Multi-Stage Chinese Trojan Records Everything, Even Sounds
Overview
This week the SonicWall Capture Labs threat research team investigated a sample of malware that has multiple infostealer, monitoring and C2 capabilities. The name of the file is translated as ‘Easy Language Program’ from Chinese, and it has two embedded payloads that are only accessible once a variety of system, language and time zone checks have been passed.
Infection Cycle
The original sample is packed with NsPack, which hinders static analysis. Normally, this format can be unpacked with relative ease, but due to certain unknown changes made, the sample had to be manually extracted from memory while being debugged.
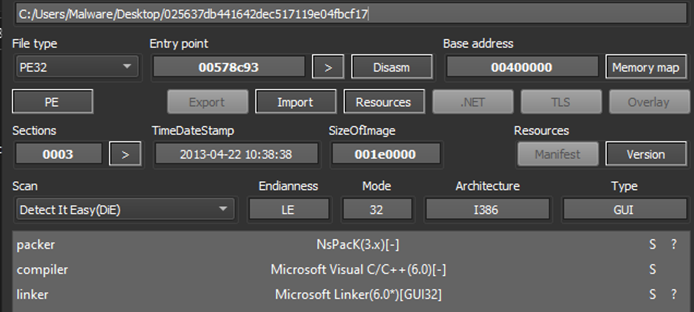
Figure 1: Original sample detection
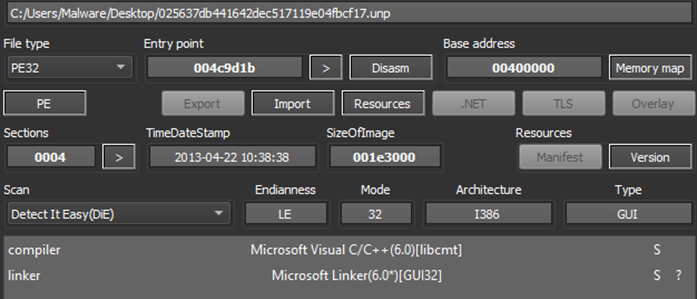
Figure 2: Unpacked sample detection
When the file is run, there is no window or visible activity. It will attempt to establish the correct environment by collecting information in the following ways:
- Location via GetSystemLocale, GetTimeZoneInformation, GetLocalTime, FileTimeToLocalTime, FileTimeToSystemTime
- Debuggers via IsDebuggerPresent, OutputDebugString, GetTickCount, GetEnvironmentStrings, CreateToolhelp32Snapshot, IsProcessorFeaturePresent, NtQuerySystemInformation
If any of these return the incorrect information, the file will terminate immediately. Successfully bypassing these measures will drop two files named ‘Delfile.sys’ and ‘Del.exe’.
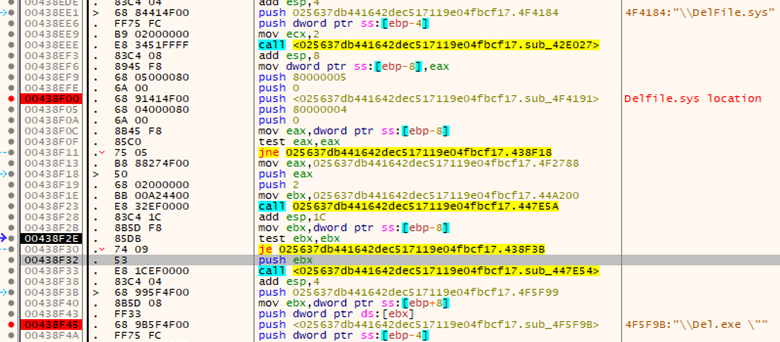
Figure 3: Embedded file locations
The .sys file is used explicitly to run ‘Del.exe’ and has a self-modifying section for runtime. There are no imports, functions or libraries listed. ‘Del.exe’ is used to control and register system services. A registry key is written to ‘SYSTEM\CurrentControlSet\Services\DelFile’. This is the persistence mechanism.
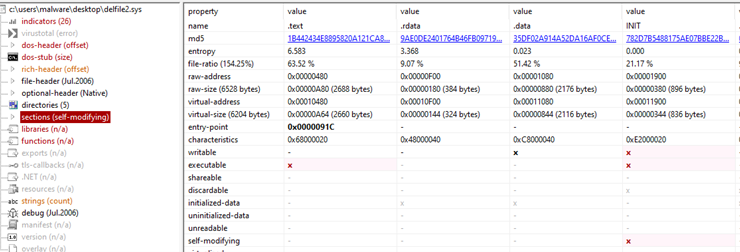
Figure 4: Output showing the self-modifying ‘INIT’ section of ‘Delfile.sys’
The main executable uses process injections to inject itself into KernelBase.dll where it hooks into and begins enumerating multiple areas of the system, including but not limited to:
- Keyboard/Mouse: GetKeyState, GetAsyncKeyState, GetCursorPos
- Processes: GetCurrentProcess, CreateToolhelp32Snapshot, Process32First, Process32Next
- Desktop: GetForegroundWindow, GetFocus, GetCapture
- Registry: RegQueryValue, RegOpenKey, RegCreateKey
- System Drive Volume: GetVolumeInformation
- Clipboard: GetClipboardData, FlushClipboardData
- Audio: waveOutWrite, midiStreamOpen
- Game software: Xbox, TenCent
The malware also looks for several networking applications: F5 VPN, Checkpoint VPN, SonicWall MobileConnect and Juniper Networks Junos Pulse. There also appears to be HTML code for a page that will show a fake error, potentially to grab credentials.
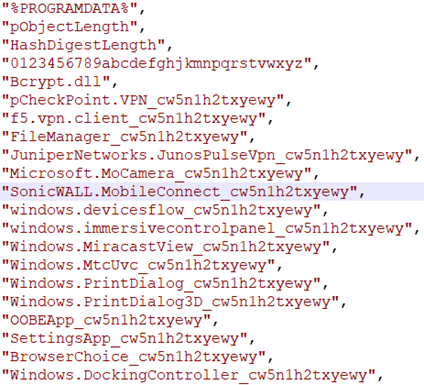
Figure 5: Partial list of software in unpacked sample
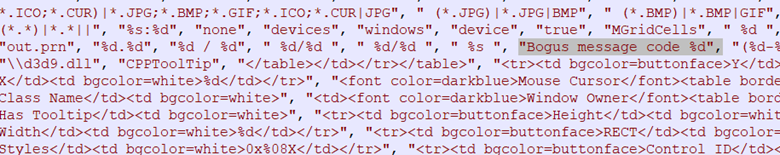
Figure 6: “Bogus message code” is referenced with HTML page code
In addition to this list, there are networking functions used to configure sockets using an older library (ws2_32.dll), along with bcrypt to encrypt any extracted data for transfer. All of the ws2_32 functions are obfuscated by using ordinals instead of the names. Additional tools confirm C2 capabilities, but no network connections were made during analysis.
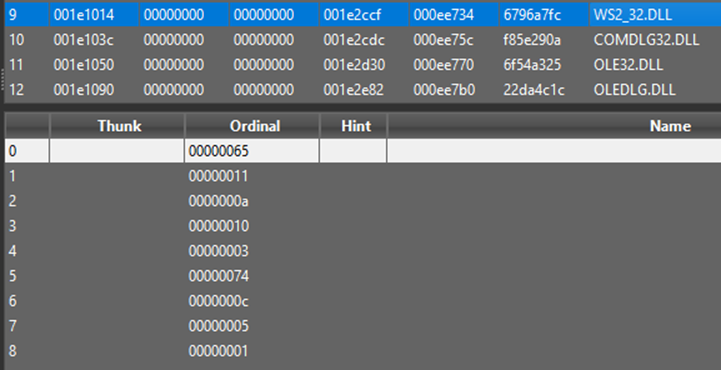
Figure 7: All of the function names have been removed and replaced with original codes
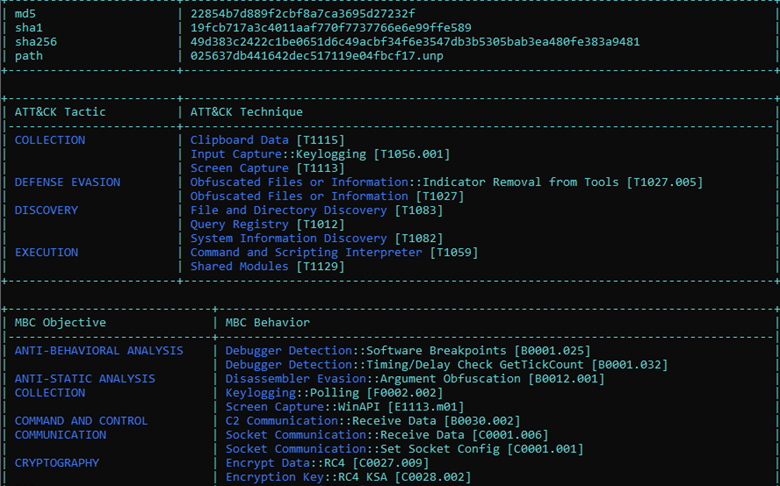
Figure 8: Partial output of capa showing evasion and C2 capabilities
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this malware, the following signatures have been released:
- MalAgent.Lang.A
- MalAgent.Lang.B
- MalAgent.Lang.Del.A
- MalAgent.Lang.Del.B
IOCs
Hashes
Main: 306710d0aef6d8f233f92a33530fce2758fab778cebe0dde2d047a50428b9813
Main (unpacked): 49d383c2422c1be0651d6c49acbf34f6e3547db3b5305bab3ea480fe383a9481
Del.exe: 7a21cd7f0364e50a2e631348e662a86fc7351ced4b7a9c8eb3f6d0688a2ec52d
Delfile.sys: 85cb69375e8be5ec8f0dfb130253fa13af3563d5dab2e4dc0b10c3dd1336c39a
URLs
- hxxp://yy[.]com/5336/1705313832
- hxxp://www.super-ec[.]cn
- hxxp://wghai[.]com/ec
- hxxp://qsyou[.]com/ec
- hxxp://www.wghai[.]com
- hxxp://bbs.wghai[.]com/forum-17-1.html/forum-12-1.html/memcp.php/ip.asp/time.asp/gonggao.txt/ec-user6.php/ec-bd.php/ec-jh.php




