As we know, email is the most popular attack vector used by threat actors to carry out targeted cyber attacks. In fact, more than 90 percent of cyber attacks start with a phishing email campaign. It is the easiest way for a cyber criminal to enter a network and execute tactics to accomplish an objective — be it data exfiltration, delivering a malicious payload or phishing for credentials.
Using social engineering, the tactics of accomplishing these objectives are highly sophisticated and targeted. Email is a primary collaborative tool to share documents, such as PDFs and Microsoft Word files, and URLs that could be weaponized with malware. Logically, phishing has evolved with this user behavior.
How email attachments are weaponized
File attachments, such as Microsoft Word documents and Adobe PDFs, have the ability to include embedded URLs, macros and scripts. This makes it possible for these files to work as executable malware. These malicious file attachments are used as delivery vehicles for ransomware and other zero-day threats. Here are some of the most popular methods files can be weaponized:
Embedded macros and scripts that hide malicious payloads
First, attackers embed a macro that obfuscates malicious payloads in the document. They then use personal information gathered through social engineering to mislead the user into enabling the macro content to run and infect the victim’s computer. These exploits take advantage of software vulnerabilities and then launch the intended payload to infect the computer.
Embedded macros and scripts that download malware from external sites
Documents can also be embedded with scripts that call external Command & Control (C&C) servers or websites to download malware inconspicuously. Often, these downloaded payloads take the form of ransomware, trojans, infostealers or botnets that make your system part of the malicious networks that carry out attacks on behalf of cyber criminals.
Fake attachments and embedded links
In some cases, attackers send documents or fake attachments, such as a PDF or a Word file, with embedded URLs. After clicking on the URL, the victim is redirected to a sign-in page that looks and feels authentic. These sign-in pages are well crafted and designed to deceive even educated users. Unsuspecting victims often fall prey by entering their credentials into the sign-in page.

High-profile phishing attacks
Google, January 2017
This phishing scam targeting Google users was clever and deceiving. Victims received an email that seemed to come from a familiar contact. The email included a legitimate file attachment that looked like a PDF or Word document. But the attachment was, in fact, an image with an embedded URL. Victims who clicked the attachment for a preview were redirected to a well-designed Google sign-in page that looked authentic. The fake page prompted the victim to enter credentials that enabled the cyber criminals to compromise the user’s Google account.
DocuSign, May 2017
A company that provides digital document-signature services, DocuSign, was the victim of a targeted phishing campaign. Users received an email that appeared to come from DocuSign and included a “Review Document” link. Once the link was clicked, a weaponized Word document with embedded malicious macro was downloaded. When the user enabled the content, the macro called a C&C server to download malware payload stealthily onto the victim’s computer.
Netflix, November 2017
Toward the end of last year, Netflix made the headlines for all the wrong reasons. A successful and sophisticated phishing campaign targeted the streaming service’s subscribers. This attack did not include any file attachments. Instead, attackers crafted a personalized email informing them that their account was suspended. They were asked to take an action by clicking on a fake link that redirected the then to a well-designed web page to collect credentials and credit card information.
Pyeongchang Olympics, January 2018
The 2018 Winter Olympics in Pyeongchang, South Korea, was one of the first victims of 2018 via a deadly, targeted spear-phishing attack. Appearing to be sent by National Counter-Terrorism Center (NCTC), the email included an attachment — a malicious Microsoft Word document with the original file name 농식품부, 평창 동계올림픽 대비 축산악취 방지대책 관련기관 회의 개최.doc (“Organized by Ministry of Agriculture and Forestry and Pyeongchang Winter Olympics”). This spear-phishing campaign’s objective was to establish back doors into the networks once the victim opened the Microsoft Word document attachment.
How to stop phishing and other email attacks
Email security is no longer just about blocking mass spam and phishing campaigns. The above incidents indicate the evolution of how cyber criminals use email as a threat vector, and how they use the versatility of PDFs and Microsoft documents to their advantage.
These are advanced email threats that are carefully planned and highly targeted attacks. Traditional anti-spam and signature-based anti-malware simply cannot stop these attacks.
A multi-layered security approach provides the best defense against these email threats. The layers should include advanced threat protection features, such as sandbox analysis for email file attachments and embedded URLs, and email authentication technologies such as SPF, DKIM and DMARC.
It is also true that not all sandboxes offer equal protection. The cloud-based SonicWall Capture Advanced Threat Protection (ATP) service blocks the most evasive malware with its multi-engine approach.
Capture ATP now includes the recently announced, patent-pending Real-Time Deep Memory Inspection (RTDMITM) technology. RTDMI blocks malware that does not exhibit any malicious behavior or hides its weaponry via encryption.
By forcing malware to reveal its weaponry in memory, the RTDMI engine proactively blocks mass-market, zero-day threats and unknown malware utilizing real-time memory-based inspection techniques. This means, by design, RTDMI can sniff out malware obfuscated within PDF files and Microsoft Office documents by threat actors.
With high performance, fast scan times and block-until-verdict capability, Capture ATP offers comprehensive protection against advanced cyber threats.
To learn more about our analysis of the cyber arms race, and what you can expect in 2018, download a complimentary copy of the 2018 SonicWall Cyber Threat Report.







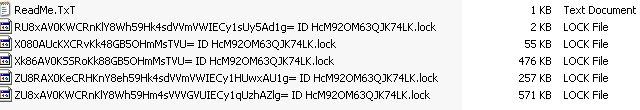
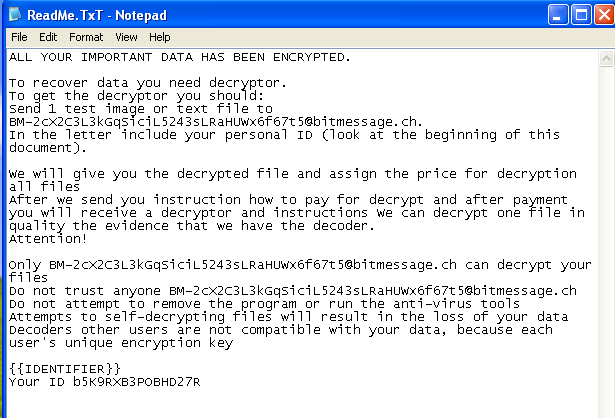


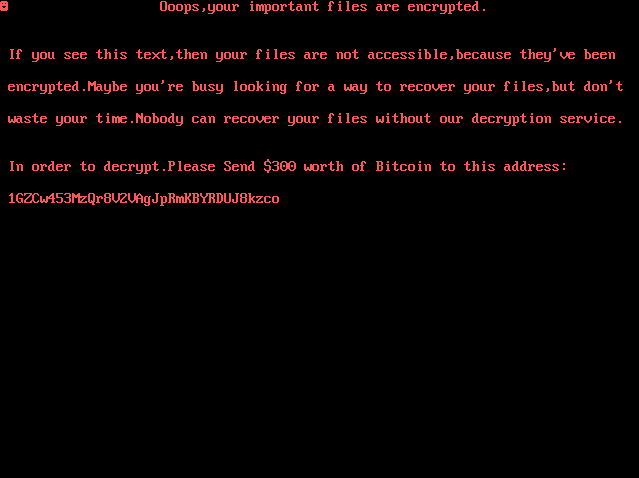
 The attacker can then submit a complex encryption key to encrypt the site’s content. This results to:
The attacker can then submit a complex encryption key to encrypt the site’s content. This results to: