Curated cybersecurity news and trends from the industry’s leading bloggers and news outlets, for you from SonicWall.
Winter is rolling on, and SonicWall is still plowing its way into headlines. ITPro cited our data while discussing major ransomware strains. Our Director of Regional Sales in LATAM, Arley Brogiato, spoke with GQ Brasil. We congratulate SonicWall’s Jason Carter and Matt Brennan for earning 2023 CRN Channel Chief Recognition.
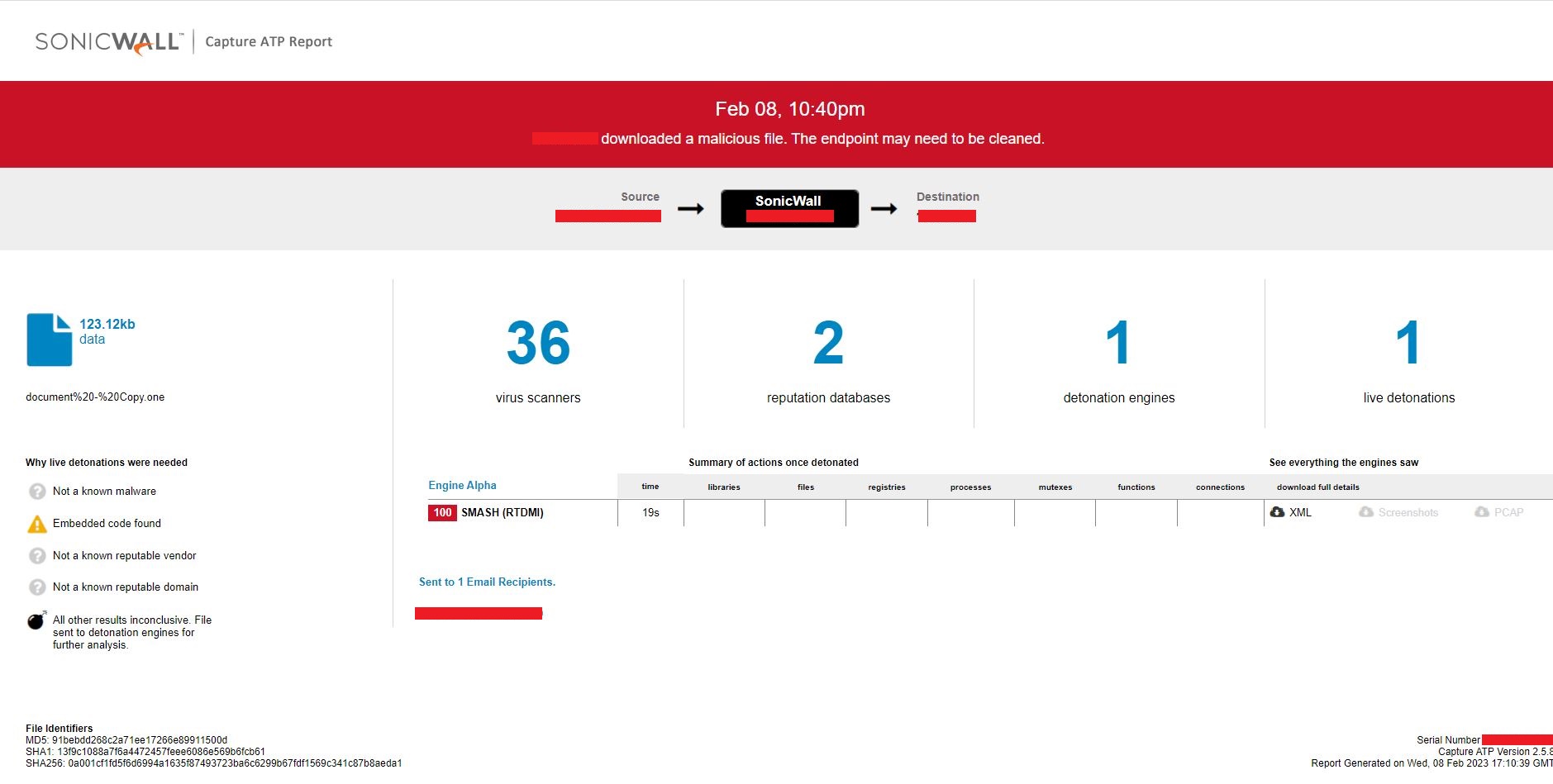
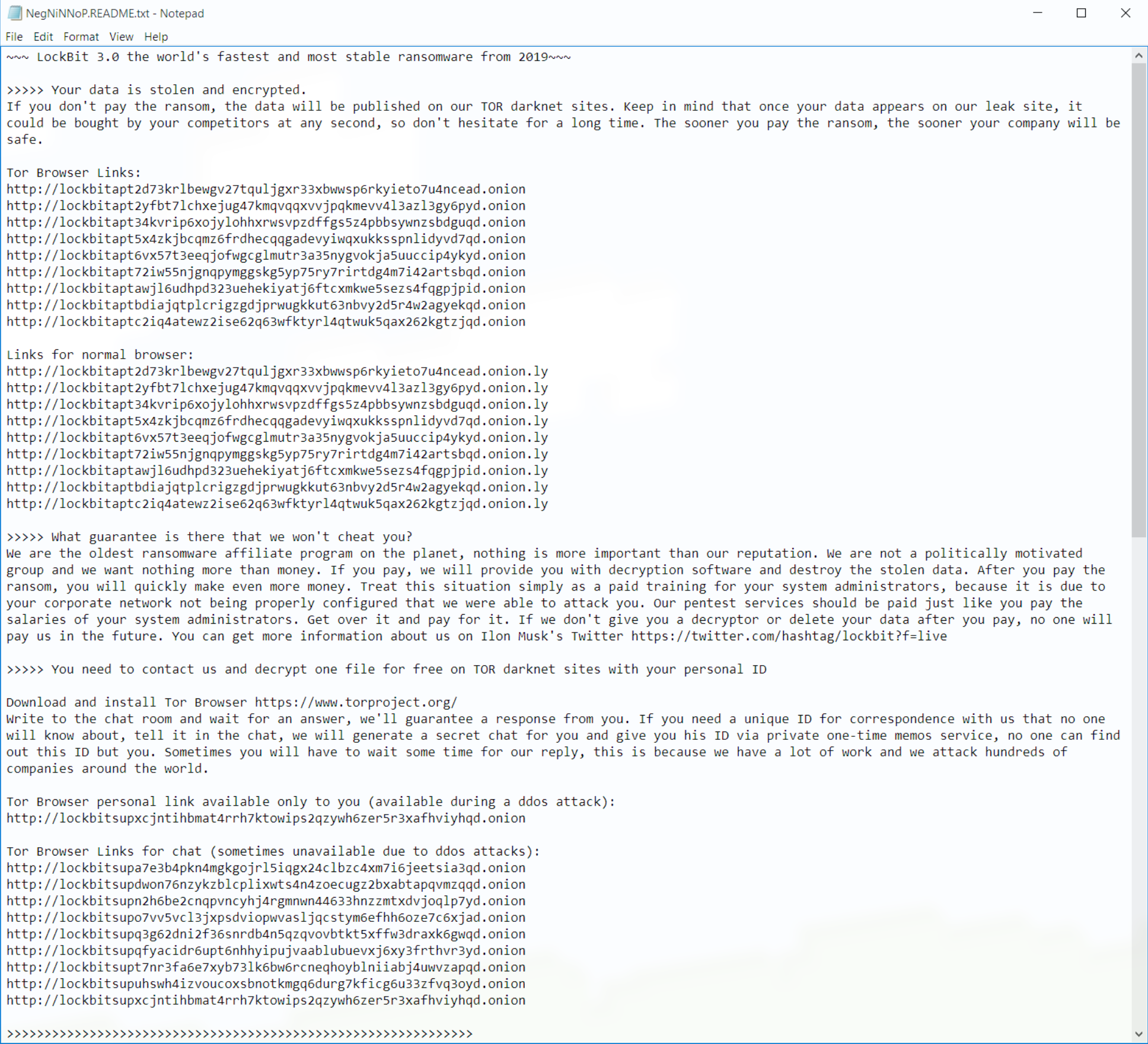
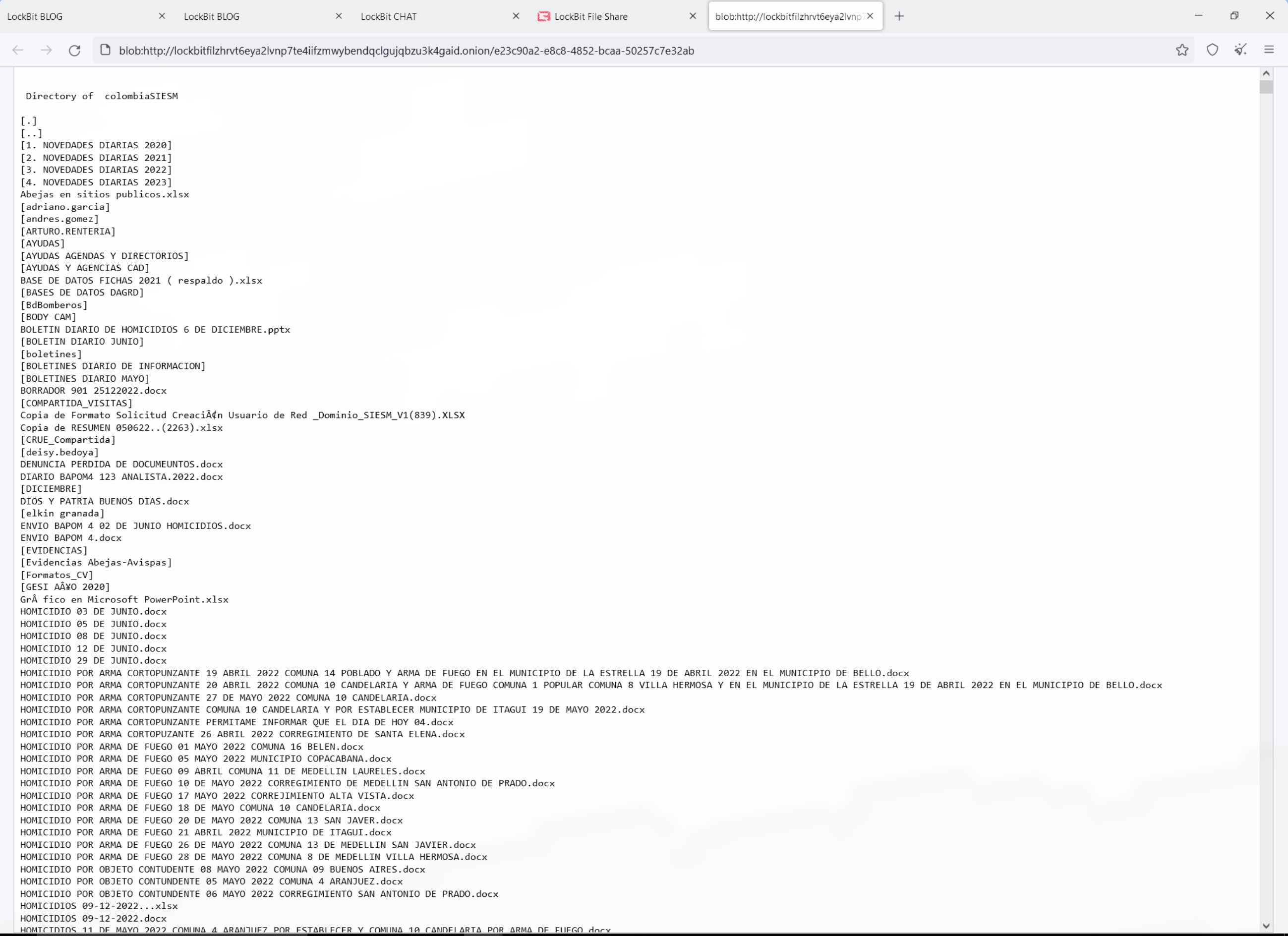
In industry news, Bleeping Computer reported on a grocery delivery service breach that affected over 1 million customers and a Canadian bookstore that suffered a major attack. Dark Reading told the tale of an ethical hacker gaining control of Toyota’s internal systems. Ransomware is running loose on an unpatched VMWare product according to Hacker News. IT Security Guru reported on an attack from the notorious LockBit ransomware gang that halted London stock trading.
Remember to keep your passwords close and your eyes peeled — cybersecurity is everyone’s responsibility.
SonicWall News
ITPro, SonicWall News: In 2020 – the third year of it being considered a major strain – security firm SonicWall revealed it was behind a third of ransomware attacks worldwide for the year.
GQ Brasil, SonicWall News: Arley Brogiato, director for Latin America and the Caribbean of the multinational security company SonicWall, does not exclude the possibility of these attacks reaching Brazilian companies, but says he is surprised by the alerts and the dissemination of the news, which on the morning of last Monday (6) competed with football game calendars and the price of cooking gas in Manaus the most sought after Google Trends.
SonicWall Blog, SonicWall News: SonicWall Chief Revenue Officer (CRO) Jason Carter and Vice President Americas Channel Sales Matt Brennan have been named to CRN’s 2023 Channel Chiefs list. Every year, CRN honors the IT channel executives who drive the channel success and evangelize the importance of channel partnerships within the IT industry.
TechToday, SonicWall News: According to a report by SonicWall, 2.8 billion malware attacks were registered, up 11% in the first half of 2022, marking the first increase in global malware volume in over three years.
Charged Retail, SonicWall News: The JD Sports incident is yet another example of the rise in cyberattack incidents, with the retail industry experiencing a 90% increase in ransomware attacks last year, according to a report from SonicWall.
Ask by Geeks, SonicWall News: One of the best small business firewalls is the SonicWall TZ400 Security Firewall. The SonicWall TZ400 NGFW Premium is considered a little more expensive than other firewall options, but its security, reliability, ease of use, and unique features justify its price.
ITPro, SonicWall News: A study last year by SonicWall found that the retail sector saw a 264% surge in ransomware attacks between February 2021 and 2022. The widespread consumer shift to online shopping during the pandemic prompted hackers to escalate attacks against online retailers.
Networking+, SonicWall News: The chances of being hit by a ransomware attack are more significant than ever. Last year, global ransomware volume skyrocketed by 105% year over year, according to the 2022 SonicWall Cyber Threat Report. While no industry was spared, the numbers were particularly gruesome for governments. Ransomware attempts on government entities rose a staggering 1,885%. That’s more than double the increase reported by healthcare (755%), education (152%), and retail (21%) combined.
CyberSecurityInsiders, SonicWall News: 2022 saw a shifting cybersecurity landscape as rising geopolitical conflicts brought new tactics, targets, and goals for cybercrime. According to recent threat intelligence from SonicWall, global ransomware attempts declined 31% YoY as cybercriminals and nation-state actors opted for never-before-seen malware variants, IoT malware, and cryptojacking in attacks motivated by financial gain and state-sponsored hacktivism.
MedTechDive, SonicWall News: Ransomware attacks in which cybercriminals attempt to extort money declined by 23% overall during the first half of 2022 but increased 328% in healthcare, according to data from cybersecurity company SonicWall.
TechTarget, SonicWall News: Logically’s MSSP offerings include extended detection and response, endpoint detection and response, and MDR; enterprise-level managed firewall services; and cybersecurity assessments, according to Skeens. The company runs a SOC. The company’s IT security technology partners include SonicWall.
iTWire, SonicWall News: iTWire really could go on and on; the list of features is almost endless. There is a database of applications for intelligent packet analysis, support for IoT devices, DNS protection, and more. However, the best thing right now is to take it for a spin yourself. You can demo the SonicWall NSsp series firewalls online without any installation or commitment and see all the features and benefits in action.
Strategic Risk, SonicWall News: There were 623 million ransomware attacks globally in 2021 according to Sonic wall, representing a 105% year on year increase. The UK saw a 228% surge and a 65% increase in never-seen-before malware.
Industry News
Weee! Grocery Service Discloses Data Breach Affecting Over 1 million Customers
The self-proclaimed largest Asian and Hispanic grocery delivery service in North America, Weee!, lost the personal data of 1.1 million customers in a recent breach. According to Bleeping Computer, a bad actor with the username ‘IntelBroker,’ began leaking data from Weee! on a data breach forum. The leak contained customers names, phone numbers, email addresses, device types, order notes and other data. Weee! does not retain customer payment information in their databases, so no customer payment data was lost. Weee! stated that they would notify all impacted customer individually if their information was exposed.
Cyberattack Disrupts London Stock Trading
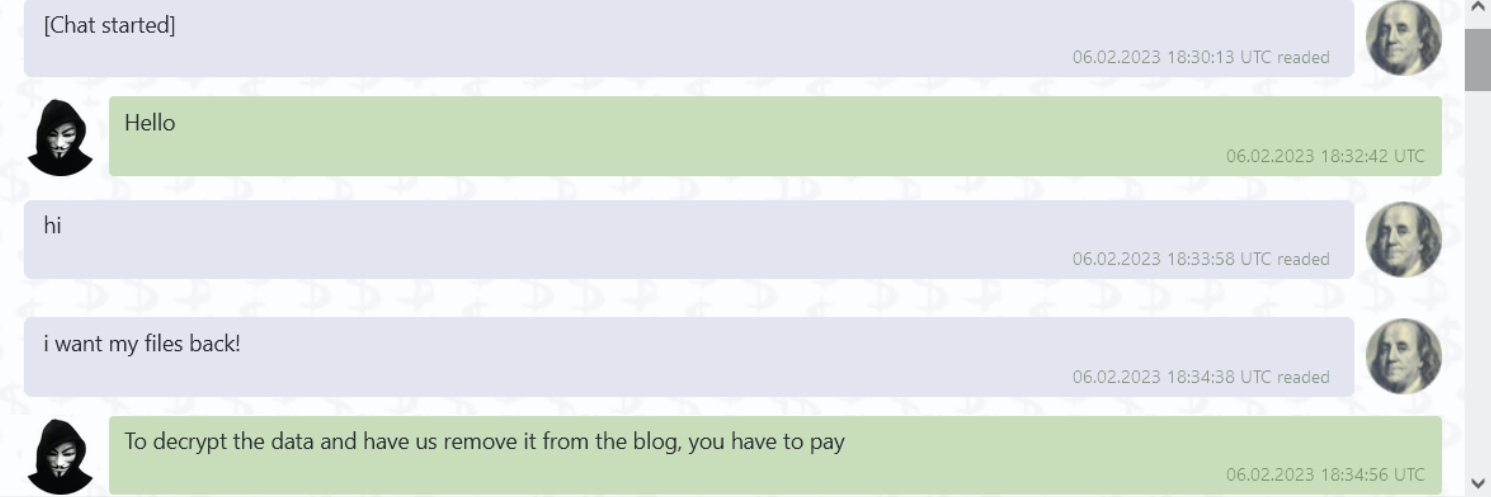
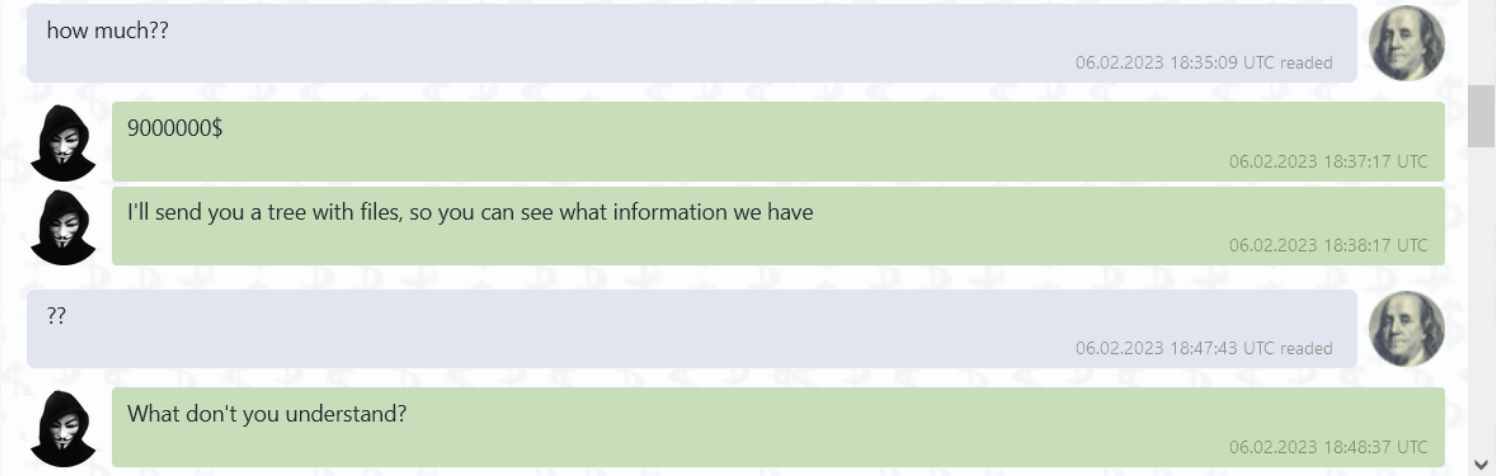
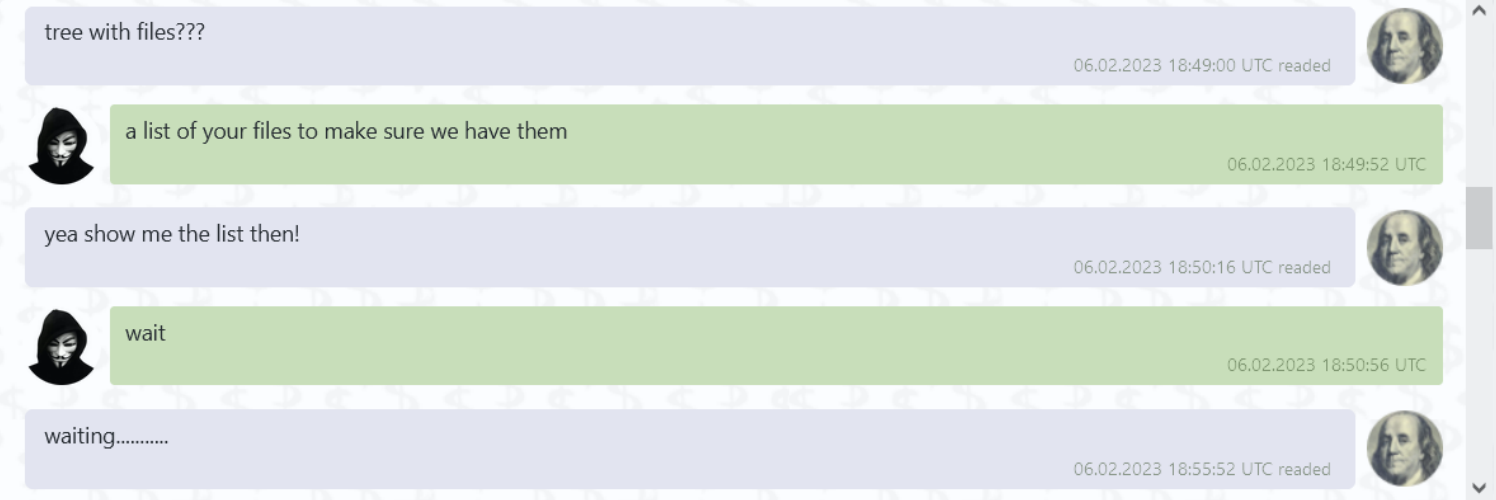
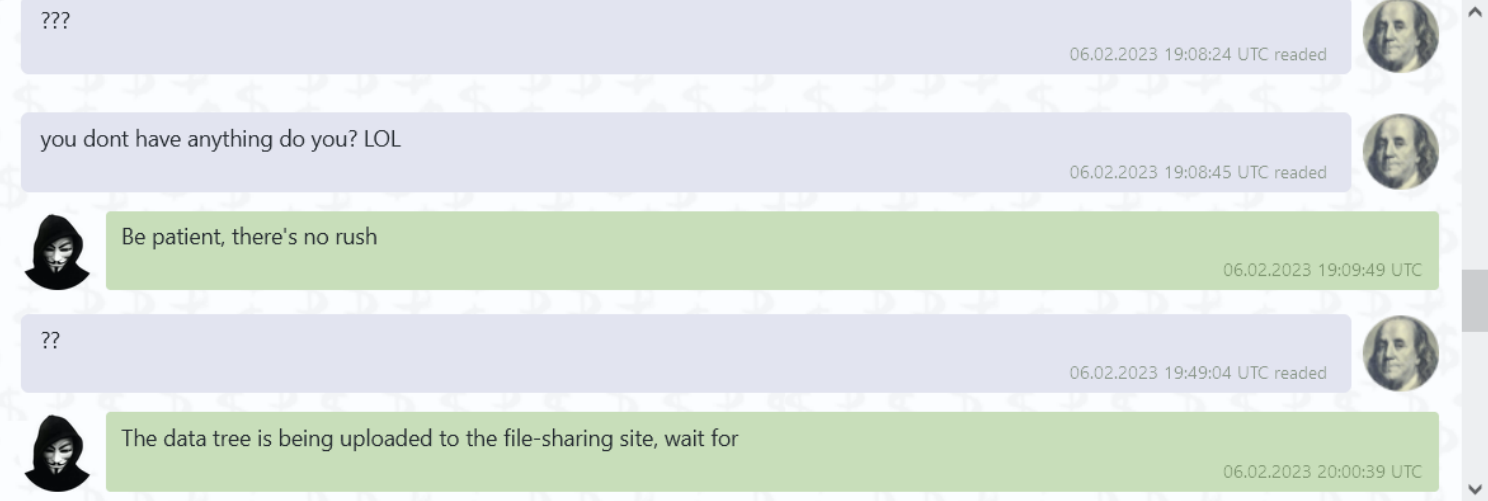
A ransomware attack brought London stock trading to a screeching halt last week. The ransomware group LockBit targeted Ion Markets in an attack. Ion Markets is a financial data group that supports a large amount of derivatives trading in the London market. According to IT Security Guru, 42 clients were affected by the attack. The attack even forced some groups to begin processing trades manually. LockBit allegedly used its signature ransomware attack which locks the victims out of accessing their data through encryption and leaves a note demanding payment. The company said all affected servers have been disconnected and they’re working to resolve the issue.
Hacker Gains SysAdmin Privileges to Toyota Through Portal Flaw
A web app for Toyota employees was broken into by an ethical hacker who simply knew the email address of one of the users. The security researcher revealed that he discovered the backdoor entrance into the app in October. In a blog post about the attack, he revealed that he was able to log in as any corporate user or supplier. He used that entryway to log in as a system administrator and therefore gain total control over the app. According to Dark Reading, he then had full access to internal projects, documents and user accounts. This is yet another sign that every business should be taking extra care with their cybersecurity. Toyota is lucky that this hacker was ethical.
Canadian Bookseller Goes Dark Following Cyberattack
The largest book retailer in Canada, Indigo Books & Music, shut down following a cyberattack. The retailer was forced to take its website offline and resort to cash only payments at its physical locations. The attack even made gift card purchases impossible. According to Bleeping Computer, it’s still unclear what type of attack the bookseller suffered. The retailer released a statement indicating they are working with a third party to determine the cause and resolve the situation.
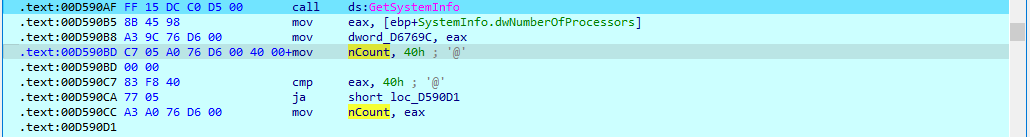
VMWare Bug Exploitation Attracts Ransomware Attacks
According to Hacker News, attacks focused on VMWare ESXi hypervisors are deploying ransomware on vulnerable systems. The attacks are targeting outdated software. A patch has been available since February 2021. The experts believe it can be traced to a Rust-based ransomware strain called ‘Nevada.’ VMWare recommends users update to the latest patch to avoid any issues.
SonicWall Blog
Can You Catch All the Phish? Take Our New Phishing IQ Quiz and Find Out! – Ken Dang
Celebrating 2023 With Expanded “3 & Free” – Matt Brennan
‘3 & Free’ Promotion: How to Upgrade to a New SonicWall TZ Series NGFW for Free – Matt Brennan
The Art of Cyber War: Sun Tzu and Cybersecurity – Ray Wyman
Talking Boundless Cybersecurity at the Schoolscape IT 2022 Conference – Mohamed Abdallah
3 & Free: 1 Amazing Deal, 2 Exceptional Firewalls, 3 Years of Superior Threat Protection – Matt Brennan
SonicWall Wins CRN’s 2022 Tech Innovator Award in Enterprise Network Security – Bret Fitzgerald
SonicWall Included on the Acclaimed CRN Edge Computing 100 List for 2022 – Bret Fitzgerald
A New Era of Partnering to Win – Robert (Bob) VanKirk
Multiply Your Security with Multifactor Authentication – Amber Wolff
10 Reasons to Upgrade to the Latest SonicWall Gen 7 TZ Firewall – Sarah Choi