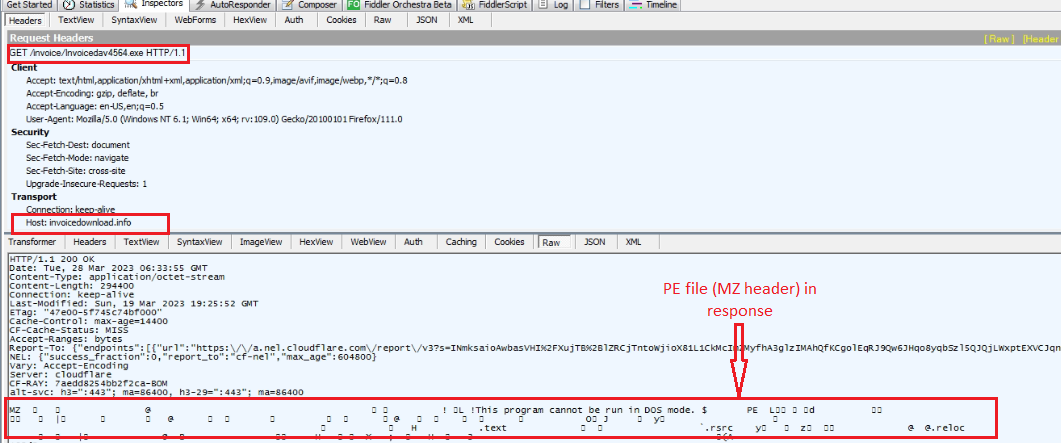
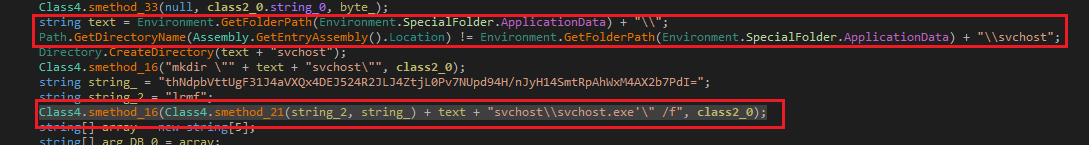
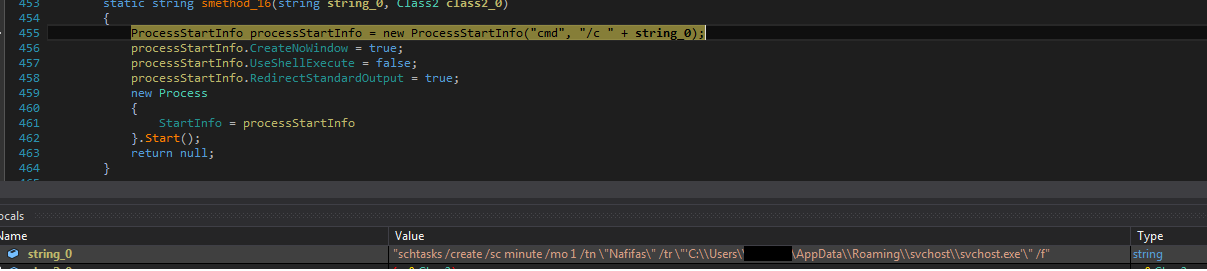
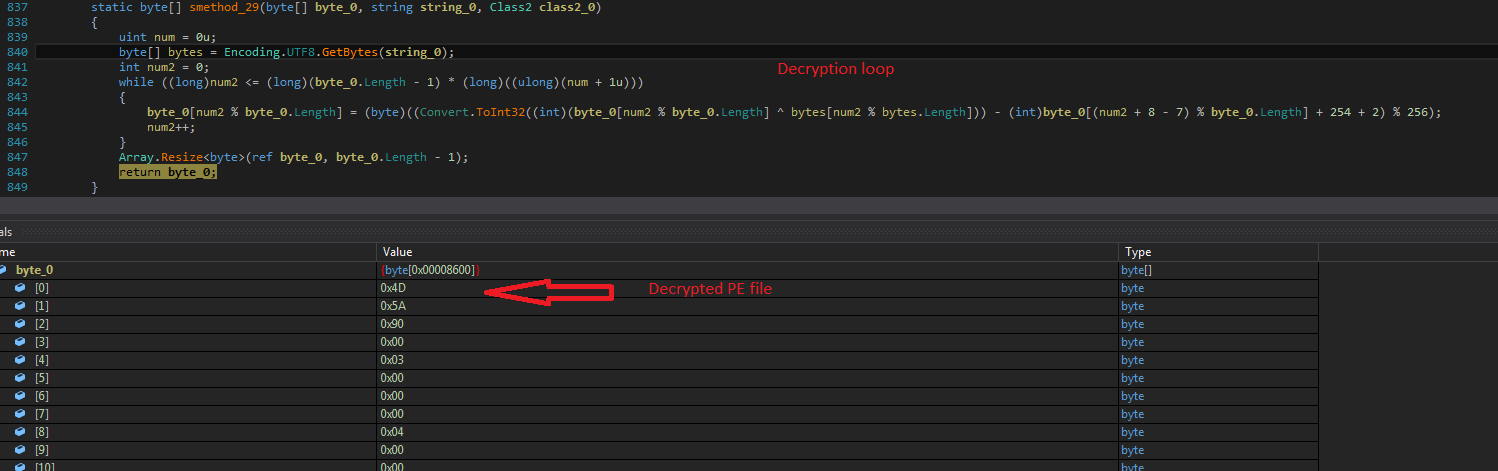
Microsoft Security Bulletin Coverage for May 2023
SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of May 2023. A list of issues reported, along with SonicWall coverage information, is as follows:
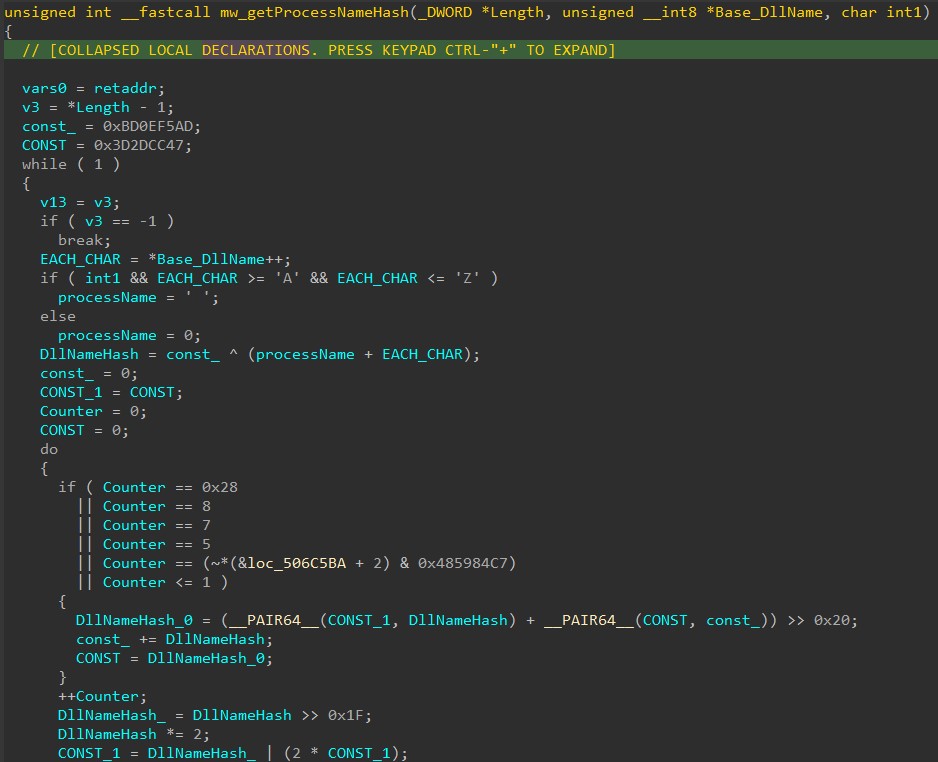
CVE-2023-24902 Win32k Elevation of Privilege Vulnerability
ASPY : 443 Exploit-exe exe.MP_321
CVE-2023-24941 Windows Network File System Remote Code Execution Vulnerability
IPS : 3768 Windows NFS Remote Code Execution (CVE-2023-24941)
IPS : 3826 Windows NFS Remote Code Execution (CVE-2023-24941) 2
IPS : 3836 Windows NFS Remote Code Execution (CVE-2023-24941) 3
CVE-2023-24949 Windows Kernel Elevation of Privilege Vulnerability
ASPY : 444 Exploit-exe exe.MP_322
CVE-2023-24950 Microsoft SharePoint Server Spoofing Vulnerability
IPS : 3769 Microsoft SharePoint Server Spoofing (CVE-2023-24950)
CVE-2023-29324 Windows MSHTML Platform Elevation of Privilege Vulnerability
IPS : 15875 Windows MSHTML Platform Elevation of Privilege (CVE-2023-29324)
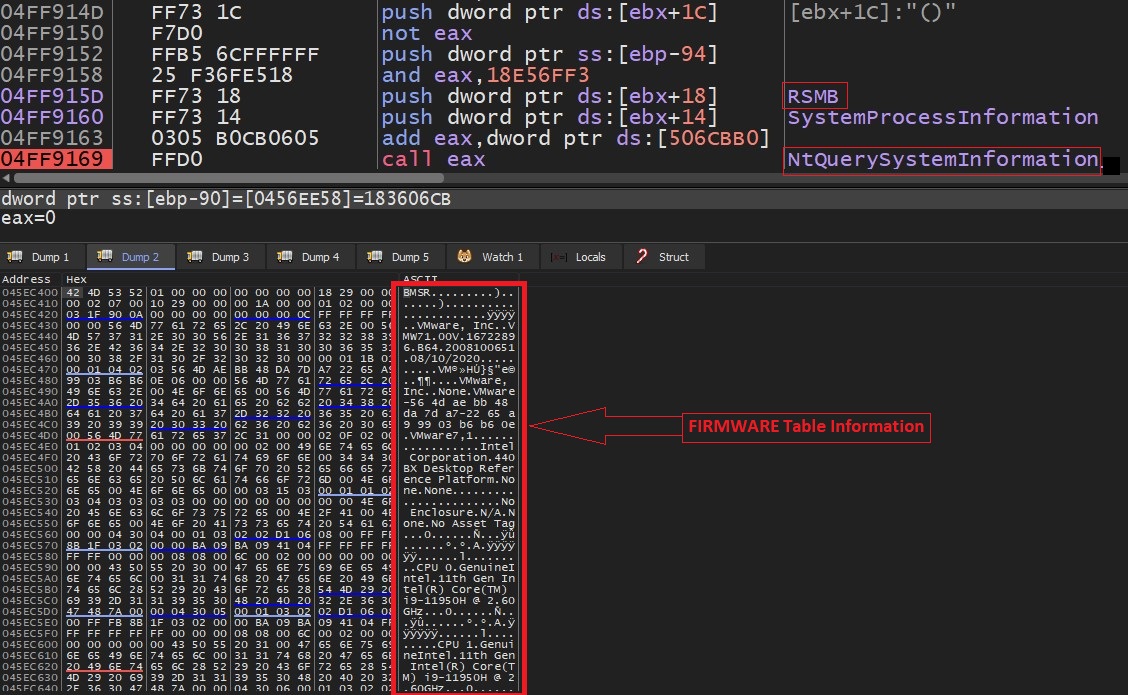
CVE-2023-29325 Windows OLE Remote Code Execution Vulnerability
ASPY : 446 Malformed-rtf rtf.MP_33
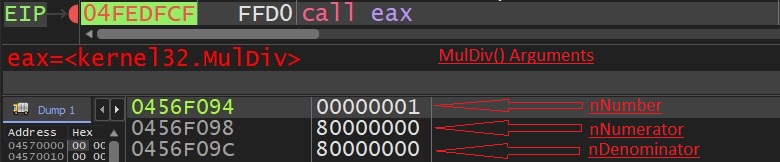
CVE-2023-29336 Win32k Elevation of Privilege Vulnerability
ASPY : 445 Exploit-exe exe.MP_323
The following vulnerabilities do not have exploits in the wild :
CVE-2023-24881 Microsoft Teams Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-24898 Windows SMB Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-24899 Windows Graphics Component Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-24900 Windows NTLM Security Support Provider Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-24901 Windows NFS Portmapper Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-24903 Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-24904 Windows Installer Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-24905 Remote Desktop Client Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-24932 Secure Boot Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2023-24939 Server for NFS Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-24940 Windows Pragmatic General Multicast (PGM) Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-24942 Remote Procedure Call Runtime Denial of Service Vulnerability
There are no known exploits in the wild.
CVE-2023-24943 Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-24944 Windows Bluetooth Driver Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-24945 Windows iSCSI Target Service Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-24946 Windows Backup Service Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-24947 Windows Bluetooth Driver Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-24948 Windows Bluetooth Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-24953 Microsoft Excel Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-24954 Microsoft SharePoint Server Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-24955 Microsoft SharePoint Server Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-28251 Windows Driver Revocation List Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2023-28283 Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-28290 Remote Desktop Protocol Client Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-29333 Microsoft Access Denial of Service Vulnerability
There are no known exploits in the wild.
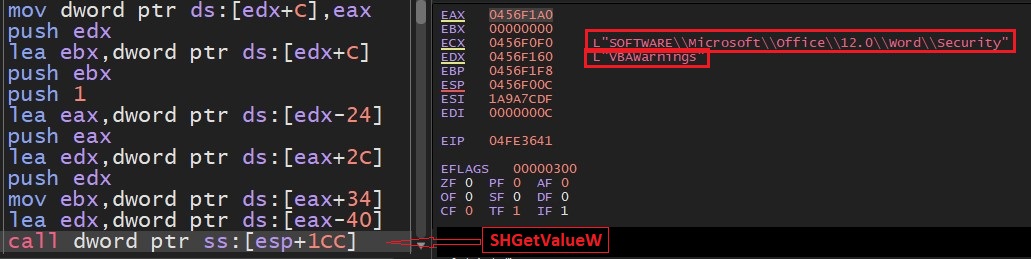
CVE-2023-29335 Microsoft Word Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2023-29338 Visual Studio Code Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2023-29340 AV1 Video Extension Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-29341 AV1 Video Extension Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2023-29343 SysInternals Sysmon for Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2023-29344 Microsoft Office Remote Code Execution Vulnerability
There are no known exploits in the wild.