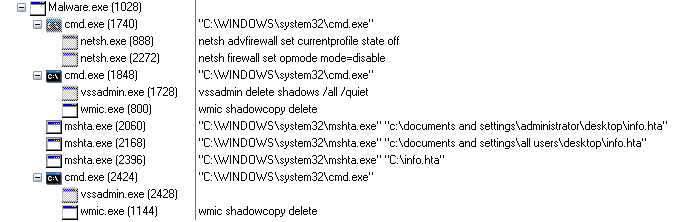
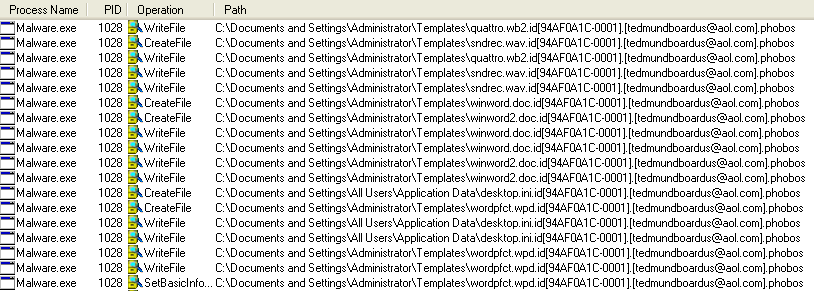
- Files Written:
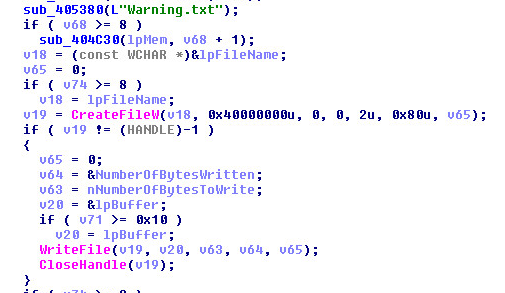
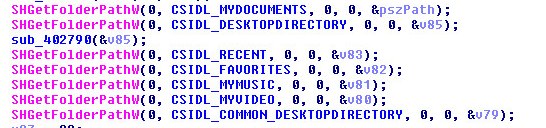
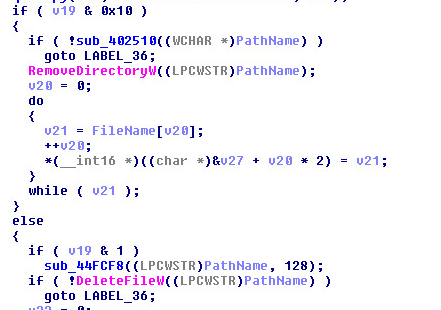
It creates a copy of itself and drops it into the AppData directory along with a malicious VBS script.
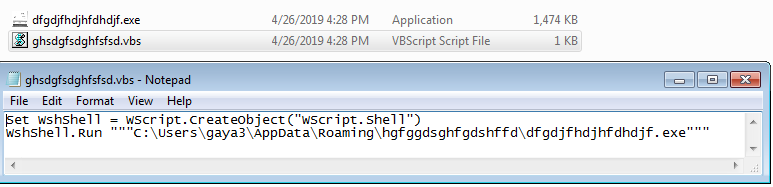
Later, it creates an entry in the Windows startup directory for persistence. Files under the startup directory execute automatically after every boot up. “ghsd
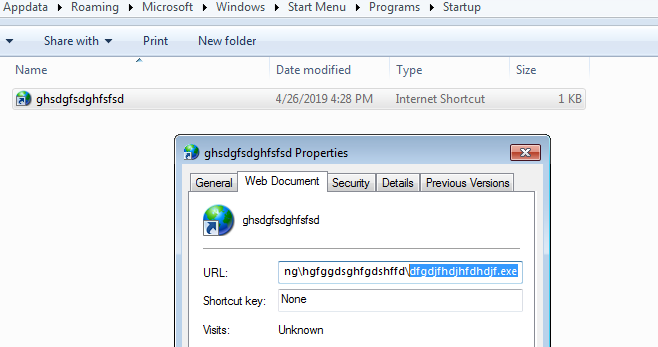
- Schedule Tasks:
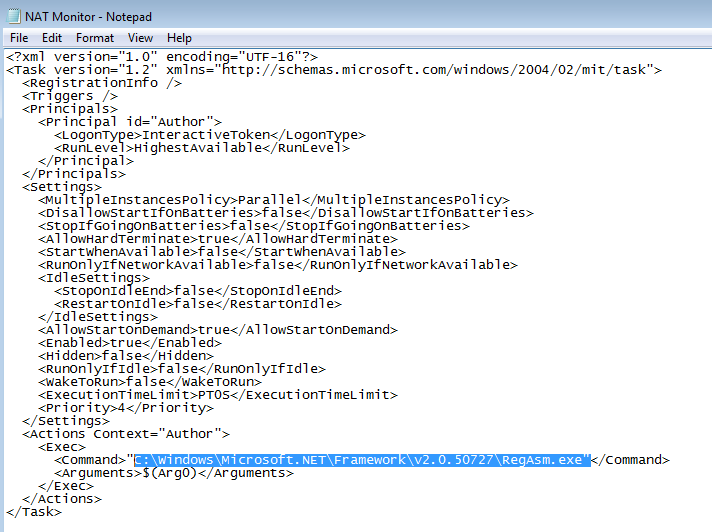
Then, it schedules a task using the following command. This task is called “NAT monitor”.
"schtasks.exe" /create /f /tn "NAT Monitor" /xml "C:\Users\gaya3\AppData\Local\Temp\tmpB400.tmp"<
The NAT monitor task is made to run “Regasm.exe” and not “natmon.exe”.
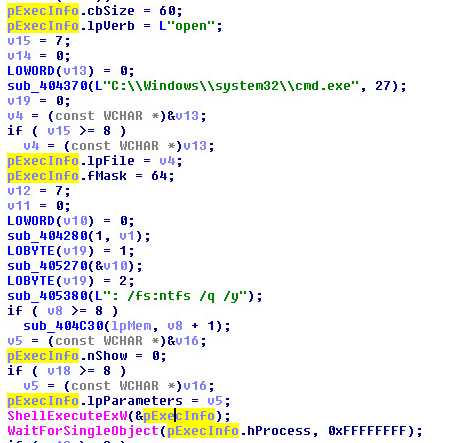
- Process Hallowing:
Regasm is a Windows command-line utility that’s used to register .NET Component Object Model (COM) assemblies. It’s digitally signed by Microsoft. Adversaries use Regasm.exe to proxy execution of code through a trusted Windows utility. This is done to bypass process white-listing and evade detection
This malware starts Regasm.exe process in the suspended state with CreateProcessA(0x4 CREATE_SUSPENDED process creation flag). It retrieves the path to itself and passes it as an argument to the process hollowing function. Process hollowing function replaces Regasm content with the malicious executable and resumes execution. Now the execution of the malicious code is masked under a legitimate process , as the path points to legitimate process “C:\Windows\Microsoft.Net\Framework\v2.0.50727\RegAsm.exe”.
Once poisoned, RegAsm.exe can be used to establish connection to the C2C server, install keylogger/ mouselogger and other elements to steal users credentials and perform financial transactions from the same computer of the client.

- Keystroke Logging :
It captures all the user keystroke information and writes it into an encrypted file called “KB_28549343.dat”

It also contains functionality to simulate keystroke presses, it may perform financial transactions with the stolen credentials from the same computer.
VT Graph:
VirusTotal threat intelligence graph of this campaign is shown below. 1000’s of similar malicious files with different file hashes observed in this campaign.
Threat Graph:

SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
GAV: 19486 Autoit.OLS
GAV: 2376 NanoBot.DN
SonicWall Capture Advanced Threat Protection (ATP) with RTDMI provides protection against this threat.
Hashes:
Email:
5b1fbbc99e01b8df2de401992bc463b35dcec53432145577fe71c0df5c757c6a
7194eb641b50af49885bb412a08f182ed3b6cde9b43a424db4654937564c38e2
ISO:
2d8fb4fb3d92f7f3fe6d599939afe8efcdf2ce5c045118d35ff016f27a1b16a4
1fb34c5ded3432f601680795e3942673ac55a0c89513a31f45e238ed773ab8e4
Exe:
49c2fe6ba8646341b6ecd869daf6fd8dfa0b522d20996f2321006d8a74d30ab6
4d76a57be034e6bae437b5c06c216cf7131d8db1e69ff6cfa881c38aabdb2818
C2C:
*.duckdns.org