OpenSSL OBJ_obj2txt Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
OpenSSL stands as a renowned open-source library, primarily utilized for SSL and TLS. The Secure Socket Layer (SSL) and the Transport Layer Security (TLS), referenced interchangeably from this point onward, are cryptographic protocols designed to ensure communication security, data integrity, and authentication over TCP/IP networks. By harnessing the power of cryptography primitives—symmetric key ciphers, cryptographically robust hash functions, and the Public Key Infrastructure (PKI)—these protocols facilitate secure communication between hosts over unsecured networks.
PKI, a prevalent authentication system for TLS, is dependent on certificates for conveying necessary cryptographic data, such as RSA keys, signatures, and identity information, all vital for encryption and authentication. The ITU standard, X.509, details the structure of these public-key certificates.
There are three existing versions of X.509: X.509 v1 and v3 are older and newer standards, respectively, utilized for certificate representation. Conversely, X.509 v2 outlines the standard for representing Certificate Revocation Lists (CRLs). These certificate representations are outlined using Abstract Syntax Notation One (ASN.1) and encoded via the Distinguished Encoding Rules (DER).
Recently, a denial-of-service vulnerability has been discovered in the OpenSSL library. This vulnerability emanates from delays encountered during the processing of ASN.1 OBJECT IDENTIFIERs.
A remote attacker can exploit this vulnerability by transmitting specially crafted packets to an OpenSSL client, or a server that has purposefully activated client authentication. Should this exploitation prove successful, it could instigate denial-of-service conditions on the impacted service.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-2650.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 4.6 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L/E:U/RL:O/RC:C).
Base score is 5.3 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:L), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is none.
• Impact of this vulnerability on data integrity is none.
• Impact of this vulnerability on data availability is low.
Temporal score is 4.6 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
It’s important to shed light on the OBJECT IDENTIFIER tag and its workings. The OBJECT IDENTIFIER data type, encoded into a TLV (Type, Length, Value) triplet, commences with a Tag value of 0x06. The encoding of each integer in a dotted decimal object identifier (OID) is governed by a set of specific rules. First and foremost, the OID’s initial two nodes are encoded onto a solitary byte, with the first node being multiplied by the decimal 40 and the result is added to the second node’s value. Secondly, node values that are either equal to or less than 127 are encoded on a single byte. Lastly, node values that are equal to or exceed 128 are encoded on multiple bytes, with Bit 7 of the leftmost byte set to one and Bits 0 through 6 of each byte containing the encoded value.
For illustration, consider the OBJECT IDENTIFIER “1.3.6.1.4.1.311.21.20”. It would be encoded as follows: “06 09 2b 06 01 04 01 82 37 15 14”. Here, “06” stands for the OBJECT IDENTIFIER tag, “09” represents the length of the OBJECT IDENTIFIER, and the subsequent bytes are the encoded values, utilizing the previously mentioned three rules.
OpenSSL library incorporates support for parsing ASN.1 encoded OBJECT IDENTIFIER in DER format. More specifically, it provides an API known as OBJ_obj2txt() for data parsing. This function commences decoding from the first byte, interpreted as the two initial sub-identifiers, as per Rule 1. Post this, the function scrutinizes each byte of the remaining encoded data in a while loop. The value will be directly regarded as the decimal sub-identifier if it’s less than 0x80 (128), aligning with Rule 2. If the value equals or exceeds 0x80, the function discards Bit 7, storing only the left 7 bits (Bits 6 – 0), and repeats this step in a for loop until a byte less than 0x80 is encountered. The function then concatenates all the lower 7 bits in these bytes and converts the bit stream into an integer. This integer’s decimal value will be the sub-identifier. Nevertheless, this function does not impose restrictions on the length of the encoded OBJECT IDENTIFIER data. Consequently, the decoding step could be extensively time-consuming if the concatenated value forms a large integer.
Triggering the Problem:
• The target must be running a vulnerable version of the affected product.
• The attacker must have the ability to delivery a malicious ASN.1 DER file to the target
Triggering Conditions:
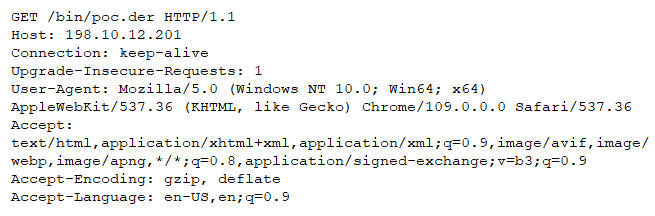
The vulnerability can be exploited if the attacker successfully delivers a malicious certificate or any other file in DER format to applications utilizing the OpenSSL library. The vulnerability is subsequently triggered upon the parsing of this malicious file, establishing a potential security risk for the system.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• FTP
• HTTP
• HTTPS
• IMAP
• NFS
• POP3
• SMB/CIFS
• SMTP
• ESMTP
• SIPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS:19207 OpenSSL OBJ_obj2txt Function DoS
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Apply the vendor-provided patch to eliminate the vulnerability.
• Filter attack traffic using the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory