Houdini and jRat Trojans found double teaming in the wild
The Sonicwall Capture Labs Research team has come across a spam campaign distributing not just one but two Remote Access Trojans (RATs). Both RATs have historically been seen propagated through spam independently as an email attachment in a variety of forms such as benign looking shipment notification, payment notice, receipts, invoices, statements or quotations. This time, the propagation method was not any different.
Infection cycle:
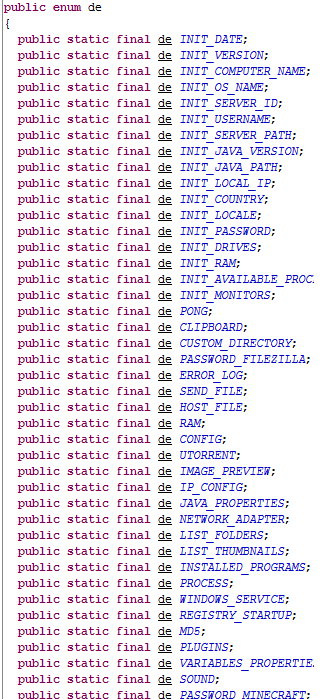
The main installer file comes as an email attachment in a Java archive file format (JAR). Once executed,it will drop two remote access Trojans – Houdini and jRat. During our analysis it created the following files in the %APPDATA% and %USERS% directories.
- %APPDATA% /microsoftkey.jar [Detected as GAV: jRat.A_3 (Trojan)]
- %APPDATA% /ntfsmgr.jar [Detected as GAV: jRat.A_2 (Trojan)]
- %APPDATA% /fifpdvUqdn.vbs [Detected as GAV: Houdini.VBS (Trojan)]
- %USERS% /nixfeknwve.vbs [Detected as GAV: Houdini.VBS (Trojan)]
The two Trojans are then executed simultaneously using javaw.exe and wscript.exe. The following registry keys were also added to ensure persistence for both Trojans and will allow them to run after each reboot:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run fifpdvUqdn exe //B “%APPDATA%\fifpdvUqdn.vbs”
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run ntfsmgr “C:\Program Files\Java\jre7\bin\javaw.exe” -jar “%APPDATA%\ntfsmgr.jar”
The jRAT components are easily identified by directory names – “blaz42” and “qt314” which contains class files.
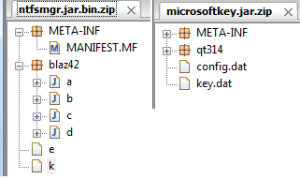
In our example ntfsmgr.jar is the main file which then drops the secondary jar file – microsoftkey.jar. They contain several classes that are platform-specific implementations of the malware capabilities with the screenshot below showing supported platforms.
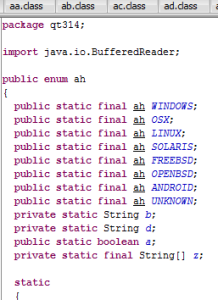
And below is a list of its functionalities which include playing sound/audio, sending files to remote servers, examining the victim’s network configurations, running arbitrary commands, image capturing, stealing passwords, etc.
While Houdini is a base64-encoded VB script that when decoded reveals the name “Houdini” within its code.
Upon execution it connects to a remote server goz.unknowncrypter.com.
![]()
Some of the sub function names within the script gives us a picture of this Trojan’s capabilities:
- Information – operating system information gathering, get volume serial number
- Site-send – send data to remote server
- Cmd – execute commands using cmd.exe
- Enumprocess – list all running processes
- Uninstall – delete registry keys and delete files
- Security – get OS version and security center info
- Fileurl/filedir – http download and save file
- Upload – send post data using http
- set objwmiservice
SonicWall Capture Labs provide protection against this threat via the following signatures:
- GAV: jRat.A_2 (Trojan)
- GAV: jRat.A_3 (Trojan)
- GAV: Houdini.VBS(Trojan)