SonicWall Capture Labs Threats Research Team investigated the sample mentioned in the story that came up on Reddit. We blogged about it recently and to investigate further we ordered a Gretel A7 device and analyzed it to verify the presence of pre-installed malware.
A brief about /system/
Pre-installed apps on an Android devices are present in /system/app/ or /system/priv-app/ folders and are usually referred to as ‘system apps’. Apps present in these folders cannot be removed by the user as they do not have access to these folders. Another reason why apps installed from device manufacturers – typically referred to as ‘bloatware’ – is typically seen in one of these folders.
Pre-installed malware is also found in these folders thereby hiding their presence from the user and making it extremely difficult to remove them using conventional means.
Analysis on the actual Gretel Device
We extracted a list of all the apps present on the device, a total of 117 (including system apps). The malicious adware discussed in our previous blog on Gretel devices was not present in this list of installed apps for our device. Based on our analysis we verify that the adware mentioned in the previous blog was not a case of pre-installed malware.
However we wanted to verify if there were any other pre-installed malicious apps on our device. We paid close attention to apps present in the system folders as this is usually a good place to hide pre-installed malware. After a preliminary analysis of apps present in the system folder the apps below showed some malicious indicators which prompted us to analyze them further:
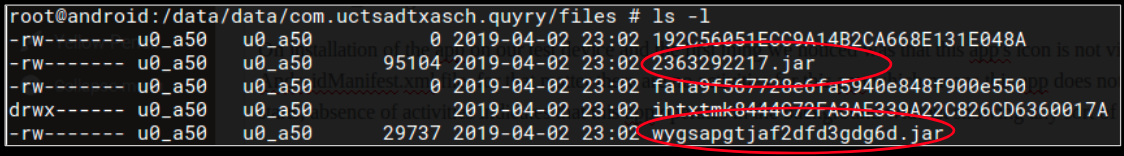
- com.android.service stored as /system/priv-app/com.android.service-9002_0711/com.android.service-9002_0711.apk
- com.ibingo.launcher3 stored as /system/priv-app/Launcher3_G_yisheng_A47_201705191558/Launcher3_G_yisheng_A47_201705191558.apk
Suspicious Network Activity
We kept an eye on the network activity on our device for a few days without installing any new apps, this helped us understand if the device exhibits any suspicious signs without any interference from a user’s side (in terms of new apps installed). The following network activities stood out during an observation period of 7 days:
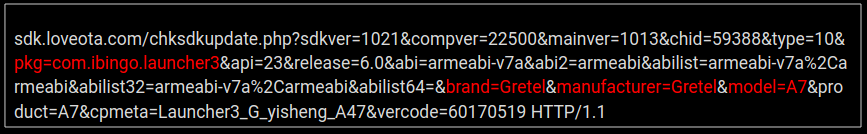
The device brand and model number were sent in the packet above along with the package name responsible for this network activity – com.ibingo.launcher3
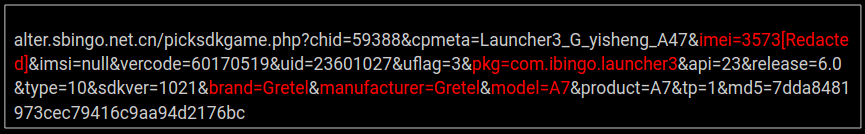
We observed network communication to the host alter.sbingo.net.cn as shown above, in one case IMEI number is leaked which is sensitive data for a device. VirusTotal investigation for this domain showed that this is connected with a number of apks with malicious detection on VT:
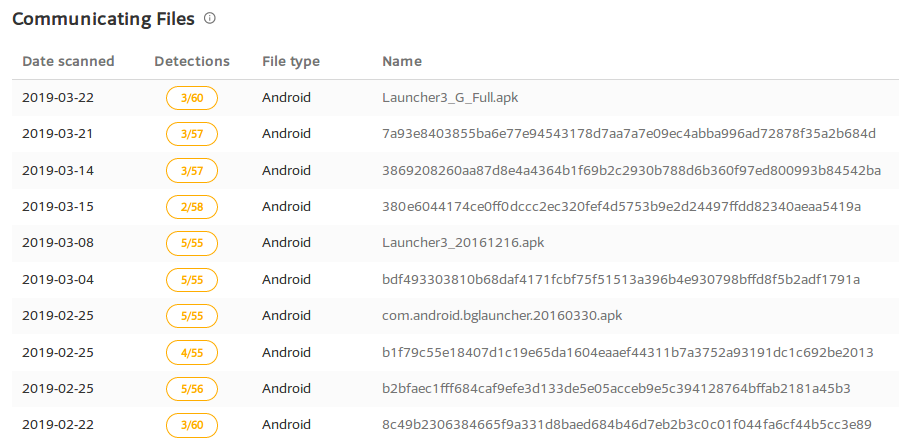
VirusTotal gave us a number of related sub-domains for sbingo.net.cn and the ones listed below have connected apks with malicious detection on VT:
- uistorefee.sbingo.net.cn
- download.sbingo.net.cn
- 1906.sbingo.net.cn
- alter.sbingo.net.cn
- uistorebtz.sbingo.net.cn
- app.sbingo.net.cn
- cdnuistore2.sbingo.net.cn
After observing these packets we analyzed the installed app com.ibingo.launcher3 which is essentially the launcher used in Gretel A7 devices. Upon analyzing and running this app on a different device we observed the same network activity as shown above. We feel there are some suspicious indicators for this app and it leaks the IMEI of the device on which this app is installed.

statistics.flurrydata.com was contacted regularly during our analysis with packets similar to the one listed above. VirusTotal investigation gave us three related sub-domains for flurrydata.com:
- statistics.flurrydata.com
- developer.flurrydata.com
- analyze.flurrydata.com
VirusTotal Relations showed statistics.flurrydata.com connected to a number of malicious apk files:
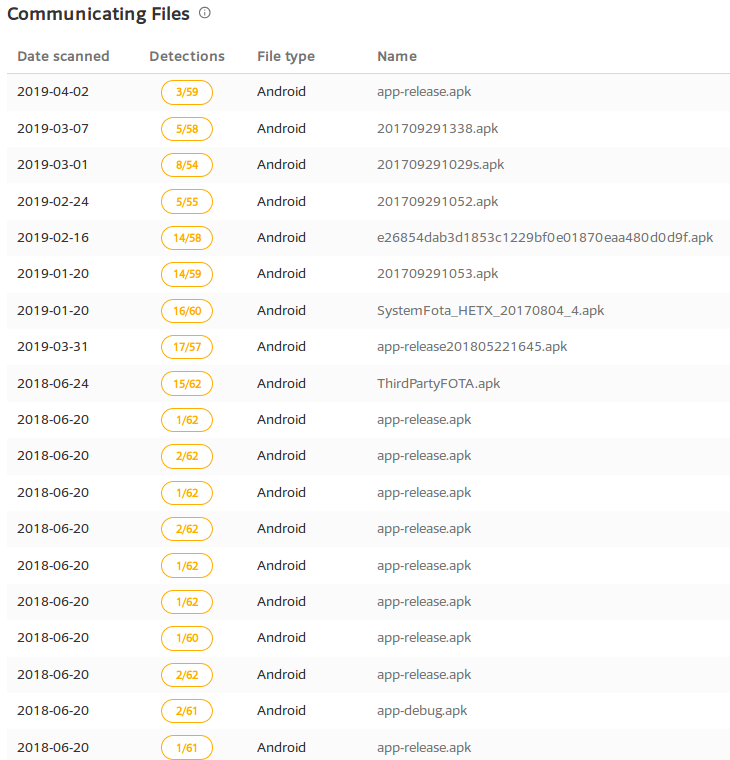
Also, we observed this domain was listed under a Mobile Ad Tracker tool on Github.
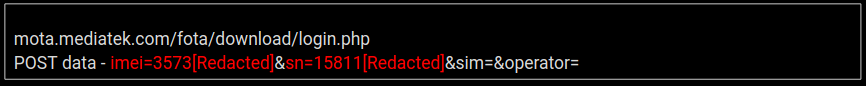
We saw another communication with a domain where the IMEI of our test device was leaked as shown above.
App analysis – com.android.service
We analysed the app com.android.service which was mentioned earlier, the following permissions are used by this app:
- Access network state
- Receive boot completed
- Wake lock
- Read external storage
- Write external storage
- Internet
- Read phone state
- Access wifi state
- System alert window
- Package usage stats
- Install packages
- Delete packages
- Access fine location
- Get tasks
There are a few dangerous permissions used by this app and it can have major implications on the device if misused:
- Install and Delete packages – The app can secretly download and install apps on the device, delete other apps as well
- System alert window – This can be used to how content on top of other apps, bankers and adware use this permission heavily
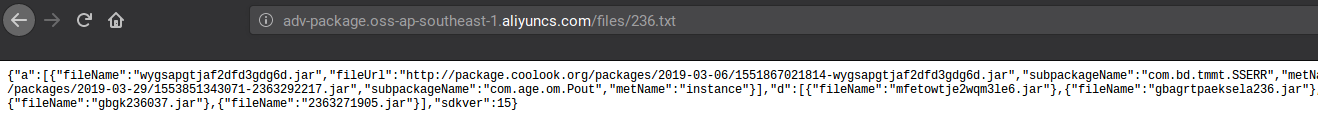
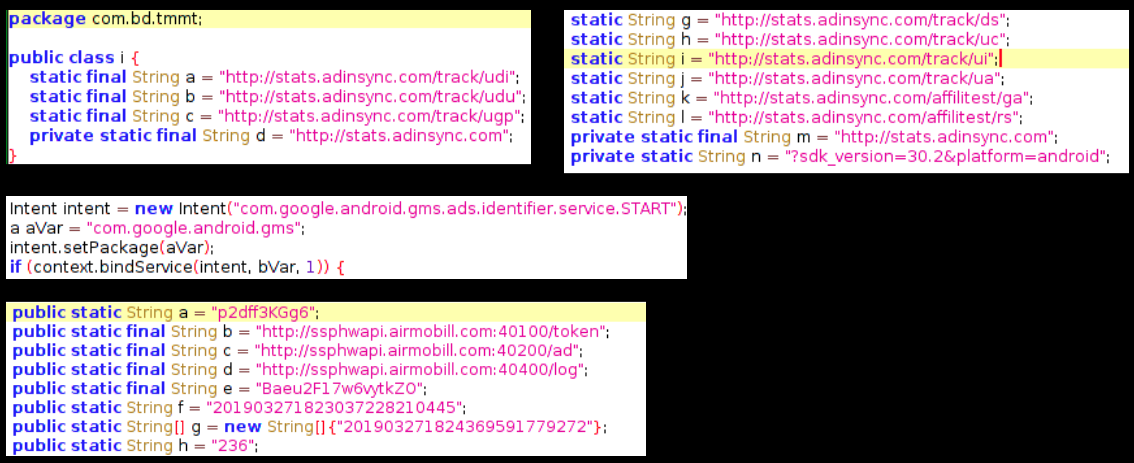
On execution the app reported to the domain iwtiger.com with the date and time of execution and the device model which is stored in a variable interestingly named pid:
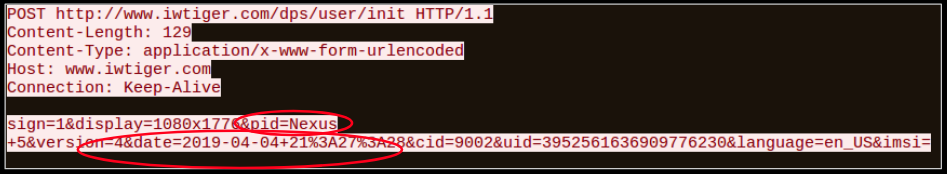
Then it downloaded an apk from static.iwtiger whose package name is com.iwtiger.plugin.activity17 in its app_dex folder
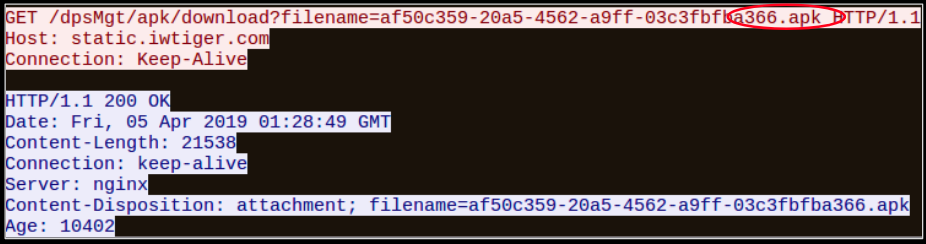
The apk com.android.service contains code similar to code present in a Github repository about dynamic loading of an apk:
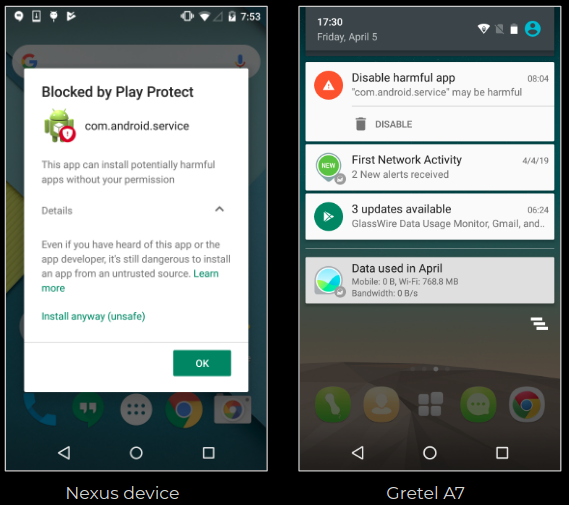
Play Protect to the rescue
During our analysis we saw the Google Play Protect notification about com.android.service being dangerous. Even though our Gretel device shipped with pre-installed malware, this threat was cleaned by Play Protect. When we tried to install this threat on a test Nexus device it was protected there as well:
Researching before buying a device
During our research we saw multiple stories where users have posted about their concerns regarding presence of malicious apps in Gretel devices:
This highlights the importance of taking time to research about a device before purchasing it. The Android ecosystem is very dynamic, malicious apps and domains are often cleaned and the current state may be different from what was observed in the past.
Closing Thoughts
Overall during our analysis period of almost a week we saw suspicious network communication through our test device, IMEI data was also leaked in a few instances which raises a cause of concern. One of the system application has the dangerous permission to install and delete package and we saw it use these permissions where an apk file gets downloaded and executed via dynamic loading technique.
We did not see the adware that we analyzed in our previous blog on our Gretel A7 device, however we did see a number of suspicious pre-installed applications and suspicious network activity during our time analyzing this device. One such app was marked as malicious by Google Play Protect.
In some reported cases advertisements were seen after a number of days of purchasing the device, we did not see any advertisements but our analysis period was considerably short so we will keep an eye on our Gretel A7 device for any suspicious activity for the next few days to come and update our blog accordingly.
SonicWALL Capture Labs provides protection against this threat via the following signatures:
- AndroidOS.Gretel.SRV
- AndroidOS.Gretel.DYN
Indicators of compromise:
- com.android.service – 8a8a2f1c13d0d57186bc343af96abe87
- com.ibingo.launcher3 – 7dda8481973cec79416c9aa94d2176bc