OpenSSL SSL/TLS MITM vulnerability (June 6, 2014)
Since the OpenSSL Heartbleed vulnerability (CVE-2014-0160) was released on April 7th, everyone talked about how to prevent similar bugs, and the existing code has been scrutinized more often. On June 5th, OpenSSL released a security advisory covering six vulnerabilities. Among them, SSL/TLS MITM vulnerability (CVE-2014-0224) is rated as the most important one.
This MITM vulnerability affects OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h. The vulnerable code in these versions of OpenSSL does not properly restrict processing of ChangeCipherSpec messages, which allows man-in-the-middle attackers to trigger use of a zero-length master key in certain OpenSSL-to-OpenSSL communications, and consequently hijack sessions or obtain sensitive information.
The patch to this vulnerability has been released on Fri, May 16th 2014. It correctly checks when to accept the CCS message. The following code snippet sets the new SSL3_FLAGS_CCS_OK flag in order to achieve this:
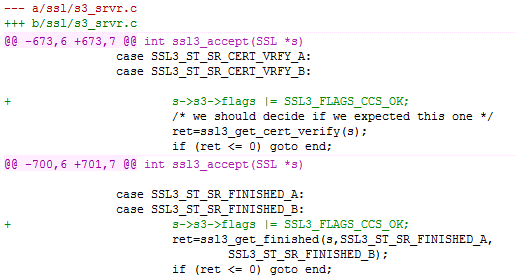
And the following code tests the flag before processing the CCS message:

To eliminate the vulnerabilities, please upgrade to the following versions accordingly:
- OpenSSL 0.9.8 SSL/TLS users (client and/or server) should upgrade to 0.9.8za.
- OpenSSL 1.0.0 SSL/TLS users (client and/or server) should upgrade to 1.0.0m.
- OpenSSL 1.0.1 SSL/TLS users (client and/or server) should upgrade to 1.0.1h.
Dell SonicWALL has researched this vulnerability and released the following IPS signature to protect their customers:
- IPS: 10386 Excessive SSL Change Cipher Spec Messages.
Dell SonicWALL has also released another IPS signature to cover DTLS invalid fragment vulnerability (CVE-2014-0195).
- IPS: 10387 OpenSSL DTLS Fragmentation DoS



