Hackers Now Attacking Unconfigured WordPress Sites
SonicWall Threat Research Labs recently received reports of attackers targeting newly installed WordPress sites. Attackers search for the following phrases:
- WordPress
- Setup Configuration File
If both phrases exist, then it is possible that the site has WordPress installed but has not been configured properly. In fact, doing a Google search for the above, results in:

After checking the first results returned by Google, we found 4 to unconfigured.
Typically, most of these sites returned show the following:
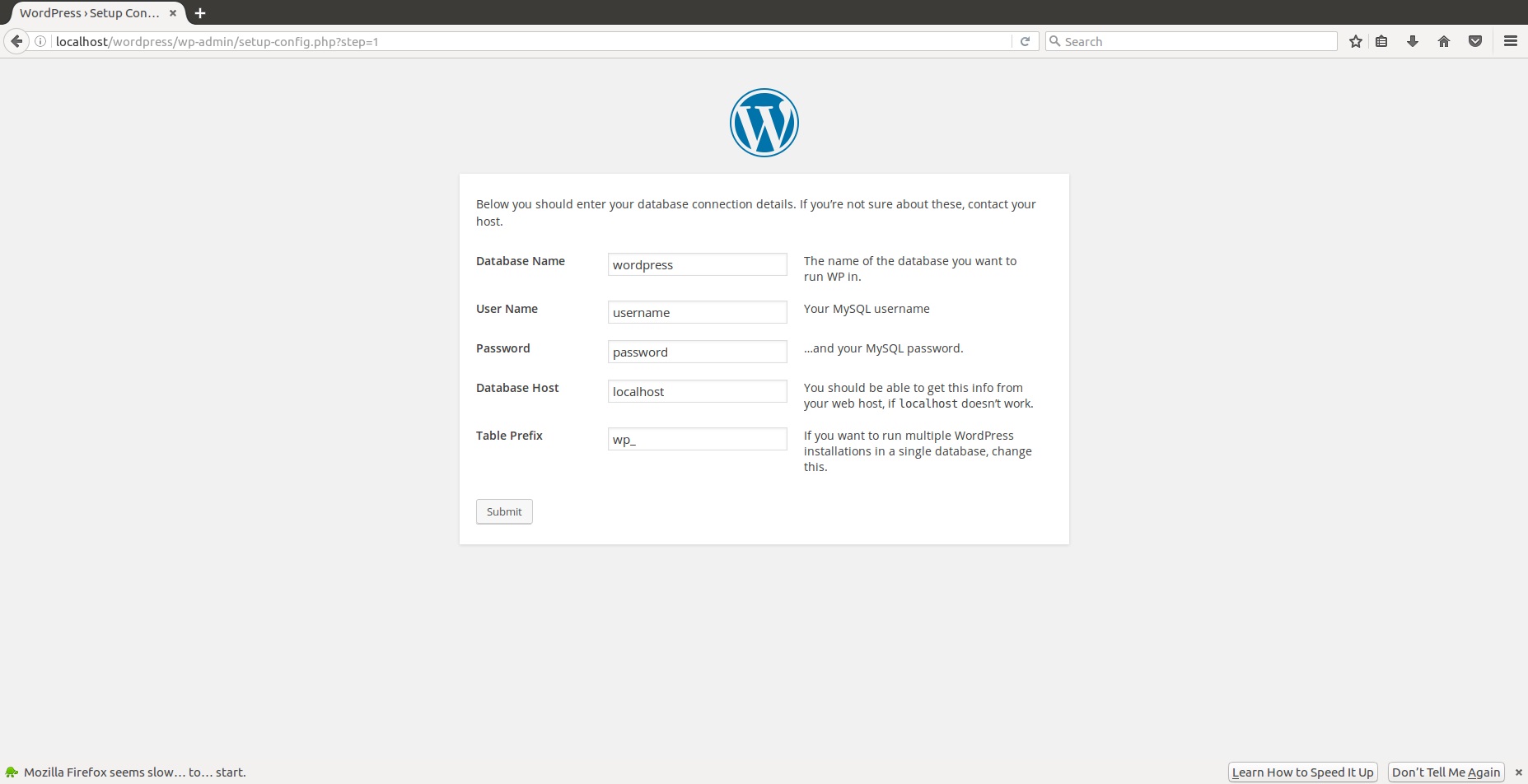
From the above, we can see that the attacker can specify any database they have control over.
The next step the attacker does is to set the first level admin account

Once the attacker has control over the WordPress website running in the target server, the attacker can do any of the following:
- Use the WordPress website for hosting malware, exploit kits, etc.
- Use the WordPress website as a launching pad to attempt control of the server. This can be done by executing specially crafted PHP scripts.
SonicWall Threat Research Team has the following signature to protect their customers from this type of attack:
- WAF 1666: WordPress Setup Attack





