Cutwail spam campaigns lure users to download various threats (April 04, 2014)
The Dell SonicWALL Threats Research team has observed a sharp increase in the number of spammed malware e-mails originating from Cutwail Botnet. We have captured a variety of spam campaigns over past two weeks that involved fake delivery notifications, voice messages, tax returns, pictures, fax messages, invoices, etc.
You can refer to our analysis of latest Cutwail variant here.
The following graph highlights our findings:
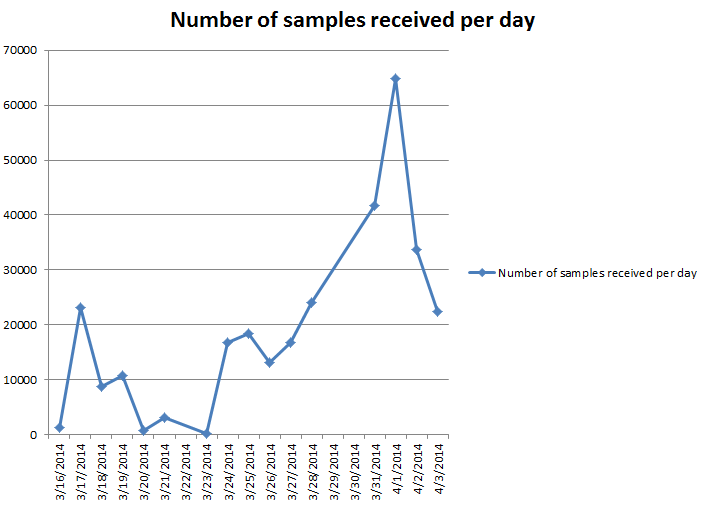
These emails have a common theme of trying to lure consumers to open the attachment which looks legitimate with the following subjects:
- ACH payment failure report
- CCL Computers – Order Despatched
- CIS Online submission received by HM Revenue and Customs
- Documents – WellsFargo
- FW: Loan docs
- Failure to deliver
- Notification of direct debit of fees
- PCI DSS Compliance Programme
- RE:Please open the attachment to view your payment slip for confirmation of order
- Some men commented on your status
- Statement of account
- You send new photo!
- message from your attorney
Below are some sample e-mails captured from these spam campaigns:


Some of the common files seen in these attachments are:
- ABSA certificate update.exe
- Annual _report.PDF.scr
- Avis_de_Paiement.scr
- B8582964793.scr
- Case_26032014.scr
- CBE_Form.scr
- Copy-04012014.scr
- Court_Notice_document_date_25-03-2014Y.exe
- DATA-204658-SCR89.scr
- PPs INvoice PROTECTED.exe
- PrivateImage_03312014.scr
- Returns Repot for march 2014.exe
- test result AF1T-2.exe
- WellsFargo_Docs_042014.scr
These files look like pdfs and word documents but with extensions .scr and .exe as shown:
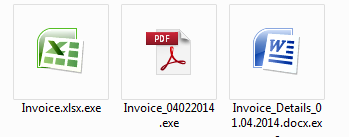


Once the user tries to open these attachments, the malicious file is executed and their machine is compromised.
We urge our users to always be vigilant and cautious before opening attachments from any unsolicited email.
Dell SonicWALL Gateway AntiVirus provides protection against these threats with the following signatures:
- GAV: Bublik.CGAE (Trojan)
- GAV: Inject.KXDK (Trojan)
- GAV: Kryptik.BYQN (Trojan)
- GAV: Kryptik.BYRX (Trojan)
- GAV: Kryptik.BYRX_2 (Trojan)
- GAV: MalAgent.H_349 (Trojan)
- GAV: MalAgent.H_350 (Trojan)
- GAV: Onkods.G (Trojan)
- GAV: Tepfer.ALEH_5 (Trojan)
- GAV: Upatre.AK (Trojan)
- GAV: Waski.A_37 (Trojan)
- GAV: Waski.A_38 (Trojan)
- GAV: Waski.A_39 (Trojan)
- GAV: Waski.A_40 (Trojan)
- GAV: Zbot.AAU_161 (Trojan)
- GAV: Zbot.PA (Trojan)
- GAV: Zbot.RYOT (Trojan)
- GAV: Zbot_133 (Trojan)
- GAV: Zortob.B_89 (Trojan)
- GAV: Inject.KXDK (Trojan)



