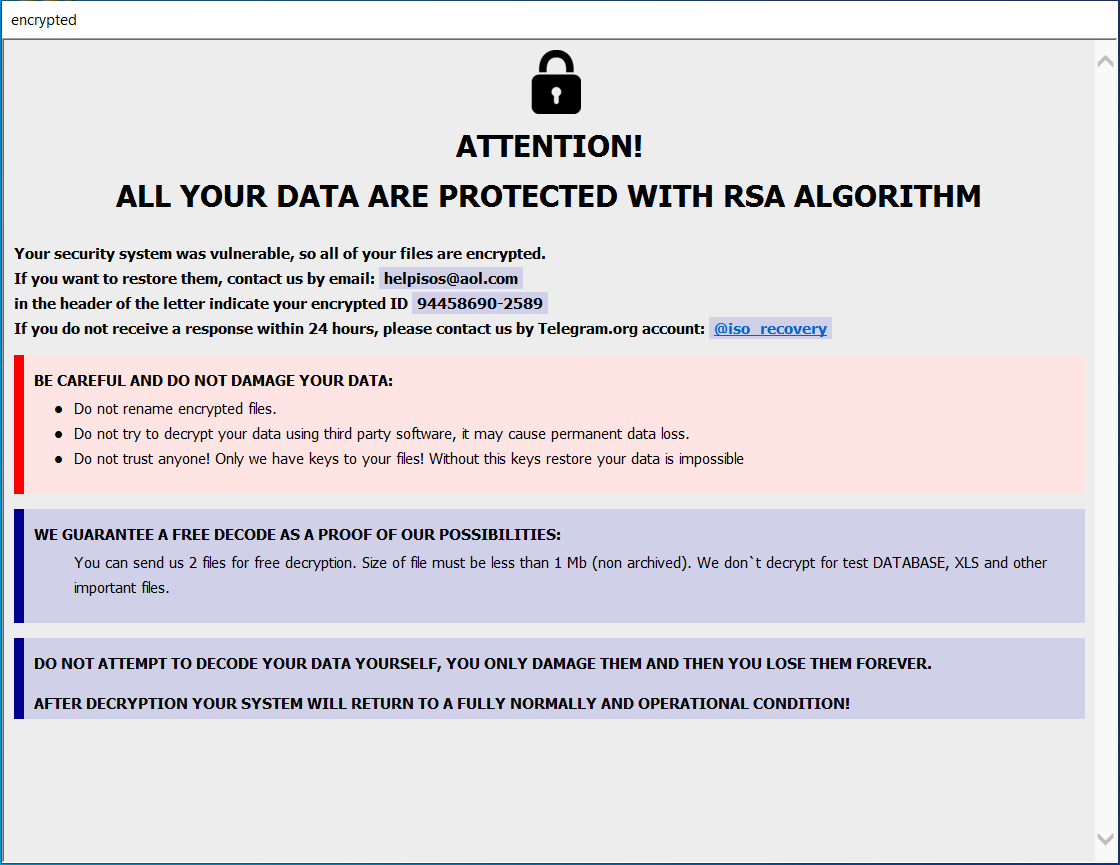
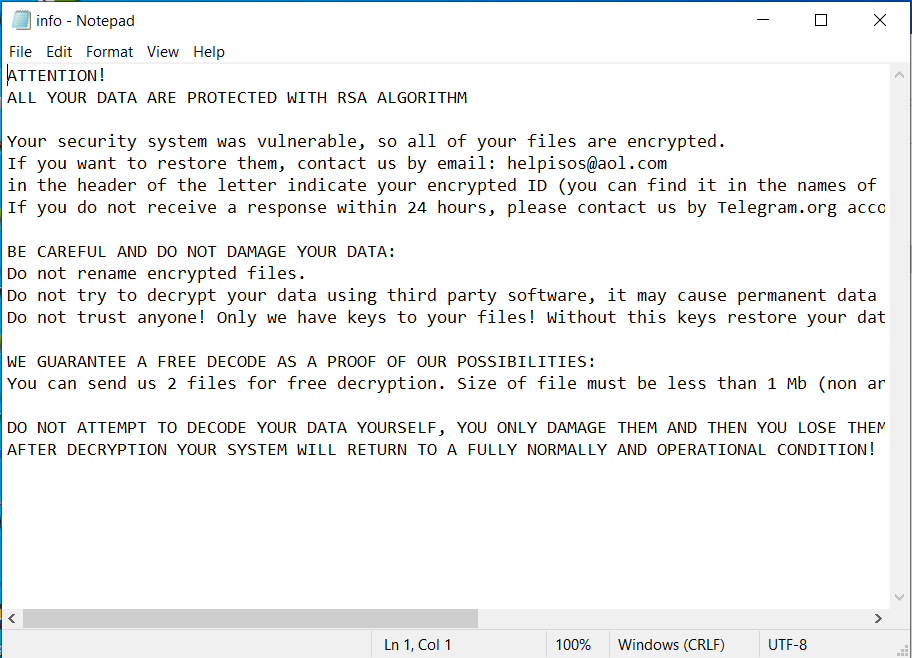
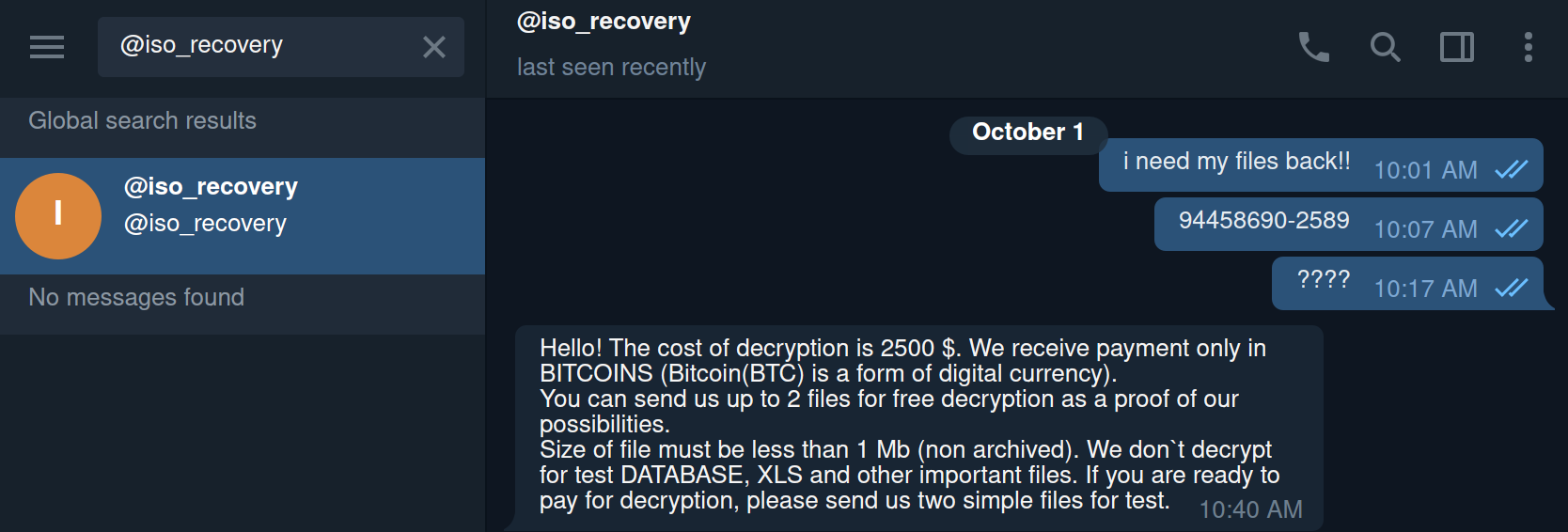
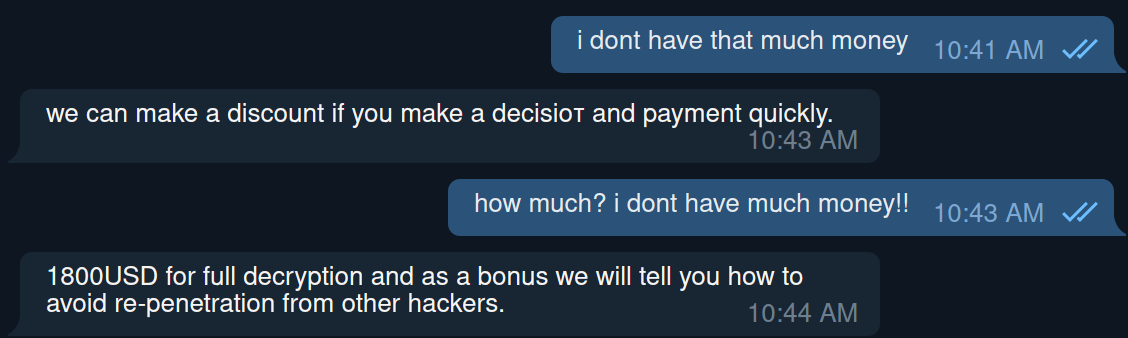
Between legislation to protect government IoT devices, developments in the TikTok saga and Supreme Court arguments, what’s happening at the federal level this week could have far-reaching implications for cybersecurity.
SonicWall in the News
Politics in the Technology World Order — Verdict Magazine
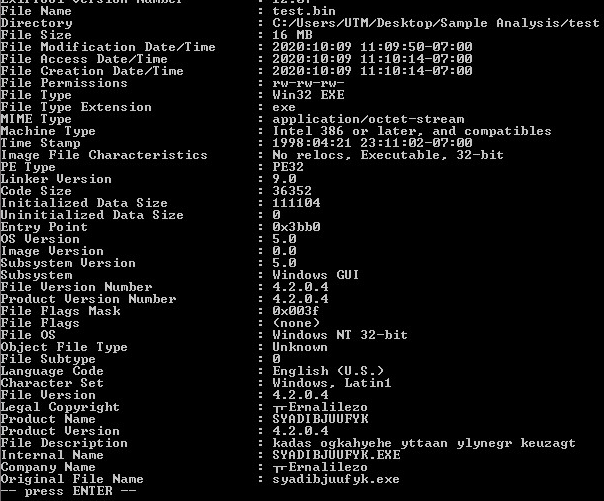
SonicWall President and CEO Bill Conner weighs in on the future of the U.S. data privacy landscape.
Perimeter 81 Looks To Take Firewall Appliances Out — Security Boulevard
SonicWall, an investor in Perimeter 81’s recent funding round, has partnered with the firm on its firewall-as-a-service software.
Sectigo to Be Acquired by GI Partners — Sectigo Press Release
In a comment about the acquisition, SonicWall President, CEO and Sectigo Board Chairman Bill Conner said, “The future is bright for Sectigo as the company builds on its impressive position as a digital identity and web security solutions leader.”
Industry News
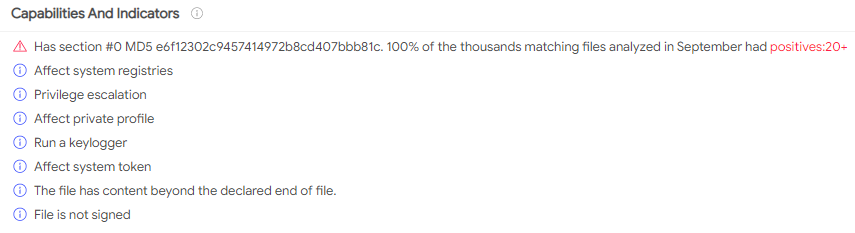
This security awareness training email is actually a phishing scam — Bleeping Computer
A creative phishing campaign spoofs a well-known security company in an email pretending to be a reminder to complete security awareness training.
Oracle-TikTok Deal to Undergo U.S. Security Review — The Wall Street Journal
The Treasury Department said it would review an agreement for Oracle and others to revamp TikTok’s U.S. operations, with the aim of avoiding a ban of the popular video-sharing app.
House approves bill to secure internet-connected federal devices against cyber threats — The Hill
The Internet of Things (IoT) Cybersecurity Improvement Act, passed unanimously by the House, would require all internet-connected devices purchased by the federal government to comply with minimum security recommendations.
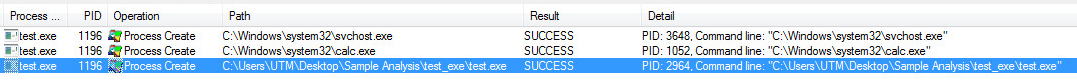
Hackers are getting more hands-on with their attacks. That’s not a good sign — ZDNet
Both nation-state-backed hackers and cybercriminals are trying to take advantage of the rise in remote working — and getting more sophisticated in their approach.
LockBit ransomware launches data leak site to double-extort victims — Bleeping Computer
The LockBit ransomware gang has launched a new data leak site to be used as part of their double extortion strategy to scare victims into paying a ransom.
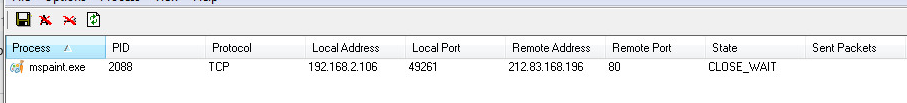
Zerologon attack lets hackers take over enterprise networks — ZDNet
If you’re managing enterprise Windows servers, don’t skip on the August 2020 Patch.
Security researchers slam Voatz brief to the Supreme Court on anti-hacking law — Cyberscoop
The Supreme Court is about to take up a case with major implications for computer research — and a group of high-profile cybersecurity specialists doesn’t want mobile voting firm Voatz to have the last word.
Don’t pay the ransom, mate. Don’t even fix a price, say Australia’s cyber security bods — The Register
Over the past 12 months, the Australian Cyber Security Centre has observed real-world impacts of ransomware incidents, which have typically originated from a user executing a file received as part of a spearphishing campaign.
Russian Intelligence Hackers Are Back, Microsoft Warns, Aiming at Officials of Both Parties — The New York Times
China is also growing more adept at targeting campaign workers, with Beijing mostly aiming at Biden campaign officials.
Iran Says US Vote Hack Allegation ‘Absurd’ — Security Week
Tehran on Friday hit back at allegations by Microsoft that Iran-based hackers had targeted the U.S. presidential campaigns.
Treasury Dept. sanctions Russian, Ukrainian individuals for election interference — The Hill
The Treasury Department has added four Russian and Ukrainian individuals to its specially designated nationals list, citing attempts by the individuals to interfere in U.S. elections.
In Case You Missed It