ImageTragick: Owning a Web Server Via Simple Upload
When it comes to editing, converting or modifying pictures, the first thing that comes into people’s minds is Photoshop, or MS Paint. However, imagine if a website had to resize, crop, blur, rotate or even watermark all pictures uploaded by many users. It becomes extremely difficult to do so manually. One of the most popular tools for image processing used by these web services is ImageMagick.
Lately, there were reports regarding multiple vulnerabilities concerning ImageMagick. Let’s explore some of them in detail.
Basic Setup
In order to understand what is going on, we need the following:
1. Web server -> For this, I setup an Ubuntu server running Apache.
2. ImageMagick -> Since this is the vulnerable toolkit we are trying to test. Here, we will mainly be focusing on the “convert” app. As the name implies, this application can be used to convert an image file from one format to another. It can also resize, crop, etc.
IE:
Convert test.jpg test.png -> This converts a JPEG file into a PNG file
Convert – resize 200×200 test.jpg out.png -> this converts and resizes a JPEG file to a PNG file
3. PHP/PERL/Python -> Since we will be dealing with the process of uploading files to the web server, we need to create server side scripts to process the uploaded files. For this, I have 2 files, an HTML page and a PHP script.
HTML:

PHP:

So We Upload Images?
Although ImageMagick processes images, it can also accept text files. These text files (.SVG and .MVG) contain special instructions which tell ImageMagick what to draw.

The file above tells ImageMagick to draw an ellipse. The edge is black, while the inside is red. In order to get the JPEG equivalent of the above, we simply run the following: Convert elipse.mvg elipse.jpg
And Voila!

The vulnerabilities occur in how ImageMagick processes certain “pseudo protocols”. Let’s explore some of them now.
CVE-2016-3714 – Code execution via insufficient character filter
Because of insufficient character filters, it is possible for an attacker to execute certain commands. Simply calling the ImageMagick’s “convert” tool, can execute unwanted instructions.
Due to insufficient character filters, it is possible to insert commands by calling the “convert” tool from the command line.
convert ‘https://example.com”;ls “-la’ new.png

The above also works if you used a MVG or SVG as follows:

Then in the command line, run:
Convert insufficient.mvg test.png
However, based on my file upload tests, I have yet to make this work. It may be just a local vulnerability. But do not fret. There is more than 1 way to own a server.
CVE-2016-3717 – Local file read
This vulnerability allows a remote attacker to read files within the web server. This is because of how ImageMagick processes the ‘label’ protocol. By including the filename an attacker want’s to view, they can produce an image file containing the file’s contents.

Uploading this file using our test HTML page we get:>/p>

CVE-2016-3715 – File deletion
Once the attacker was able to view the file contents, they need to remove traces of this. One way of doing it is by deleting the image file created by the previous exploit. This is done using the ‘ephemeral’ protocol.
Using the ellipse example earlier, we can delete the generated image file containing /etc/passwd:

CVE-2016-3718 – SSRF
Perhaps the most tragic of all the ImageMagick vulnerabilities right now, is the SSRF (Server Side Request Forgery) vulnerability. This vulnerability allows an attacker to have the web server download remote files.
If it is only allows file downloads, then why is it tragic? The reason is simple. The downloaded file(s) can be backdoor scripts. In 2015, it was reported that pastebin.com, a legitimate site was used to house malicious scripts. Using the “url” protocol, an HTTP GET request can be initiated to download a php backdoor directly from pastebin.com.

After uploading the malicious MVG, we can then go to the downloaded “backdoor.php”

As you can see, the above php script is capable of doing far more than information disclosure or file deletion.
Prevention Methods:
As seen in the above, filename extension checks do not help prevent exploiting the above mentioned vulnerabilities. In fact, as shown, our uploaded files have the .jpg extension.
Some suggest using a policy file to disable the vulnerable ImageMagick coders/protocols. However, if you are sure that you do not need to use MVG and SVG files, then you can simply use the PHP getimagesize() function. If the uploaded file is MVG or SVG (which are essentially text files), this function returns false.

Dell SonicWALL Threat Research Team has researched these vulnerabilities and released the following signatures to protect their customers:
- IPS11587: ImageMagick Local File Read
- IPS11584: ImageMagick Remote Code Execution 1
- IPS11585: ImageMagick Remote Code Execution 2
- IPS11589: ImageMagick SSRF
- WAF9023: ImageMagick Local File Read
- WAF9022: ImageMagick File Deletion
- WAF9021: ImageMagick Server Side Remote Forgery
























 Below is the number of critical CVEs related to IE 11 and Edge in last 9 months:
Below is the number of critical CVEs related to IE 11 and Edge in last 9 months:
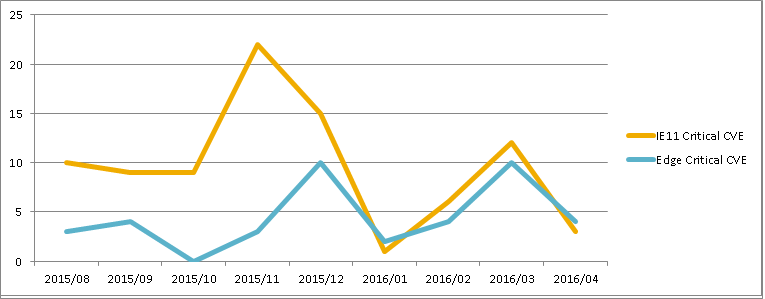 Over past years Microsoft has lost market share in web browser (source:StatCounter) and we think one of the reasons is that Internet Explorer is more prone to vulnerabilities.
Over past years Microsoft has lost market share in web browser (source:StatCounter) and we think one of the reasons is that Internet Explorer is more prone to vulnerabilities.
.svg.png) Microsoft is taking right direction on improving security in Edge. We hope Microsoft keeps this effort that one day Edge will become a solid and integrated product.
Microsoft is taking right direction on improving security in Edge. We hope Microsoft keeps this effort that one day Edge will become a solid and integrated product.



