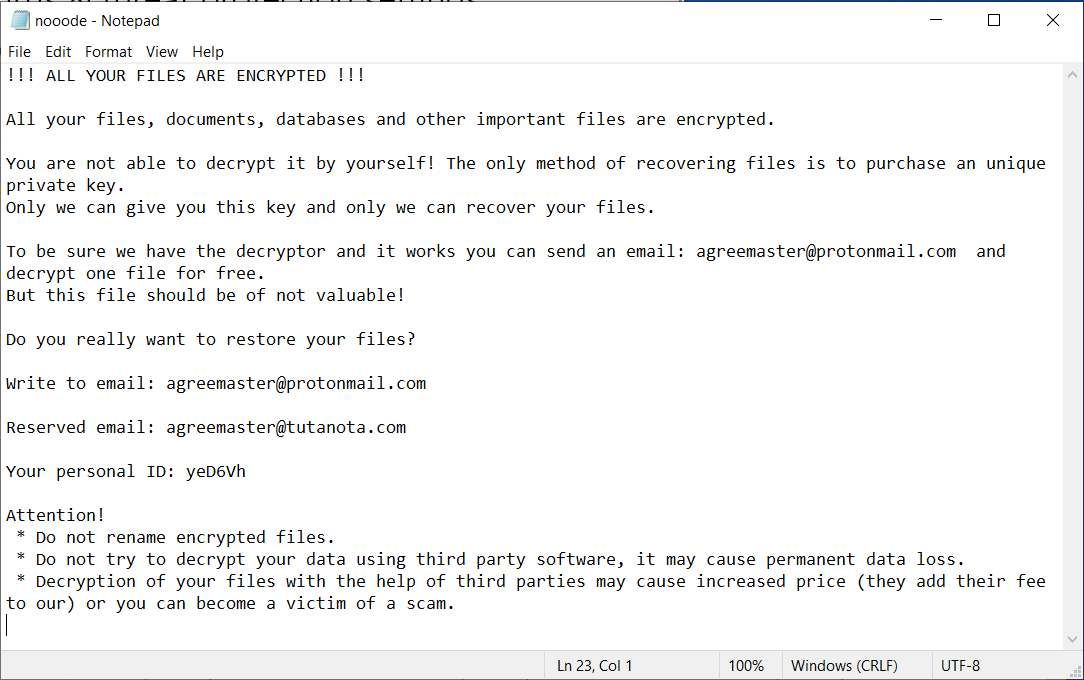
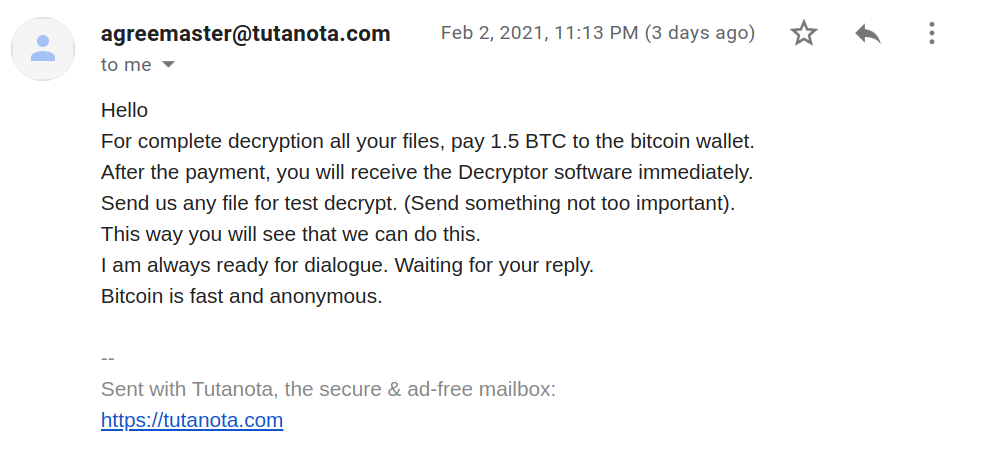
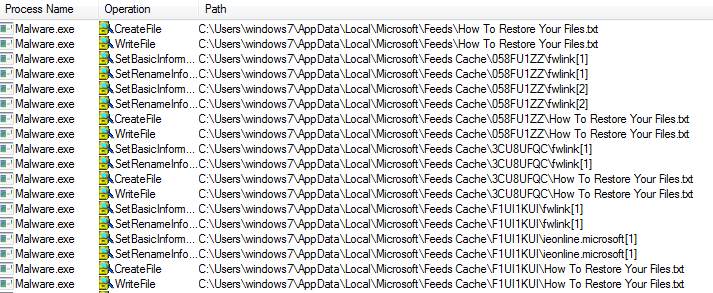
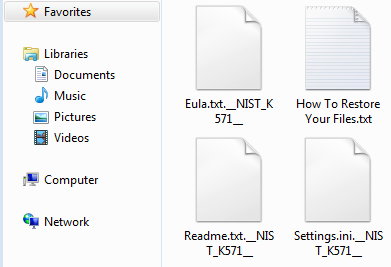
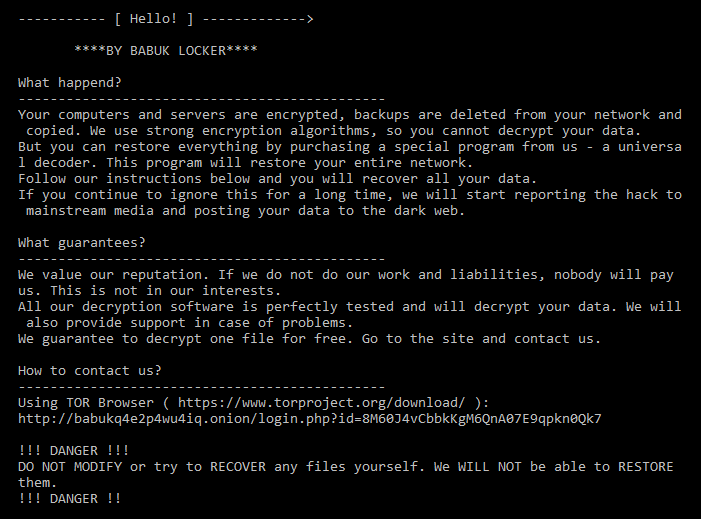
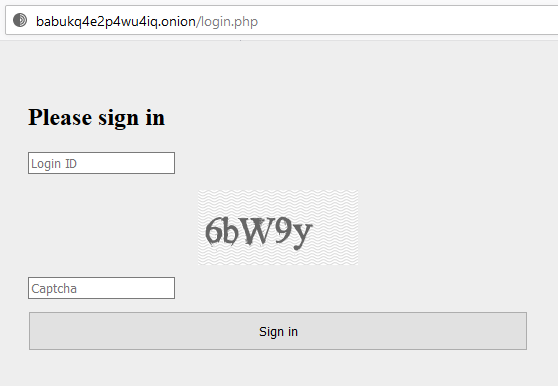
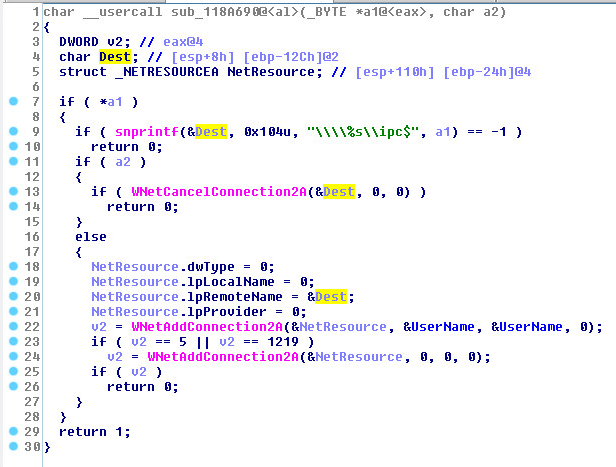
SonicWall Capture Labs Threat Research team has observed hackers actively targeting the recent remote code execution vulnerability in the Apache Struts framework.
This vulnerability is due to insufficient input validation, leading to a forced double OGNL evaluation when evaluating raw user input. A remote attacker could exploit this vulnerability by sending a crafted request to the target server. Successful exploitation will allow an attacker to execute arbitrary code with the privileges of the server.
Apache Struts:
Apache Struts is a modern Java framework that uses the Model, View, Controller (MVC) architecture for building enterprise-ready web applications.
Model – The central component, which manages the data, logic, and rules of the application.
View – Presents information to the user, sometimes allowing multiple views of the same information.
Controller – Accepts input and converts it to commands for the model or view.

Object-Graph Navigation Language (OGNL) is an open-source expression language for Java, which, while using simpler expressions than the full range of those supported by the Java language, allows getting and setting propertiesproperties as well as execution of methods of Java classes.
OGNL uses Java reflection and inspection to address the Object Graph of the runtime application. This allows the program to change behavior based on the state of the object graph instead of relying on compile-time settings. It also allows changes to the object graph.
Due to its ability to create or change executable code, OGNL is capable of introducing critical security flaws to any framework that uses it.
Vulnerability | CVE-2020-17530 :
The OGNL context map is initialized with the mitigating controls that enforce the validations for accessing
packages, classes, and their normally private/ or protected methods/fields. These controls are defined by an instance
of the SecurityMemberAccess class. Similarly, by leveraging introspection via the BeanMap instance, private
properties of the SecurityMemberAccess instance can be accessed and modified. Most importantly excludedClasses and excludedPackageNames containing the set of excluded classes and package names
respectively can be cleared and thus effectively disabling every class and package access restriction.
An attacker is therefore able to completely disable all OGNL expression mitigation controls related to package and
class access. Arbitrary code execution can eventually be realized by invoking suitable methods from previously disallowed classes, for example, Execute.exec() method from “freemarker.template.utility package”.
Exploit:
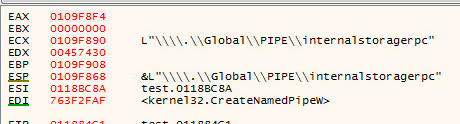
SonicWall observed the below exploit request in which the BeanMap instance has been leveraged to access and modify the member access and set excludedClasses and excludedPackageNames to empty. One of the disallowed classes “Execute” from the “freemarker.template.utility” package that gives FreeMarker the ability to execute external commands is called to download and execute a malicious file.
Successful exploitation results in the execution of malicious payload “ssa” with the privileges of the server.
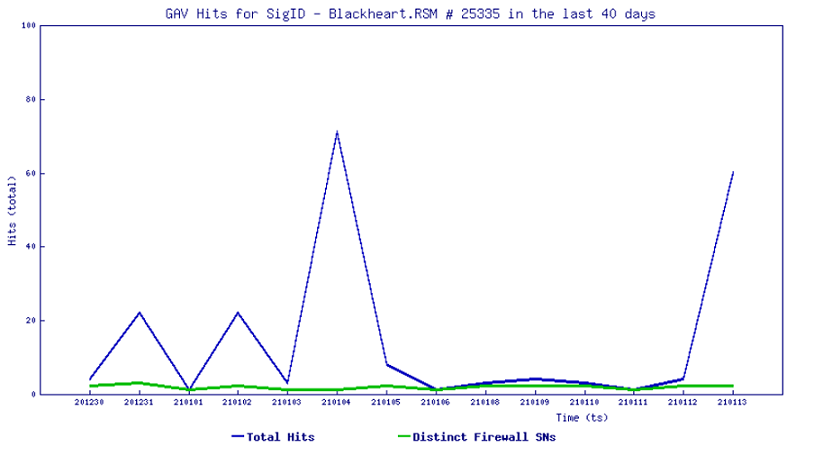
Trend Chart:
IPS hits for the signature “14514” in the last 40 days.

SonicWall Capture Labs Threat Research team protects against this exploit with the following signature:
IPS: 14514 Apache Struts OGNL Wildcard Remote Code Execution 8
Problem:
Some of the tag’s attributes could perform a double evaluation if a developer applied forced OGNL evaluation by using the %{...} syntax. Using forced OGNL evaluation on untrusted user input can lead to a Remote Code Execution and security degradation.
Affected Products:
Apache Software Foundation Struts 2.0.0 through 2.5.25
Fix:
Avoid using forced OGNL evaluation on untrusted user input, and/or upgrade to Struts 2.5.26, which checks to ensure that expression evaluation won’t lead to the double evaluation.
IOC (Attacker IP’s):
45.146.164.15
67.202.216.194
209.141.33.226
183.57.18.186
167.98.184.6
34.227.121.223
65.124.187.154
107.152.127.190
74.120.44.66
70.98.52.141
144.121.77.34
162.43.198.100
24.173.20.130
192.0.100.121
203.199.72.210
70.102.106.66
34.205.208.125
52.17.98.131
64.19.77.134
205.250.171.58
207.99.76.20
208.105.178.30
64.39.99.230
184.71.110.118
64.39.99.197
64.39.99.246
54.88.149.100
69.193.159.2
204.141.21.156
61.160.215.21
50.239.218.222
71.164.82.98
64.141.27.66
68.118.118.226
128.177.30.162
107.130.178.41
209.141.61.233
64.39.111.60
138.197.142.180
62.8.108.89
64.139.53.114
38.140.141.210
10.100.6.180
24.103.47.50
91.216.32.25
216.235.247.146
50.202.87.195
196.46.54.18
64.39.99.70
64.39.99.13
64.39.99.74
172.30.131.7
64.39.108.132
64.39.99.58
216.171.185.30
64.39.99.69
64.39.99.213
192.168.21.220
64.39.99.252
64.39.99.65
64.39.99.251
198.46.104.42
64.39.108.51
209.53.168.82
64.39.99.61
64.39.99.93
154.59.121.145
207.207.37.172
64.39.99.247
50.235.254.58
64.39.99.233
74.62.85.138
64.39.99.226
187.44.110.185
64.39.99.243
64.39.108.47
64.39.99.210
204.186.244.226
64.39.99.94
23.30.178.61
64.39.108.38
203.71.63.9
64.39.99.92
154.59.121.144
81.82.218.18
96.66.66.65
64.39.99.112
64.39.99.17
64.39.99.235
64.39.99.52
167.98.182.132
64.39.99.64
64.39.99.231
64.39.108.129
192.248.233.26
91.216.32.24
172.31.48.102
118.163.176.200
204.14.69.210
161.11.129.109