Excel with misleading macrosheet name spreading Zloader
SonicWall Capture Labs Threats Research team has been observing modifications in the techniques being used to distribute ZLoader using MS-Excel file. It all began around Jan 2020, when the first campaign was seen using XLM macro instead of the commonly used VBA macro. Since then, we have observed significant improvements like addition of evasion and sandbox bypassing techniques through XLM macro as already described in our previous blog.
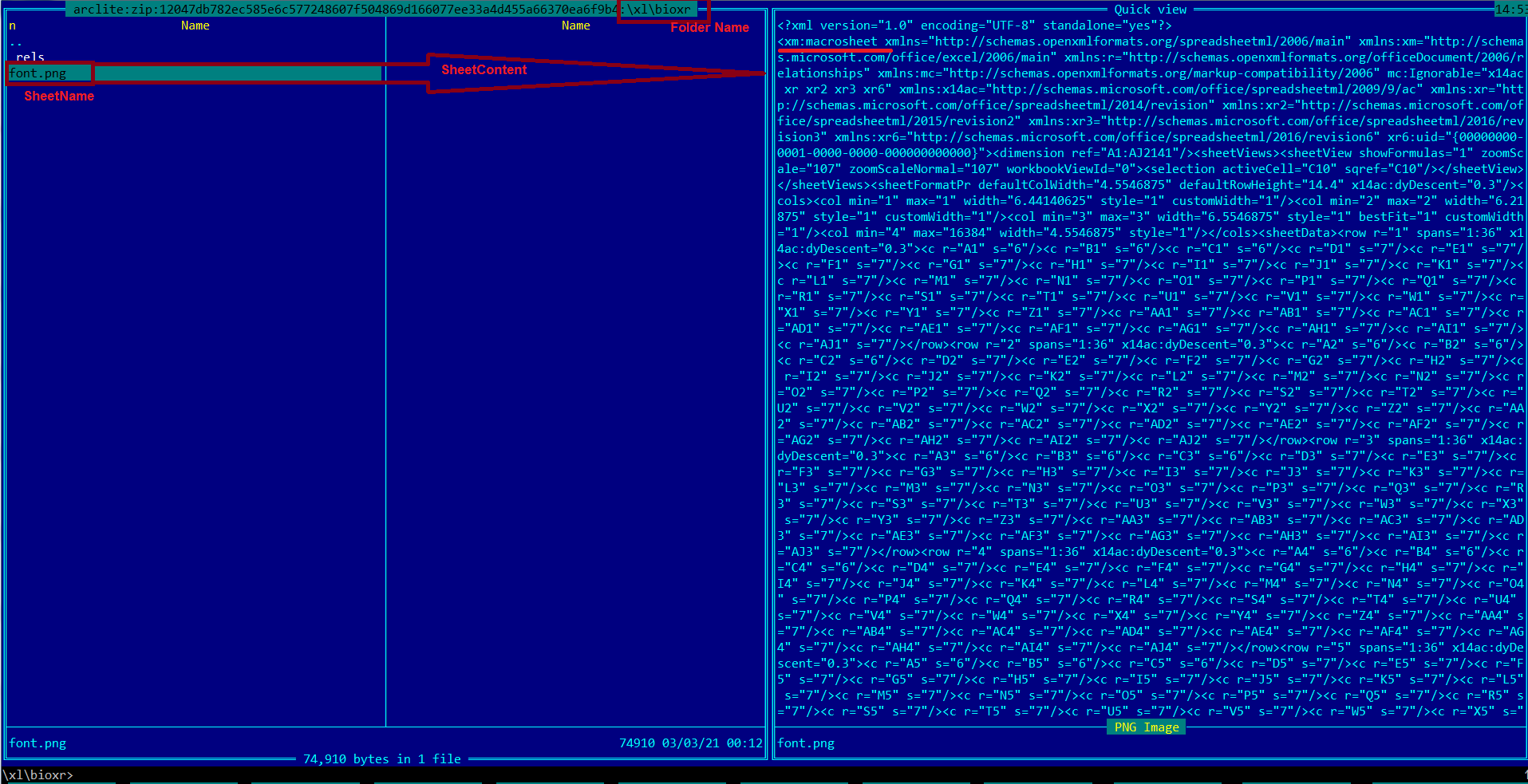
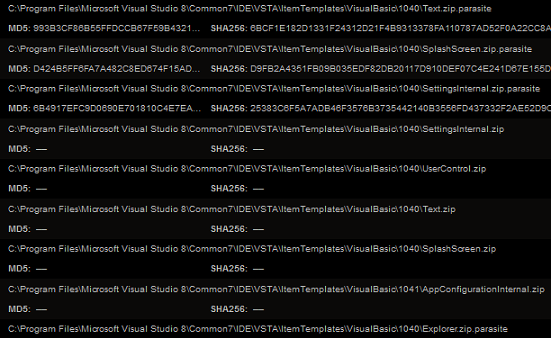
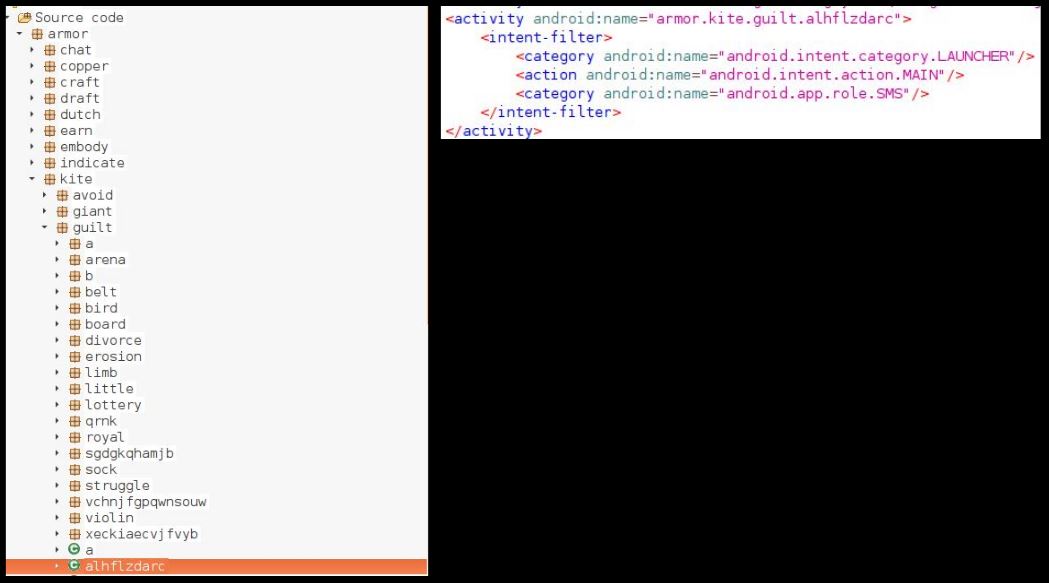
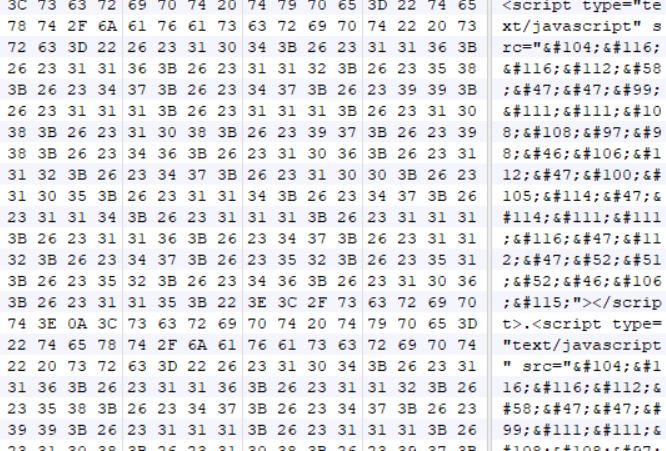
This variant uses OOXML format based MS-Excel file. In the OOXML format based MS-Excel file, usually the XLM macro sheets are stored inside “macrosheets” folder. The sheets are named either “Sheet<digit>.xml” or “intlsheet<digit>.xml”. This variant uses a completely different folder and file name to store macro sheet. The macro sheet and folder are named “foto.png” and “bioxr” respectively, as shown in the below image:
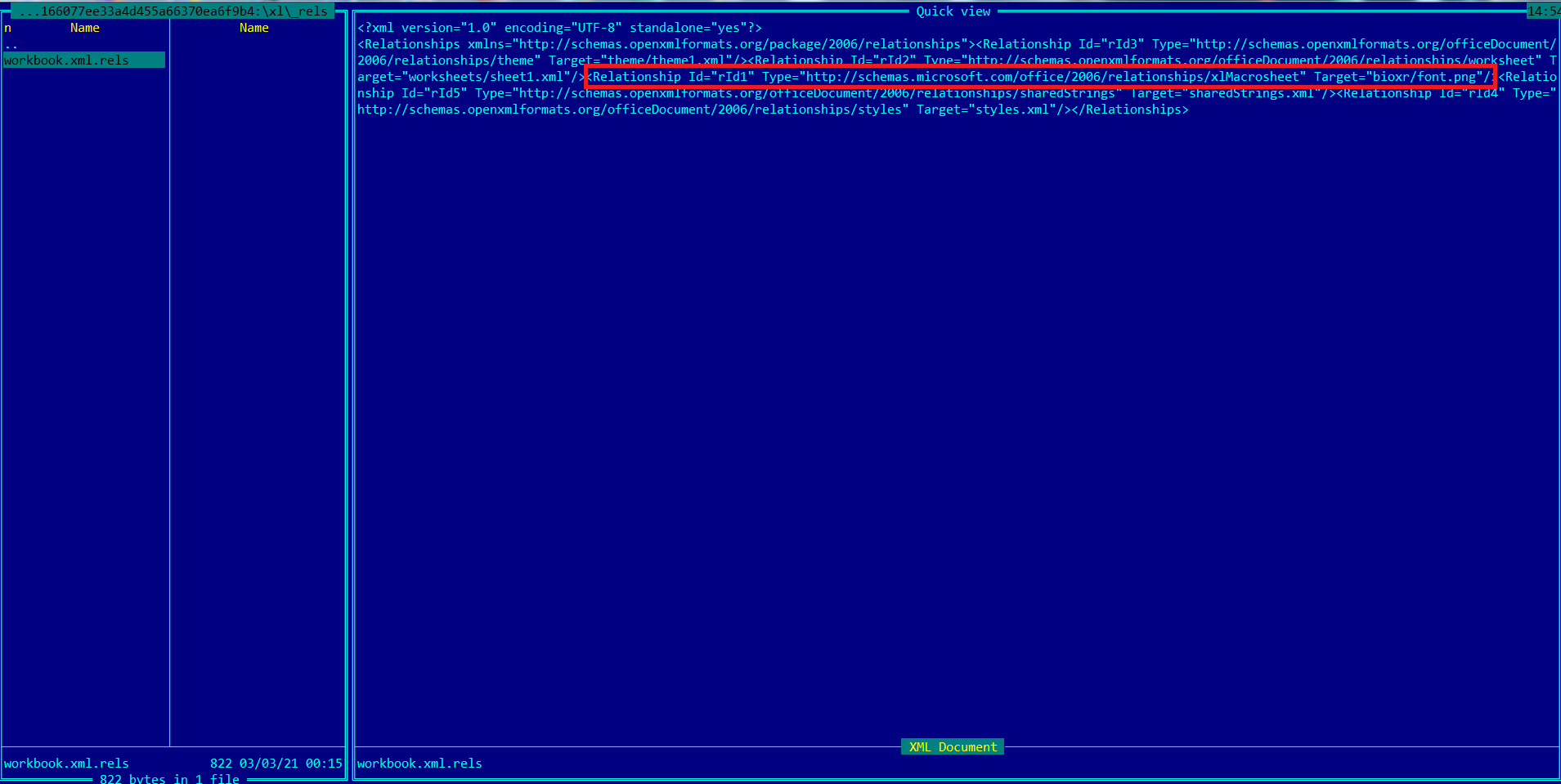
Engines looking for macro sheets specifically inside “macrosheets” folder might fail to identify these files as XLM based Macro files. After careful inspection of the “workbook.xml.rels” file, we found that both the folder and the file name for the macro sheet are misleading as shown below:
Sample Analysis:
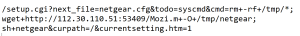
Upon opening the file, the user is displayed instructions to enable macro as shown below:
The sample contains two sheets, one is a hidden macro sheet. It has a defined name “Aut0_Open”, which enables macro execution as soon as the file is opened. Font size in the sheet is kept small ( “2”) to inhibit reading of the content.
Upon execution of XLM macro, payload belonging to Zloader family is downloaded and saved as C:\<random>\<random>\ServApi.exe
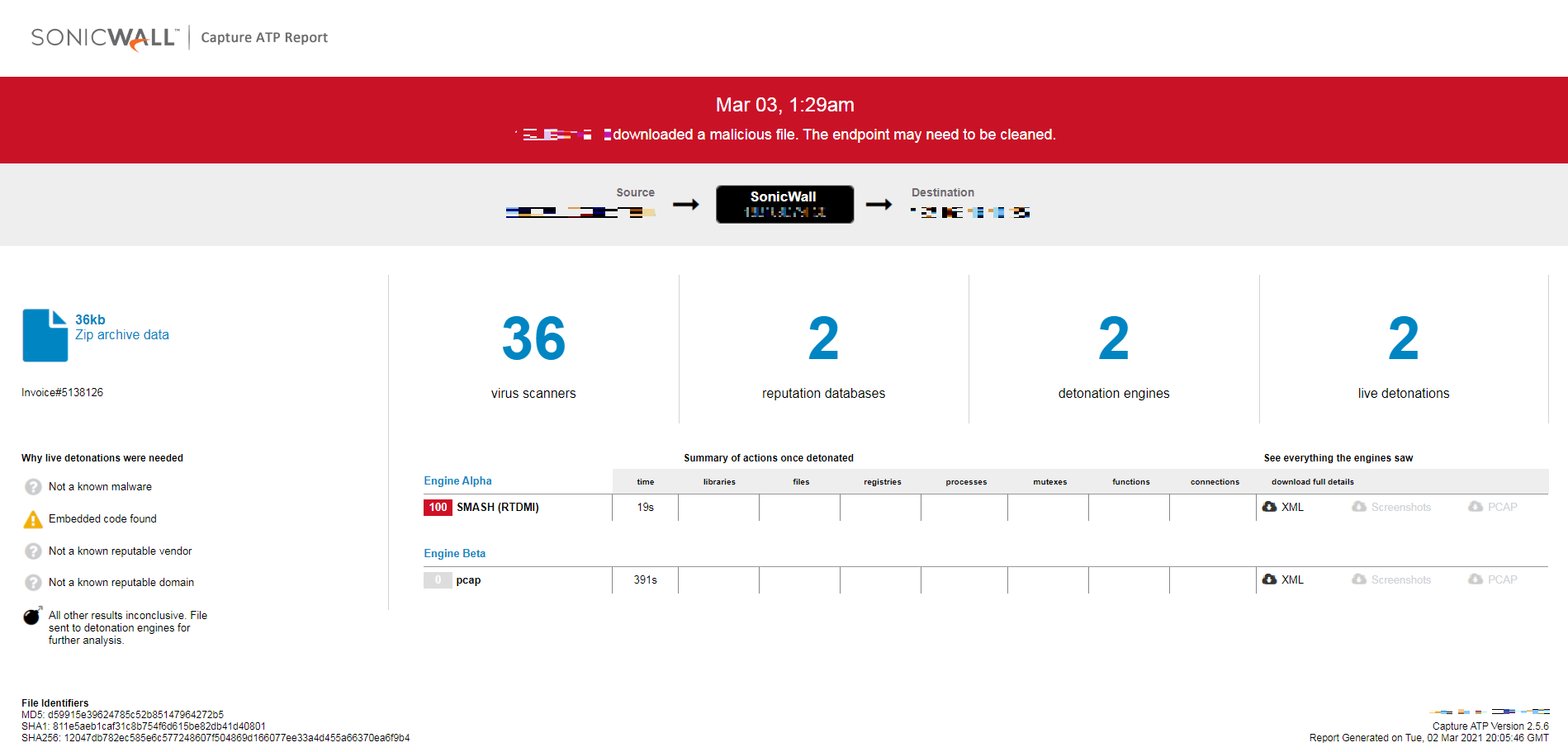
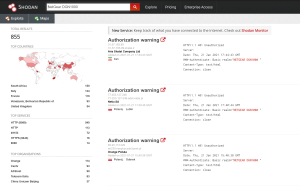
SonicWall Capture ATP protects against this threat as shown below:
Indicators of Compromise:
SHA256 of malicious Excel Files:
- 12047db782ec585e6c577248607f504869d166077ee33a4d455a66370ea6f9b4
- 189735e1fde7511cd9cedfb317f544971411691192c25ca36147998e492753d7
- 18d1cc06d96c741e0c21c1ceea194f37ca5941264cc0a26d89cba8e09c132485
- 18e6f2976642ca37a4e81358ea8da608b5d34a50b1954d0c3041e902ae23e192
- 18f33627843309fdef93e7edc7c24c856912d19a9622c2647165247e1aa16386
- 1a03a110254fe594cb08e5db44b5dd7d00ebedf5bf6944e2aff7807195b7bff6
- 1b29453e458e36c8b8b17371d4cb254a7cea4f1b035dc2d308e75ca1829766f3
- 20af190130ad3ac40a01df57341929d968616ef717bc9e691308ccaf4f41a683
- 211eb2bbaf1e1dcadd3f10c6c77ff2243f8690b1cd9f9dd5218d48d1b4edd02e
- 224b3303d4f32bc71fa3322d9385d004293459ed74885179178d04c880dbf6f8
- 2335e54b766bf5dc2a9078b995a4878ff350aa39d83ef7eabe77433c5c26e998
Network Connection:
- safedot[.]digital
- Domain registred on 25-Feb-2021
Files:
- C:\<random>\<random>\ServApi.exe