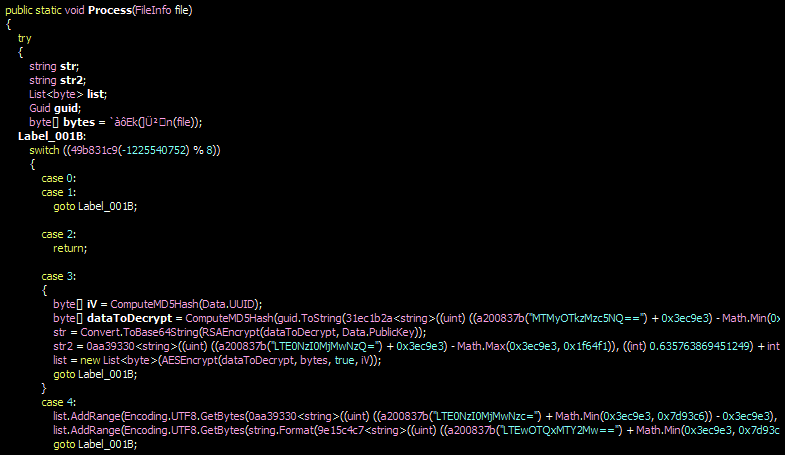
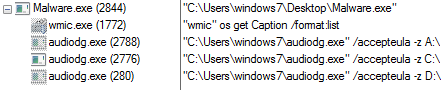
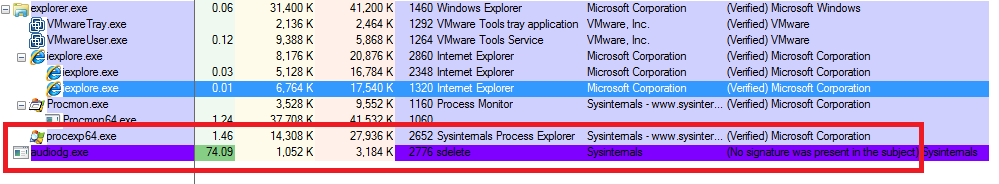
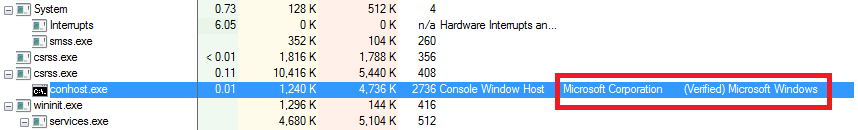
Technology and data usage are changing at a rapid pace. Finding a way to store, manage and distribute data is a major challenge. Plus, the need for compute and storage grows at unprecedented rates. You need to buy racks, then hire staff to configure, maintain and monitor appliances.
It’s a no-brainer that cloud adoption is becoming inevitable.
According to a recent study by RightScale, more than 81 percent of enterprises have a multi-cloud strategy in place. Of this group, 51 percent have embraced hybrid cloud environments, while 21 percent use multiple public clouds and 10 percent have various private cloud strategies.
Cloud adoption drives business growth by increasing agility and innovation, while reducing cost. According to Gartner, by 2020 a “No-Cloud” policy will be as rare as a “No-Internet” policy is today. So, you can imagine the importance of secure cloud adoption. It is the future.
Private Cloud Security from SonicWall
In line with this, SonicWall continues to expand its cloud offering with added support of the Microsoft Hyper-V platform on SonicWall Network Security virtual (NSv) firewall series, along with new flexible licensing options. SonicWall also recently announced support for AWS* and Azure platforms.
Hyper-V support is available across the full suite of NSv firewalls. The flexible licensing model introduces a non-perpetual method of licensing your firewalls. Securing data wherever it resides should be consistent and seamless, providing you increased flexibility and an improved security posture.
Do I Need Virtual Firewalls?
While securing the cloud is a must, it is not an easy task. Gartner predicts that through 2020, 95 percent of cloud security failures will be the customer’s fault. And according to Research and Markets, the cloud data center market is expected to reach $67.5 billion by 2023.
With the widespread adoption of virtualization, it becomes increasingly critical to secure workloads and data across your multi-cloud deployment. Virtual firewalls can be deployed quickly, driving productivity and innovation. By being virtual, there is a huge benefit of shifting from CapEx to OpEx models.
Virtual firewalls, like NSv, address some of the critical needs of public cloud security. Below are some of the key benefits of leveraging NSv to protect your public cloud infrastructure and resources.
- Gain complete visibility into virtual environment for threat prevention
- Implement proper security zoning and ensure appropriate placement of policies
- Defend against zero-day vulnerabilities with SonicWall Capture ATP
- Prevent service disruptions in the virtual ecosystem
- Gain centralized control and visibility with single-pane-of-glass management via Capture Security Center
- Leverage agility and scalability without performance impact
- Maintain security governance, compliance and risk management
Plus, as the threat landscape evolves and takes advantage of various vulnerabilities in the cloud and virtual workloads, it is essential to secure cloud infrastructure. Some of the common type of attacks include cross-virtual machine attacks and side-channel attacks, like PortSmash and Foreshadow.
Virtual firewalls can be used to defend against information threats and protect against unauthorized takeover of virtual machines (VMs). It can provide security at every level of the virtual environment, providing granular security posture control.
What Cloud Platforms do SonicWall Virtual Firewalls Support?
With NSv virtual firewalls you can leverage next-gen firewall capabilities across your multi-cloud deployments. Platform support currently extends to ESXi, Azure, AWS* and Hyper-V*.
How Can I Purchase NSv?
Previously, NSv was available only via perpetual licensing. To solve the challenge of relying just on perpetual model licensing and provide flexibility to our customers, SonicWall introduces non-perpetual licensing for NSv. This is an additional offering to the current SonicWall perpetual licensing model.
SonicWall licensing models provide customers the flexibility to choose perpetual licensing or non-perpetual licensing based on their requirements.
Non-Perpetual Licensing Model
Non-perpetual licensing is ideal for those who require a short-term solution and agile deployments. It’s a single bundle for firewall software, security and support services, making it simple to purchase these appliances. Once the period ends, all services expire at the same time. Customers are notified via MySonicWall before service expiration.
The non-perpetual licensing model is available via the three options: IPS/App Control Subscription, TotalSecure Subscription and TotalSecure Advanced Subscription, which is available over a one-year period.
| Service Offering Type |
Bundled Service |
| IPS/App Control Subscription |
NSv Software + IPS + App Control + Support |
| TotalSecure Subscription |
NSv Software + CGSS + Support + CSC |
| TotalSecure Advanced Subscription |
NSv Software + AGSS + Support + CSC |
Perpetual Licensing Model
Perpetual licensing is SonicWall’s traditional licensing model where firewall services do not expire, while security and support services do. Perpetual licensing is suitable to customers that require long-term solutions.
Virtual Firewall Promo: NSa/NSsp with NSv
The SonicWall NSv promo enables organizations to extend the next-gen security of their private data center to the public cloud and ensure end-to-end security of their multi-cloud environment.
Organizations can test drive SonicWall virtual firewalls at no additional cost or commitment to see if it fits their needs and requirements.
- Test drive an NSv with a TotalSecure subscription for one year at no additional cost
- Get an NSv TotalSecure subscription with Comprehensive Gateway Security Service (CGSS), Capture Security Center and 24×7 support
- Requires eligible SonicWall NSa or NSsp firewall with an active AGSS/CGSS subscription
- Deploy NSv firewalls across public and private cloud platforms, including ESXi, Azure, AWS* and Hyper-V*
To take advantage of the SonicWall NSv virtual firewall promo, please contact your dedicated SonicWall SecureFirst partner or reach out to SonicWall online.
To best capitalize on virtualization trends, IT must operationalize the complete virtualization of computing, networking, storage and security in a systematic way. A new approach is required to select an appropriate and effective next-generation virtual firewall solution. Download our exclusive brief to explore fundamental capabilities, core solution requirements and best practices.
* Hyper-V and AWS availability pending.