OpenSSL HeartBleed Vulnerability(CVE-2014-0160) Actively Targeted(Apr 9, 2014)
Dell SonicWALL Threats Research Team has observed the OpenSSL HeartBleed Vulnerability being actively targeted in the wild.
This Critical vulnerability has been assigned CVE-2014-0160. This is an Information Disclosure Vulnerability which can be used to reveal up to 64K of memory due to an incorrect bounds check. OpenSSL has also released a Security Advisory that addresses this issue. Since the OpenSSL vulnerable version 1.0.1 has been in the field since March of 2012, in addition to applying the OpenSSL version 1.0.1g patch issued on April 7th, 2014, please issue new keys and revoke any previous keys based on insecure versions.
Dell SonicWALL firewalls with activated Intrusion Prevention protect customers’ servers against this attack with the following signatures by testing the bytes in the heartbeat packet against the limits that are outside the normal bounds:
- IPS:3616 OpenSSL Heartbleed Information Disclosure 1
- IPS:3638 OpenSSL Heartbleed Information Disclosure 2
- IPS:3652 OpenSSL Heartbleed Information Disclosure 3
- IPS:3653 OpenSSL Heartbleed Information Disclosure 4
- IPS:3661 OpenSSL Heartbleed Information Disclosure 5
- IPS:3663 OpenSSL Heartbleed Information Disclosure 6
The following is the format of a HeartBeat Request. Malicious attackers can craft this specific request to extract sensitive information from vulnerable servers not behind a Next Gen firewall.

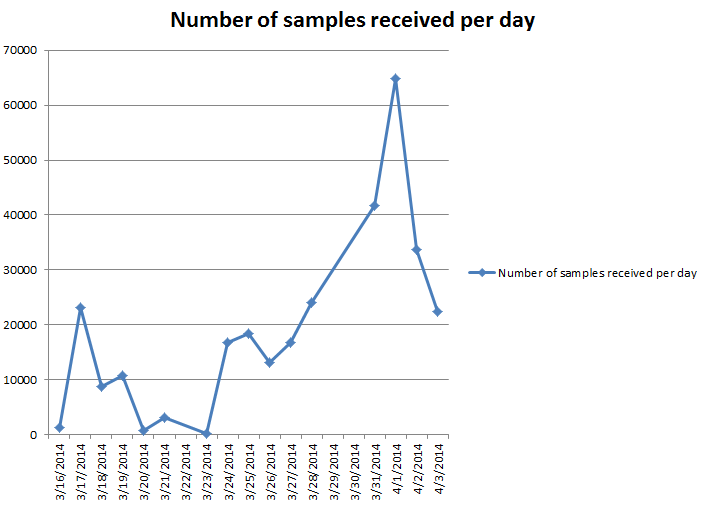
Following stats show how this attack is being actively exploited.

Here, it is quite evident that the hourly hits are increasing.

The distribution below shows USA being targeted the most.