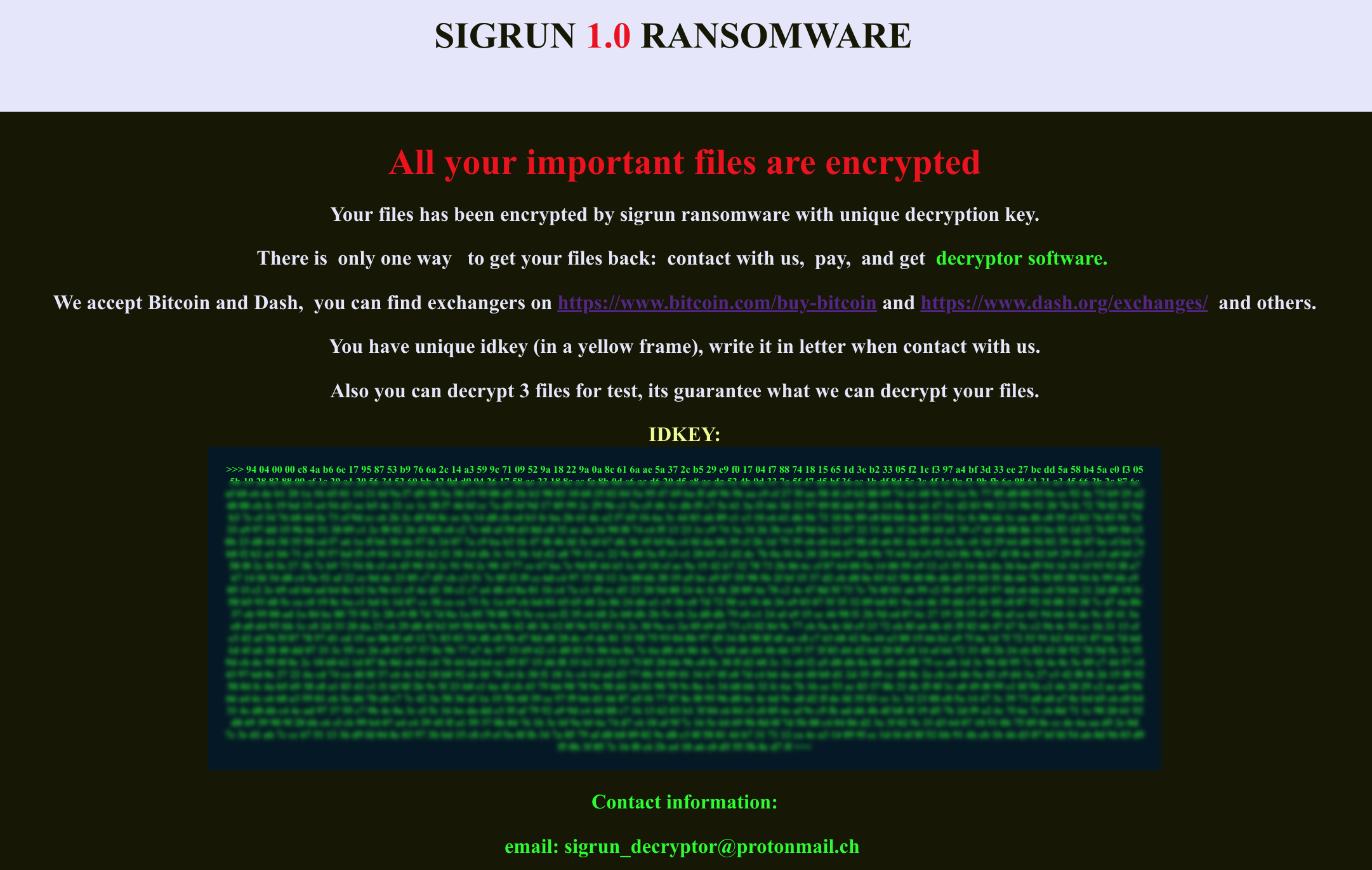
eWeek Goes 1-on-1 with SonicWall CEO Bill Conner
Bill Conner has a plan for SonicWall. And he’s already ahead of it.
In a recent interview with eWeek, the SonicWall CEO provided high-level perspective on not only where SonicWall is and how it got here, but also where it’s going in the future. It was a candid, one-on-one conversation that really lets the industry get to know SonicWall as a company.
“Everything comes through some kind of a network … where we think the market is going is really going to be about automated, real-time breach detection and prevention,” said Conner.
Announced in May 2018, SonicWall financially separated from Quest with oversubscribed investment interest and unprecedented growth in the last six quarters. This success is less than two years removed from Francisco Partner’s purchase of SonicWall from Dell.
“We still have Dell as a partner, and as an OEM, and still do a great deal of business with them,” Conner told eWeek. “We also have business that has nothing to do with Dell.”
Conner walked eWeek through the last 10 months of fast-moving growth for SonicWall, which included 12 new products that featured updates to trusted firewalls, introduced new virtual firewall offerings and unveiled the SonicWall Capture Cloud Platform.
Conner stressed that all of the development into defending endpoints, email and other areas of vulnerability does not mean that SonicWall is diverging from its true nature, which is primarily that of a network security company. SonicWall is simply expanding the breadth of its cyber security portfolio to deliver more cost-effective, real-time protection to customers and partners.
“One of the big questions when I came in was, ‘Is the brand going to be alive?’” said Conner. “Then there were questions about our roadmap and ability to deliver … Now our vision, that I started talking about six quarters ago, is starting to be real.”
This fiscal year SonicWall also added over 24,000 SecureFirst partner organizations, a 60 percent year-over-year increase, while closing $530 million in partner deal registrations. Since the start of 2018, SonicWall has collected 27 cybersecurity industry accolades, most recently being named the Editor’s Choice Security Company of the Year by Cyber Defense Magazine.