Madangel infects executable files on the system (August 2, 2013)
Dell SonicWall Threats Research Team observed reports of a File Infector Virus family – Madangel that infects the executables present on the system. The infected executable will then run the malicious code to propagate it further. The injected code contains hardcoded URL’s which it may use to report infection and/or for updating itself. Madangel virus family has been around for many years, and the last variant spotted in year 2011 is still active in the wild.
Infection Cycle:
Upon execution the Virus drops the following file on the system:
- %WINDOWS%system32Serverx.exe [Detected as GAV: Madang.A (Virus)]
In order to start after reboot the Virus adds the following key to the registry:
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun Serverx “%WINDOWS%system32Serverx.exe”
It creates the following Mutex on the system to mark its presence :
- Angry Angel v3.0
The Virus then starts searching for files ending with .exe in the entire system and also in any attached drives. Once found it appends a 4495 Bytes code to this executable at the end of the original code. We observed that the files present in the C:Windows directory are not modified.
We compared an original .exe file with the same file post-infection side-by-side as seen in the image below. We can clearly see that malicious code is appended to it.

Execution of any executable henceforth will also invoke the malicious code. Below we see an instance of calculator.exe executed post-infection. The malicious code can be clearly seen present in it.
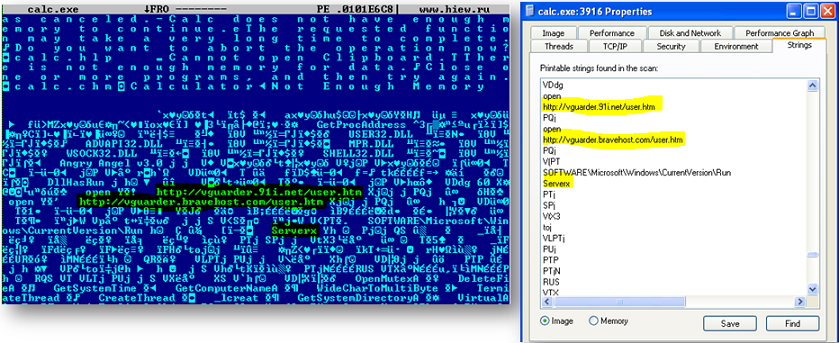
We observed two hardcoded URL’s present in the code:
- http://vguarder.91i.net/user.htm
- http://vguarder.bravehost.com/user.htm
At the time of writing this post both URL’s seem to have been cleaned/down, however there are reports that these links were hosting malicious content in the past. We also observed a component by the name updatex.exe in the code. Based on the name we can fairly assume that this code updates the Virus with additional components. We did not observe any network activity from this Malware during our analysis.
Dell SonicWALL Gateway AntiVirus provides protection against these threats with the following signature:
- GAV: Madang.A (Virus)



