Netgear ProSAFE NMS300 SQLi Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
The Netgear ProSAFE Network Management System (NMS300) is a centralized and comprehensive management application designed for network administrators. It enables them to discover, monitor, configure, and report on SNMP-based enterprise-class network devices. The Netgear Network Management System NMS300 provides insights into network elements, including third-party devices, and its web-based user interface simplifies the process of monitoring and administering an entire network.
An SQL injection vulnerability has been reported in Netgear ProSafe NMS300. This vulnerability arises due to improper input validation in the getNodesByTopologyMapSearch component.
A remote, authenticated attacker could exploit this vulnerability by sending a specially crafted request to the target server. Successful exploitation of this vulnerability could result in SQL injection or, in the worst-case scenario, remote code execution in the context of the SYSTEM user.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-38099.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.6 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 9.9 (AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is low.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.6 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
When a user navigates to the device list through the topology map search feature, an HTTP GET request is dispatched to the Request-URI “/topology.do?method=getDeviceListByDim”. Upon receipt of this request, the function TopologyMapController.getDeviceByDim() is invoked. This function displays the values of all devices identified in the preceding search request. Multiple parameter values are saved into different variables, with the ‘exclude’ parameter being of particular relevance to this vulnerability. The value for the ‘exclude’ parameter is stored in the ‘exclude’ variable.
Following this, the NodeInfoDao.getNodesTopologyMapSearch() method is invoked, passing the ‘exclude’ variable’s value into the ‘equips’ variable. This function is responsible for constructing and running the SQL query needed to fetch the specified device list. The corresponding SQL query is stored as a string in the ‘sql’ variable:
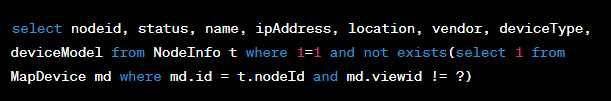
If the ‘equips’ variable’s value is not empty, the string ” and nodeId not in (equips) ” is appended to the ‘sql’ variable’s value (where equips is replaced by the ‘equips’ variable’s value). The SQL query contained in the ‘sql’ variable is then executed, and the result of the query is returned.
Triggering the Problem:
• The target must be running a vulnerable version of the software.
• The attacker must have network access to the vulnerable software.
• The attacker must have permission to view the device list via the Topology map search component.
Triggering Conditions:
The vulnerability is triggered when the HTTP request is received that includes an embedded SQL injection which will get triggered when the request is processed.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
What a successful GET Request might look like:
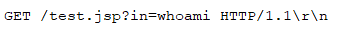
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 4001 NETGEAR ProSAFE NMS300 SQL Injection
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor-supplied patch to eliminate this vulnerability.
• Filtering traffic based on the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory
